Introduction
This document describes how packet captures can be taken from the Jabber Guest Server.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- The Jabber Guest must have access to Internet to download the package.
- WinSCP software installed on the PC to collect the captures.
Components Used
The information in this document is based on these software and hardware versions:
- Jabber Guest versions 10.5 and 10.6
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Problem: How Packet Captures can be taken from Jabber Guest Server?
Solution
Step 1.
The Jabber Guest server must have access to Internet, for it to download the package from the Internet. In case a web proxy is used, follow the procedure to allow CentOS on Jabber Guest to use the web proxy to download the package.
Refer to the link https://www.centos.org/docs/5/html/yum/sn-yum-proxy-server.html to follow the procedure.
After making sure that the Jabber Guest Server can download the package, proceed to Step 2.
Step 2.
Log in to the Jabber Guest server using Secure Socket Host (SSH) root credentials and run the yum search tcpdump command to find the latest version of tcpdump.

Step 3.
Run the yum install tcpdump command to install the tcpdump package on the Jabber Guest Server.
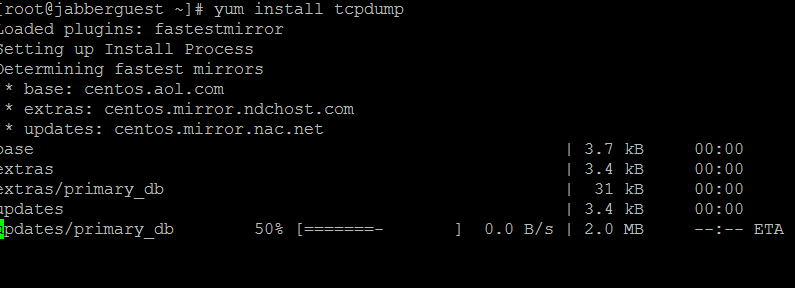
Step 4.
You are sent through several prompts. Enter y on every component to verify each prompt.
Step 5.
Tcpdump is now available again for packet captures from the Jabber Guest Server.
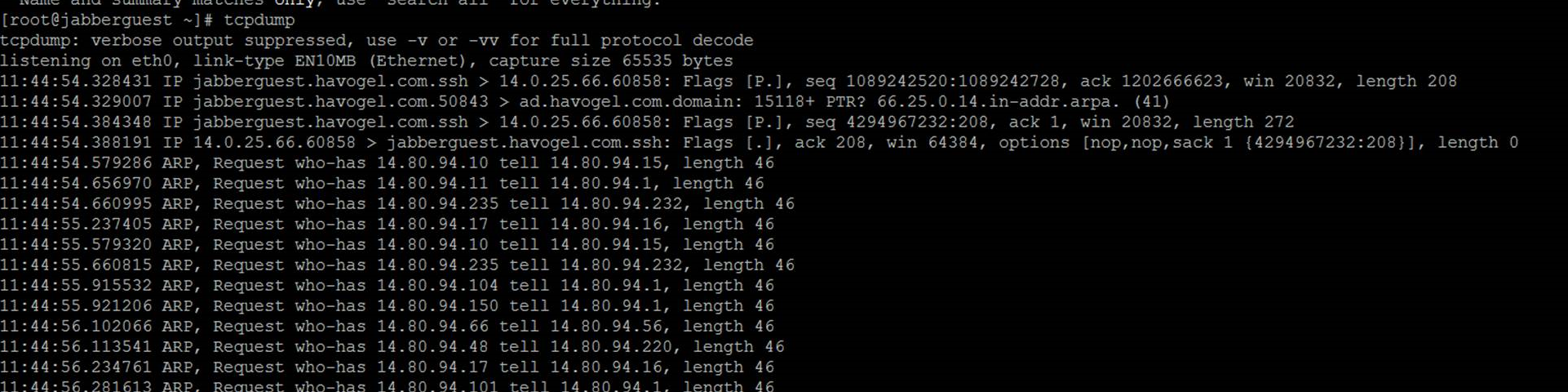
You can run the tcpdump and write the capture on a .pcap file using the tcpdump -w TAC.pcap command.
Step 6.
You can collect the files from the Jabber Guest Server with WinSCP. An enhancement on the product to take the packet captures from the web GUI is opened and is tracked under:
https://tools.cisco.com/bugsearch/bug/CSCuu99856/?reffering_site=dumpcr
