You can choose how the users logging into the Nexus Dashboard GUI are authenticated. This release supports local authentication as well as LDAP, RADIUS, and TACACS remote authentication servers. User roles and permissions are described in this section, remote authentication configuration is described in Remote Authentication, and local user configuration is described in Users.
Roles and Permissions
Cisco Nexus Dashboard allows user access according to roles defined by role-based access control (RBAC). Roles are used in both local and external authentication and apply to either the Nexus Dashboard, the services running in it, or both. All roles can be assigned with read-only or write privileges. Read-only access allows the user to view objects and configurations, while write access allows them to make changes.
The following sections describes the user roles available in Nexus Dashboard and their associated permissions within the platform as well as the individual services.
The same roles can be configured on a remote authentication server and the server can be used to authenticate the Nexus Dashboard users. Additional details about remote authentication are available in the Remote Authentication section.
Nexus Dashboard and Orchestrator Roles
| User Role | ND Platform | Orchestrator Service |
|---|---|---|
|
Administrator |
Provides full access to all settings, features, and tasks. The only role that allows adding and removing services. |
Full access. |
|
Approver |
Same as |
Allows approval or denial of template configurations; does not allow editing or deploying templates. |
|
Dashboard User |
Allows access to the Dashboard view and launching applications; does not allow any changes to the Nexus Dashboard configurations. |
No access. |
|
Deployer |
Same as |
Allows the user to deploy templates to fabrics; does not allow editing or approving templates. |
|
Policy Manager |
Same as |
No access. |
|
Site Administrator |
Allows access to configurations related to the fabric on-boarding and configuration. |
Allows changing the fabric status between |
|
Site Manager |
Allows access to deployment of policies to the fabric. |
Allows policy, schema, and monitoring template (tenant SPAN) configurations. |
|
Tenant Manager |
Same as |
Allows tenant policy, schema, and monitoring template (tenant SPAN) configurations. |
|
User Manager |
Allows access to users settings, such as creating users, changing permissions, and adding remote authentication providers. |
No access. |
Each role above is associated with a set of permissions, which in turn are used to show relevant and hide not relevant elements from the user’s view.
Nexus Dashboard Insights
The Insights service does not support RBAC and any account that can log in to the Nexus Dashboard has full access to Insights.
Nexus Dashboard Fabric Controller Roles
| User Role | Nexus Dashboard Fabric Controller |
|---|---|
|
NDFC Access Admin |
Allows you to perform operations related to network interfaces in NDFC’s Interface Manager screen. An
However, an
|
|
NDFC Change Approver |
Users with this privilege can approve change control tickets. A user that is assigned with the NDFC Change Approver role can double-check changes that are associated with a specific ticket and approve or deny those changes. |
|
NDFC Change Deployer |
Users with this privilege can deploy change control tickets. |
|
NDFC Device Upgrade Admin |
Allows you to perform operations related to device upgrades in NDFC’s Image Management screen. |
|
NDFC Network Admin |
Allows full administrative access. |
|
NDFC Network Operator |
Allows read-only access the following NDFC menus:
A
However, a
|
|
NDFC Network Stager |
Allows you to make configuration changes, but a A
However, a
A |
Choosing Default Authentication Domain
By default, the login screen will select the local domain for user authentication; you can manually change the domain at login time by selecting any of the available login domains from the dropdown menu.
Alternatively, you can set a different default login domain to the most commonly used as follows:
The domain must already exist before you can set it as the default domain. Adding remote authentication domains is described in Remote Authentication.
-
Navigate to your Nexus Dashboard’s Admin Console.
-
Choose the default login domain.
-
From the main navigation menu, select Admin > Authentication.
-
In top right of the Default Authentication tile, click the Edit icon.
The Default Authentication window opens.
-
-
In the Default Authentication that opens, choose the Login Domain from the dropdown.
Remote Authentication
Cisco Nexus Dashboard supports a number of remote authentication providers, including LDAP, TACACS, and Radius.
When configuring external authentication servers:
-
You must configure each user on the remote authentication servers.
-
All LDAP configurations are case sensitive.
For example, if you have
OU=Cisco Userson the LDAP server andOU=cisco userson the Nexus Dashboard, the authentication will not work. -
For LDAP configurations, we recommend using
CiscoAVPairas the attribute string. If, for any reason, you are unable to use an Object ID1.3.6.1.4.1.9.22.1, an additional Object IDs1.3.6.1.4.1.9.2742.1-5can also be used in the LDAP server.Alternatively, instead of configuring the Cisco AVPair values for each user, you can create LDAP group maps in the Nexus Dashboard.
-
Single sign-on (SSO) between the Nexus Dashboard, fabrics, and applications is available for remote users only.
-
When using SSO to cross-launch into an APIC fabric from your Nexus Dashboard’s Fabrics page, the AV pairs defined for the Nexus Dashboard user are also used when logging into the APIC.
For example, a user defined as
adminfor the Nexus Dashboard cluster will also haveadminprivileges in the APIC.
Configuring Remote Authentication Server
When configuring the remote authentication server for the Nexus Dashboard users, you must add a custom attribute-value (AV) pair, specifying the username and the roles assigned to them.
The user roles and their permissions are the same as for the local users you would configure directly in the Nexus Dashboard GUI as described in Roles and Permissions.
