How to Configure the Cisco VPN 3000 Concentrator to Support TACACS+ Authentication for Management Accounts
Available Languages
Contents
Introduction
This document provides step-by-step instructions in order to configure the Cisco VPN 3000 Series Concentrators to support the TACACS+ Authentication for Management Accounts.
As soon as a TACACS+ server is configured on the VPN 3000 Concentrator, the locally configured account names and passwords such as admin, config, isp, and so forth, are no longer used. All logins to the VPN 3000 Concentrator are sent to the configured external TACACS+ server for user and password verification.
The definition of a privilege level for each user on the TACACS+ server determines the permissions on the VPN 3000 Concentrator for each TACACS+ username. Then, match that up with the AAA Access Level defined under the locally configured username on the VPN 3000 Concentrator. This is an important point because as soon as a TACACS+ server is defined, the locally configured usernames on the VPN 3000 Concentrator are no longer valid. But, they are still used only in order to match up the returned privilege level from the TACACS+ server, with the AAA Access Level under that local user. The TACACS+ username is then assigned the privileges that the locally configured VPN 3000 Concentrator user has defined under their profile.
For example, described in detail in the configuration sections, a TACACS+ user/group is configured to return a TACACS+ Privilege Level of 15. Under the Administrators section of the VPN 3000 Concentrator, the admin user has its AAA Access Level also set to 15. This user is allowed to modify the configuration under all sections, and to read/write files. Because TACACS+ Privilege Level and AAA Access Level match, the TACACS+ user is given those permissions on the VPN 3000 Concentrator.
As an example, if you decide that a user needs to be able to modify the configuration, but not read/write files, assign them a privilege level of 12 on the TACACS+ server. You can pick any number between one and 15. Then, on the VPN 3000 Concentrator, pick one of the other locally configured administrators. Next, set its AAA Access Level to 12, and set the permissions on this user in order to be able to modify the configuration, but not to read/write files. Because of the matching privilege/access level, the user gets those permissions when they login.
The locally configured usernames on the VPN 3000 Concentrator are no longer used. But, the Access Rights and AAA Access Levels under each of those users are used in order to define the privileges a particular TACACS+ user gets when you login.
Prerequisites
Requirements
Ensure that you meet these requirements before you attempt this configuration:
-
Ensure that you have IP connectivity to the TACACS+ server from the VPN 3000 Concentrator. If your TACACS+ server is towards the public interface, do not forget to open the TACACS+ (TCP port 49) on the public filter .
-
Ensure backup access via the console is operational. It is easy to accidentally lock all users out of the configuration when you first set this up. The only way to recover access is via the console, which still uses the locally configured usernames and passwords.
Components Used
The information in this document is based on these software and hardware versions:
-
Cisco VPN 3000 Concentrator Software Release 4.7.2.B (Alternatively, any release of 3.0 or later OS software works.)
-
Cisco Secure Access Control Server for Windows Servers Release 4.0 (Alternately, any release of 2.4 or later software works.)
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Configure the TACACS+ Server
Add an Entry for the VPN 3000 Concentrator in the TACACS+ Server
Complete these steps in order to add an entry for the VPN 3000 Concentrator in the TACACS+ server.
-
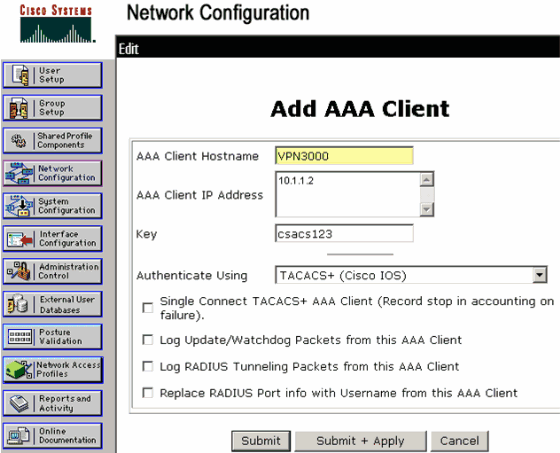
Click Network Configuration in the left panel. Under AAA Clients, click Add Entry.
