Configure and Onboard APs on Non-SDA EWC-Switch (C9800-SW)
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Introduction
This document describes the process to onboard and provision an Access Point (AP) with an Embedded Wireless Controller on a Catalyst 9000 (Catalyst 9K) switch (EWC-Switch) in a non-SDA deployments (there is no CIsco DNA Center in use).
Prerequisites
Requirements
You are required to execute these prerequisites:
- Install the Wireless Sub-Package on the Catalyst 9K switch that will act as the Wireless LAN Controller (WLC).
- Ensure the Loopback interface is configured so it will be configured as the Wireless Management Interface (WMI).
- Ensure the GUI access to the Catalyst 9K switch is enabled as configuration via the GUI is recommended.
Note: The EWC-Switch on non-SDA deployments is only supported in 17.3.X releases.
Components Used
The information in this document is based on these software and hardware versions:
- C9300-24P switch, Cisco IOS® XE Version 17.3.4
- Wireless Sub-Package for Version 17.3.4
- C9120-AX AP
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Configure
Network Diagram
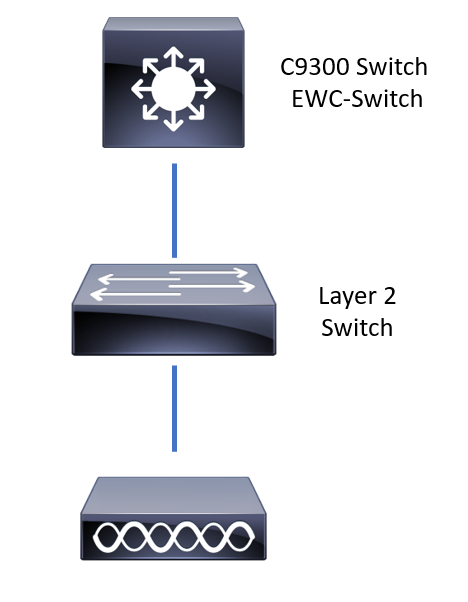
APs are allowed to be directly connected to EWC-Switch, but it is not a requirement. You are recommended to use an access switch to plug in APs to allow for high availability (HA) failover in case the active EWC-Switch goes down.
Configurations
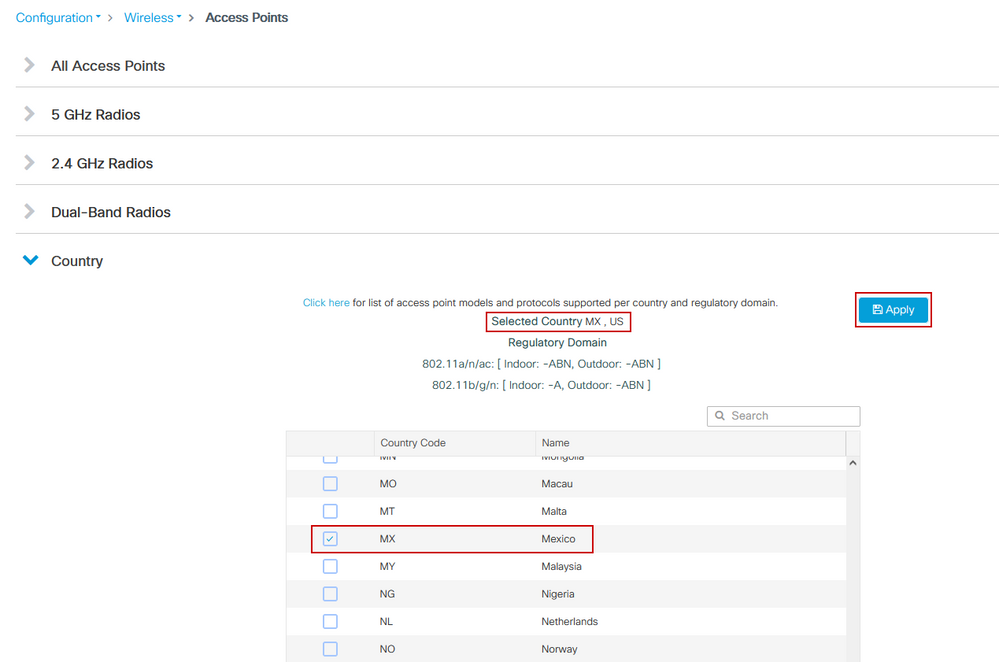
Step 1. Configure the country code for geographical locations where APs will be deployed. This is mandatory in order to enable APs to register and ensures compliance with regulatory domain guidelines for the country in which they are deployed. From the GUI, navigate to Configuration > Wireless > Access Points and click the Country tab. Choose all applicable Country Code(s) to match regulatory domains of APs.
Note: In versions from 17.3.1 to 17.3.3, EWC-Switch GUI lists the country codes but does not apply any selections until one country code is added via the CLI as documented in Cisco bug ID CSCvw20478. After one country code is configured, you can add more country codes via GUI.
CLI configuration (17.3.1 to 17.3.3):
9300-1#configure terminal
9300-1(config)#ap dot11 5ghz shutdown
Disabling the 802.11a network may strand mesh APs.
Are you sure you want to continue? (y/n)[y]: y
9300-1(config)#ap dot11 24ghz shutdown
Disabling the 802.11b network may strand mesh APs.