The following tables list the Nexus Dashboard user roles and the AV pair you would use to define the roles on a remote authentication server, such as LDAP.
| User Role | AV Pair Value |
|---|---|
|
Administrator |
|
|
Approver |
|
|
Dashboard User |
|
|
Deployer |
|
|
Policy Manager |
|
|
Site Administrator |
|
|
Site Manager |
|
|
Tenant Manager |
|
|
User Manager |
|
| User Role | AV Pair Value |
|---|---|
|
NDFC Access Admin |
|
|
NDFC Device Upgrade Admin |
|
|
NDFC Network Admin |
|
|
NDFC Network Operator |
|
|
NDFC Network Stager |
|
The AV pair string format differs when configuring a read-write role, read-only role, or a combination of read-write and read-only roles for a specific user.
Note that ND must have its own AV pair value (such as "all//app-user|site-admin"), even if users are only using NDFC. The ND AV pair value of “app-user” is not sufficient for the NDFC administrator role. You must configure the AV pair value of "admin" or "site-admin" for the NDFC administrator. If you don’t configure the AV pair value, it can cause NDFC pages to not load properly.
A typical string includes the domain, followed by the read-write roles separated from the read-only roles using the slash (/) character; individual roles are separated by the pipe (|) character:
shell:domains=<domain>/<writeRole1>|<writeRole2>/<readRole1>|<readRole2>
For example, the following string illustrates how to assign the Tenant Manager and Policy Manager roles to a user, while still allowing them to see objects visible to the User Manager users:
shell:domains=all/tenant-policy|site-policy/aaa
Note that if you want to configure only the read-only or only read-write permissions for a user, you must still include the slash (/) character. The following examples show how to set just the read-write or read-only access to the objects available to Site Administrator role:
-
Read-only:
shell:domains=all//site-admin -
Read-write:
shell:domains=all/site-admin/
Adding LDAP as Remote Authentication Provider
-
You must have at least one user already configured on the LDAP server as described in Configuring Remote Authentication Server.
You will need to use an existing user for end-to-end verification of LDAP configuration settings.
To add an LDAP remote authentication provider:
-
Navigate to your Nexus Dashboard’s Admin Console.
-
Add an authentication domain.
-
From the main navigation menu, select Admin > Authentication.
-
In the main pane, click the Actions menu and select Create Login Domain.
-
-
In the Create Login Domain screen that opens, provide domain details.
-
Provide the Name for the domain.
-
(Optional) Provide its Description.
-
From the Realm dropdown, select
Ldap. -
Then click +Add Provider to add a remote authentication server.
The Add Provider window opens.
-
-
Provide the remote authentication server details.
-
Provide the Hostname or IP Address of the server.
-
(Optional) Provide the Description of the server.
-
Provide the Port number.
The default port is
389for LDAP. -
Provide the Base DN and Bind DN.
The Base DN and Bind DN depend on how your LDAP server is configured. You can get the Base DN and Bind DN values from the distinguished name of the user created on the LDAP server.
Base DN is the point from which the server will search for users. For example,
DC=nd,DC=local.Bind DN is the credentials used to authenticate against the server. For example,
CN=admin,CN=Users,DC=nd,DC=local. -
Provide and confirm the Key.
This is the password for your Bind DN user. Anonymous bind is not supported, so you must provide a valid value in these fields.
-
Specify the Timeout and number of Retries for connecting to the authentication server.
-
Provide the LDAP Attribute field for determining group membership and roles.
The following two options are supported:
-
ciscoAVPair(default) — used for LDAP servers configured with Cisco AVPair attributes for user roles. -
memberOf— used for LDAP servers configured with LDAP group maps. Adding a group map is described in a following step.
-
-
(Optional) Enable SSL for LDAP communication.
If you enable SSL, you must also provide the SSL Certificate and the SSL Certificate Validation type:
-
Permissive: Accept a certificate signed by any certificate authority (CA) and use it for encryption. -
Strict: Verify the entire certificate chain before using it.
-
-
Choose Default or Custom in the Filter Type field.
If you choose Custom LDAP filter, a sample of a working syntax is
(cn={username}). -
(Optional) Enable Server Monitoring.
If you choose to enable monitoring, you must also provide the Username and Password for it.
-
In the Validation fields, provide a Username and Password of a user already configured on the LDAP server you are adding.
Nexus Dashboard will use this user to verify the end-to-end authentication to ensure that the settings you provided are valid.
-
Click Save to complete provider configuration.
-
Repeat this step for any additional LDAP authentication servers you want to use with this domain.
-
-
(Optional) Enable and configure LDAP Group Map Rules.
If you want to authenticate your LDAP users using Cisco AV pair strings, skip this step.
-
In the LDAP Auth Choice, select
LDAP Group Map Rules. -
Click Add LDAP Group Map Rule.
The Add LDAP Group Map Rule window opens.
-
Provide the Group DN for the group.
The format depends on your LDAP tree. For example:
DN=xxx,OU=xxx,DC=xxxand so on. -
Select one or more Roles for the group.
-
Click Save to save the group configuration.
-
Repeat this step for any additional LDAP groups.
-
-
Click Create to finish adding the domain.
Adding Radius or TACACS as Remote Authentication Provider
-
You must have at least one user already configured on the remote authentication server as described in Configuring Remote Authentication Server.
You will need to use an existing user for end-to-end verification of the provider configuration settings.
To add a Radius or TACACS remote authentication provider:
-
Navigate to your Nexus Dashboard’s Admin Console.
-
Add an authentication domain.
-
From the main navigation menu, select Admin > Authentication.
-
In the main pane, click the Actions menu and select Create Login Domain.
-
-
In the Create Login Domain screen that opens, provide domain details.
-
Provide the Name for the domain.
-
(Optional) Provide its Description.
-
From the Realm dropdown, select
RadiusorTacacs. -
Then click +Add Provider to add a remote authentication server.