-
On the next window, fill out the form to add the VPN Concentrator as the TACACS+ client. This example uses:
-
AAA Client Hostname = VPN3000
-
AAA Client IP Address = 10.1.1.2
-
Key = csacs123
-
Authenticate using = TACACS+ (Cisco IOS)
Click Submit + Restart.
-
Add a User Account in the TACACS+ Server
Complete these steps in order to add a user account in the TACACS+ server.
-
Create a user account in the TACACS+ server that can be later used for TACACS+ authentication. Click User Setup in the left panel, add user "johnsmith" and click Add/Edit in order to do this.
-
Add a password for this user, and assign the user to an ACS group that contains the other VPN 3000 Concentrator administrators.
Note: This example defines the privilege level under this particular user ACS group profile. If this is to be done on a per-user basis, choose Interface Configuration > TACACS+ (Cisco IOS) and check the User box for the Shell (exec) service. Only then are the TACACS+ options described in this document available under each user profile.
Edit the Group on the TACACS+ Server
Complete these steps to edit the group on the TACACS+ server.
-
Click Group Setup in the left panel.
-
From the drop-down menu, choose the group the user was added to in the Add a User Account in the TACACS+ Server section, which is Group 1 in this example, and click Edit Settings.
-
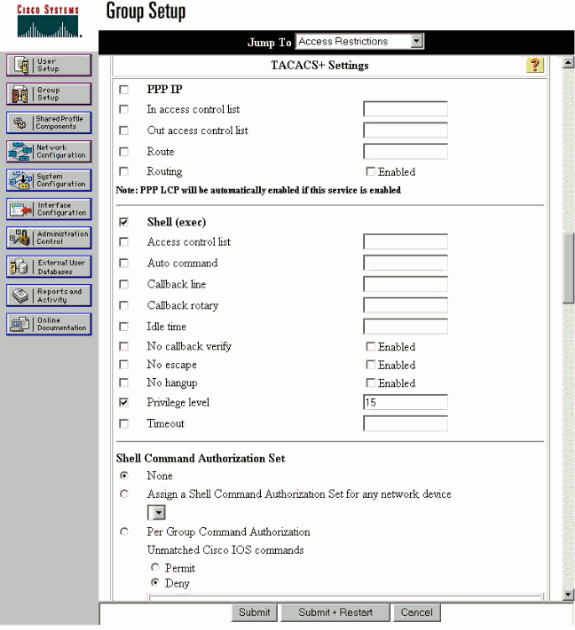
On the next window, make sure that these attributes are selected under TACACS+ Settings:
-
Shell (exec)
-
Privilege level = 15
Once done, click Submit + Restart.
-
Configure the VPN 3000 Concentrator
Add an Entry for the TACACS+ Server in the VPN 3000 Concentrator
Complete these steps in order to add an entry for the TACACS+ server in the VPN 3000 Concentrator.
-
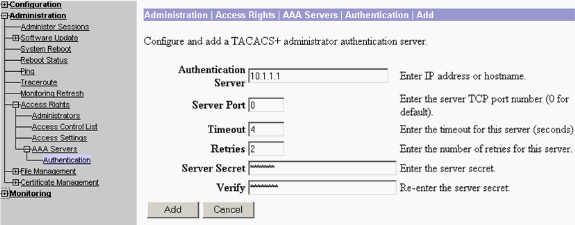
Choose Administration > Access Rights > AAA Servers > Authentication in the navigation tree in the left panel, and then click Add in the right panel.
As soon as you click Add in order to add this server, locally configured username/passwords on the VPN 3000 Concentrator are no longer used. Ensure backup access via the console works in case of a lock-out.
-
On the next window, fill out the form as seen here:
-
Authentication Server = 10.1.1.1 (IP address of TACACS+ server)
-
Server Port = 0 (default)
-
Timeout = 4
-
Retries = 2
-
Server Secret = csacs123
-
Verify = csacs123
-
Modify the Admin Account on the VPN Concentrator for TACACS+ Authentication
Complete these steps to modify the admin account on the VPN Concentrator for TACACS+ authentication.