Are you sure you want to continue? (y/n)[y]: y
9300-1(config)#wireless country MX
9300-1(config)#no ap dot11 5ghz shutdown
9300-1(config)#no ap dot11 24ghz shutdown
Step 2. Enable wireless controller functionality and configure the VLAN that the APs will reside in. Navigate to Configuration > Embedded Wireless Setup, slide Embedded Wireless Setup to Enabled and under Location Configuration, click + Add.
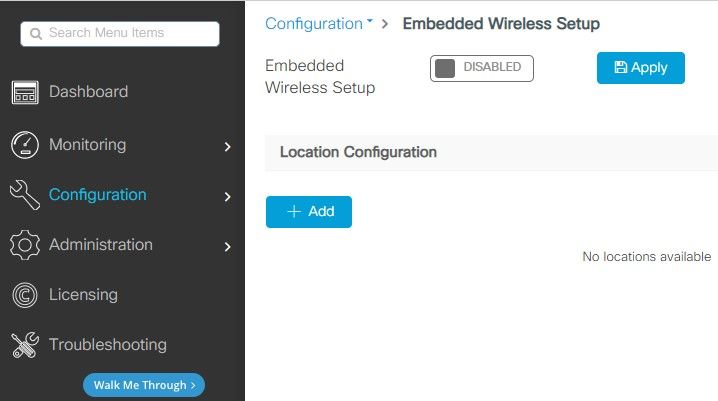
When Embedded Wireless Setup is enabled, these commands are pushed to the CLI. These CLIs enable lisp fabric on the Catalyst 9K switch so it will serve as control-plane/map server node, wireless controller with loopback as the WMI and WLC to control-plane mapping to allow the APs and the clients to be onboarded.
9300-1(config)#router lisp
9300-1(config-router-lisp)# locator-table default
9300-1(config-router-lisp)# locator-set rloc_ewlc
9300-1(config-router-lisp-locator-set)# IPv4-interface Loopback0
9300-1(config-router-lisp-locator-set)# auto-discover-rlocs
9300-1(config-router-lisp-locator-set)# exit-locator-set
9300-1(config-router-lisp)# locator-set WLC
9300-1(config-router-lisp-locator-set)# <Loopback0 IP address>
9300-1(config-router-lisp-locator-set)# exit-locator-set
9300-1(config-router-lisp)# service ipv4
9300-1(config-lisp-srv-ipv4)# encapsulation vxlan
9300-1(config-lisp-srv-ipv4)# itr map-resolver <Loopback0 IP address>
9300-1(config-lisp-srv-ipv4)# etr map-server <Loopback0 IP address> key <internal key>
9300-1(config-lisp-srv-ipv4)# etr map-server <Loopback0 IP address> proxy-reply
9300-1(config-lisp-srv-ipv4)# etr
9300-1(config-lisp-srv-ipv4)# sgt
9300-1(config-lisp-srv-ipv4)# no map-cache away-eids send-map-request
9300-1(config-lisp-srv-ipv4)# proxy-etr
9300-1(config-lisp-srv-ipv4)# proxy-itr <Loopback0 IP address>
9300-1(config-lisp-srv-ipv4)# map-server
9300-1(config-lisp-srv-ipv4)# map-resolver
9300-1(config-lisp-srv-ipv4)# exit-service-ipv4
9300-1(config-router-lisp)# service ethernet
9300-1(config-lisp-srv-eth)# itr map-resolver <Loopback0 IP address>
9300-1(config-lisp-srv-eth)# itr
9300-1(config-lisp-srv-eth)# etr map-server <Loopback0 IP address> key <internal key>
9300-1(config-lisp-srv-eth)# etr map-server <Loopback0 IP address> proxy-reply
9300-1(config-lisp-srv-eth)# etr
9300-1(config-lisp-srv-eth)# map-server
9300-1(config-lisp-srv-eth)# map-resolver
9300-1(config-lisp-srv-eth)# exit-service-ethernet
9300-1(config-router-lisp)# ipv4 source-locator Loopback0
9300-1(config-router-lisp)# map-server session passive-open WLC
9300-1(config-router-lisp)# exit
9300-1(config)# interface LISP0
9300-1(config-if)# exit
9300-1(config)# router lisp
9300-1(config-router-lisp)# site site_uci
9300-1(config-router-lisp-site)# description map-server configured from Wireless LAN Controller
9300-1(config-router-lisp-site)# authentication-key <internal key>
9300-1(config-router-lisp-site)# exit-site
9300-1(config-router-lisp)# exit-router-lisp
9300-1(config)# ip dhcp relay information option
9300-1(config)# wireless fabric
9300-1(config)# wireless management interface Loopback0
9300-1(config-mgmt-interface)# exit
9300-1(config)# wireless fabric control-plane default-control-plane
9300-1(config-wireless-cp)# ip address <Loopback0 IP address> key 0 <internal key>
9300-1(config-wireless-cp)# exit
Step 3. In the pop-up generated post Step 2, within the General tab, enter the Location Name and AP Onboarding details like VLAN and Subnet Mask. By default, the VLAN field is pre-populated with 2045. A different VLAN ID is allowed to be used but the VLAN ID must be between 2045 and 4094 and it must be independent from client traffic (no wired, or wireless clients are allowed to use this VLAN). Once the details are complete, click Apply
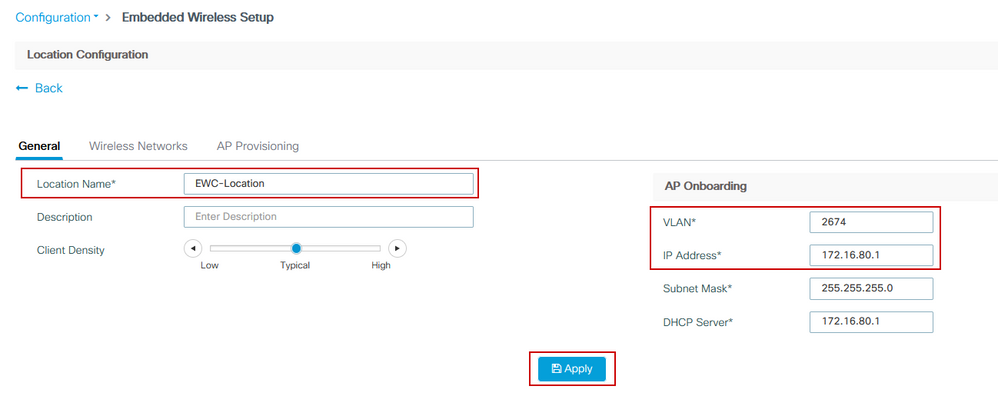
This creates the VLAN for the APs, an SVI for that AP VLAN (default gateway for the APs), AP location, Policy and RF tags, and L2 and L3 Virtual Network Identifiers (VNIDs). These are the commands seen in the CLI as a result of Step 3.
