Configure LDAP Attribute Map for RAVPN on FTD Managed by FDM
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Introduction
This document describes the procedure to use a Lightweight Directory Access Protocol (LDAP) server to authenticate and authorize Remote Access VPN (RA VPN) users, and grant them different network access based on their group membership on the LDAP server.
Prerequisites
Requirements
- Basic knowledge of RA VPN configuration on Firewall Device Manager (FDM)
- Basic knowledge of LDAP server configuration on FDM
- Basic knowledge of REpresentational State Transfer (REST) Application Program Interface (API) and FDM Rest API Explorer
- Cisco FTD version 6.5.0 or newer managed by FDM
Components Used
The following hardware and software versions of application/devices were used:
- Cisco FTD version 6.5.0, build 115
- Cisco AnyConnect version 4.10
- Microsoft Active Directory (AD) Server
- Postman or any other API development tool
Note: Configuration support for the Microsoft AD Server and Postmal tool is not provided by Cisco.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Authentication Flow

LDAP Attribute Map Flow Explained
- The user initiates a remote access VPN connection to the FTD and provides a username and password for their Active Directory (AD) account.
- The FTD sends a LDAP request to the AD server over port 389 or 636 (LDAP over SSL)
- The AD responds back to the FTD with all attributes associated with the user.
- The FTD matches the received attribute values with the LDAP Attribute Map created on the FTD. This is the Authorization process.
- The user then connects and inherits settings from the Group-Policy matched with the memberOf attribute in the LDAP Attribute Map.
For the purpose of this document, the Authorization of AnyConnect users is done using the memberOf LDAP attribute.
- The memberOf attribute from the LDAP Server for each user is mapped to a ldapValue entity on the FTD. If the user belongs to the matching AD group, the Group-Policy associated with that ldapValue is inherited by the user.
- If the memberOf attribute value for a user is not matched with any of the ldapValue entity on the FTD, the default Group-Policy for the selected Connection Profile is inherited. In this example, NOACCESS Group-Policy is inherited to .
Configure
LDAP Attribute Map for FTD managed by FDM is configured with REST API.
Configuration Steps on FDM
Step 1. Verify Device is registered to Smart Licensing.
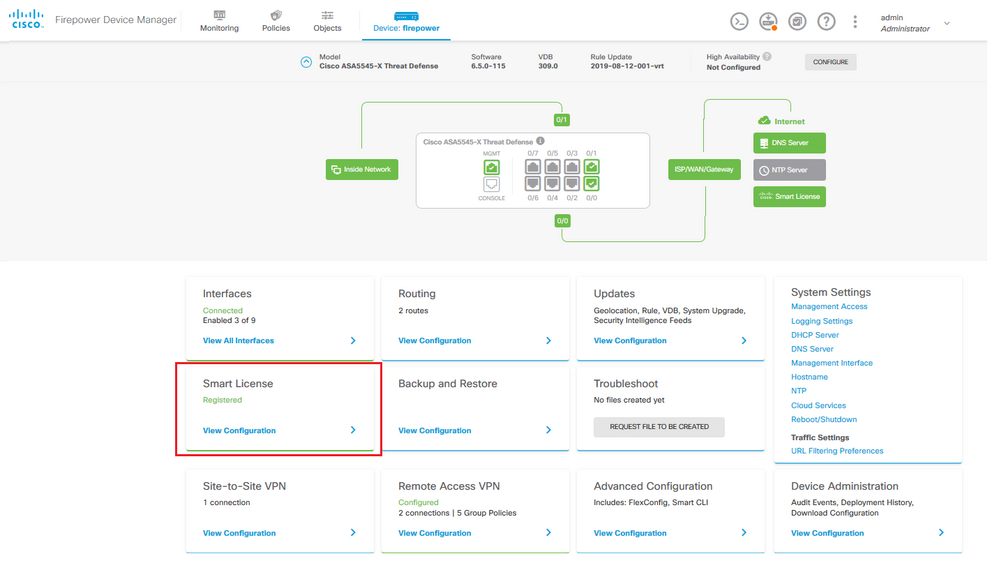
Step 2. Verify AnyConnect Licenses are enabled on the FDM.
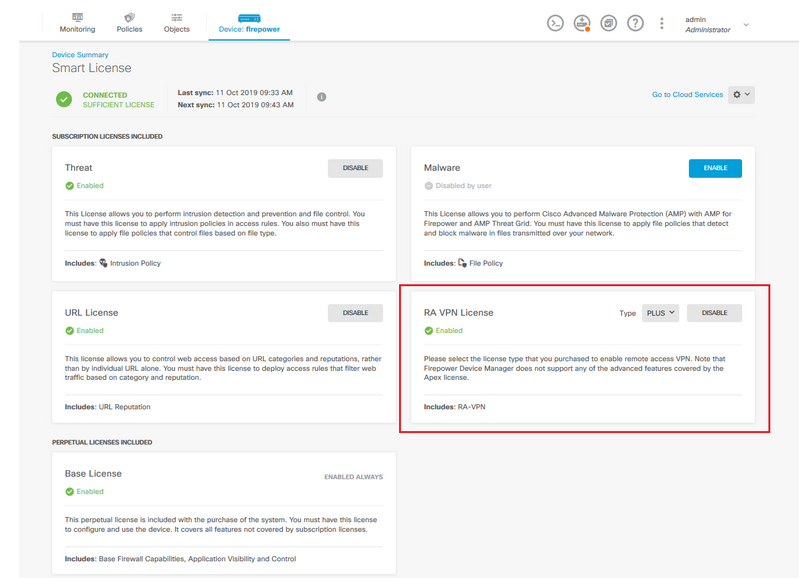
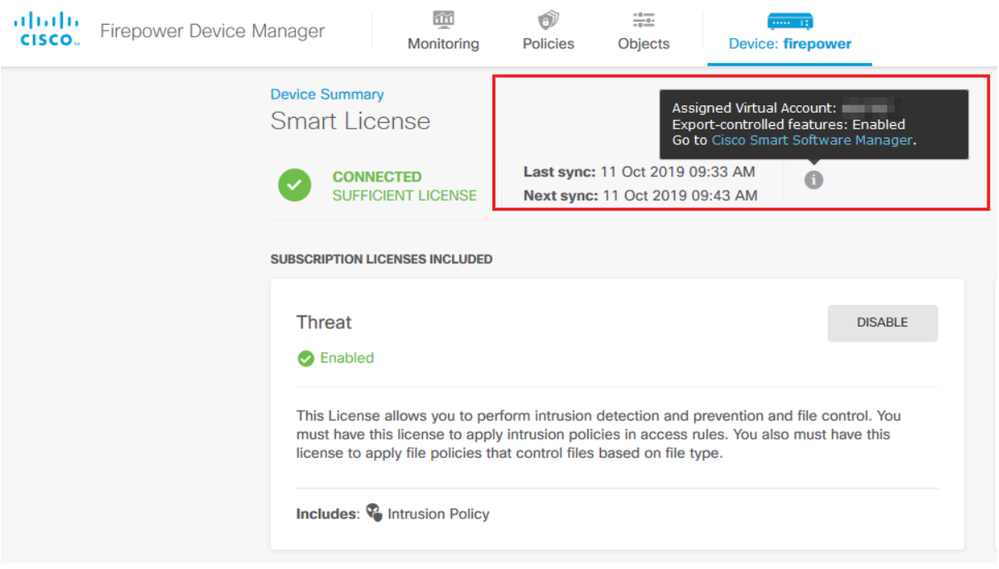
Step 3. Verify Export-controlled features is Enabled in the token.
Note: This document assumes that RA VPN is already configured. Please refer to the following document for more information on How to configure RAVPN on FTD managed by FDM.
Step 4. Navigate to Remote Access VPN > Group Policies.
