Introduction
This document provides sample configurations for Converged Access deployment in a small-branch single switch network. These configurations can be used across hundreds or even thousands of branches to deploy the wireless network at the branch locations with tried and tested configurations.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on these software and hardware versions:
- Catalyst 3850 Series Switch
- Cisco IOS Version 03.03.00SE or later
- Cisco IES Version 1.2 or later
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
The small-size remote branch office or retail store can consist of a single or a stack of ethernet switches to provide network connectivity to the wired and wireless users. Such small networks can converge the ethernet switching with next-generation wireless capability on the same catalyst switch.
For such network designs, the switch can integrate Wireless LAN Controller (WLC) mobility controller and mobility agent (MA) functions without requiring any additional Converged Access elements, such as Switch-Peer-Group (SPG) in the network. These networks can require guest wireless services, as well as common security and network access policy enforcement across all branch offices.
Configure
Network Diagram
This image illustrates a reference topology for a typical branch network.
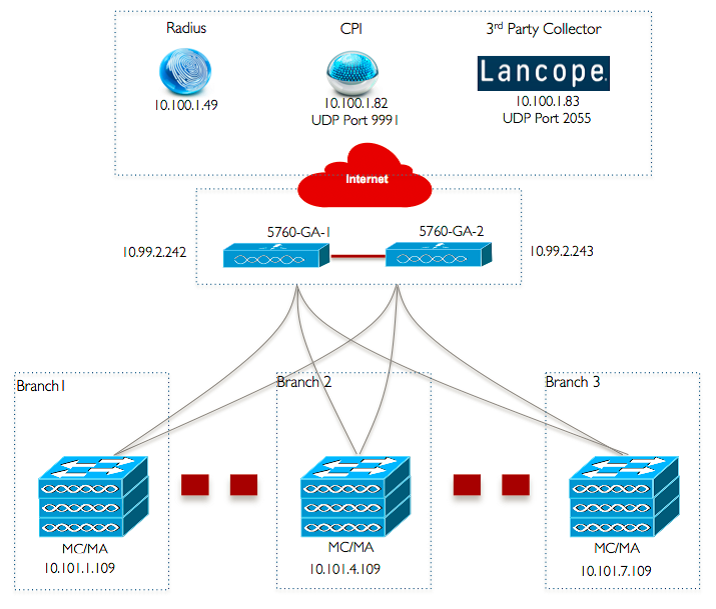
Configurations
Base Layer 2/3 Configuration
- VLAN Trunk Protocol (VTP) Mode: Transparent
This example shows the configuration of VTP mode.
vtp domain ‘name'
vtp mode transparent
- Spanning Tree: Rapid-Per VLAN Spanning tree (PVST)
This example shows the Rapid-PVST configuration.
spanning-tree mode rapid-pvst
spanning-tree portfast default
spanning-tree portfast bpduguard default
spanning-tree portfast bpdufilter default
spanning-tree extend system-id
This example shows how the VLANs are created.
vlan 151
name Voice_VLAN
!
vlan 152
name Video_VLAN
!
vlan 155
name WM_VLAN
!
vlan 158
name 8021X_WiFi_VLAN
- Configure Default Gateway
The Default Gateway configuration is shown in this example.
ip default-gateway <ip address>
ip route vrf Mgmt-vrf 0.0.0.0 0.0.0.0 172.26.150.1
- Configure Management Virtual Routing and Forwarding (VRF)
The Management VRF configuration is shown in this example.
interface GigabitEthernet0/0
description Connected to FlashNet - DO NOT ROUTE
vrf forwarding Mgmt-vrf
ip address 172.26.150.202 255.255.255.0
no ip redirects
no ip proxy-arp
load-interval 30
carrier-delay msec 0
negotiation auto
no cdp enable
vrf definition Mgmt-vrf
- Configure IP DHCP Snooping
In this example, DHCP snooping is configured for all wireless client VLANs.
ip dhcp snooping vlan 151-154,156-165
no ip dhcp snooping information option
ip dhcp snooping wireless bootp-broadcast enable
ip dhcp snooping
Note: Uplink ports must be marked as trust as shown in the Uplink Ports/Port-Channel example.
- Configure Address Resolution Protocol (ARP) Inspection
In this example, ARP inspection is configured for all wireless client VLANs.
ip arp inspection vlan 151-154,156-165
ip arp inspection validate src-mac dst-mac ip allow zeros
Note: Uplink ports must be marked as trust as shown in the Uplink Ports/Port-Channel example.
- Uplink Ports/Port-Channel (allow necessary VLANs)
In this example, Uplink Port/Port-Channel is configured.
interface Port-channel1
description Connected Dist-1
switchport trunk native vlan 4002
switchport trunk allowed vlan 151-166,4093
switchport mode trunk
ip arp inspection trust
load-interval 30
carrier-delay msec 0
ip dhcp snooping trust
interface GigabitEthernet1/1/1
description Connected Dist-1
switchport trunk native vlan 4002
switchport trunk allowed vlan 151-166,4093
switchport mode trunk
ip arp inspection trust
load-interval 30
channel-protocol pagp
channel-group 1 mode desirable
ip dhcp snooping trust
interface GigabitEthernet1/1/2
description Connected Dist-1
switchport trunk native vlan 4002
switchport trunk allowed vlan 151-166,4093
switchport mode trunk
ip arp inspection trust
load-interval 30
channel-protocol pagp
channel-group 1 mode desirable
ip dhcp snooping trust
Mobility
- Wireless Management Interface
In this example, wireless functionality is enabled and the 5760 Guest Anchor WLC is configured as the mobility peer.
interface vlan 105
description Wireless Management Interface
ip address 10.101.1.109 255.255.255.240
load-interval 30
logging event link-status
no shutdown
wireless management interface vlan 105
wireless mobility group name 3850_Branch_1
wireless mobility group member ip 10.99.2.242 public-ip 10.99.2.242 group GA-Domain-1
wireless mobility group member ip 10.99.2.243 public-ip 10.99.2.243 group GA-Domain-2
Note:You can use a Cisco 5508 WLC or an 8510 AireOS as a guest anchor controller.
Security
This example shows the configuration of Global Parameters.
aaa new-model
aaa authentication login PRIME_RADIUS_AUTH_GRP group PRIME_RADIUS_SERVER_GRP
aaa authentication dot1x PRIME_RADIUS_AUTH_GRP group PRIME_RADIUS_SERVER_GRP
aaa authorization network PRIME_RADIUS_AUTHO_GRP group PRIME_RADIUS_SERVER_GRP
aaa authorization network PRIME_CWA_MAC_FILTER group PRIME_RADIUS_SERVER_GRP
aaa accounting Identity PRIME_RADIUS_ACCT_GRP start-stop group PRIME_RADIUS_SERVER_GRP
aaa server radius dynamic-author
client 10.100.1.49 server-key 7 02050D480809
auth-type any
!
!
radius server PRIME_RADIUS_SERVER_1
address ipv4 10.100.1.49 auth-port 1812 acct-port 1813
timeout 1
key 7 121A0C041104
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 31 send nas-port-detail
!
aaa group server radius PRIME_RADIUS_SERVER_GRP
server name PRIME_RADIUS_SERVER_1
WLAN
The 802.1X WLAN configuration is shown in this example.
wlan ABCCorp-8021X 1 ABCCorp-8021X
band-select
aaa-override
nac
wifidirect policy deny
client vlan 8021X_WiFi_VLAN
ip flow monitor wireless-avc-basic input
ip flow monitor wireless-avc-basic output
accounting-list PRIME_RADIUS_ACCT_GRP
security dot1x authentication-list PRIME_RADIUS_AUTH_GRP
session-timeout 21600
wmm require
no shutdown
The Pre-Shared Key WLAN configuration is shown in this example.
wlan ABCCorp_PSK 2 ABCCorp_PSK
band-select
client vlan PSK_WiFi_VLAN
ip flow monitor wireless-avc-basic input
ip flow monitor wireless-avc-basic output
no security wpa akm dot1x
security wpa akm psk set-key ascii 8 AAPAAQeRgFGCE_dLbEOcNPP[AAAAAAMcLKMPc^TcSbIhbU\HeaSXF_AAB
service-policy output ABCCorp_PSK-PARENT-POLICY
session-timeout 7200
wifidirect policy deny
wmm require
no shutdown
The Open WLAN configuration is shown in this example.
wlan ABCCorp_OPEN 3 ABCCorp_OPEN
band-select
client vlan Open_WiFi_VLAN
ip flow monitor wireless-avc-basic input
ip flow monitor wireless-avc-basic output
no security wpano security wpa akm dot1x
no security wpa wpa2
no security wpa wpa2 ciphers aes
service-policy output ABCCorp_OPEN-PARENT-POLICY
session-timeout 1800
wifidirect policy deny
wmm require
no shutdown
Guest Solution
The CWA Guest WLAN configuration is shown in this example.
wlan ABCCorp-Guest 15 ABCCorp-Guest
aaa-override
accounting-list PRIME_RADIUS_ACCT_GRP
client vlan GUEST_VLAN
ip flow monitor wireless-avc-basic input
ip flow monitor wireless-avc-basic output
load-balance
security dot1x authentication-list PRIME_RADIUS_AUTH_GR
Pmac-filtering PRIME_CWA_MAC_FILTER
mobility anchor 10.99.2.242
mobility anchor 10.99.2.243
nac
no security wpa
no security wpa am dot1x
no security wpa wpa2
no security wpa wpa2 ciphers aes
session-timeout 3600
wmm require
no shutdown
- Mobility and Guest WLAN configuration on 5760 Guest Anchor 1
In this example, Mobility and Guest WLAN is configured on 5760 Guest Anchor 1.
wireless mobility group name GA-Domain-1
wireless mobility group member ip 10.101.1.109 public-ip 10.101.1.109 group 3850_Branch_1
wlan ABCCorp-Guest 15 ABCCorp-Guest
aaa-override
accounting-list PRIME_RADIUS_ACCT_GRP
client vlan GUEST_WiFi_VLAN
ip flow monitor wireless-avc-basic input
ip flow monitor wireless-avc-basic output
load-balance
security dot1x authentication-list PRIME_RADIUS_AUTH_GRP
mac-filtering PRIME_CWA_MAC_FILTER
mobility anchor 10.99.2.242
nac
no security wpa
no security wpa am dot1x
no security wpa wpa2
no security wpa wpa2 ciphers aes
session-timeout 3600
wmm require
no shutdown
- Redirect ACL for CWA (Central Web-Auth)
The configuration to redirect ACL for CWA is shown in this example.
Extended IP access list PRIME-CWA-REDIRECT-ACL
10 deny icmp any any
20 deny udp any eq bootps any
30 deny udp any any eq bootpc
40 deny udp any eq bootpc any
50 deny udp any any eq domain
60 deny tcp any any eq domain
70 deny ip any host 10.100.1.49
80 permit tcp any any eq www
Advanced IOS Wireless Services
- Application Visibility and Control (AVC) Configuration
This example shows the configuration of AVC.
flow exporter PRIME_FNF_COLLECTOR_1
description FLEXIBLE NETFLOW COLLECTOR
destination 10.100.1.82
dscp 46
transport udp 9991
!
!
flow monitor wireless-avc-basic
exporter PRIME_FNF_COLLECTOR_1
record wireless avc basic
This example shows the configuration of WLAN.
wlan ABCCorp-8021X 1 ABCCorp-8021X
ip flow monitor wireless-avc-basic input
ip flow monitor wireless-avc-basic output
- Egress Bandwidth Shaping for WLANs
The example shows the configuration of Egress Bandwidth shaping for WLANs.
policy-map ABCCrop-8021X-PARENT-POLICY
description PRIME-ABCCorp-8021X EGRESS PARENT POLICY
class class-default
shape average percent 40
queue-buffers ratio 0
policy-map ABCCorp-PSK-PARENT-Policy
description PRIME-ABCCorp-PSK EGRESS PARENT POLICY
class class-default
shape average percent 30
queue-buffers ratio 0
This example shows the configuration of WLAN.
wlan ABCCorp-8021X 1 ABCCorp-8021X
service-policy output ABCCorp-8021X-PARENT-POLICY
Best Practices
Best practices for wireless configuration include:
- Using the wireless client fast-ssid-change command to configure fast SSID changing.
- Using the passwd encryption on and passwd key obfuscate commands for password encryption.


 Feedback
Feedback