9300-1(config)# interface LISP0.4097
9300-1(config-subif)# router lisp
9300-1(config-router-lisp)# locator-set rloc_ewlc
9300-1(config-router-lisp-locator-set)# exit-locator-set
9300-1(config-router-lisp)# instance-id 4097
9300-1(config-lisp-inst)# remote-rloc-probe on-route-change
9300-1(config-lisp-inst)# dynamic-eid APONBOARDING_0_2674_4097_8188
9300-1(config-lisp-inst-dyn-eid)# database-mapping 172.16.80.0/24 locator-set rloc_ewlc
9300-1(config-lisp-inst-dyn-eid)# exit-dynamic-eid
9300-1(config-lisp-inst)# service ipv4
9300-1(config-lisp-inst-srv-ipv4)# eid-table default
9300-1(config-lisp-inst-srv-ipv4)# map-cache 172.16.80.0/24 map-request
9300-1(config-lisp-inst-srv-ipv4)# route-export site-registrations
9300-1(config-lisp-inst-srv-ipv4)# distance site-registrations 250
9300-1(config-lisp-inst-srv-ipv4)# map-cache site-registration
9300-1(config-lisp-inst-srv-ipv4)# exit-service-ipv4
9300-1(config-lisp-inst)# exit-instance-id
9300-1(config-router-lisp)# instance-id 8188
9300-1(config-lisp-inst)# remote-rloc-probe on-route-change
9300-1(config-lisp-inst)# service ethernet
9300-1(config-lisp-inst-srv-eth)# eid-table vlan 2674
9300-1(config-lisp-inst-srv-eth)# database-mapping mac locator-set rloc_ewlc
9300-1(config-lisp-inst-srv-eth)# exit-service-ethernet
9300-1(config-lisp-inst)# exit-instance-id
9300-1(config-router-lisp)# site site_uci
9300-1(config-router-lisp-site)# eid-record instance-id 4097 172.16.80.0/24 accept-more-specifics
9300-1(config-router-lisp-site)# eid-record instance-id 8188 any-mac
9300-1(config-router-lisp-site)# exit-site
9300-1(config-router-lisp)# exit
9300-1(config)# vlan 2674
9300-1(config-vlan)# name AP_VLAN2674
9300-1(config-vlan)# exit
9300-1(config)# interface Vlan2674
9300-1(config-if)# description APONBOARDING_0_2674_4097_8188
9300-1(config-if)# mac-address 0000.0C9F.FAD1
9300-1(config-if)# ip address 172.16.80.1 255.255.255.0
9300-1(config-if)# ip helper-address 172.16.80.1
9300-1(config-if)# no ip redirects
9300-1(config-if)# ip route-cache same-interface
9300-1(config-if)# no lisp mobility liveness test
9300-1(config-if)# ip directed-broadcast
9300-1(config-if)# lisp mobility APONBOARDING_0_2674_4097_8188
9300-1(config-if)#exit
9300-1(config)# wireless fabric name APONBOARDING_0_2674_4097_8188 l2-vnid 8188 l3-vnid 4097 ip 172.16.80.0 255.255.255.
Step 4. Configure the Catalyst 9K switch to also act as DHCP server for the AP VLAN and create corresponding DHCP pools. Navigate to Administration > DHCP Pools and click + Add. Set a pool name and network parameters, ensure that default gateway is set to the SVI IP address; otherwise the APs partially join the controller.
