Configuring the VPN 3000 Concentrator to Communicate with the VPN Client Using Certificates
Available Languages
Contents
Introduction
This document includes step-by-step instructions on how to configure the Cisco VPN 3000 Series Concentrators with VPN Clients with the use of certificates.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on Cisco VPN 3000 Concentrator software version 4.0.4A.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to the Cisco Technical Tips Conventions for more information on document conventions.
VPN 3000 Concentrator Certificates for VPN Clients
Complete these steps in order to configure VPN 3000 Concentrator certificates for VPN Clients.
-
The IKE policy must be configured to use certificates on the VPN 3000 Concentrator Series Manager. In order to configure the IKE policy, select Configuration > System > Tunneling Protocols > IPsec > IKE Proposals, and move CiscoVPNClient-3DES-MD5-RSA to the Active Proposals.
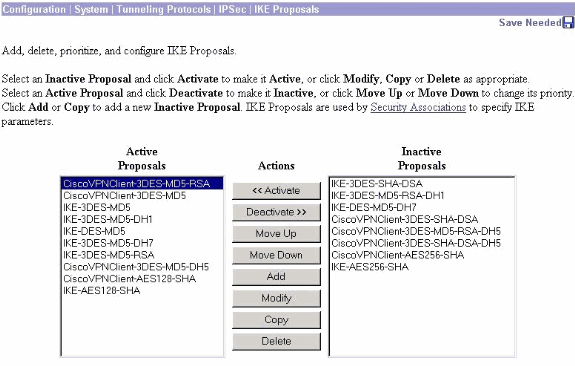
-
You must also configure the IPsec policy to use certificates. Select Configuration > Policy Management > Traffic Management > Security Associations, highlight ESP-3DES-MD5 and then click Modify to configure the IPsec policy to configure the IPsec policy.
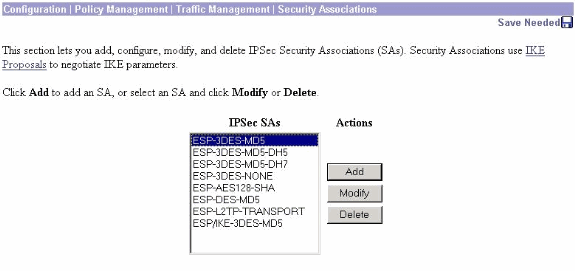
-
On the Modify window, under Digital Certificates, make sure to select your installed identity certificate. Under IKE Proposal, select CiscoVPNClient-3DES-MD5-RSA and click Apply.
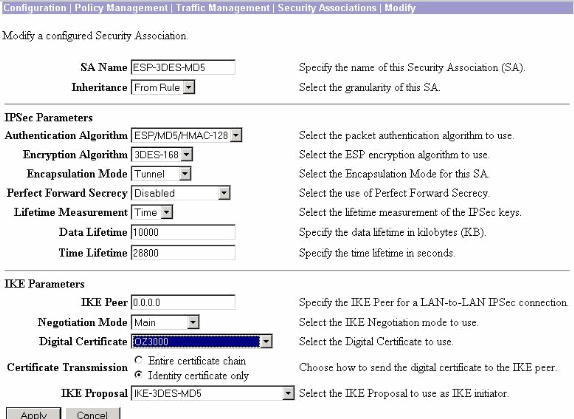
-
In order to configure an IPsec group, select Configuration > User Management > Groups > Add, add a group called IPSECCERT (the IPSECCERT group name matches the Organizational Unit (OU) in the identity certificate), and select a password.
This password is not used anywhere if you use certificates. In this example, "cisco123" is the password.
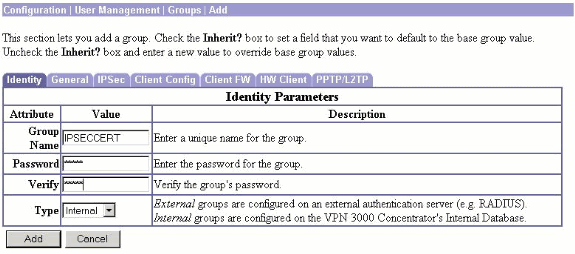
-
On the same page, click the General tab and make sure that you select IPsec as the Tunneling Protocol.
