Introduction
This document describes the steps to export Secure Malware Analytics Appliance service metrics data to Prometheus Monitoring Software.
Contributed by Cisco TAC Engineers.
Prerequisites
Cisco recommends that you have knowledge of Secure Malware Analytics Appliance and Prometheus software.
Requirements
- Secure Malware Analytics Appliance (version 2.13 onwards)
- Prometheus software license
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
The Riemann/Elastic search-based monitoring system running on the Appliance is replaced by Prometheus-based monitoring from Secure Malware Analytics Appliance version 2.13 onwards.
Note: The main purpose of this integration is to monitor the statistics of your Secure Malware Analytics Appliance using Prometheus Monitoring System software. This includes an interface, traffic statistics, etc.
Configure
Step 1. Log in to Secure Malware Analytics Appliance, navigate to Operations > Metrics in order to find the API key and Basic Authentication Password.
Step 2. Install Prometheus Server software: https://prometheus.io/download/
Step 3. Create a .yml file, it must be calledprometheus.yml and it must has this details:
scrape_configs:
- job_name: 'metrics'
bearer_token_file: 'token.jwt'
scheme: https
file_sd_configs:
- files:
- 'targets.json'
relabel_configs:
- source_labels: [__address__]
regex: '[^/]+(/.*)' # capture '/...' part
target_label: __metrics_path__ # change metrics path
- source_labels: [__address__]
regex: '([^/]+)/.*' # capture host:port
target_label: __address__ # change target
Step 4. Run the CLI command in order to generate a JWT Token for authentication, as it is specified in the configuration file above:
curl -k -s -XPOST -d 'user=threatgrid&password=<TGA Password>&method=password' "https://_opadmin IP_:443/auth?method=password" | tee token.jwt
Step 5. Run this command to verify the Expiration Date field for the token (1 Hour Validity).
awk -F. '{print $2}' token.jwt | base64 --decode 2>/dev/null | sed -e 's;\([^}]\)$;\1};' | jq .
Command output example below:
{
"user": "threatgrid",
"pw_method": "password",
"addr": "<Removed>",
"exp": 1604098219,
"iat": 1604094619,
"iss": "<Removed>",
"nbf": 1604094619
}
Note: The time is displayed in Epoch format.
Step 6. Pull the configuration of services, after login into opadmin interface, enter this line from the UI:
https://_opadmin IP_/metrics/v1/config
Step 7. After restarting the Prometheus service, the configuration is activated.
Step 8. Access the Prometheus page:
http://localhost:9090/graph
You can see the Secure Malware Analytics Appliance services in "UP" state, as shown in the mage.
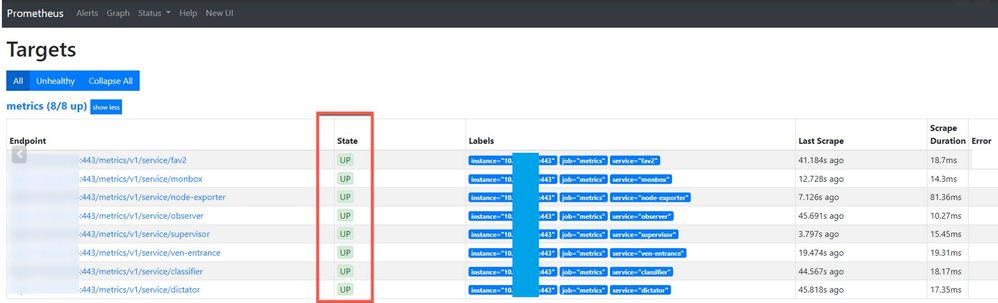
Verify
You can see the data is received from the Secure Malware Analytics Applianced devices, review the metrics in base on your own requirements, as shown in the mage.
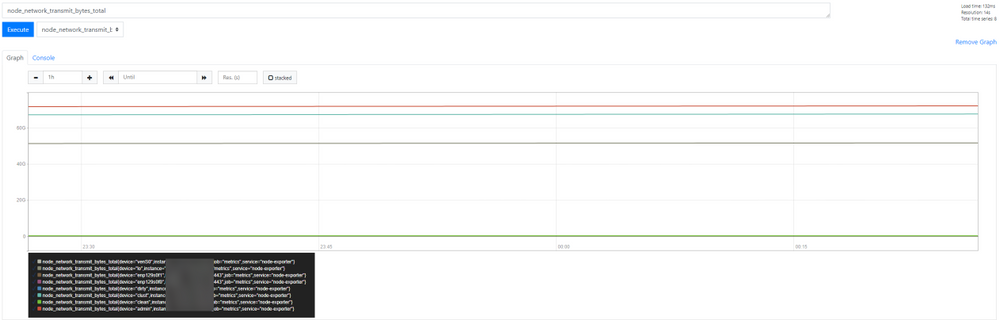
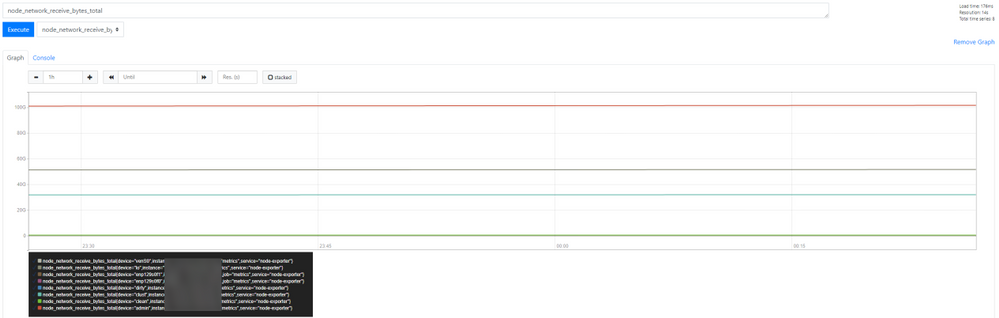
Note: This feature works only to collect specific data. Data flow management is the responsibility of the Prometheus server.
There is no supported troubleshooting from Cisco TAC side, you can reach out 3rd party vendor support for additional feature support.




 Feedback
Feedback