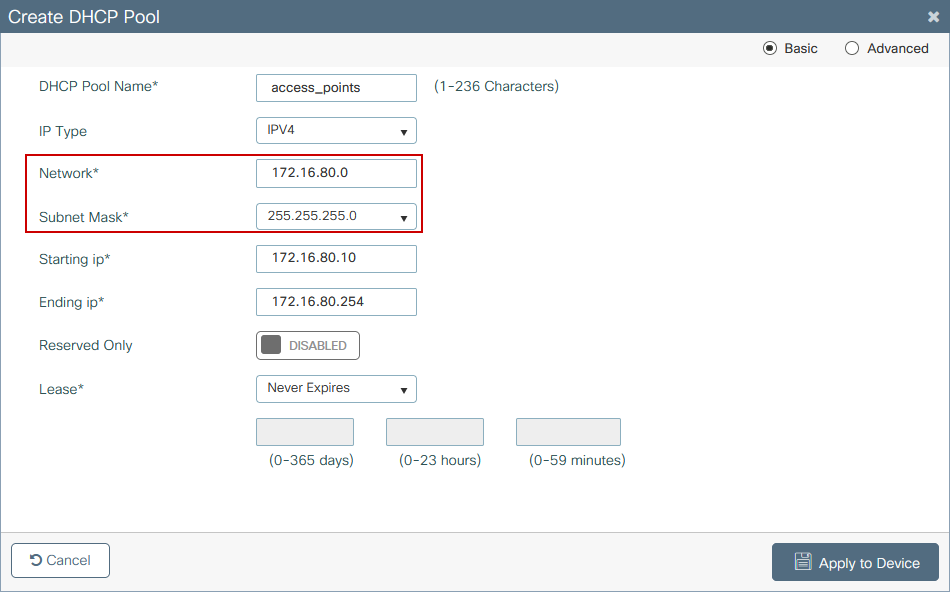
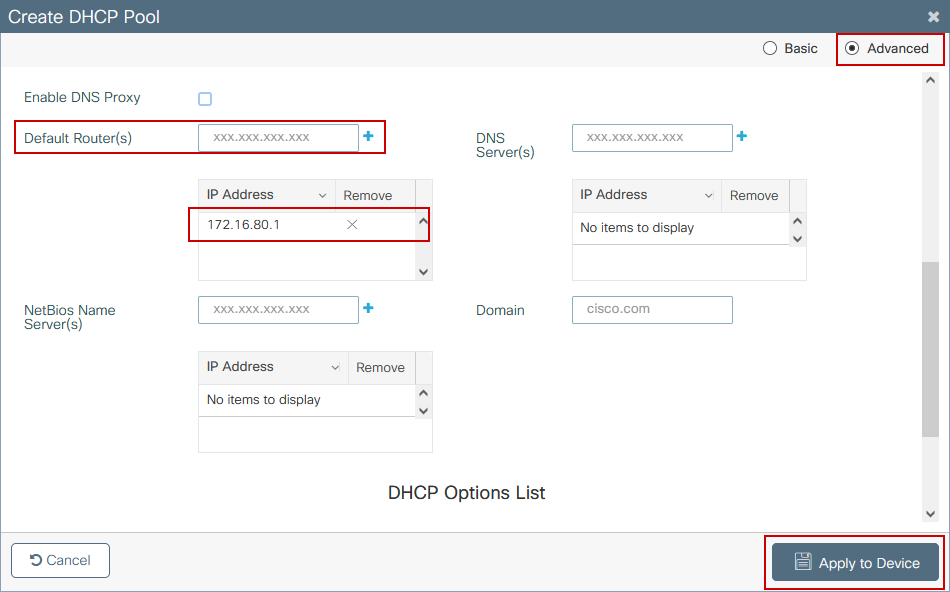
CLI configuration:
9300-1#configure terminal
9300-1(config)#ip dhcp excluded-address 172.16.80.0 172.16.80.9
9300-1(config)#ip dhcp pool <DHCP pool name>
9300-1(dhcp-config)#network 172.16.80.0 255.255.255.0
9300-1(dhcp-config)#default-router 172.16.80.1
Step 5. Configure switchport in access mode and assign it to the previously defined VLAN.
3850-1(config)#interface <interface to AP>
3850-1(config-if)#switchport mode access
3850-1(config-if)#switchport access vlan <AP vlan ID>
Step 6. Navigate to Configuration > Embedded Wireless Setup and choose the site created in Step 3. Click the AP Provisioning tab and from the list of Available APs, choose the APs that need to be provisioned and click the blue arrow icon to change it to Associated AP list. Once all APs of interest have been assigned to the specific location, click Apply.
Caution: The EWC-Switch allows for manual tag creation and assignment; however this is not a supported configuration and the only supported tag assignment is by Location Assignment. Only one location is supported on the EWC-Switch, so all of the APs must be in the same subnet and assigned to the same location.