The Add Provider window opens.
-
-
Provide the remote authentication server details.
-
Provide the Hostame or IP Address of the server.
-
(Optional) Provide the Description of the server.
-
Choose Authorization Protocol used by the server.
You can choose
PAP,CHAP, orMS-CHAP. -
Provide the Port number.
The default port is
1812for RADIUS and49for TACACS -
Provide and confirm the Key.
This is the password used for connecting to the provider server.
-
(Optional) Choose whether you want to enable Server Monitoring.
If you choose to enable monitoring, you must also provide the Username and Password for it.
-
In the Validation fields, provide a Username and Password of a user already configured on the remote server you are adding.
Nexus Dashboard will use this user to verify the end-to-end authentication to ensure that the settings you provided are valid.
-
Click Save to complete provider configuration.
-
Repeat this step for any additional remote authentication servers.
-
-
Click Create to finish adding the domain.
Validating Remote User Logins
Nexus Dashboard provides a way to validate reachability of the remote authentication provider by performing a login attempt using a specific user’s credentials.
-
Navigate to your Nexus Dashboard’s Admin Console.
-
Navigate to the domain you want to test.
-
From the main navigation menu, select Admin > Authentication.
-
Click on a specific domain.
-
In the right properties sidebar, click the details icon.
The domain’s Overview page opens.
-
-
In the Overview page, click Validate next to the provider you want to test.
-
In the Validate Provider window, enter the Username and Password of a user defined in this authentication provider and click Validate
You will see a message indicating whether authentication was successful or not.
If authentication failure message is displayed, ensure that the authentication provider server is reachable and the user credentials you used to test are valid and configured on the provider.
Editing Remote Authentication Domains
If you want to make changes to a domain you have created:
-
Navigate to your Nexus Dashboard’s Admin Console.
-
From the main navigation menu, select Admin > Authentication.
-
From the Actions menu for the domain, select Edit Login Domain.
You cannot change the name and the type of the authentication domain, but you can make changes to the description and provider configuration.
If you make any changes to the login domain, including simply updating the description, you must re-enter the
keyfor all existing providers.
Deleting Remote Authentication Domains
-
Navigate to your Nexus Dashboard’s Admin Console.
-
From the main navigation menu, select Admin > Authentication.
-
From the Actions menu for the domain, select Delete Login Domain.
-
In the Confirm Delete prompt, click OK to confirm.
Multi-Factor Authentication
Starting with Release 2.1.2, you can configure your Nexus Dashboard to use multi-factor authentication (MFA) for user login.
When configuring multi-factor authentication:
-
You will configure each user in your MFA provider, as described in Configuring Okta Account as MFA Provider
This release supports only Okta as MFA provider.
-
You will establish MFA provider and client integration, as described in Configuring MFA Client.
This release supports only Duo as MFA client.
-
You will add the MFA provider as an external authentication domain in Nexus Dashboard, as described in Adding Okta as Remote Authentication Provider.
Configuring Okta Account as MFA Provider
The following steps provide basic configuration required to enable MFA for Nexus Dashboard using Okta as a provider. Detailed Okta configurations are outside the scope of this document, see Okta documentation for all available options.
To configure Okta for Nexus Dashboard MFA:
-
Log in to your Okta account.
To create an account, browse to https://developer.okta.com.
-
Create a new app integration.
-
From the left navigation menu, select Applications > Applications.
-
Click Create App Integration.
-
For Sign-in method, select
OIDC - OpenID Connect. -
For Application Type, select
Web Application. -
Click Next.
-
Provide App integration name, for example,
nd-mfa.The following steps assume you used
nd-mfaas the app integration name. If you choose a different name, replacend-mfawhere appropriate. -
For Sign-in redirect URIs, enter
https://<nd-node1-ip>/oidccallbackReplace the
<nd-node1-ip>with your cluster node IP address, then click +Add URI to provide the URIs for all nodes in the cluster. -
For Controlled Access, choose
Skip group assignment for now. -
Leave other fields at their default values and click Save.
-
-
Add the required attributes to the default user.
-
From the left navigation menu, select Directory > Profile Editor.
-
Click the Okta User (default) profile.
-
Click +Add Attribute.
-
For Data type, choose
string. -
For Display name, Variable name, and Description, enter
CiscoAVPair. -
Ensure that Attribute required is
unchecked. -
Leave other fields at default values and click Save and Add Another.
-
For Data type, choose
string. -
For Display name, Variable name, and Description, enter
nduser. -
Ensure that Attribute required is
unchecked. -
Leave other fields at default values and click Save.
-
-
Add the required attributes to the
nd-mfauser you created.-
From the left navigation menu, select Directory > Profile Editor.
-
Click the nd-mfa User (default) profile.
-
Click +Add Attribute.
-
For Data type, choose
string. -
For Display name, Variable name, and Description, enter
CiscoAVPair. -
Ensure that Attribute required is
checked. -
Leave other fields at default values and click Save and Add Another.
-
For Data type, choose
string. -
For Display name, Variable name, and Description, enter
nduser. -
Ensure that Attribute required is
checked. -
Leave other fields at default values and click Save.
-
-
Map the attributes.
-
From the left navigation menu, select Directory > Profile Editor.
-
Click the nd-mfa User profile.
-
In the Attributes area of the main window, click Mappings.
The nd-mfa User Profile Mappings window opens.