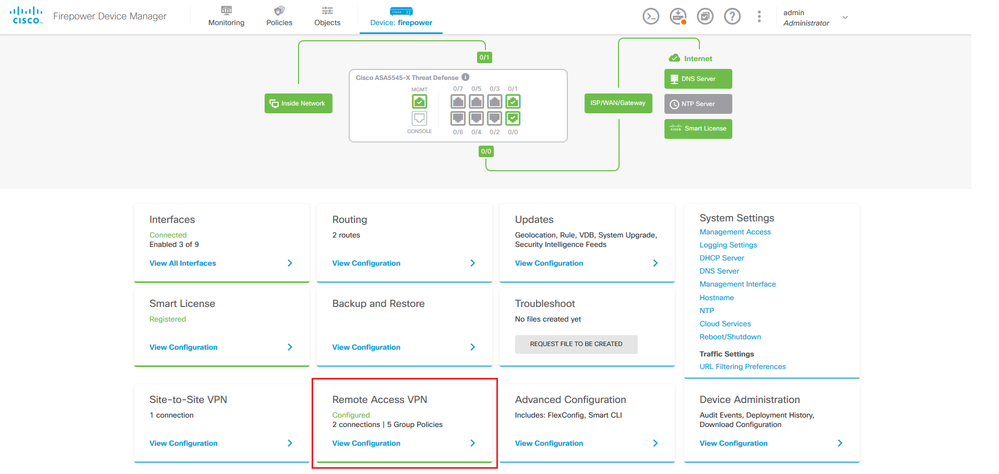
Step 5. Navigate to Group Policies. Click on '+' to configure the different Group-Policies for each AD group. In this example, the Group-policies Finance-Group-Policy, HR-Group-Policy and IT-Group-Policy are configured to have access to different subnets.
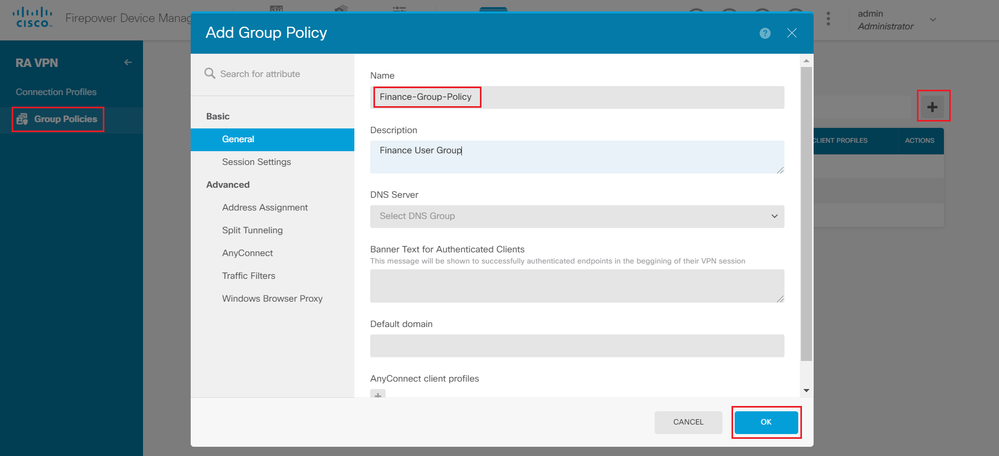
The Finance-Group-Policy has the following settings:
firepower# show run group-policy Finance-Group-Policy group-policy Finance-Group-Policy internal group-policy Finance-Group-Policy attributes banner value You can access Finance resource dhcp-network-scope none vpn-simultaneous-logins 3 vpn-idle-timeout 30 vpn-idle-timeout alert-interval 1 vpn-session-timeout none vpn-session-timeout alert-interval 1 vpn-filter none vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelspecified ipv6-split-tunnel-policy tunnelall split-tunnel-network-list value Finance-Group-Policy|splitAcl split-dns none split-tunnel-all-dns disable client-bypass-protocol disable msie-proxy method no-modify vlan none address-pools none ipv6-address-pools none webvpn <output omitted>
Similarly, HR-Group-Policy has below settings:
firepower# show run group-policy HR-Group-Policy group-policy HR-Group-Policy internal group-policy HR-Group-Policy attributes banner value You can access Finance resource dhcp-network-scope none vpn-simultaneous-logins 3 vpn-idle-timeout 30 vpn-idle-timeout alert-interval 1 vpn-session-timeout none vpn-session-timeout alert-interval 1 vpn-filter none vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelspecified ipv6-split-tunnel-policy tunnelall split-tunnel-network-list value HR-Group-Policy|splitAcl split-dns none split-tunnel-all-dns disable client-bypass-protocol disable msie-proxy method no-modify vlan none address-pools none ipv6-address-pools none webvpn <output omitted>
Finally, IT-Group-Policy has the next settings:
firepower# show run group-policy IT-Group-Policy group-policy IT-Group-Policy internal group-policy IT-Group-Policy attributes banner value You can access Finance resource dhcp-network-scope none vpn-simultaneous-logins 3 vpn-idle-timeout 30 vpn-idle-timeout alert-interval 1 vpn-session-timeout none vpn-session-timeout alert-interval 1 vpn-filter none vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelspecified ipv6-split-tunnel-policy tunnelall split-tunnel-network-list value IT-Group-Policy|splitAcl split-dns none split-tunnel-all-dns disable client-bypass-protocol disable msie-proxy method no-modify vlan none address-pools none ipv6-address-pools none webvpn <output omitted>
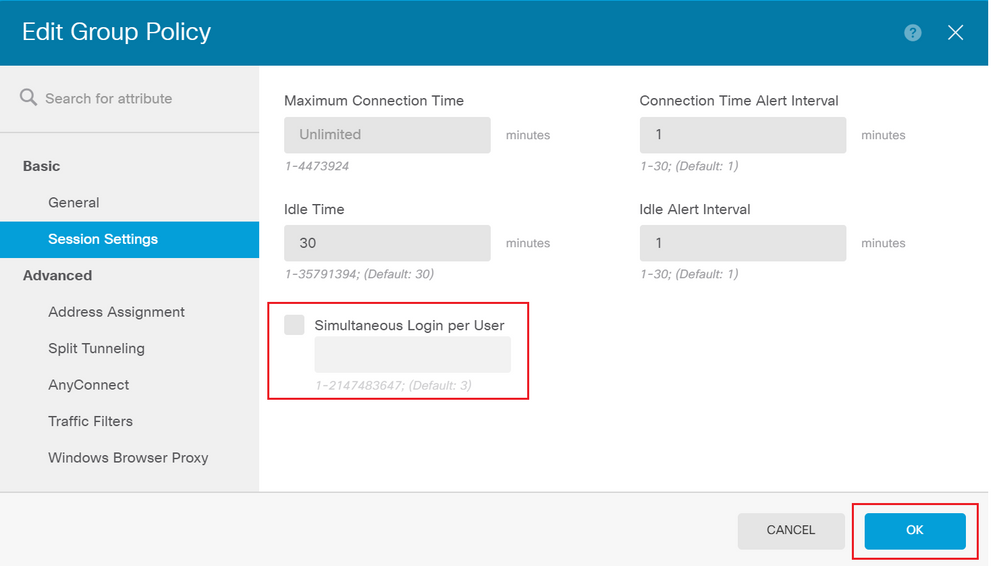
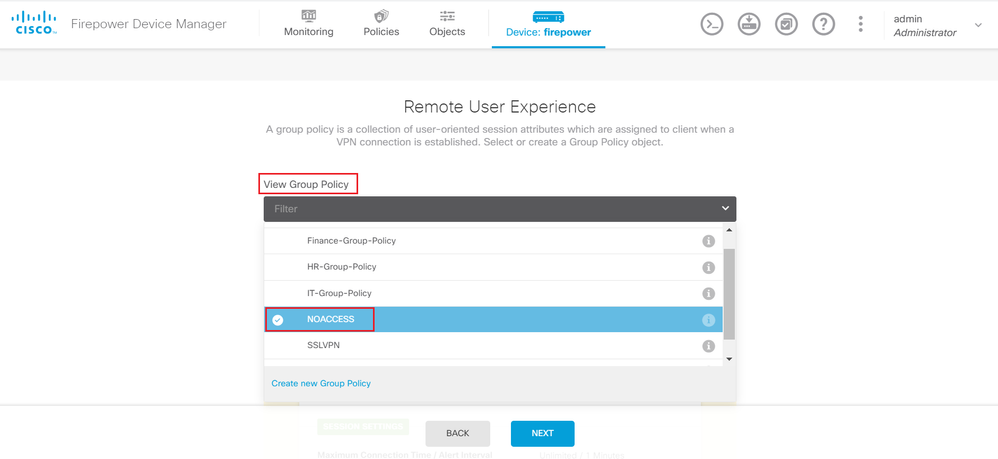
Step 6. Create a Group-Policy NOACCESS and navigate to Session Settings and uncheck the Simultaneous Login per User option. This sets the vpn-simultaneous-logins value to 0.