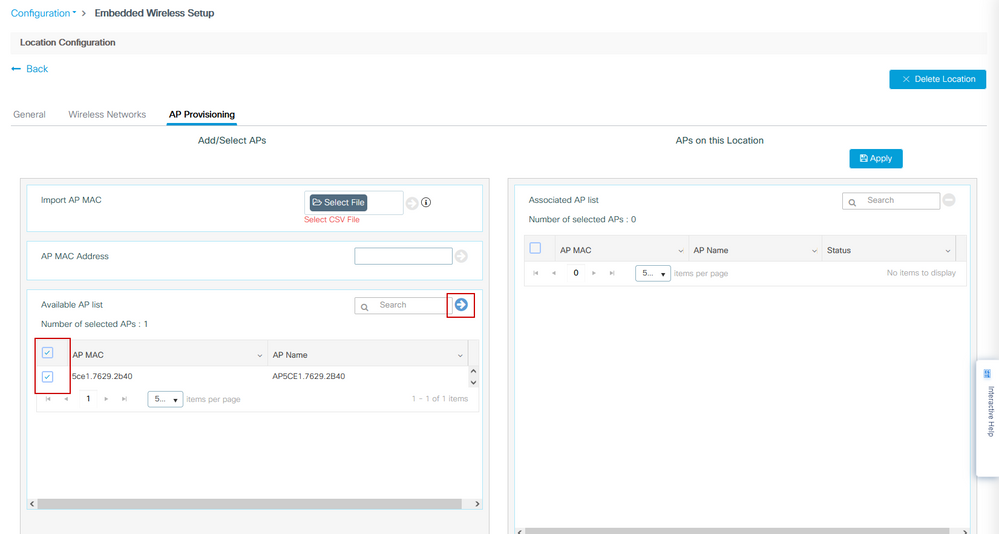
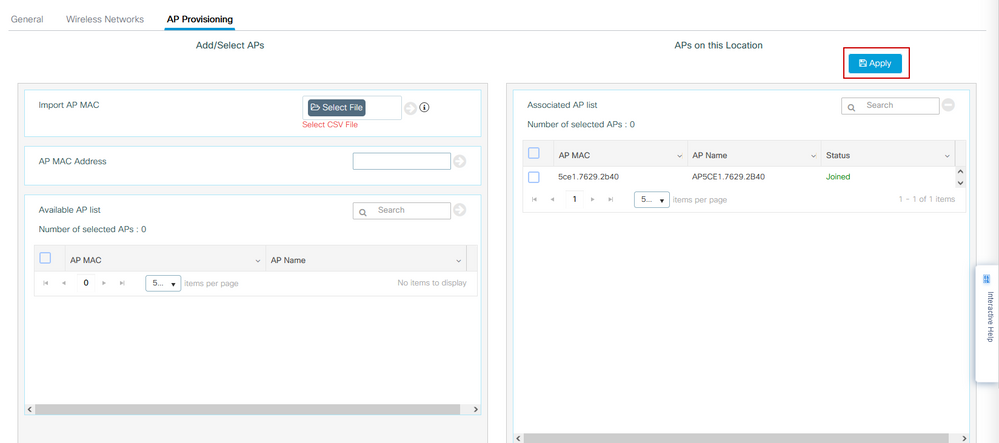
This step adds this configuration to the EWC-Switch:
9300-1(config)# ap location name EWC-Location
9300-1(config-ap-location)# ap-eth-mac <AP mac address>
9300-1(config-ap-location)# tag policy EWC-Location
9300-1(config-ap-location)# tag rf EWC-Location
The ap-eth-mac <AP mac address> command repeats for every AP that is added to the location. A single site will support up to 500 APs.
Verify
Use this command to verify VLAN creation and status for both WMI and AP Onboard.
9300-1#show wireless fabric summary
Fabric Status : Enabled
Control-plane:
Name IP-address Key Status
--------------------------------------------------------------------------------------------
default-control-plane 172.16.0.1 ciscoeca Up
Fabric VNID Mapping:
Name L2-VNID L3-VNID IP Address Subnet Control plane name
----------------------------------------------------------------------------------------------------------------------
APONBOARDING_0_2674_4097_8188 8188 4097 172.16.80.0 255.255.255.0
Verify the AP registration status with these commands:
9300-1#show wireless stats ap join summary
Number of APs: 1
Base MAC Ethernet MAC AP Name IP Address Status Last Failure Phase Last Disconnect Reason
----------------------------------------------------------------------------------------------------------------------------------------------------------------------
ac4a.569c.f560 5ce1.7629.2b40 AP5CE1.7629.2B40 172.16.80.10 Joined Run Tag modified
9300-1#show fabric ap summary
Number of Fabric AP : 1
AP Name Slots AP Model Ethernet MAC Radio MAC Location Country IP Address State
----------------------------------------------------------------------------------------------------------------------------------------------------
AP5CE1.7629.2B40 2 9120AXI 5ce1.7629.2b40 ac4a.569c.f560 default location US 172.16.80.10 Registered
Use this command to verify VxLAN tunnel status with APs.
9300-1#show access-tunnel summary
Access Tunnels General Statistics:
Number of AccessTunnel Data Tunnels = 1
Name RLOC IP(Source) AP IP(Destination) VRF ID Source Port Destination Port
------ --------------- ------------------ ------ ----------- ----------------
Ac0 172.16.0.1 172.16.80.10 0 N/A 4789
Name IfId Uptime
------ ---------- --------------------
Ac0 0x00000069 0 days, 00:20:11
Verify AP tag assignment with this command. APs must all have the same tags and show Location under Source.
9300-1#show ap tag summary
Number of APs: 1
AP Name AP Mac Site Tag Name Policy Tag Name RF Tag Name Misconfigured Tag Source
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------
AP5CE1.7629.2B40 5ce1.7629.2b40 default-site-tag EWC-Location EWC-Location No Location
Note: In this example, 172.16.0.1 is the Loopback0 IP address (which is wireless management) and APs join to it. Since this is fabric in a box, all fabric components point to that as well.
Troubleshoot
Conditional Debugging and Radio Active Tracing
Enable conditional debugs and capture Radio Active (RA) trace to troubleshoot the join process, RA traces provide debug level traces for all processes that interact with the specified condition (AP MAC address in this case). In order to enable conditional debug, follow these steps.
Step 1. Ensure there are no debug conditions enabled.