-
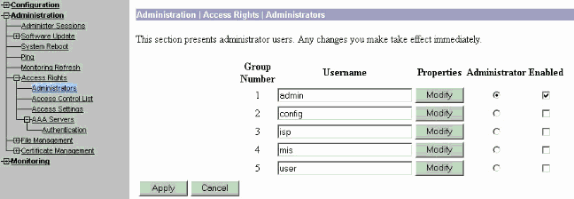
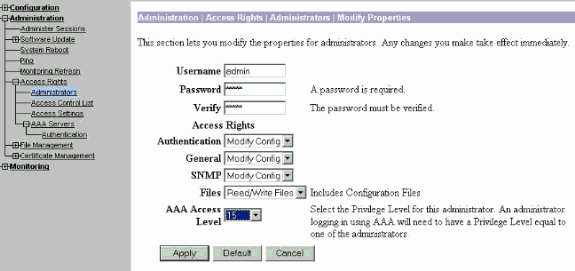
Click Modify for the user admin in order to modify the properties of this user.
-
Choose the AAA Access Level as 15.
This value can be any number between one and 15. Note that it must match the TACACS+ Privilege Level defined under the user/group profile on the TACACS+ server. The TACACS+ user then picks up the permissions defined under this VPN 3000 Concentrator user for the modification of the configuration, reading/writing files, and so forth.
Verify
There is currently no verification procedure available for this configuration.
Troubleshoot
Complete the steps in these instructions in order to troubleshoot your configuration.
-
In order to test the authentication:
-
Choose Administration > Access Rights > AAA Servers > Authentication.
-
Select your server, and then click Test.
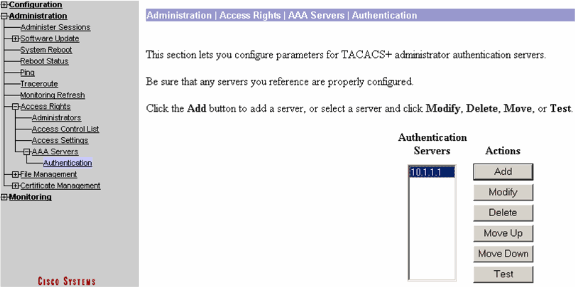
Note: When the TACACS+ server is configured on the Administration tab, there is no way to set up the user to authenticate on the VPN 3000 local database. You can only fallback using another external database or TACACS server.
-
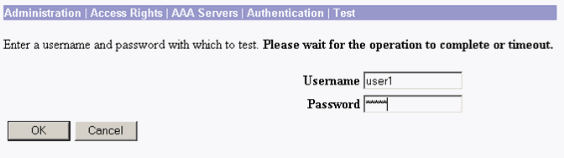
Enter the TACACS+ username and password and click OK.
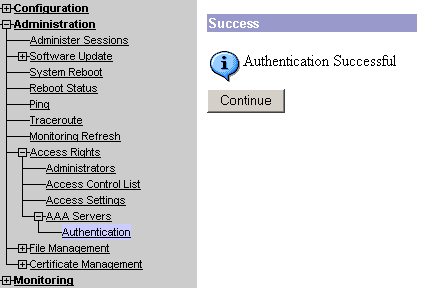
A successful authentication appears.
For TACACS+ Servers
-
-
If it fails, there is either a configuration problem or an IP connectivity issue. Check the Failed Attempts Log on the ACS server for messages related to the failure.
-
If no messages appear in this log then there is probably an IP connectivity issue. The TACACS+ request does not reach the TACACS+ server. Verify the filters applied to the appropriate VPN 3000 Concentrator interface allows TACACS+ (TCP port 49) packets in and out.
-
If the failure displays as service denied in the log, then the Shell (exec) service has not been correctly enabled under the user or group profile on the TACACS+ server.
-
-
If the test authentication is successful, but logins to the VPN 3000 Concentrator continue to fail, check the Filterable Event Log via the console port.
If you see a similar message:
65 02/09/2005 13:14:40.150 SEV=5 AUTH/32 RPT=2 User [ johnsmith ] Protocol [ HTTP ] attempted ADMIN logon. Status: <REFUSED> authorization failure. NO Admin Rights
This message indicates the privilege level assigned on the TACACS+ server has no matching AAA access level under any of the VPN 3000 Concentrator users. For example, user johnsmith has a TACACS+ privilege level of 7 on the TACACS+ server, but none of the five VPN 3000 Concentrator administrators have an AAA access level of 7.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
31-Oct-2006 |
Initial Release |








 Feedback
Feedback