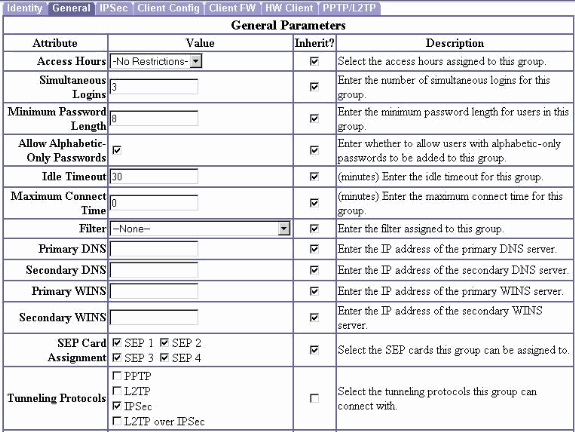
-
Click the IPsec tab and make sure that your configured IPsec Security Association (SA) is selected under IPsec SA and click Apply.
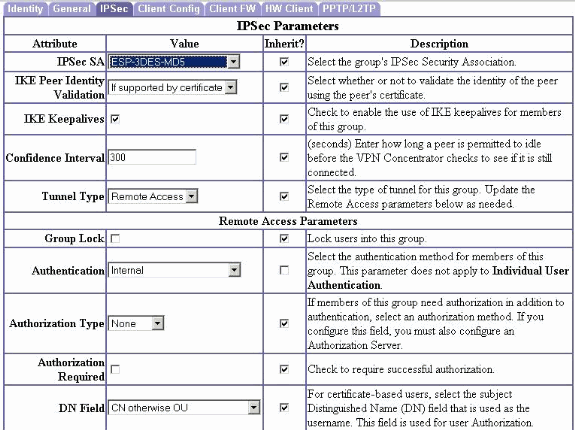
-
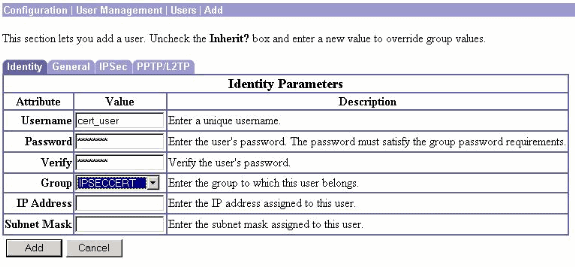
In order to configure an IPsec group on the VPN 3000 Concentrator, select Configuration > User Management > Users > Add, specify a User Name, Password, and the Group name, and then click Add.
In the example, these fields are used:
-
User Name = cert_user
-
Password = cisco123
-
Verify = cisco123
-
Group = IPSECCERT
-
-
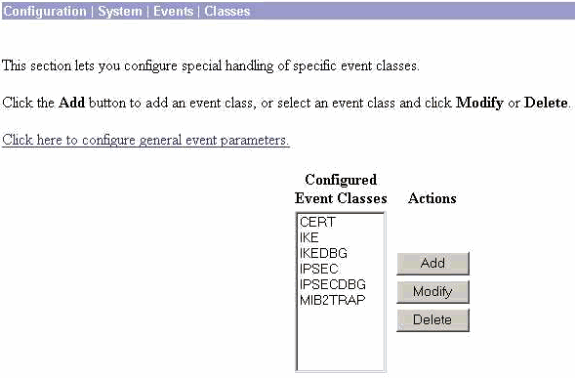
In order to enable debugging on the VPN 3000 Concentrator select Configuration > System > Events > Classes and add these classes:
-
CERT 1-13
-
IKE 1-6
-
IKEDBG 1-10
-
IPSEC 1-6
-
IPSECDBG 1-10
-
-
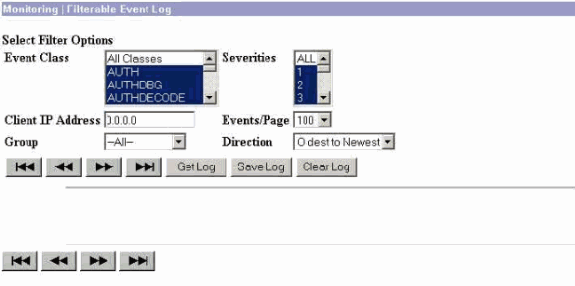
Select Monitoring > Filterable Event Log in order to view the debugs.
Note: If you decide to change the IP addresses, you can make an enrollment of the new IP addresses and install the issued certificate later with those new addresses.
Verify
There is currently no verification procedure available for this configuration.
Troubleshoot
Refer to Troubleshooting Connection Problems on the VPN 3000 Concentrator for further troubleshooting information.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
06-Sep-2001 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)










 Feedback
Feedback