9300-1#clear platform condition all
Step 2. Enable the debug condition for the AP MAC address that you want to monitor.
By default, monitor-time is 30 minutes (1800 seconds). You can increase the debugs to run for up to 2085978494 seconds.
9300-1#debug wireless mac <AP_RADIO_MAC> {monitor-time <seconds>}
9300-1#debug wireless mac <AP_ETHERNET_MAC> {monitor-time <seconds>}
Note: In order to debug multiple APs, run debug wireless mac command per each AP's radio and Ethernet MAC address. Only Ethernet MAC debug will show the DTLS transactions.
Note: C9800 debugging operates in store and process model. That is, debugging is not displayed on the terminal session and all the logs are buffered internally in order to be viewed later.
Step 3. Bounce AP switchport or capwap reset AP from the AP CLI to capture the full trace.
Step 4. Stop the debugs if the issue is reproduced before the default or configured monitor time is up.
9300-1#no debug wireless mac <AP_RADIO_MAC>
9300-1#no debug wireless mac <AP_ETHERNET_MAC>
Once the monitor-time has elapsed or the debug wireless has been manually stopped, the EWC-Switch generates a local file with the name:
ra_trace_MAC_aaaabbbbcccc_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log
Step 5. Collect the file of the MAC address activity. You have the option to copy the ra trace.log to an external server for offline parsing or display the output directly on the terminal session. Offline parsing is preferred due to the volume of tracelogs generated.
Check the name of the RA traces file.
9300-1#dir flash: | inc ra_trace
Copy the file to an external server:
9300-1#copy flash:ra_trace_MAC_<AP_RADIO_MAC>_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log tftp://<a.b.c.d>/ra-AP_RADIO_MAC.txt
9300-1#copy flash:ra_trace_MAC_<AP_ETHERNET_MAC>_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log tftp://<a.b.c.d>/ra-AP_ETHERNET_MAC.txt
In order to display the tracelogs on a terminal session:
9300-1#more flash:ra_trace_MAC_<AP_RADIO_MAC>_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log
9300-1#more flash:ra_trace_MAC_<AP_ETHERNET_MAC>_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log
Step 6. If the root cause is not obvious, collect the internal logs which are a more verbose view of tracelogs. You do not need to debug the client again as the command provides debug logs that have been already collected and internally stored.
9300-1#show logging profile wireless internal filter <AP_RADIO_MAC> to-file flash:ra-internal-<AP_RADIO_MAC>.txt
9300-1#show logging profile wireless internal filter <AP_ETHERNET_MAC> to-file flash:ra-internal-<AP_RADIO_MAC>.txt
Note: This command output returns traces for all logging levels for all processes and is quite voluminous. Contact the Technical Assistance Center (TAC) in order to help parse through these traces.
9300-1#copy flash:ra-internal-<AP_RADIO_MAC>.txt tftp://<a.b.c.d>/ra-internal-<AP_RADIO_MAC>.txt
9300-1#copy flash:ra-internal-<AP_RADIO_MAC>.txt tftp://<a.b.c.d>/ra-internal-<AP_RADIO_MAC>.txt
In order to display the tracelogs on the terminal session:
9300-1#more flash:ra-internal-<AP_RADIO_MAC>.txt
9300-1#more flash:ra-internal-<AP_ETHERNET_MAC>.txt
Step 7. Remove the debug conditions.
Note: Ensure that you always remove the debug conditions after you troubleshoot the issue.
Example of a Successful AP Join
This is the output of a successful connection attempt from the RA trace perspective. Use the log samples to verify in which stage the AP gets stuck.
CAPWAP Discovery request and response:
2021/09/30 17:49:13.823492 {wncmgrd_R0-0}{1}: [capwapac-discovery] [7353]: (note): MAC: ac4a.569c.f560 IP:172.16.80.10[5264], Discovery Request received
2021/09/30 17:49:13.823519 {wncmgrd_R0-0}{1}: [capwapac-discovery] [7353]: (note): MAC: ac4a.569c.f560 EWLC TAGS payload is not present in discovery request
2021/09/30 17:49:13.823793 {wncmgrd_R0-0}{1}: [ewlc-infra-evq] [7353]: (debug): instance :0 port:12289MAC: 0002.0002.ffff
2021/09/30 17:49:13.824314 {wncmgrd_R0-0}{1}: [capwapac-discovery] [7353]: (note): MAC: ac4a.569c.f560 Public IP learnt is FALSE, public IP discovery is FALSE, private IP discovery is TRUE.
2021/09/30 17:49:13.824414 {wncmgrd_R0-0}{1}: [capwapac-discovery] [7353]: (note): MAC: ac4a.569c.f560 IP:172.16.80.10[5264], Discovery Response sentDTLS handshake for certificate validity check:
2021/09/30 17:49:23.259157 {wncd_x_R0-0}{1}: [capwapac-smgr-srvr] [7770]: (note): MAC: ac4a.569c.f560 DTLS session create callback received.