The vpn-simultaneous-logins value in the Group-Policy when set to 0 terminates the VPN connection of the user immediately. This mechanism is used to prevent users that belong to any AD User-Group other than the configured ones (in this example Finance, HR or IT) from establishing successful connections to the FTD and accessing secure resources available only for the allowed User-Group accounts.
Users that belong to correct AD User-Groups match the LDAP Attribute Map on the FTD and inherit the mapped Group-Policies, while users that do not belong to any of the allowed groups then inherit the default Group-Policy of the connection profile, which in this case is NOACCESS.
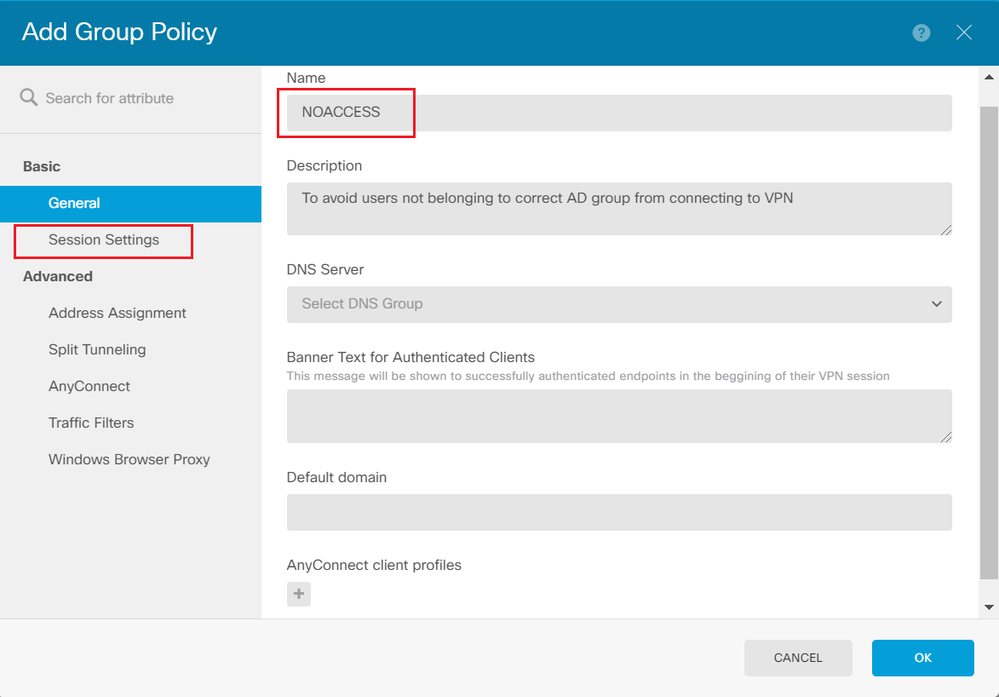
The NOACCESS Group-Policy has the following settings:
firepower# show run group-policy NOACCESS group-policy NOACCESS internal group-policy NOACCESS attributes dhcp-network-scope none vpn-simultaneous-logins 0 vpn-idle-timeout 30 vpn-idle-timeout alert-interval 1 vpn-session-timeout none vpn-session-timeout alert-interval 1 vpn-filter none vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelall ipv6-split-tunnel-policy tunnelall split-dns none split-tunnel-all-dns disable client-bypass-protocol disable msie-proxy method no-modify vlan none address-pools none ipv6-address-pools none webvpn anyconnect ssl dtls none anyconnect mtu 1406 anyconnect ssl keepalive 20 anyconnect ssl rekey time 4 anyconnect ssl rekey method new-tunnel anyconnect dpd-interval client 30 anyconnect dpd-interval gateway 30 anyconnect ssl compression none anyconnect dtls compression none anyconnect profiles none anyconnect ssl df-bit-ignore disable always-on-vpn profile-setting
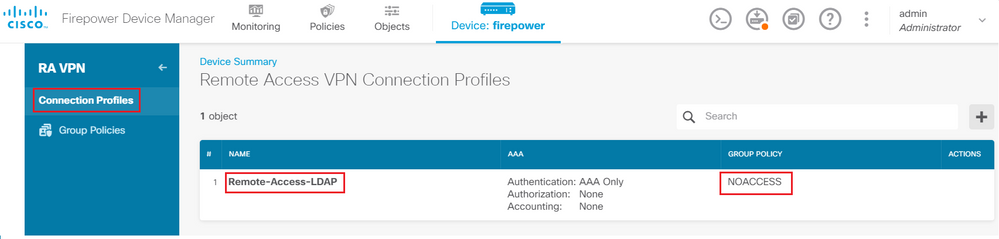
Step 7. Navigate to Connection Profiles and create a Connection-Profile. In this example the profile name is Remote-Access-LDAP. Choose Primary Identity Source AAA Only and create a new Authentication Server type AD.
