Introduction
This document describes how to decode a certificate with well-known online tools & their interpretation to create a certificate chain in the 9800 WLC.
Prerequisites
Requirements
Cisco recommends that you have basic knowledge of these topics:
- Cisco Catalyst 9800 Wireless LAN Controller (WLC)
- Digital Certificate, Certificate Signing Request (CSR) concept.
- OpenSSL software.
Components Used
The information in this document is based on these software and hardware versions:
- OpenSSL software in 1.1.1w version
- Windows computer
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
CSR Generation
The CSR can be generated in the controller or with OpenSSL.
To generate a CSR in the 9800 WLC navigate to Configuration > Security > PKI Management > Add Certificate > Generate Certificate Signing Request.
When a Certificate Signing Request is generated, information such as a Private Key, Common Name (CN), Country Code, State, Location, Organization and Oganization Unit is required.
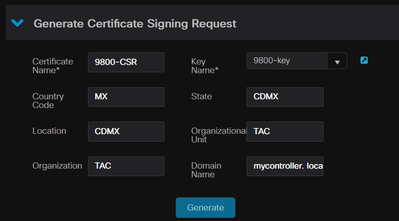 CSR Generation in WLC
CSR Generation in WLC
All the CSR information filled in the request is displayed in the decode.
OpenSSL software is the single source of truth when a certificate is decoded. It shows all the information about it.
To decode a certificate in a Windows or MacBook computer with OpenSSL installed, open the Command Prompt as Administrator and run the command openssl x509 -in <certificate.crt> -text -noout. The output is shown as console information.

Note: Not all openSSL version are supported in 9800 WLC. Suggested versions are 0.9.8 and 1.1.1w
There are other online tools to decode certificates that show the output in a more user-friendly way such as CertLogik and SSL Shopper that are not presented in this document.
Be aware that they use the same OpenSSL command already mentioned to decode the certificates.
Third Party Certificate
The CSR is sent to the Certificate Authority (CA) to have it signed and returned. Download all the certificate chain so that you can upload it to the WLC.
To understand the chain of a certificate, all the files received by CA can be decoded. Ensure they are in Base64 format.
You can receive multiple files from the CA. It depends on the number of Intermediate CA files.
To identify each file, you need to decode it.
When a signed certificate is decoded, the Issuer section is added. This refers to the CA that signed the certificate.
If you decode a CSR file which is not signed, the Issuer section does not exist because it is not signed yet.
This is an example of a multi-level authorization or chained certificate scenario:
- Root CA
- Intermediate CA Certificate
- Device certificate
Decoded Root CA
For a Root CA, since is the highest auhority of the chain, the Issuer and Subject must be the same.
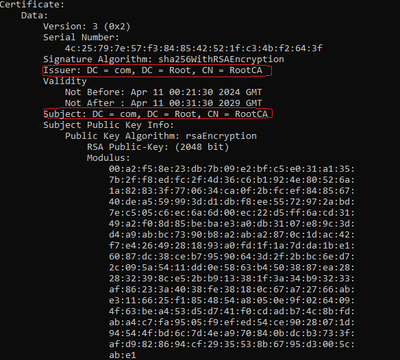 Decoded Root CA
Decoded Root CA
Decoded Intermediate CA
For Intermediate CA, since it is signed by the Root CA, the Issuer must match with the Root CA CN.
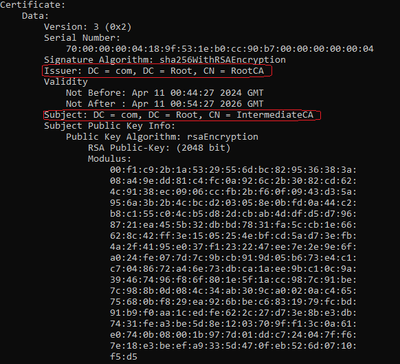 Decoded Intermediate CA
Decoded Intermediate CA
Decoded Device Certificate
For the Device Certificate, since it is signed by the Intermediate CA, the Issuer must match with the Intermediate CA CN
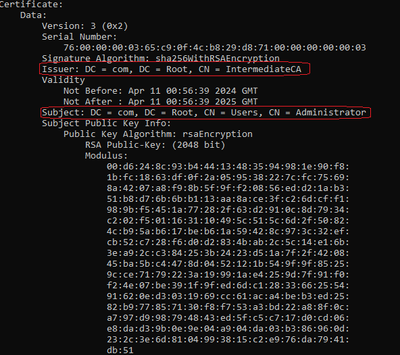 Decoded Device Certificate
Decoded Device Certificate
In a scenario where more than 1 intermediate CA is used, use the same decode process.
Once the chain order is identified, it can be uploaded to the controller.
The 9800 WLC needs the whole chain in the correct order so the certificate can operate properly.
For subsequent steps to upload a certificate to the controller, refer to Generate and Download CSR Certificates on Catalyst 9800 WLCs.
Ensure that you understand the decode process before continuing. If so, the next steps need to be completed to have a Web Auth, Web Admin, or Management certificate uploaded in a 9800 WLC.






 Feedback
Feedback