2021/09/30 17:49:23.259393 {wncd_x_R0-0}{1}: [capwapac-smgr-sess] [7770]: (info): Session-IP: 172.16.80.10[5264] Mac: PMTU 576, effective capwap size 416
2021/09/30 17:49:23.259406 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (debug): DTLS record type: 22, handshake
2021/09/30 17:49:23.259406 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (info): DTLS client hello
2021/09/30 17:49:23.260931 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (debug): DTLS record type: 22, handshake
2021/09/30 17:49:23.260931 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (info): DTLS client hello
2021/09/30 17:49:23.267234 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (debug): DTLS record type: 22, handshake
2021/09/30 17:49:23.267332 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (debug): DTLS record type: 22, handshake
2021/09/30 17:49:23.267891 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (debug): DTLS record type: 22, handshake
2021/09/30 17:49:23.270741 {wncd_x_R0-0}{1}: [ewlc-dtls-sessmgr] [7770]: (info): Remote Host: 172.16.80.10[5264] MAC: ac4a.569c.f56 Completed cert verification, status:CERT_VALIDATE_SUCCESS
2021/09/30 17:49:23.608757 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (debug): DTLS record type: 22, handshake
2021/09/30 17:49:23.608990 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (debug): DTLS record type: 20, change cipher-spec
2021/09/30 17:49:23.609255 {wncd_x_R0-0}{1}: [ewlc-dtls-sess] [7770]: (info): Remote Host: 172.16.80.10[5264] MAC: ac4a.569c.f56 DTLS session established
2021/09/30 17:49:23.609348 {wncd_x_R0-0}{1}: [capwapac-smgr-sess] [7770]: (info): Session-IP: 172.16.80.10[5264] Mac: PMTU 576, effective capwap size 456
2021/09/30 17:49:23.609361 {wncd_x_R0-0}{1}: [capwapac-smgr-srvr] [7770]: (info): Session-IP: 172.16.80.10[5264] Mac: DTLS session has been established for AP
2021/09/30 17:49:23.650838 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (debug): DTLS record type: 23, application dataCAPWAP join request and response:
2021/09/30 17:49:23.650970 {wncd_x_R0-0}{1}: [capwapac-smgr-sess] [7770]: (info): Session-IP: 172.16.80.10[5264] Mac: Capwap message received, type: join_request
2021/09/30 17:49:23.650972 {wncd_x_R0-0}{1}: [capwapac-smgr-sess] [7770]: (note): MAC: ac4a.569c.f560 Received CAPWAP join request
2021/09/30 17:49:23.652901 {wncd_x_R0-0}{1}: [rrm-client] [7770]: (ERR): ac4a.569c.f560 Failed to override default values inradio oper for slot 1, reg domain chk status failed
2021/09/30 17:49:23.653789 {wncd_x_R0-0}{1}: [rrm-client] [7770]: (ERR): ac4a.569c.f560 Failed to override default values inradio oper for slot 0, reg domain chk status failed
2021/09/30 17:49:23.653959 {wncd_x_R0-0}{1}: [apmgr-capwap-join] [7770]: (info): ac4a.569c.f560 Retrieved AP SW version: 17.3.4.30, for AP model: C9120AXI-B, AP image type: ap1g7, site-tag: default-site-tag
2021/09/30 17:49:23.653967 {wncd_x_R0-0}{1}: [apmgr-db] [7770]: (info): ac4a.569c.f560 Operation state of AP changed to: Registered
2021/09/30 17:49:23.654039 {wncd_x_R0-0}{1}: [apmgr-capwap-join] [7770]: (note): MAC: ac4a.569c.f560 Successfully processed Join request. AP name: AP5CE1.7629.2B40, Model: C9120AXI-B, radio slots: 2, rlan slots: 0, site tag name: default-site-tag, policy tag name: EWC-Location, rf tag name: EWC-Location
2021/09/30 17:49:23.654112 {wncmgrd_R0-0}{1}: [ewlc-infra-evq] [7353]: (note): Msg type :mesg->msgtype Priority:1
2021/09/30 17:49:23.654233 {wncd_x_R0-0}{1}: [capwapac-smgr-srvr] [7770]: (info): MAC: ac4a.569c.f560 Join Response generated with MTU 1485. as per MTU payload, update flag: 0
2021/09/30 17:49:23.654311 {wncd_x_R0-0}{1}: [capwapac-smgr-srvr] [7770]: (note): MAC: ac4a.569c.f560 Join processing complete. AP in joined stateCAPWAP configuration:
2021/09/30 17:49:23.947851 {wncd_x_R0-0}{1}: [apmgr-ap-global] [7770]: (info): ac4a.569c.f560 Lispagent was triggered during ap join.
2021/09/30 17:49:23.948023 {wncd_x_R0-0}{1}: [capwapac-smgr-srvr] [7770]: (info): Session-IP: 172.16.80.10[5264] Mac: ac4a.569c.f560 Config status request was processed and Config status response was sent. AP in Configuration state.