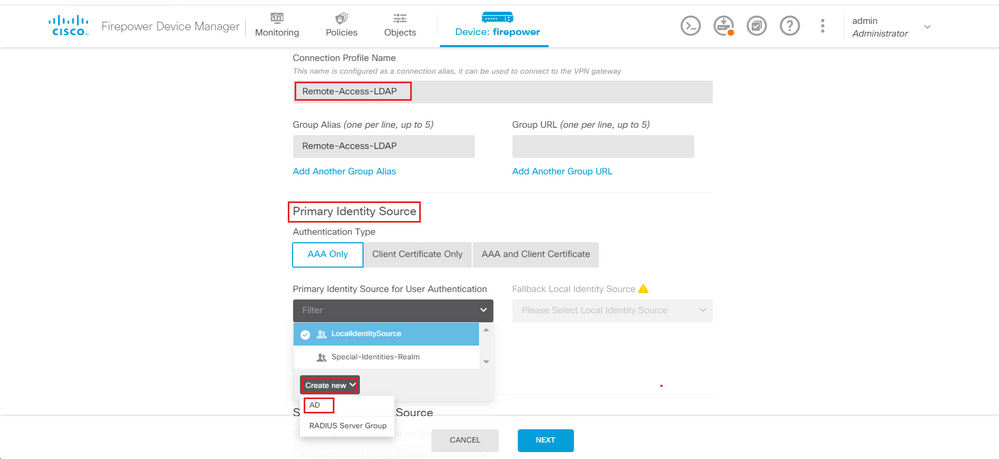
Enter the information of the AD server:
- Directory Username
- Directory Passowrd
- Base DN
- AD Primary Domain
- Hostname / IP Address
- Port
- Encryption type
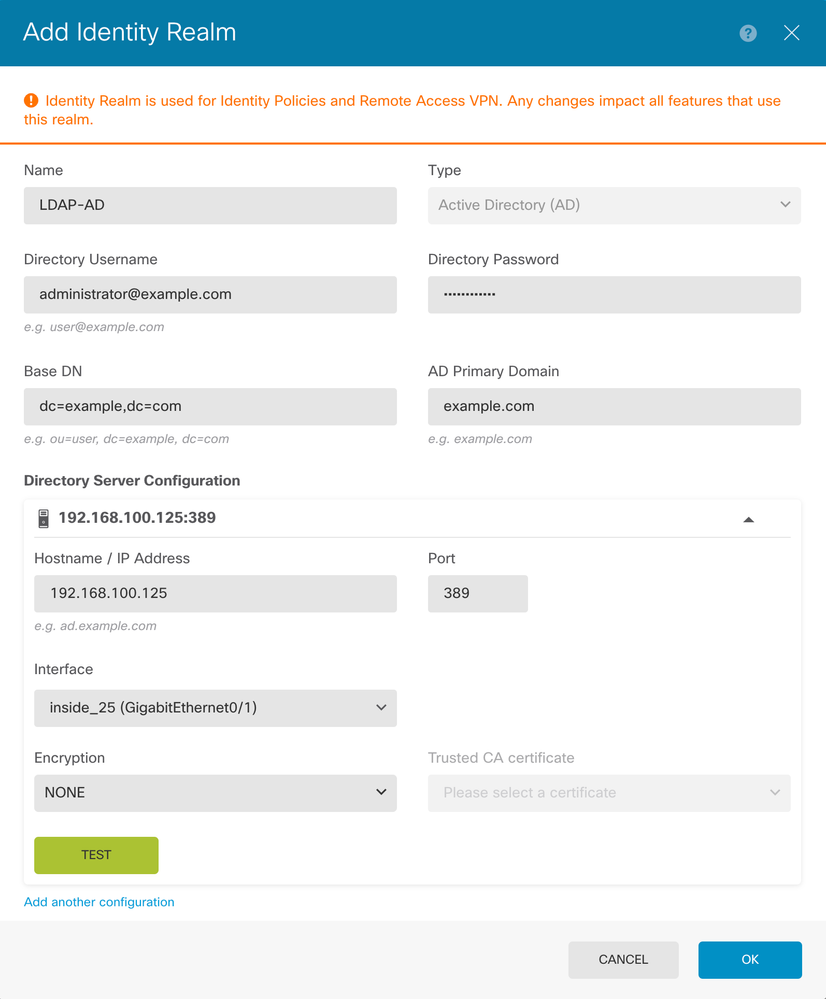
Click on Next and choose NOACCESS as the default Group-Policy for this connection profile.
Save All changes. The connection profile Remote-Access-LDAP is now be visible under RA VPN configuration.
Configuration Steps for LDAP Attribute Map
Step 1. Launch the API Explorer of the FTD.
The API Explorer contains the entire list of API available on the FTD. Navigate to https://<FTD Management IP>/api-explorer
Scroll down to the LdapAttributeMap section and click on it to see all the supported options.
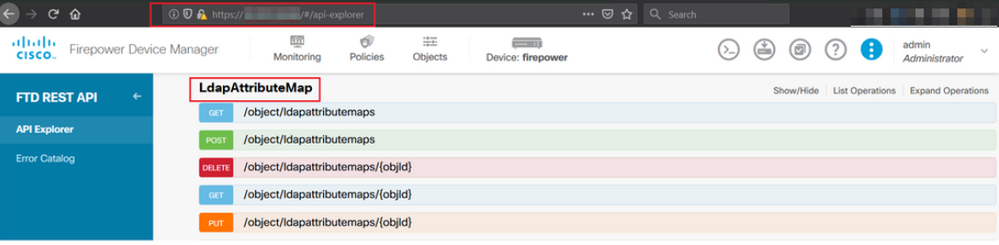
Note: In this example, we use Postman as the API Tool to configure LDAP Attribute Map.
Step 2.Add a Postman collection for LDAP Authorization.
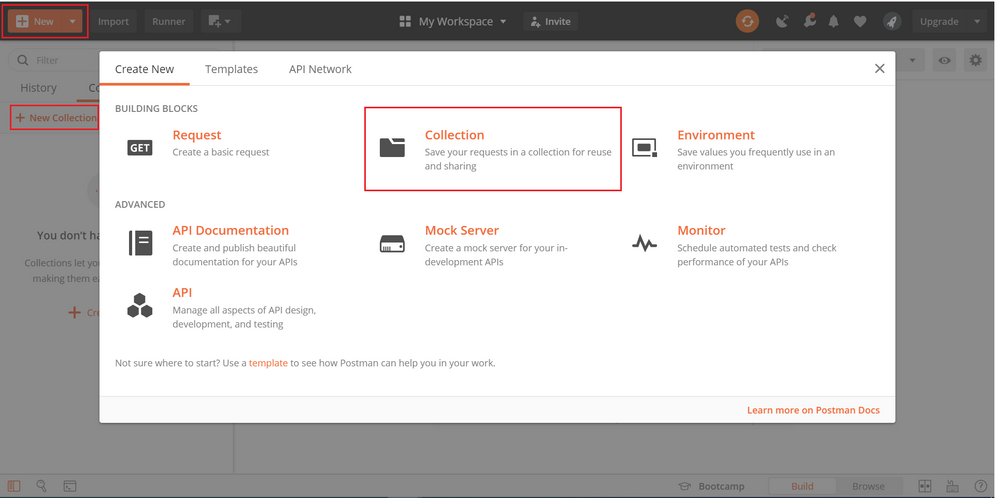
Enter a name for this collection.
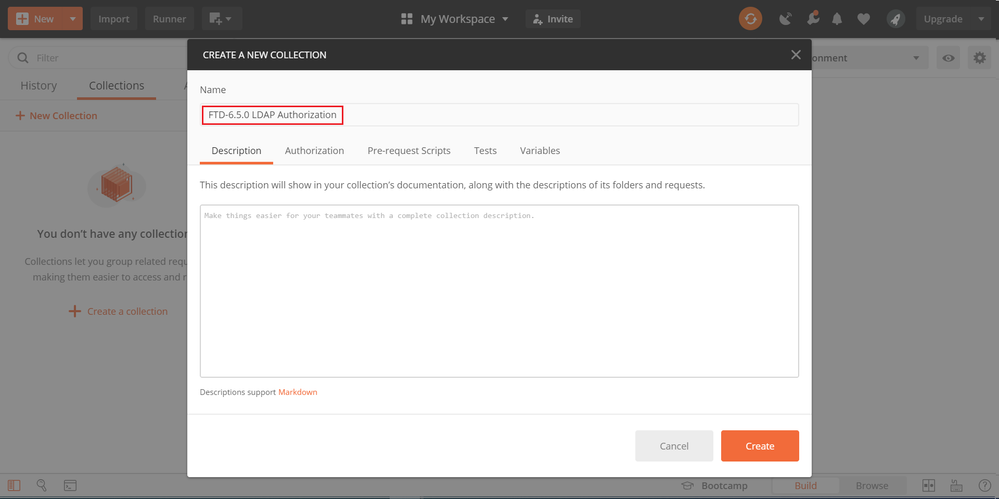
Edit the Authorization tab and select the type OAuth 2.0
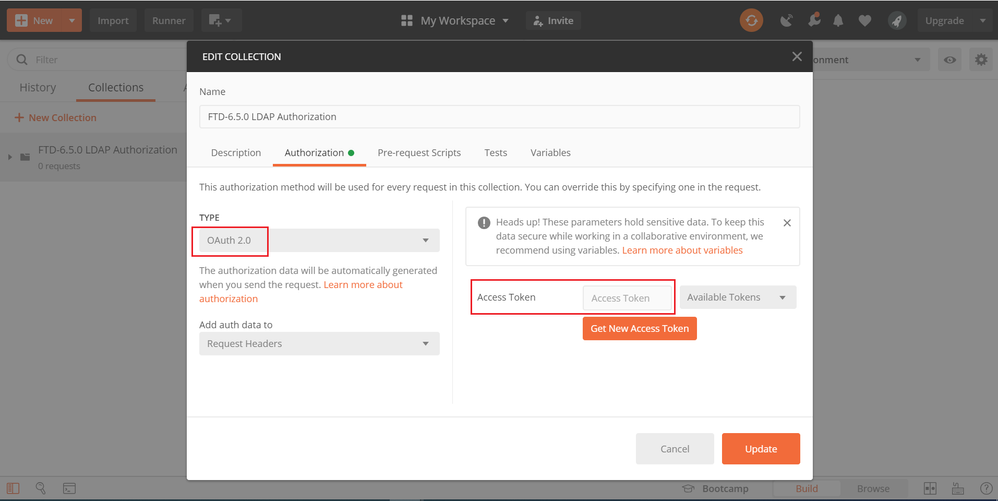
Ste 3. Navigate to File > Settings, turn off the SSL certificate verification to avoid a SSL handshake failure when sending API requests to the FTD. This is done if the FTD uses a self-signed certificate.
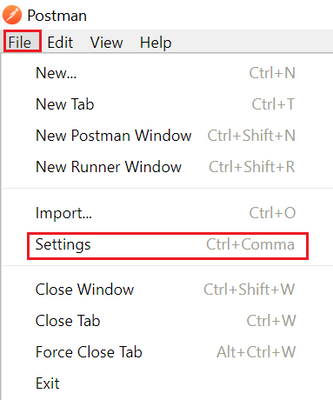
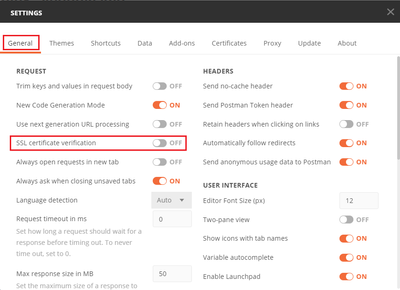
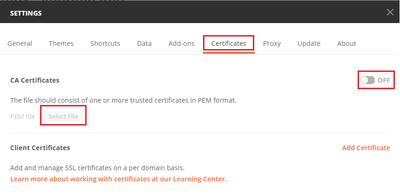
Alternatively, the certificate used by the FTD can be added as a CA certificate in the Certificate section of the Settings.
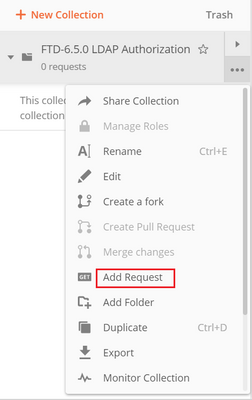
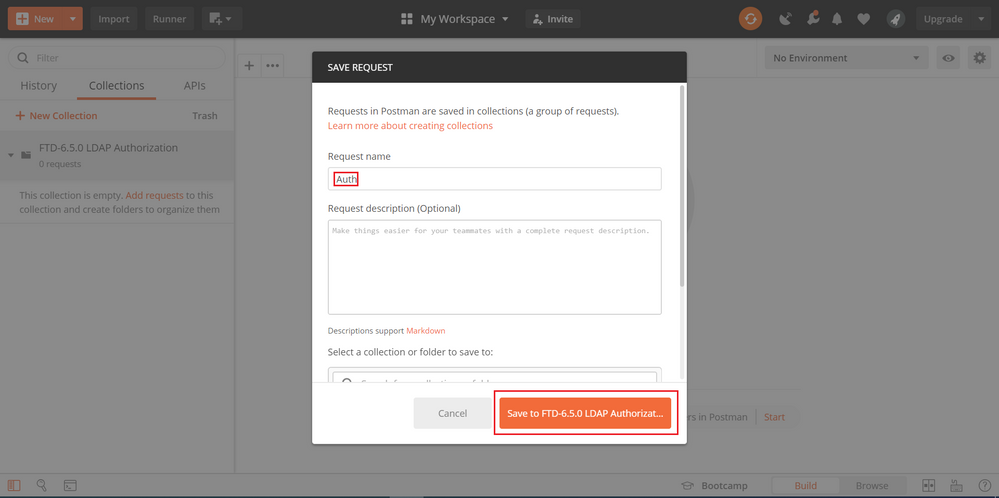
Step 4. Add a new POST request Auth to create a login POST request to the FTD, in order to get the token to authorize any POST/GET requests.
All Postman requests for this collection must contain the next:
BaseURL: https://<FTD Management IP>/api/fdm/latest/
In the request URL, append the base URL with the respective objects that need to be added or modified.
Here, an authentication request for a token is created, referred from https://<FTD Management IP>/api-explorer. This needs to be checked for other objects and the necessary changes need to be made for them.
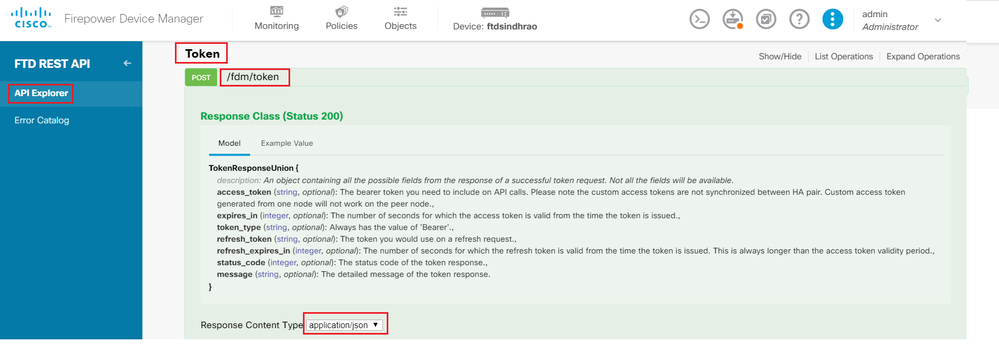
Navigate to Headers and click on Manage Presets.
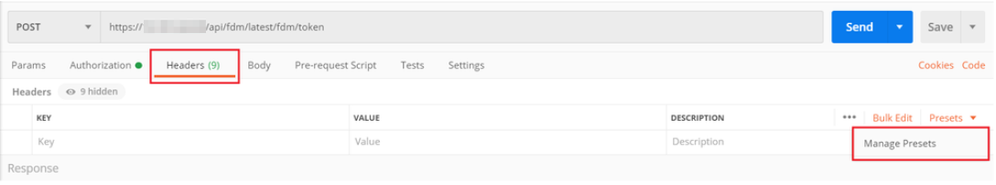
Crate a new Preset Header-LDAP and add the below Key-Value pair:
| Content-Type | application/json |
| Accept | application/json |
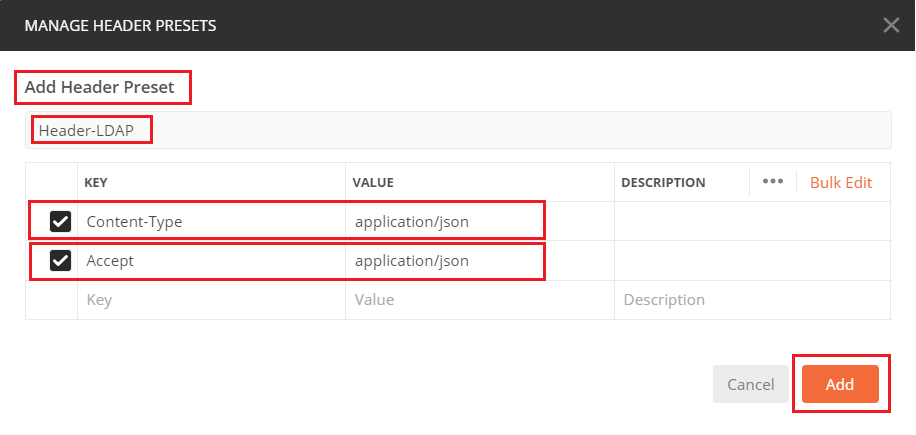
For all other requests, navigate to respective Header tabs and select this Preset Header value: Header-LDAP for the REST API requests to use json as the primary data type.