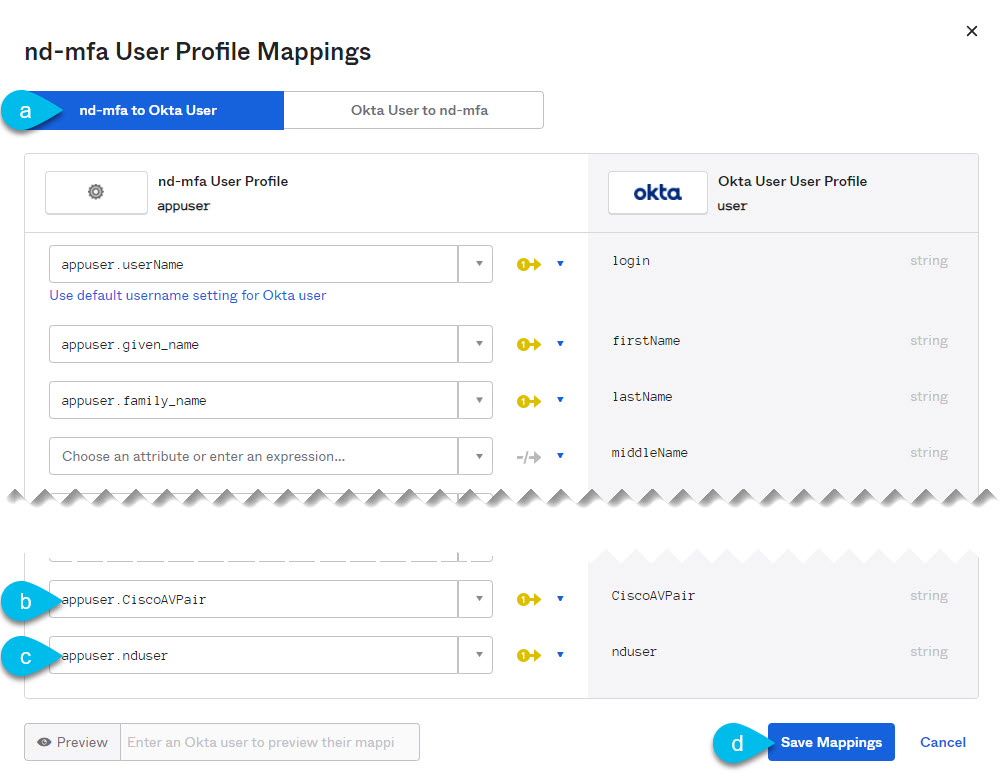
-
At the top of the nd-mfa User Profile Mappings window, click nd-mfa to Okta User.
-
Select
app.CiscoAVPairfrom the dropdown menu next toCiscoAVPair. -
Select
app.nduserfrom the dropdown menu next tonduser. -
Click Save Mappings.
-
Click Apply updates now.
-
-
Create users.
-
From the left navigation menu, select Directory > People.
-
Click +Add person.
-
Provide the user information.
-
Click Save and Add Another to add another user or click Save to finish.
You must add all users that you want to be able to log in to your Nexus Dashboard.
-
-
Assign users to the app.
-
From the left navigation menu, select Applications > Application.
-
Click the application you created (
nd-mfa). -
Select the Assignments tab.
-
Choose Assign > Assign to People.
The Assign nd-mfa to People window opens.
-
In the Assign nd-mfa to People window, click Assign next to the user you want to be able to log in to your Nexus Dashboard.
-
In the user details window that opens, provide a value for CiscoAVPair and nduser fields.
The CiscoAVPair values are described in the Configuring Remote Authentication Server, for example
shell:domains=all/admin/.The nduser value will be used as the username for this user when logging in to your Nexus Dashboard.
-
Click Save and Go Back.
-
Assign another user or click Done to finish.
You must add all users that you created in a previous step.
-
-
Configure Claims for the app.
-
From the left navigation menu, select Security > API.
-
Click the default name.
-
Select the Claims tab.
-
Click +Add Claim to add the
CiscoAVPairclaim. -
In the Name field, enter
CiscoAVPair. -
From the Include in token type dropdown, select
ID Token.We recommend using
ID Token, howeverAccess Tokenis also supported. -
In the Value field, enter
appuser.CiscoAVPair. -
Click Save.
-
Click +Add Claim to add the
nduserclaim. -
In the Name field, enter
nduser. -
From the Include in token type dropdown, select
ID Token.You must create both claims in the same token, mixing
ID TokenandAccess Tokenis not supported. -
In the Value field, enter
appuser.nduser. -
Click Save.
-
-
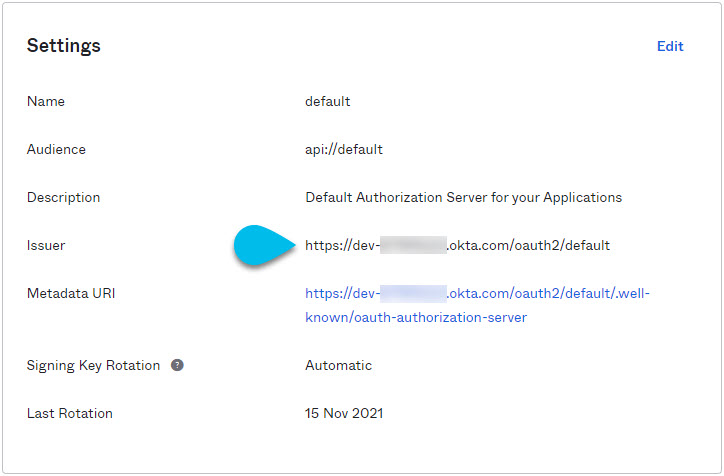
Gather the required Okta account information for adding it as authentication provider for your Nexus Dashboard.
-
From the left navigation menu, select Security > API.
-
Click the default name.
-
Note down the Issuer value.
-
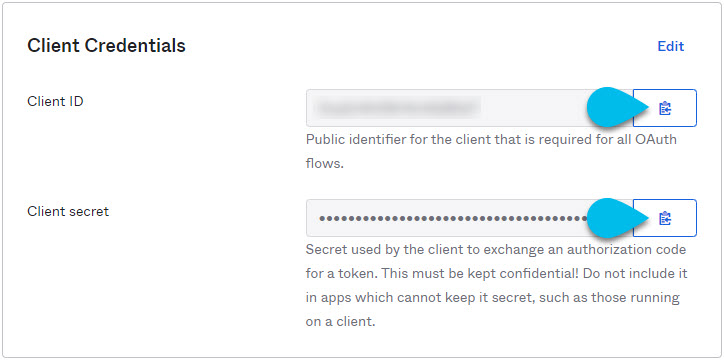
From the left navigation menu, select Application > Applications.
-
Click the application you created (
nd-mfa). -
Note down the Client ID and Client Secret values.
-
Configuring MFA Client
This release supports only Cisco Duo as MFA client.
The following steps provide basic configuration required to enable using Cisco Duo for Nexus Dashboard MFA. Detailed Duo configurations are outside the scope of this document, see Cisco Duo documentation for all available options.
To configure Duo:
-
Log in to your Okta account.
-
Add DUO as an MFA type.
-
From the left navigation menu, select Security > Multifactor.
-
In the Factor Types tab, select
Duo Security.If you do not have the
Duo Securityoption, you will need to open a support case with Okta from https://support.okta.com/help/s/opencase. -
In the Duo Security window, provide the required information.
For more information on how to obtain integration key, secret key, and API hostname, see https://duo.com/docs/okta.
Ensure that Duo Username Format is set to
Email. -
Click Save.
-
-
Create a Duo rule.
-
From the left navigation menu, select Applications > Application.
-
Click the application you created (
nd-mfa). -
Select the Sign On tab.
-
In the Sign On Policy area, click +Add Rule.
-
Provide the name for the rule.
-
In the Access area, enable Prompt for factor and select Every sign on.
-
Specify other options as required by your use case.
-
Click Save.
-
-
Configure Okta and Duo integration.
There are two ways you can allow the users you configured in Okta to use the Duo app for MFA — have the Duo admin add all the same users in Duo dashboard or have each individual user log in to Okta and self-enroll.
To configure users in Duo dashboard:
-
Log in to your Duo dashboard as admin user.
-
From the left navigation menu, select Users.
-
Click Add User and provide the details that match the user’s information in Okta.
-
Repeat this step for all users you added in Okta.
To self-enroll:
-
Instruct every user you created in Configuring Okta Account as MFA Provider to log in to Okta on their own using your specific Okta domain.
You can determine the Okta domain to use by navigating to Application > Application, then clicking the
nd-mfaapplication you created and copying the Okta domain URL: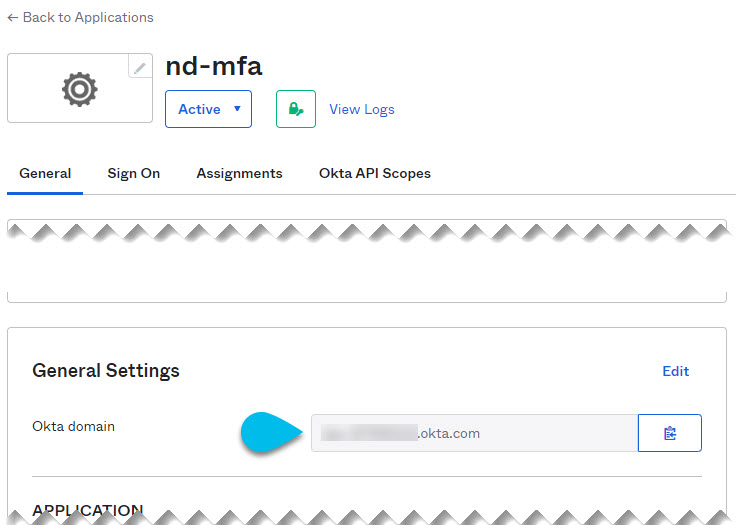
-
Once they’re logged in, they can navigate to the Settings page from the top right user menu.
-
Choose Duo Security Setup and follow the instructions on the screen.
-
Adding Okta as Remote Authentication Provider
-
You must have at least one user already configured in Okta as described in Configuring Okta Account as MFA Provider.
-
You must have the Client ID, Client Secret, and Issuer information from your Okta account available, which is described in the last step of Configuring Okta Account as MFA Provider.
-
If you want to use a proxy to connect to your Okta account, the proxy must already be configured as described in System Settings.
To add Okta as remote authentication provider:
-
Log in to your Nexus Dashboard as an
adminuser. -
Navigate to the Admin Console.
-
Add an authentication domain.
-
From the main navigation menu, select Admin > Authentication.
-
In the main pane, click the Actions menu and select Create Login Domain.
-
-
In the Create Login Domain screen that opens, provide domain details.
-
Provide the Name for the domain.
-
(Optional) Provide its Description.
-
From the Realm dropdown, select
OIDC. -
In the Client ID field, enter the client ID you obtained from your Okta account.
-
In the Client Secret field, enter the client secret you obtained from your Okta account.
-
In the Issuer field, enter the URI you obtained from your Okta account.
-
(Optional) Check the User Proxy option if you want to connect to Okta over a proxy.
-
Leave the Scopes options unchecked.
This release supports the
openidscope only.
-
-
Click Create to finish adding the domain.
Logging In To Nexus Dashboard Using MFA
-
Navigate to one of your Nexus Dashboard IPs as your typically would.
-
From the Login Domain dropdown, select the OIDC domain you created in Adding Okta as Remote Authentication Provider.
The Username and Password fields will not be displayed.
-
Click Login.
You will be redirected to the Okta login page.
-
Log in using a user that was configured in Okta as described in Configuring Okta Account as MFA Provider.
A push notification will be sent to your Duo client.
-
Approve the login using Duo.
You will be redirected back to the Nexus Dashboard UI and logged in using the Okta user.
Users
The Users GUI page allows you to view and manage all users that have access to the Nexus Dashboard.
The Local tab displays all local users while the Remote tab displays users that are configured on the remote authentication servers you have added as described in the Remote Authentication section.
-
The default local
adminuser cannot be deleted. -
Single sign-on (SSO) between the Nexus Dashboard, fabrics, and applications is available for remote users only. For more information on configuring remote users, see Remote Authentication.
Adding Local Users
-
Navigate to your Nexus Dashboard’s Admin Console.
-
Create a new local user.
-
From the main navigation menu, select Admin > Users.
-
In the main pane, click Create Local User.
-
-
In the Create Local User screen that opens, provide user details.
-
Provide the User ID that will be used for loggin in.
-
Provide and confirm the initial Password.
-
Provide the First Name, Last Name, and Email Address for the user.
-
Choose the user’s Roles and Privileges.
You can select one or more roles for each user. The available roles and their permissions are described in Roles and Permissions.
For all of the user roles you select, you can choose to enable read-only or read-write access. In case of read-only access, the user will be able to view the objects and settings allowed by their user Role but unable to make any changes to them.
-
Click Create to save the user.
-
Editing Local Users
-
Navigate to your Nexus Dashboard’s Admin Console.
-
Open user details screen.
-
From the main navigation menu, select Admin > Users.
-
In the main pane, click on the user’s name.
-
In the details pane that opens, click the Details icon.
-
-
In the <user-name> details screen that opens, click the Edit icon.
-
In the Edit User screen that opens, update the settings as necessary.
Security
The Security GUI page allows you to view and manage certificates used by the Nexus Dashboard.
Security Configuration
The Administrative > Security Configuration page allows you to configure authentication session timeouts and security certificates used by your Nexus Dashboard cluster.
-
You must have the keys and certificates you plan to use with Nexus Dashboard already generated.
Typically, this includes the following files:
-
Private key (
nd.key) -
Certificate Authority’s (CA) public certificate (
ca.crt) -
CA-signed certificate (
nd.crt)
Generating these files for self-signed certificates is described in Generating Private Key and Self-Signed Certificate.
-
-
We recommend creating a configuration backup of your Nexus Dashboard cluster before making changes to the security configurations.
For more information about backups, see "Backup and Restore" in Nexus Dashboard Operations.
To edit security configuration:
-
Navigate to your Nexus Dashboard’s Admin Console.
-
Edit security configuration.
-
From the main navigation menu, select Admin > Security.
-
In the main pane, select the Security Configuration tab.
-
In the main pane, click the Edit icon.
-
-
In the Security Configuration screen that opens, update one or more fields as required:
Note that uploading the keys and certificate files is not supported and you will need to paste the information in the following fields.
-
Update the Session Timeout.
This field defines the duration of the API tokens with the default duration set to 20 minutes.
-
Update the Idle Timeout.
This field defines the duration of the UI session.
-
In the Domain Name field, provide your domain.
-
Select Check the Enforce Strict Content Security Policy to disable Qualtrics integration from the browser at a system wide level.
-
Click the SSL Ciphers field and select any additional cipher suites you want to enable from the dropdown or click the x icon on an existing cipher suite to remove it.
Cipher suites define agorithms (such as key exchange, bulk encryption, and message authentication code) used to secure a network connection. This field allows you to customize which cipher suites your Nexus Dashboard cluster will use for network communication and disable any undesired suites, such as the less secure TLS1.2 and TLS1.3.
-
In the Key field, provide your private key.
-
In the RSA Certificate field, provide the CA-signed or self-signed certificate.
-
In the Root Certificate field, provide the CA’s public certificate.
-
(Optional) If your CA provided an Intermediate Certificate, provide it in the Intermediate Certificate field.
-
Click Save to save the changes.
After you save your changes, the GUI will reload using the new settings.
-
Security Domains
A restricted security domain allows an administrator to prevent a group of users from viewing or modifying any objects created by a group of users in a different security domain, even when users in both groups have the same assigned privileges.
For example, an administrator in restricted security domain (domain1) will not be able to see fabrics, services, cluster or user configurations in another security domain (domain2).
Note that a user will always have read-only visibility to system-created configurations for which the user has proper privileges. A user in a restricted security domain can be given a broad level of privileges within that domain without the concern that the user could inadvertently affect another group’s physical environment.
To create a security domain:
-
Navigate to your Nexus Dashboard’s Admin Console.
-
Create a new security domain.
-
From the main navigation menu, select Admin > Security.
-
In the main pane, select the Security Domains tab.
-
In the main pane, click Create Security Domain.
-
-
In the Create Security Domain screen that opens, provide the domain details.
-
Provide the Name for the domain.
-
(Optional) Provide a description for the domain.
-
Click Create to save the domain.
-
Validating Peer Certificates
You can import a fabric controller’s Certificate Authority (CA) root certificate chain into Nexus Dashboard. This allows you to verify that the certificates of hosts to which your Nexus Dashboard connects (such as fabric controllers) are valid and are signed by a trusted Certificate Authority (CA) when you add the fabrics.
Exporting Certificate Chain From Cisco APIC
-
Log in to your Cisco APIC.
-
Check which key ring is being used for management access:
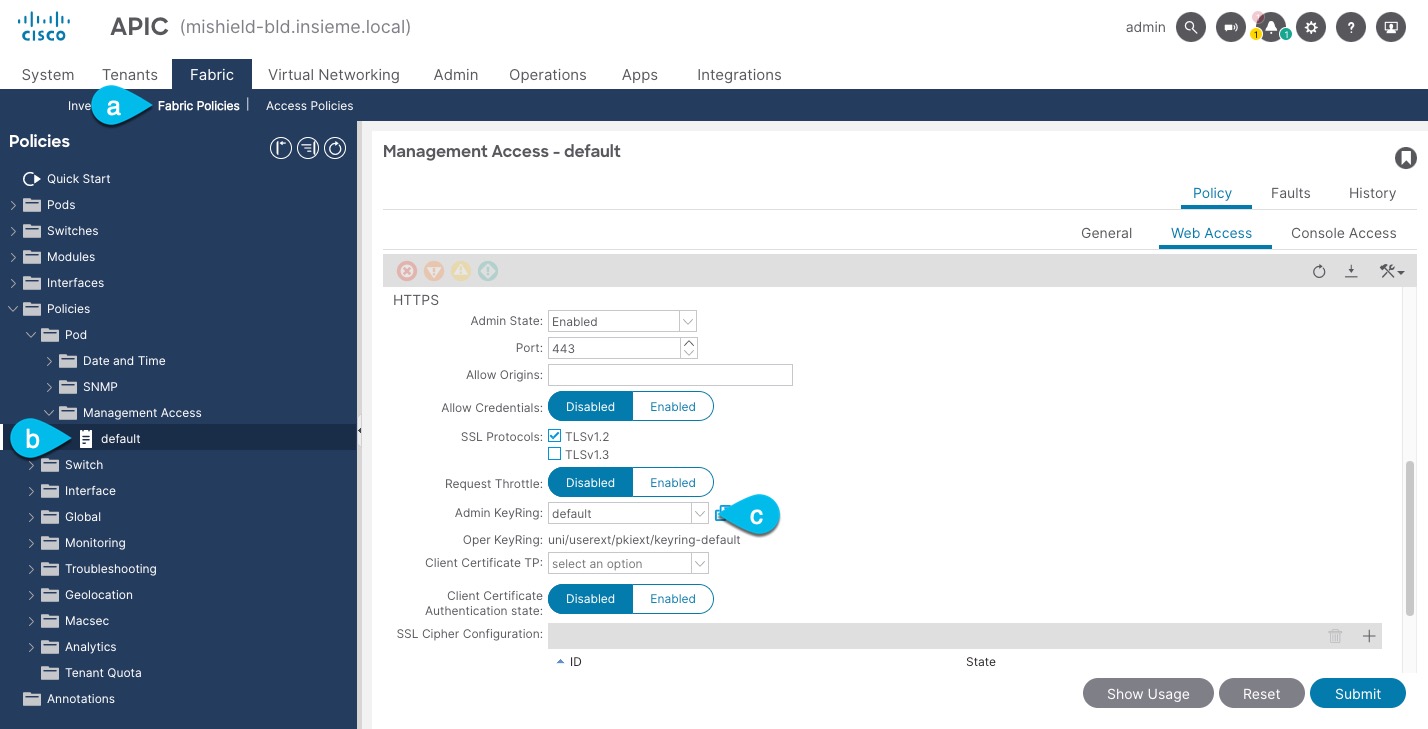
-
In the top navigation bar, choose Fabric > Fabric Policies.
-
In the left navigation menu, choose Policies > Pod> Management Access.
-
In the main pane, note the name in the Admin KeyRing field.
In the above example, the
defaultkey ring is being used. However, if you created a custom key ring with a custom certificate chain, the name of that key ring would be listed in the Admin KeyRing field.Custom security configuration for Cisco APIC is described in detail in Cisco APIC Security Configuration Guide for your release.
-
-
Export the certificate used by the key ring:
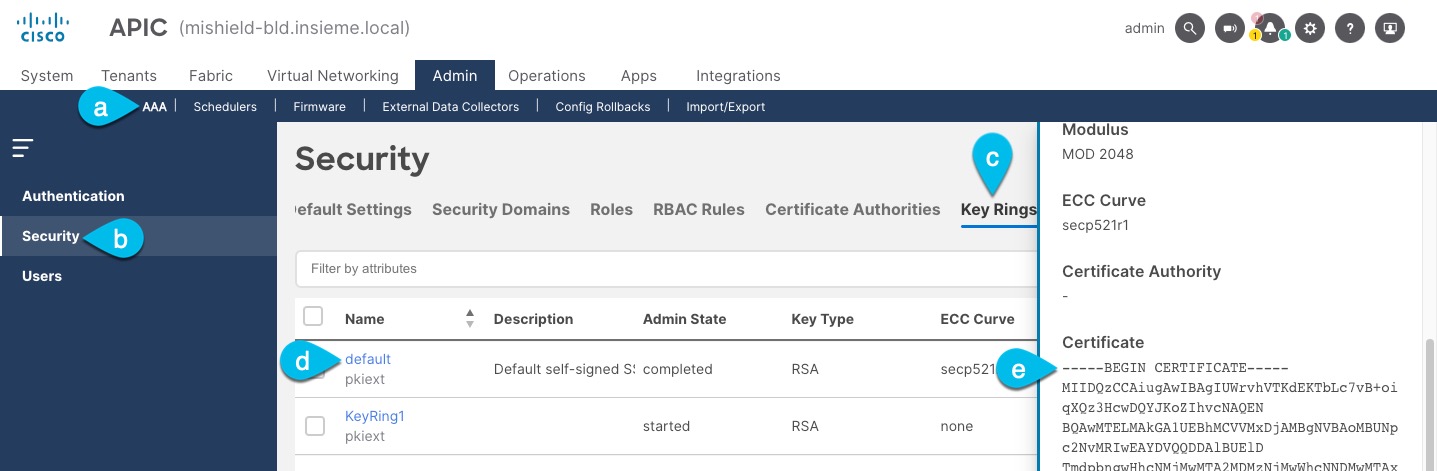
-
In the top navigation bar, choose Admin > AAA.
-
In the left navigation menu, choose Security.
-
In the main pane, choose the Key Rings tab.
-
Click the name of the key ring you found in the previous step and copy the Certificate.
The above example shows the
defaultkey ring from the previous step. However, if you had a custom key ring configured, choose the CA certificate chain used to create the key ring.You must include the
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----in the text you copy, for example:-----BEGIN CERTIFICATE----- MIIDQzCCAiugAwIBAgIUWrvhVTKdEKTbLc7vB+oiqXQz3HcwDQYJKoZIhvcNAQEN [...] -----END CERTIFICATE-----
-
Exporting Certificate Chain From Cisco NDFC
-
Log in to the Nexus Dashboard that’s hosting the service.
In case of NDFC, there is no separate certificate from the service so you use the Nexus Dashboard host’s certificate.
-
Export the certificate.
-
In the main navigation menu, choose Admin > Security.
-
In the main pane, choose the Security Configuration tab
-
In the Security Configuration page, click the Edit icon.
-
Copy the Root Certificate.
We recommend copying the certificate chain from the Edit page instead of directly from the Security Configuration page to ensure that there are no spaces or new line characters (
\n) in the string you copy.
You must include the
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----in the text you copy, for example:-----BEGIN CERTIFICATE----- MIIDhTCCAm2gAwIBAgIIOqlnNF7g9e8wDQYJKoZIhvcNAQELBQAwSzELMAkGA1UE [...] -----END CERTIFICATE-----
-
Exporting Certificate Chain From Cisco DCNM
-
SSH in to you Cisco DCNM as the
sysadminuser.Unlike the other fabric controllers, DCNM certificates are not available in the UI, so you must use the CLI.
# ssh -l sysadmin <dcnm-ip-address> -
Change into the
/var/lib/dcnm/afw/apigateway/directory.The certificate (
dcnmweb.crt) file is located in this directory.dcnm# cd /var/lib/dcnm/afw/apigateway/ dcnm# ls -ltr /* View the contents of the folder total 128 -rw------- 1 root root 1844 Nov 18 13:14 dcnmweb.key.2019-11-20T132939-08:00 -rw-r--r-- 1 root root 1532 Nov 18 13:14 dcnmweb.crt.2019-11-20T132939-08:00 -rw------- 1 root root 1844 Nov 20 10:15 dcnmweb.key.2019-11-20T132950-08:00 -rw-r--r-- 1 root root 1532 Nov 20 10:15 dcnmweb.crt.2019-11-20T132950-08:00 -rw------- 1 root root 1844 Dec 22 13:59 dcnmweb.key -rw-r--r-- 1 root root 1532 Dec 22 13:59 dcnmweb.crt -
Check for root certificate.
Depending on which Certificate Authority you used to sign your certificate, the root certificate may be included in the
dcnmweb.crtfile or may be provided as a separate file.To check whether the root certificate is included:
dcnm# openssl x509 -text -noout -in dcnmweb.crtIf the file includes the root certificate, copy it. Otherwise, use the root certificate file you should have obtained when signing your certificate.
Exporting Certificate Chain From Cisco Cloud Network Controller
-
Log in to your Cisco Cloud Network Controller.
-
Export the certificate.
-
In the main navigation menu, choose Admin > Security.
-
In the main pane, choose the Key Rings tab.
-
Click the name of the certificate you want to import into your Nexus Dashboard and copy the Certificate Authorities.
The above example shows the
defaultkey ring. However, if you had a custom key ring configured, choose the CA certificate chain used to create the key ring.You must include the
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----in the text you copy, for example:-----BEGIN CERTIFICATE----- MIIDvTCCAqWgAwIBAgIJAI6W9R8DXDgLMA0GCSqGSIb3DQEBDQUAMEAxCzAJBgNV [...] -----END CERTIFICATE-----
-
Importing Certificates Into Nexus Dashboard
-
Log in to your Nexus Dashboard where you plan to onboard the fabrics.
-
Import the certificate into Nexus Dashboard.
-
Log in to your Nexus Dashboard where you will onboard the fabrics.
-
In the left navigation menu, choose Admin > Security.
-
In the main pane, select the CA Certificates tab.
-
Click Add CA certificate, provide a unique name for the certificate, and paste the certificate chain you copied from your fabric’s controller.
-
-
Proceed with adding the fabric as you typically would, but enable the Verify Peer Certificate option.
Note that if you enable the Verify Peer Certificate option but don’t import the valid certificate, fabric onboarding will fail.
Adding fabrics is described in Adding Fabrics.
Trademarks
THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: http://www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
© 2017-2024 Cisco Systems, Inc. All rights reserved.
First Published: 2024-03-01
Last Modified: 2024-03-01
Americas Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 527-0883