2021/09/30 17:49:23.948157 {wncd_x_R0-0}{1}: [lisp-agent-db] [7770]: (ERR): Invalid source IP address type
2021/09/30 17:49:23.948344 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (note): Map request msg sent successfully for AP vnid 4097
2021/09/30 17:49:23.949993 {wncmgrd_R0-0}{1}: [hl-core] [7353]: (debug): Radio change on AP ac4a.569c.f560 not connected to a L1 cache entry
2021/09/30 17:49:23.950130 {wncmgrd_R0-0}{1}: [hl-core] [7353]: (debug): Radio change on AP ac4a.569c.f560 not connected to a L1 cache entry
2021/09/30 17:49:24.889682 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (debug): DTLS record type: 23, application data
2021/09/30 17:49:24.889807 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (debug): DTLS record type: 23, application data
2021/09/30 17:49:24.889992 {wncd_x_R0-0}{1}: [capwapac-smgr-sess] [7770]: (info): Session-IP: 172.16.80.10[5264] Mac: ac4a.569c.f560 Capwap message received, type: config_status_request
2021/09/30 17:49:24.890020 {wncd_x_R0-0}{1}: [capwapac-smgr-sess-fsm] [7770]: (info): Session-IP: 172.16.80.10[5264] Mac: ac4a.569c.f560 process config status request
2021/09/30 17:49:24.890045 {wncd_x_R0-0}{1}: [capwapac-smgr-srvr] [7770]: (info): Session-IP: 172.16.80.10[5264] Mac: ac4a.569c.f560 Updating capwap path MTU: 1485 received in config status request
2021/09/30 17:49:24.890048 {wncd_x_R0-0}{1}: [capwapac-smgr-sess] [7770]: (info): Session-IP: 172.16.80.10[5264] Mac: ac4a.569c.f560 PMTU 1485, effective capwap size 1368
2021/09/30 17:49:24.890134 {wncd_x_R0-0}{1}: [apmgr-msgelem] [7770]: (info): ac4a.569c.f560 AP domain name is not set in config status
2021/09/30 17:49:24.890135 {wncd_x_R0-0}{1}: [apmgr-msgelem] [7770]: (info): ac4a.569c.f560 AP IPv6 nameserver is not set in config status
[...]
2021/09/30 17:49:24.890818 {wncd_x_R0-0}{1}: [capwapac-smgr-srvr] [7770]: (info): Session-IP: 172.16.80.10[5264] Mac: ac4a.569c.f560 Config status request was processed and Config status response was sent. AP in Configuration state.
2021/09/30 17:49:24.892967 {wncmgrd_R0-0}{1}: [hl-core] [7353]: (debug): Radio change on AP ac4a.569c.f560 not connected to a L1 cache entry
2021/09/30 17:49:24.892993 {wncmgrd_R0-0}{1}: [hl-core] [7353]: (debug): Radio change on AP ac4a.569c.f560 not connected to a L1 cache entry
2021/09/30 17:49:24.964085 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [7770]: (debug): DTLS record type: 23, application data
[...]
2021/09/30 17:49:24.964384 {wncd_x_R0-0}{1}: [ble-d] [7770]: (debug): BLE LTX DB: Creating AP ac4a.569c.f560
2021/09/30 17:49:24.964474 {wncd_x_R0-0}{1}: [ble-d] [7770]: (debug): BLE LTX DB: Successfully created AP ac4a.569c.f560
2021/09/30 17:49:24.964479 {wncd_x_R0-0}{1}: [ble-d] [7770]: (debug): BLE LTX DB: Setting capability
2021/09/30 17:49:24.964479 {wncd_x_R0-0}{1}: [ble-d] [7770]: (debug): BLE LTX DB: Updating AP ac4a.569c.f560
2021/09/30 17:49:24.964483 {wncd_x_R0-0}{1}: [ble-d] [7770]: (debug): BLE LTX DB: Successfully updated AP ac4a.569c.f560
[...]
2021/09/30 17:49:25.000954 {wncd_x_R0-0}{1}: [apmgr-capwap-config] [7770]: (info): ac4a.569c.f560 AP is in config ready state. Initial configuration will be pushed.
2021/09/30 17:49:25.000972 {wncd_x_R0-0}{1}: [apmgr-capwap-config] [7770]: (info): ac4a.569c.f560 Sending FIPS vendor payload config, FIPS status 0
2021/09/30 17:49:25.000975 {wncd_x_R0-0}{1}: [apmgr-capwap-config] [7770]: (info): Preparing FIPS config, fips status 0
2021/09/30 17:49:25.000978 {wncd_x_R0-0}{1}: [apmgr-capwap-config] [7770]: (info): Preparing WLANCC config, wlancc status 0
2021/09/30 17:49:25.001064 {wncd_x_R0-0}{1}: [apmgr-ap-global] [7770]: (info): ac4a.569c.f560 AP is in Local mode.
2021/09/30 17:49:25.001064 {wncd_x_R0-0}{1}: [apmgr-ap-global] [7770]: (info): ac4a.569c.f560 Mode update on AP join : AP already in Local mode which matches site configuration
2021/09/30 17:49:25.001081 {wncd_x_R0-0}{1}: [apmgr-db] [7770]: (info): ac4a.569c.f560 Tag process ap wlan config mapping. wlans[0] associated to to APIf the AP is not in Local mode, then it reboots to apply a mode change. A log similar to this one is printed on EWC-Switch console:
*Sep 29 20:54:07.769: %APMGR_TRACE_MESSAGE-4-WLC_CONFIG_CHECKER_WARNING: Switch 1 R0/0: wncd: config check: The mode of AP ac4a.569c.f560 is changed from Flexconnect to Local.
*Sep 29 20:54:07.769: %APMGR_TRACE_MESSAGE-3-WLC_EXEC_MSG: Switch 1 R0/0: wncd: % Error: AP: AP5CE1.7629.2B40 will go for a reboot due to Mode change from Flexconnect to Local
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
2.0 |
10-Oct-2021 |
Initial Release |
1.0 |
10-Oct-2021 |
Initial Release |
Contributed by Cisco Engineers
- Jesus Herrera GarciaCisco TAC
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback