Wireless LAN Controller Mesh Network Configuration Example
Available Languages
Contents
Introduction
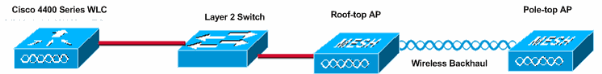
This document provides a basic configuration example for how to establish a point-to-point bridged link using the Mesh Network solution. This example uses two lightweight access point (LAPs). One LAP operates as a roof-top access point (RAP), the other LAP operates as a pole-top access point (PAP), and they are connected to a Cisco Wireless LAN (WLAN) Controller (WLC). The RAP is connected to the WLC through a Cisco Catalyst switch.
Please refer to Wireless LAN Controller Mesh Network Configuration Example for Releases 5.2 and later for WLC release 5.2 and later versions
Prerequisites
-
The WLC is configured for basic operation.
-
The WLC is configured in Layer 3 mode.
-
The switch for the WLC is configured.
Requirements
Ensure that you meet these requirements before you attempt this configuration:
-
Basic knowledge of the configuration of LAPs and Cisco WLCs
-
Basic knowledge of Lightweight AP Protocol (LWAPP).
-
Knowledge of the configuration of an external DHCP server and/or domain name server (DNS)
-
Basic configuration knowledge of Cisco switches
Components Used
The information in this document is based on these software and hardware versions:
-
Cisco 4402 Series WLC that runs firmware 3.2.150.6
-
Two (2) Cisco Aironet 1510 Series LAPs
-
Cisco Layer 2 Switch
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Background Information
Cisco Aironet 1510 Series Lightweight Outdoor Mesh AP
The Cisco Aironet 1510 Series Lightweight Outdoor Mesh AP is a wireless device designed for wireless client access and point-to-point bridging, point-to-multipoint bridging, and point-to-multipoint mesh wireless connectivity. The outdoor access point is a standalone unit that can be mounted on a wall or overhang, on a rooftop pole, or on a street light pole.
The AP1510 operates with controllers to provide centralized and scalable management, high security, and mobility. Designed to support zero-configuration deployments, the AP1510 easily and securely joins the mesh network and is available to manage and monitor the network through the controller GUI or CLI.
The AP1510 is equipped with two simultaneously operating radios: a 2.4-GHz radio used for client access and a 5-GHz radio used for data backhaul to other AP1510s. Wireless LAN client traffic passes through the backhaul radio of the AP or is relayed through other AP1510s until it reaches the controller Ethernet connection.
Roof-top Access Point (RAP)
RAPs have a wired connection to a Cisco WLC. They use the backhaul wireless interface to communicate with neighboring PAPs. RAPs are the parent node to any bridging or mesh network and connect a bridge or mesh network to the wired network. Therefore, there can only be one RAP for any bridged or mesh network segment.
Note: When you use the mesh networking solution for LAN-to-LAN bridging, do not connect a RAP directly to a Cisco WLC. A switch or router between the Cisco WLC and the RAP is required because Cisco WLCs do not forward Ethernet traffic that comes from an LWAPP-enabled port. RAPs can work in Layer 2 or Layer 3 LWAPP mode.
Pole-top Access Point (PAP)
PAPs have no wired connection to a Cisco WLC. They can be completely wireless, and support clients that communicate with other PAPs or RAPs, or they can be used to connect to peripheral devices or a wired network. The Ethernet port is disabled by default for security reasons, but you should enable it for PAPs.
Note: Cisco Aironet 1030 Remote Edge LAPs support single-hop deployments while Cisco Aironet 1500 Series Lightweight Outdoor APs support both single- and multi-hop deployments. As such, Cisco Aironet 1500 Series Lightweight Outdoor APs can be used as rooftop APs and as PAPs for one or more hops from the Cisco WLC.
Features Not Supported on Mesh Networks
These controller features are not supported on mesh networks:
-
Multi-country support
-
Load-based CAC (Mesh networks support only bandwidth-based, or static, CAC.)
-
High availability (fast heartbeat and primary discovery join timer)
-
EAP-FASTv1 and 802.1X authentication
-
EAP-FASTv1 and 802.1X authentication
-
Locally significant certificate
-
Location-based services
Access Point Startup Sequence
This list describes what happens when the RAP and PAP start up:
-
All traffic travels through the RAP and the Cisco WLC before it is sent to the LAN.
-
When the RAP comes up, the PAPs automatically connect to it.
-
The connected link uses a shared secret to generate a key that is used to provide Advanced Encryption Standard (AES) for the link.
-
Once the remote PAP connects to the RAP, the mesh APs can pass data traffic.
-
Users can change the shared secret or configure the mesh APs using the Cisco command line interface (CLI), the Cisco web user interface of the controller, or the Cisco Wireless Control System (Cisco WCS). Cisco recommends that you modify the shared secret.
Configure
Complete these steps in order to configure the WLC and the APs for point-to-point bridging.
Enable Zero Touch Configuration (Enabled by Default)
GUI Configuration
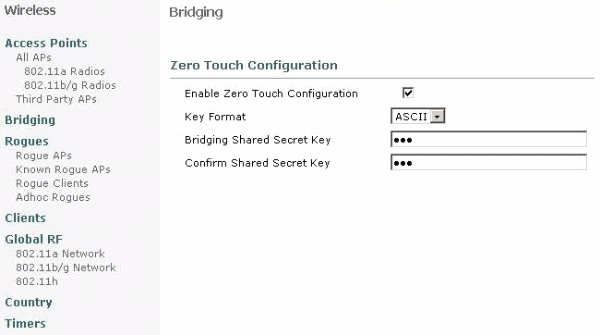
Enable Zero Touch Configuration enables the APs to get the shared secret key from the controller when it registers with the WLC. If you uncheck the this box, the controller does not provide the shared secret key, and the APs use a default pre-shared key for secure communication. The default value is enabled (or checked). Complete these steps from the WLC GUI:
Note: There is no provision for Zero-Touch configuration in WLC version 4.1 and later.
-
Choose Wireless > Bridging and click Enable Zero Touch Configuration.
-
Select the Key Format.
-
Enter the Bridging Shared Secret Key.
-
Enter the Bridging Shared Secret Key again in the Confirm Shared Secret Key.
CLI Configuration
Complete these steps from the CLI:
-
Issue the config network zero-config enable command in order to enable the zero touch configuration.
(Cisco Controller) >config network zero-config enable
-
Issue the config network bridging-shared-secret <string> command in order to add the bridging shared secret key.
(Cisco Controller) >config network bridging-shared-secret Cisco
Add the MIC to the AP Authorization List
The next step is to add the AP to the authorization list on the WLC. In order to do this, choose Security > AP Policies, enter the AP MAC address under Add AP to Authorization List and click Add.
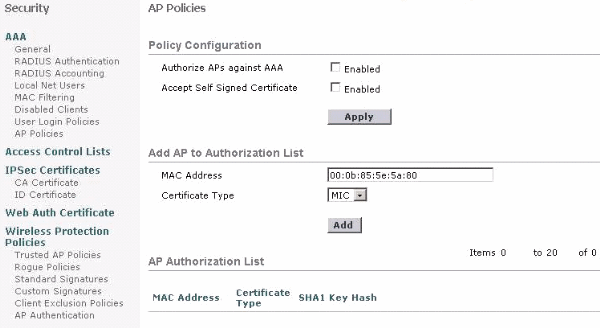
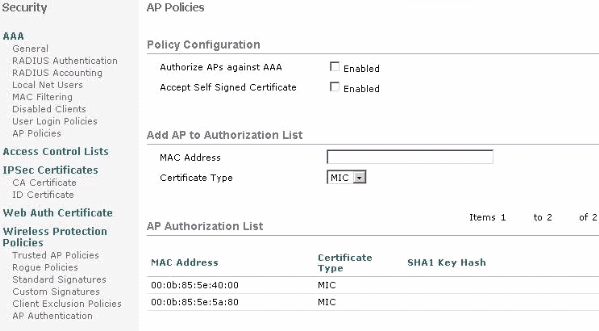
In this example, both APs (the RAP and the PAP) are added to the AP authorization list on the controller.
CLI Configuration
Issue the config auth-list add mic <AP mac> command in order to add the MIC to the authorization list.
(Cisco Controller) >config auth-list add mic 00:0b:85:5e:40:00 (Cisco Controller) >config auth-list add mic 00:0b:85:5e:5a:80
Configuration
This document uses this configuration:
| Cisco WLC 4402 |
|---|
(Cisco Controller) >show run-config
Press Enter to continue...
System Inventory
Switch Description............................... Cisco Controller
Machine Model.................................... WLC4402-12
Serial Number.................................... FLS0943H005
Burned-in MAC Address............................ 00:0B:85:40:CF:A0
Crypto Accelerator 1............................. Absent
Crypto Accelerator 2............................. Absent
Power Supply 1................................... Absent
Power Supply 2................................... Present, OK
Press Enter to continue Or <Ctl Z> to abort
System Information
Manufacturer's Name.............................. Cisco Systems, Inc
Product Name..................................... Cisco Controller
Product Version.................................. 3.2.150.6
RTOS Version..................................... 3.2.150.6
Bootloader Version............................... 3.2.150.6
Build Type....................................... DATA + WPS
System Name...................................... lab120wlc4402ip100
System Location..................................
System Contact...................................
System ObjectID.................................. 1.3.6.1.4.1.14179.1.1.4.3
IP Address....................................... 192.168.120.100
System Up Time................................... 0 days 1 hrs 4 mins 6 secs
Configured Country............................... United States
Operating Environment............................ Commercial (0 to 40 C)
Internal Temp Alarm Limits....................... 0 to 65 C
Internal Temperature............................. +42 C
State of 802.11b Network......................... Disabled
State of 802.11a Network......................... Disabled
Number of WLANs.................................. 1
3rd Party Access Point Support................... Disabled
Number of Active Clients......................... 0
Press Enter to continue Or <Ctl Z> to abort
Switch Configuration
802.3x Flow Control Mode......................... Disable
Current LWAPP Transport Mode..................... Layer 3
LWAPP Transport Mode after next switch reboot.... Layer 3
FIPS prerequisite features....................... Disabled
Press Enter to continue Or <Ctl Z> to abort
Network Information
RF-Network Name............................. airespacerf
Web Mode.................................... Enable
Secure Web Mode............................. Enable
Secure Shell (ssh).......................... Enable
Telnet...................................... Enable
Ethernet Multicast Mode..................... Disable Mode: Ucast
User Idle Timeout........................... 300 seconds
ARP Idle Timeout............................ 300 seconds
ARP Unicast Mode............................ Disabled
Cisco AP Default Master..................... Disable
Mgmt Via Wireless Interface................. Enable
Bridge AP Zero Config....................... Enable
Bridge Shared Secret........................ youshouldsetme
Allow Old Bridging Aps To Authenticate...... Disable
Over The Air Provisioning of AP's........... Disable
Mobile Peer to Peer Blocking................ Disable
Apple Talk ................................. Disable
AP Fallback ................................ Enable
Web Auth Redirect Ports .................... 80
Fast SSID Change ........................... Disabled
Press Enter to continue Or <Ctl Z> to abort
Port Summary
STP Admin Physical Physical Link Link Mcast
Pr Type Stat Mode Mode Status Status Trap Appliance POE
-- ------- ---- ------- ---------- ---------- ------ ------- --------- -------
1 Normal Forw Enable Auto 1000 Full Up Enable Enable N/A
2 Normal Forw Enable Auto 1000 Full Up Enable Enable N/A
Mobility Configuration
Mobility Protocol Port........................... 16666
Mobility Security Mode........................... Disabled
Default Mobility Domain.......................... airespacerf
Mobility Group members configured................ 3
Switches configured in the Mobility Group
MAC Address IP Address Group Name
00:0b:85:33:a8:40 192.168.5.70 <local>
00:0b:85:40:cf:a0 192.168.120.100 <local>
00:0b:85:43:8c:80 192.168.5.40 airespacerf
Interface Configuration
Interface Name................................... ap-manager
IP Address....................................... 192.168.120.101
IP Netmask....................................... 255.255.255.0
IP Gateway....................................... 192.168.120.1
VLAN............................................. untagged
Active Physical Port............................. 1
Primary Physical Port............................ 1
Backup Physical Port............................. Unconfigured
Primary DHCP Server.............................. 192.168.1.20
Secondary DHCP Server............................ Unconfigured
ACL.............................................. Unconfigured
AP Manager....................................... Yes
Interface Name................................... management
MAC Address...................................... 00:0b:85:40:cf:a0
IP Address....................................... 192.168.120.100
IP Netmask....................................... 255.255.255.0
IP Gateway....................................... 192.168.120.1
VLAN............................................. untagged
Active Physical Port............................. 1
Primary Physical Port............................ 1
Backup Physical Port............................. Unconfigured
Primary DHCP Server.............................. 192.168.1.20
Secondary DHCP Server............................ Unconfigured
ACL.............................................. Unconfigured
AP Manager....................................... No
Interface Name................................... service-port
MAC Address...................................... 00:0b:85:40:cf:a1
IP Address....................................... 192.168.250.100
IP Netmask....................................... 255.255.255.0
DHCP Protocol.................................... Disabled
AP Manager....................................... No
Interface Name................................... virtual
IP Address....................................... 1.1.1.1
Virtual DNS Host Name............................ Disabled
AP Manager....................................... No
WLAN Configuration
WLAN Identifier.................................. 1
Network Name (SSID).............................. lab120wlc4402ip100
Status........................................... Enabled
MAC Filtering.................................... Enabled
Broadcast SSID................................... Enabled
AAA Policy Override.............................. Disabled
Number of Active Clients......................... 0
Exclusionlist Timeout............................ 60 seconds
Session Timeout.................................. 1800 seconds
Interface........................................ management
WLAN ACL......................................... unconfigured
DHCP Server...................................... Default
Quality of Service............................... Silver (best effort)
WMM.............................................. Disabled
802.11e.......................................... Disabled
Dot11-Phone Mode (7920).......................... Disabled
Wired Protocol................................... None
IPv6 Support..................................... Disabled
Radio Policy..................................... All
Radius Servers
Authentication................................ 192.168.1.20 1812
Security
802.11 Authentication:........................ Open System
Static WEP Keys............................... Enabled
Key Index:...................................... 1
Encryption:..................................... 104-bit WEP
802.1X........................................ Disabled
Wi-Fi Protected Access (WPA1)................. Disabled
Wi-Fi Protected Access v2 (WPA2).............. Disabled
IP Security................................... Disabled
IP Security Passthru.......................... Disabled
L2TP.......................................... Disabled
Web Based Authentication...................... Disabled
Web-Passthrough............................... Disabled
Auto Anchor................................... Disabled
Cranite Passthru.............................. Disabled
Fortress Passthru............................. Disabled
RADIUS Configuration
Vendor Id Backward Compatibility................. Disabled
Credentials Caching.............................. Disabled
Call Station Id Type............................. IP Address
Administrative Authentication via RADIUS......... Enabled
Keywrap.......................................... Disabled
Load Balancing Info
Aggressive Load Balancing........................ Enabled
Aggressive Load Balancing Window................. 0 clients
Signature Policy
Signature Processing........................... Enabled
Spanning Tree Switch Configuration
STP Specification...................... IEEE 802.1D
STP Base MAC Address................... 00:0B:85:40:CF:A0
Spanning Tree Algorithm................ Disable
STP Bridge Priority.................... 32768
STP Bridge Max. Age (seconds).......... 20
STP Bridge Hello Time (seconds)........ 2
STP Bridge Forward Delay (seconds)..... 15
Spanning Tree Port Configuration
STP Port ID................................. 8001
STP Port State.............................. Forwarding
STP Port Administrative Mode................ 802.1D
STP Port Priority........................... 128
STP Port Path Cost.......................... 4
STP Port Path Cost Mode..................... Auto
STP Port ID................................. 8002
STP Port State.............................. Forwarding
STP Port Administrative Mode................ 802.1D
STP Port Priority........................... 128
STP Port Path Cost.......................... 4
STP Port Path Cost Mode..................... Auto |
Configure Bridging Parameters for the APs
This section provides instructions on how to configure the role of the AP in the mesh network and related bridging parameters. You can configure these parameters using either the GUI or the CLI.
-
Click Wireless and then All APs under Access Points. The All APs page appears.
-
Click the Detail link for your AP1510 in order to access the All APs > Details page
On this page, the AP Mode under General is automatically set to Bridge for APs that have bridge functionality, such as the AP1510. This page also shows this information under Bridging Information. Under Bridging Information, choose one of these options in order to specify the role of this AP in the mesh network:
-
MeshAP—Choose this option if the AP1510 has a wireless connection to the controller.
-
RootAP—Choose this option if the AP1510 has a wired connection to the controller.
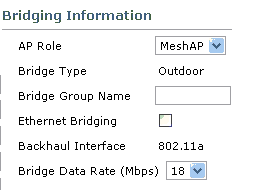
Verify
Use this section to confirm that your configuration works properly.
After the APs register with the WLC, you can view them under the Wireless tab at the top of the GUI of the WLC:
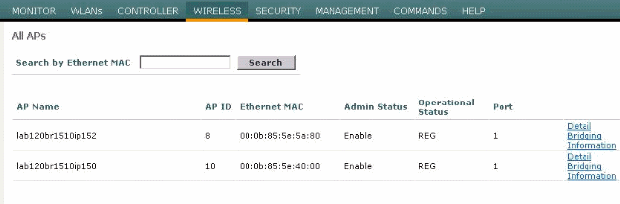
On the CLI, you can use the show ap summary command in order to verify that the APs registered with the WLC:
(Cisco Controller) >show ap summary AP Name Slots AP Model Ethernet MAC Location Port ------------------ ----- ---------- ----------------- ---------------- ---- lab120br1510ip152 2 OAP1500 00:0b:85:5e:5a:80 default_location 1 lab120br1510ip150 2 OAP1500 00:0b:85:5e:40:00 default_location 1 (Cisco Controller) >
Click Bridging Details in the GUI in order to verify the role of the AP:
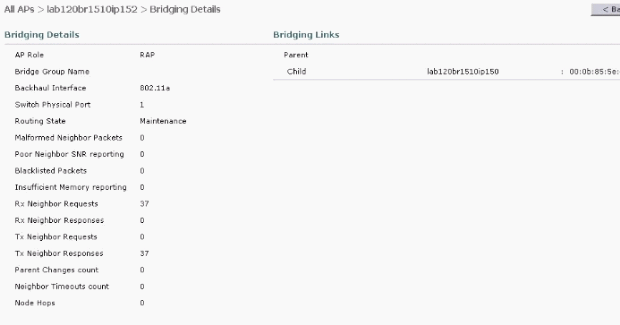
On the CLI, you can use the show mesh path <Cisco AP> and show mesh neigh <Cisco AP> commands in order to verify that the APs registered with the WLC:
(Cisco Controller) >show mesh path lab120br1510ip152 00:0B:85:5E:5A:80 is RAP (Cisco Controller) >show mesh neigh lab120br1510ip152 AP MAC : 00:0B:85:5E:40:00 FLAGS : 160 CHILD worstDv 255, Ant 0, channel 0, biters 0, ppiters 10 Numroutes 0, snr 0, snrUp 0, snrDown 26, linkSnr 0 adjustedEase 0, unadjustedEase 0 txParent 0, rxParent 0 poorSnr 0 lastUpdate 1150103792 (Mon Jun 12 09:16:32 2006) parentChange 0 Per antenna smoothed snr values: 0 0 0 0 Vector through 00:0B:85:5E:40:00 (Cisco Controller) >
Troubleshoot
Mesh APs doesn't associate to the WLC is one of the most common issues seen in the Mesh deployment. Complete these checks:
-
Check that the MAC Address of the access point is added in the Mac Filter list in the WLC. This can be seen under Security > Mac Filtering.
-
Check the shared secret between the RAP and the MAP. You can see this message in the WLC when there is a mismatch in the key.
" LWAPP Join-Request AUTH_STRING_PAYLOAD, invalid BRIDGE key hash AP 00:0b:85:68:c1:d0"Note: Always try to use the Enable Zero Touch Configuration option if available for a version. This automatically configures the key for the Mesh APs and avoids misconfigurations.
-
RAPs do not forward any broadcast messages on their Radio interface. So configure the DHCP server to send IP addresses through unicast so that MAP can get their IP addresses forwarded by RAP. Otherwise use a static IP for the MAP.
-
Either leave the Bridge Group Name at default values or make sure that Bridge Group Names are configured exactly the same on MAPs and the corresponding RAP.
These are issues that are specific to Mesh Access Points. For connectivity issues that are common between the WLC and an access point, refer to Troubleshoot a Lightweight Access Point Not Joining a Wireless LAN Controller.
Troubleshooting Commands
Note: Refer to Important Information on Debug Commands before you use debug commands.
You can use these debug commands to troubleshoot the WLC:
-
debug pem state enable —Used to configure the access policy manager debug options.
-
debug pem events enable —Used to configure the access policy manager debug options.
-
debug dhcp message enable —Shows the debug of DHCP messages that are exchanged to and from the DHCP server.
-
debug dhcp packet enable —Shows the debug of DHCP packet details that are sent to and from the DHCP server.
Some additional debug commands that you can use to troubleshoot are:
-
debug lwapp errors enable—Shows the debug of LWAPP errors.
-
debug pm pki enable—Shows the debug of certificate messages that are passed between the AP and the WLC.
This debug lwapp events enable WLC command output shows that the LAP gets registered to the WLC:
(Cisco Controller) >debug lwapp events enable Mon Jun 12 09:04:57 2006: 00:0b:85:5e:40:00 Received LWAPP JOIN REQUEST from AP 00:0b:85:5e:40:00 to 06:0a:10:10:00:00 on port '1' Mon Jun 12 09:04:57 2006: 00:0b:85:5e:40:00 AP lab120br1510ip150: txNonce 00:0B:85:40:CF:A0 rxNonce 00:0B:85:5E:40:00 Mon Jun 12 09:04:57 2006: 00:0b:85:5e:40:00 LWAPP Join-Request MTU path from AP 00:0b:85:5e:40:00 is 1500, remote debug mode is 0 Mon Jun 12 09:04:58 2006: 00:0b:85:5e:40:00 Successfully added NPU Entry for AP 00:0b:85:5e:40:00 (index 1) Switch IP: 192.168.120.101, Switch Port: 12223, intIfNum 1, vlanId 0 AP IP: 192.168.120.150, AP Port: 58368, next hop MAC: 00:0b:85:5e:40:00 Mon Jun 12 09:04:58 2006: 00:0b:85:5e:40:00 Successfully transmission of LWAPP Join-Reply to AP 00:0b:85:5e:40:00 Mon Jun 12 09:04:58 2006: 00:0b:85:5e:40:00 Register LWAPP event for AP 00:0b:85:5e:40:00 slot 0 Mon Jun 12 09:04:58 2006: 00:0b:85:5e:40:00 Register LWAPP event for AP 00:0b:85:5e:40:00 slot 1 Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 Received LWAPP CONFIGURE REQUEST from AP 00:0b:85:5e:40:00 to 00:0b:85:40:cf:a3 Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 Updating IP info for AP 00:0b:85:5e:40:00 -- static 1, 192.168.120.150/255.255.255.0, gtw 192.168.120.1 Mon Jun 12 09:04:59 2006: spamVerifyRegDomain RegDomain set for slot 0 code 0 regstring -A regDfromCb -A Mon Jun 12 09:04:59 2006: spamVerifyRegDomain RegDomain set for slot 1 code 0 regstring -A regDfromCb -A Mon Jun 12 09:04:59 2006: spamEncodeDomainSecretPayload:Send domain secret airespacerf<65,4d,c3,6f,88,35,cd,4d,3b,2b,bd,95,5b,42,6d,ac,b6,ab,f7,3d> to AP 00:0b:85:5e:40:00 Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 Successfully transmission of LWAPP Config-Message to AP 00:0b:85:5e:40:00 Mon Jun 12 09:04:59 2006: Running spamEncodeCreateVapPayload for SSID 'lab120wlc4402ip100' Mon Jun 12 09:04:59 2006: Running spamEncodeCreateVapPayload for SSID 'lab120wlc4402ip100' Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 AP 00:0b:85:5e:40:00 associated. Last AP failure was due to Link Failure, reason: STATISTICS_INFO_RES Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 Received LWAPP CHANGE_STATE_EVENT from AP 00:0b:85:5e:40:00 Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 Successfully transmission of LWAPP Change-State-Event Response to AP 00:0b:85:5e:40:00 Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 apfSpamProcessStateChangeInSpamContext: Down LWAPP event for AP 00:0b:85:5e:40:00 slot 0 Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 Received LWAPP Down event for AP 00:0b:85:5e:40:00 slot 0! Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 Received LWAPP CONFIGURE COMMAND RES from AP 00:0b:85:5e:40:00 Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 Received LWAPP CHANGE_STATE_EVENT from AP 00:0b:85:5e:40:00 Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 Successfully transmission of LWAPP Change-State-Event Response to AP 00:0b:85:5e:40:00 Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 apfSpamProcessStateChangeInSpamContext: Down LWAPP event for AP 00:0b:85:5e:40:00 slot 1 Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 Received LWAPP Down event for AP 00:0b:85:5e:40:00 slot 1! Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 Received LWAPP CONFIGURE COMMAND RES from AP 00:0b:85:5e:40:00 Mon Jun 12 09:04:59 2006: 00:0b:85:5e:40:00 Received LWAPP CONFIGURE COMMAND RES from AP 00:0b:85:5e:40:00
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
01-Dec-2013 |
Initial Release |

 Feedback
Feedback