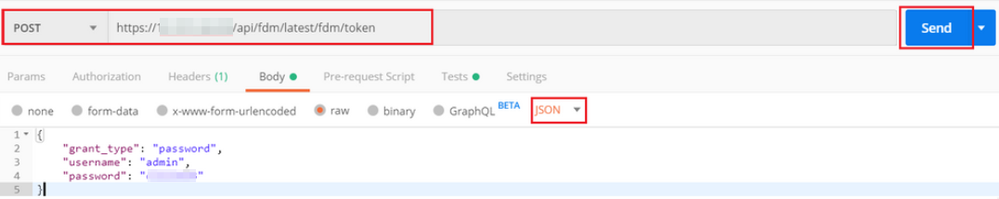
The Body of the POST Request to get the token must contain the next:
| Type | raw - JSON (application/json) |
| grant_type | password |
| username | Admin Username in order to log in to the FTD |
| password | Password associated with the admin user account |
{
"grant_type": "password",
"username": "admin",
"password": "<enter the password>"
}
Once you click send, the body of the response contains the access token which is used in order to send any PUT/GET/POST requests to the FTD.
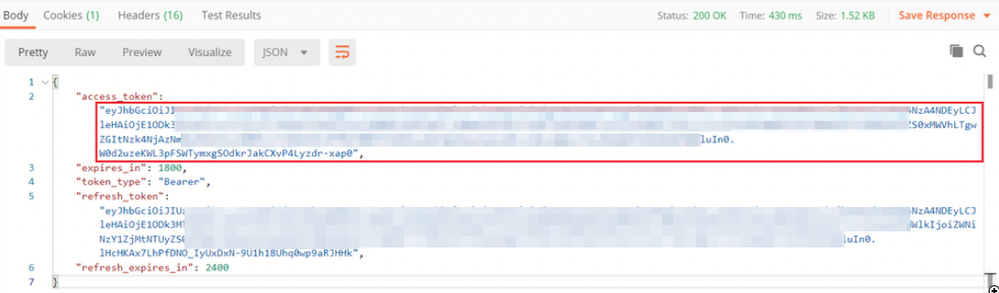
{
"access_token": "eyJhbGciOiJIUzI1[...output omitted...]dkrJakCXvP4Lyzdr-xap0",
"expires_in": 1800,
"token_type": "Bearer",
"refresh_token":"eyJhbGciOiJIUzI1[...output omitted...]dkrJakCXvP4Lyzdr-xap0",
"refresh_expires_in": 2400
}
This token is then used to authorize all subsequent requests.
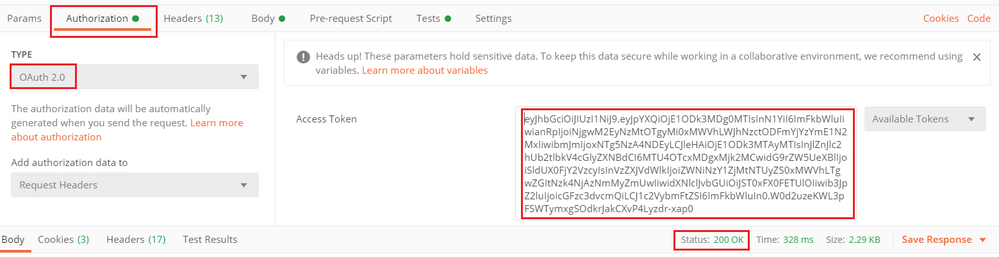
Navigate to Authorization tab of every new request and select the next:
| Type | OAuth 2.0 |
| Token | The access token received by running the Log In POST Request |
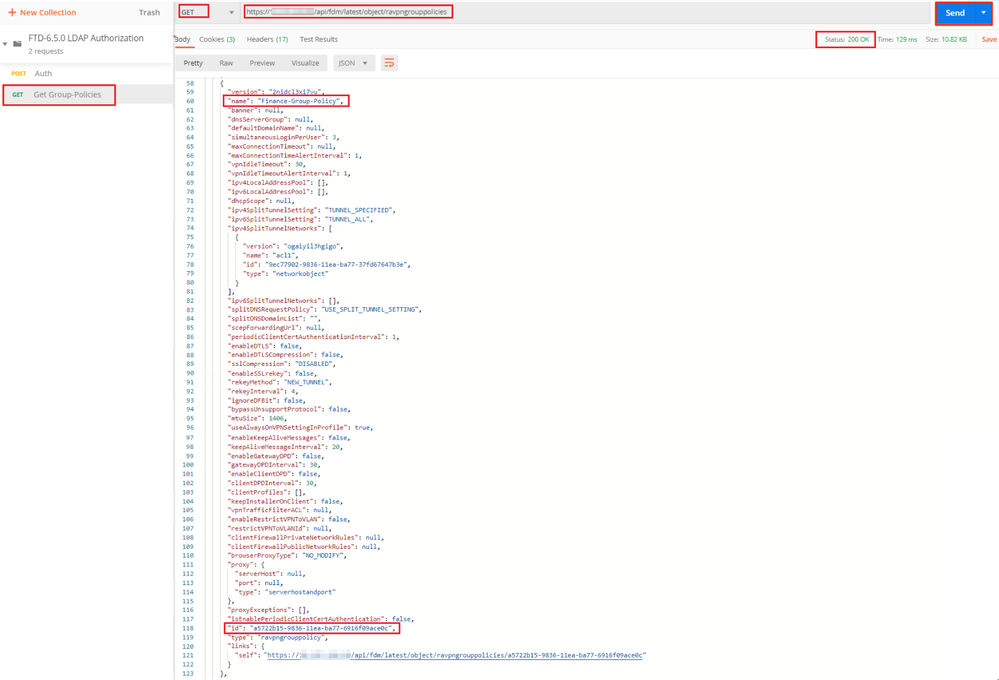
Step 5. Add a new GET request Get Group-Policies to get the Group-Policy status and settings. Collect the name and id for each configured Group-Policy (in this example: Finance-Group-Policy, HR-Group-Policy and IT-Group-Policy) to use in the next step.
The URL to get the configured Group-Policies is: https://<FTD Management IP>/api/fdm/latest/object/ravpngrouppolicies
In the next example, Group-Policy Finance-Group-Policy is highlighted.
Step 6. Add a new POST request Create LDAP Attribute Map to create the LDAP Attribute Map. In this document, the model LdapAttributeMapping is used. Other models also have similar operations and methods to create Attribute map. Examples for these models is available in the api-explorer as mentioned earlier in this document.
The URL to POST the LDAP Attribute Map is: https://<FTD Management IP>/api/fdm/latest/object/ldapattributemaps
The body of POST request must contain the following:
| name | Name for LDAP Attribute-Map |
| type | ldapattributemapping |
| ldapName | memberOf |
| ciscoName | GROUP_POLICY |
| ldapValue | memberOf value for User from AD |
| ciscoValue | Group-Policy name for each User Group in FDM |
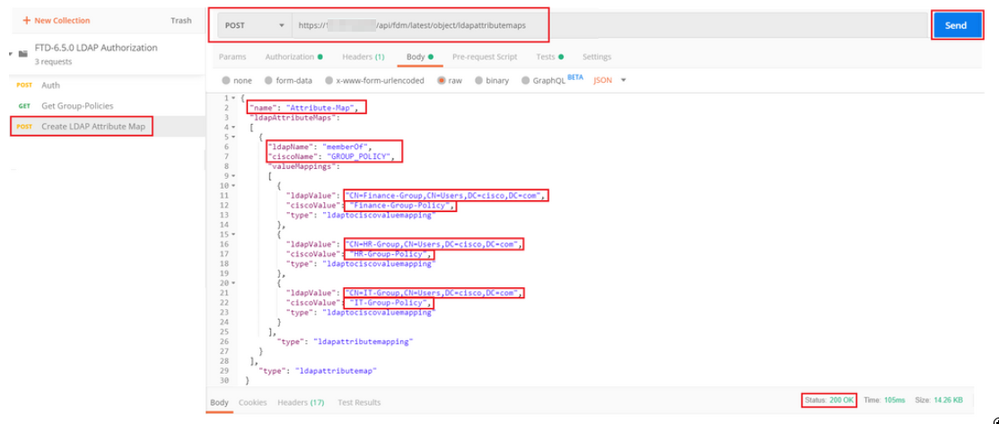
The body of the POST request contains the LDAP Attribute map information that maps a specific Group-Policy to an AD group based on the memberOf value:
{
"name": "Attribute-Map",
"ldapAttributeMaps":
[
{
"ldapName": "memberOf",
"ciscoName": "GROUP_POLICY",
"valueMappings":
[
{
"ldapValue": "CN=Finance-Group,CN=Users,DC=cisco,DC=com",
"ciscoValue": "Finance-Group-Policy",
"type": "ldaptociscovaluemapping"
},
{
"ldapValue": "CN=HR-Group,CN=Users,DC=cisco,DC=com",
"ciscoValue": "HR-Group-Policy",
"type": "ldaptociscovaluemapping"
},
{
"ldapValue": "CN=IT-Group,CN=Users,DC=cisco,DC=com",
"ciscoValue": "IT-Group-Policy",
"type": "ldaptociscovaluemapping"
}
],
"type": "ldapattributemapping"
}
],
"type": "ldapattributemap"
}
Note: The memberOf field can be retrived from AD server with the dsquery command or can be fetched from the LDAP debugs on the FTD. In the debug logs, look for memberOf value: field.
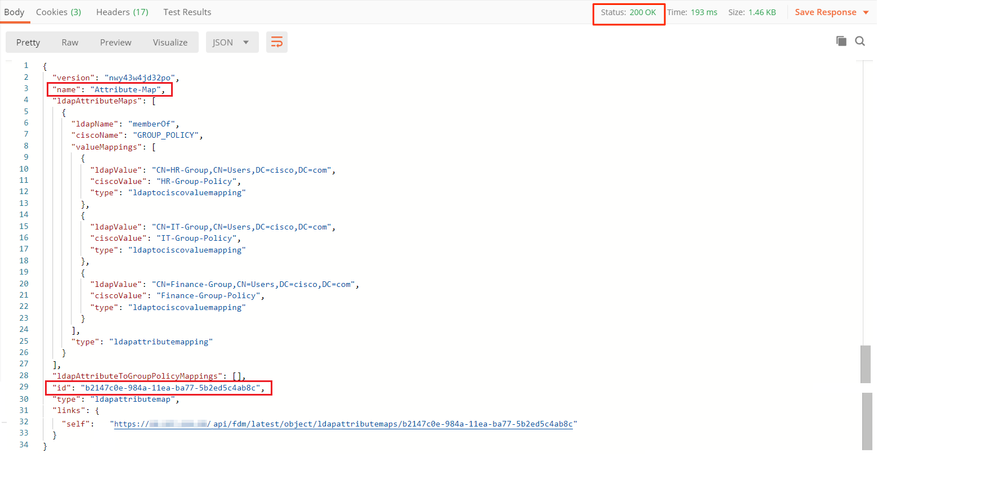
The Response of this POST request looks similar to the next ouput:
Step 7. Add a new GET request to obtain the current AD realm configuration on FDM.
The URL to get the current AD realm configuration is: https://<FTD Management IP>/api/fdm/latest/object/realms
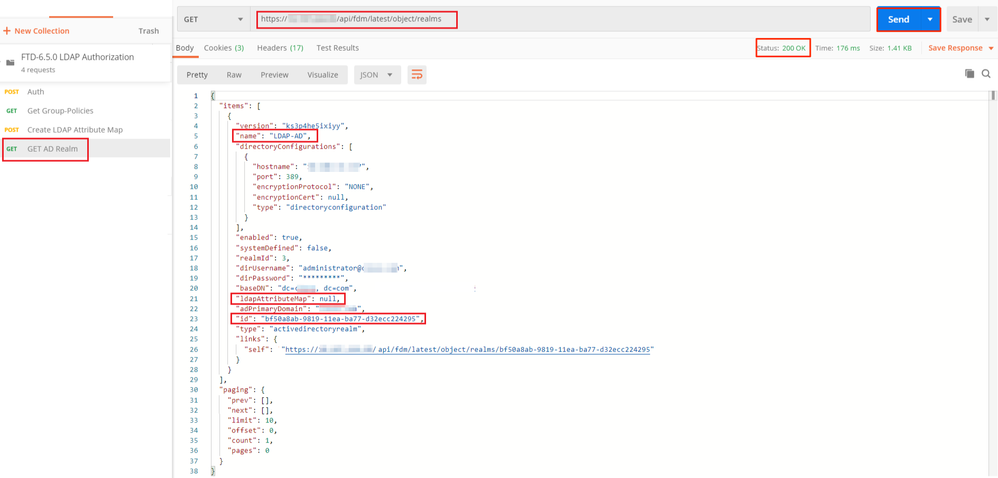
Notice that the value for key ldapAttributeMap is null.
Step 8. Create a new PUT request to edit the AD Realm. Copy the GET response output from previous step and add it to the Body of this new PUT request. This step can be used to make any modifications to the current AD Realm setup, for example: change password, IP address or add new value for any key like ldapAttributeMap in this case.
Note: It is important to copy the contents of the item list rather than the whole GET response output. The Request URL for the PUT request has to be appended with the item id of the object for which changes are made. In this example, the value is: bf50a8ab-9819-11ea-ba77-d32ecc224295
The URL to edit the current AD realm configuration is: https://<FTD Management IP>/api/fdm/latest/object/realms/<realm ID>
The body of the PUT request must contain the following :
| version | version obtained from response of previous GET request |
| id | id obtained from response of previous GET request |
| ldapAttributeMap | ldap-id from Response of Create LDAP Attribute Map request |
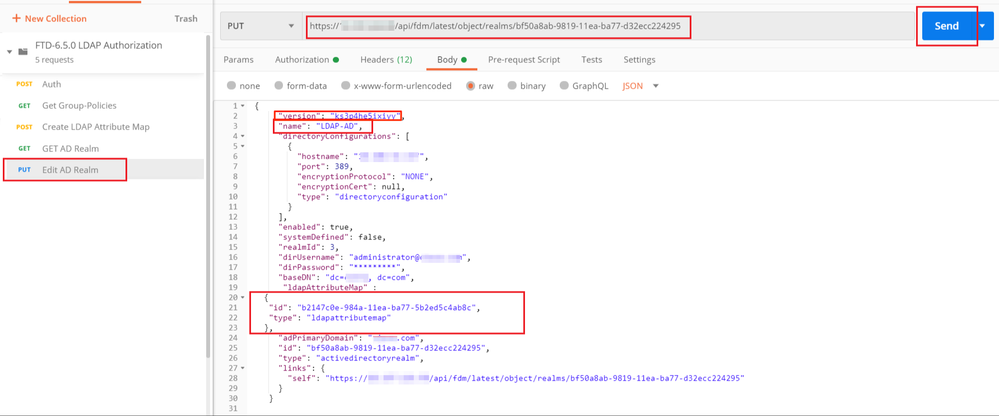
The body for the configuration in this example is:
{
"version": "ks3p4he5ixiyy",
"name": "LDAP-AD",
"directoryConfigurations": [
{
"hostname": "<IP Address>",
"port": 389,
"encryptionProtocol": "NONE",
"encryptionCert": null,
"type": "directoryconfiguration"
}
],
"enabled": true,
"systemDefined": false,
"realmId": 3,
"dirUsername": "administrator@example.com",
"dirPassword": "*********",
"baseDN": "dc=example, dc=com",
"ldapAttributeMap" :
{
"id": "b2147c0e-984a-11ea-ba77-5b2ed5c4ab8c",
"type": "ldapattributemap"
},
"adPrimaryDomain": "example.com",
"id": "bf50a8ab-9819-11ea-ba77-d32ecc224295",
"type": "activedirectoryrealm",
"links": {
"self": "https://<FTD Management IP Address>/api/fdm/latest/object/realms/bf50a8ab-9819-11ea-ba77-d32ecc224295"
}
}Verify that the ldapAttributeMap id matches in the Response Body for this request.
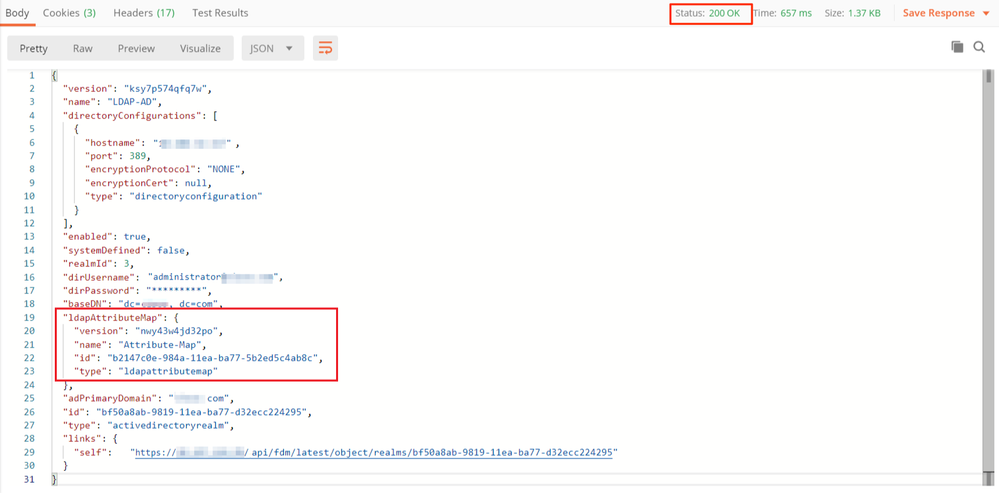
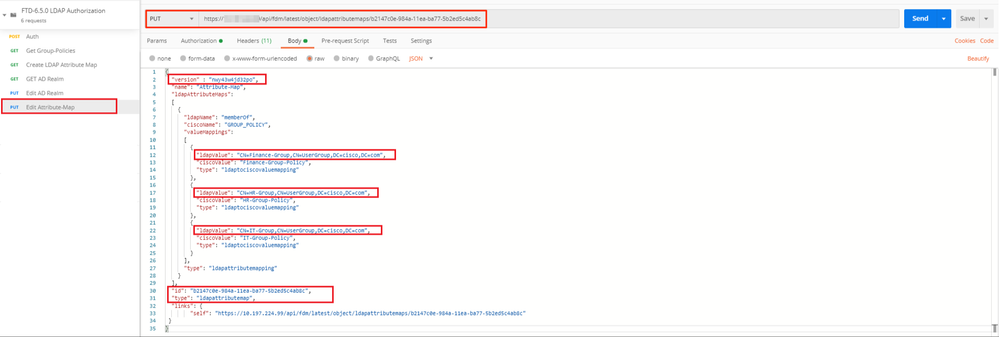
(Optional). The LDAP attribute map can be modified with PUT requests. Create a new PUT request Edit Attribute-Map and make any changes like the name of the Attribute-Map or memeberOf value. T
In the next example, the value of ldapvalue has been modified from CN=Users to CN=UserGroup for all three groups.
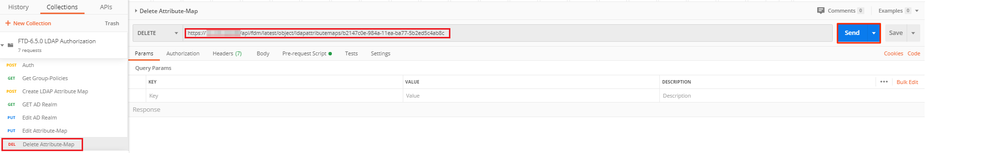
(Optional). To delete an existing LDAP Attribute-Map, create a DELETE Request Delete Attribute-Map. Include the map-id from the previous HTTP response and append with the base URL of the delete request.
Note: If the memberOf attribute contains spaces, it must be URL encoded for the Web Server to parse it. Otherwise a 400 Bad Request HTTP Response is received. For string containing white-spaces spaces, either "%20" or "+" can be used to avoid this error.
Step 9. Navigate back to FDM, select the Deployment icon and click on Deploy Now.
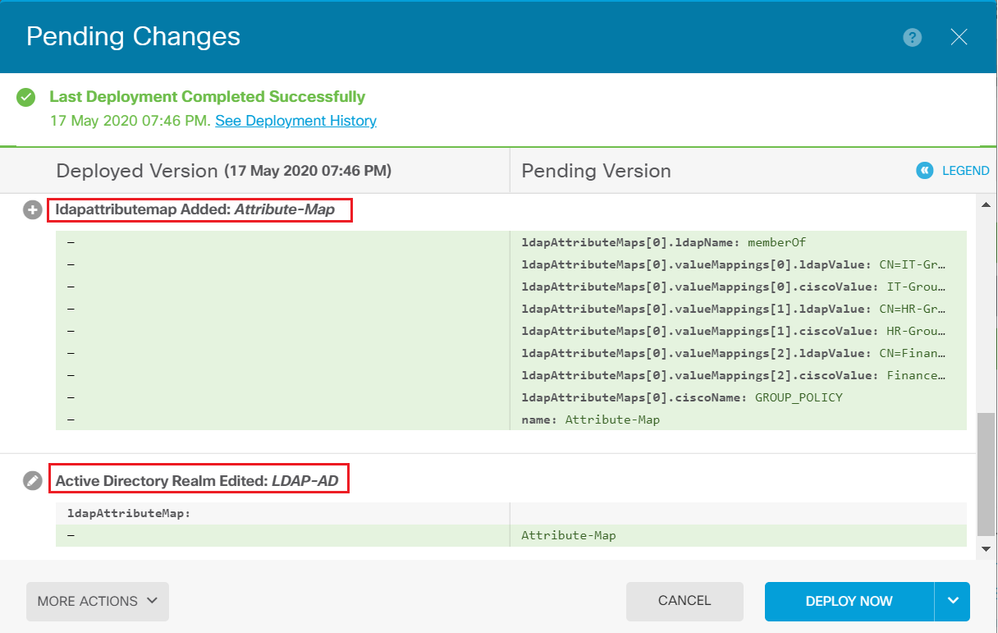
Verify
The deployment changes can be verified in the Deployment History section of the FDM.
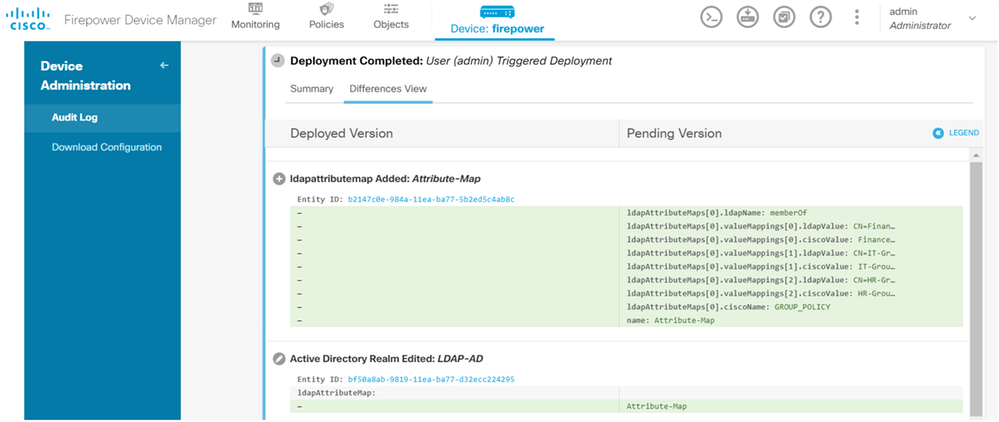
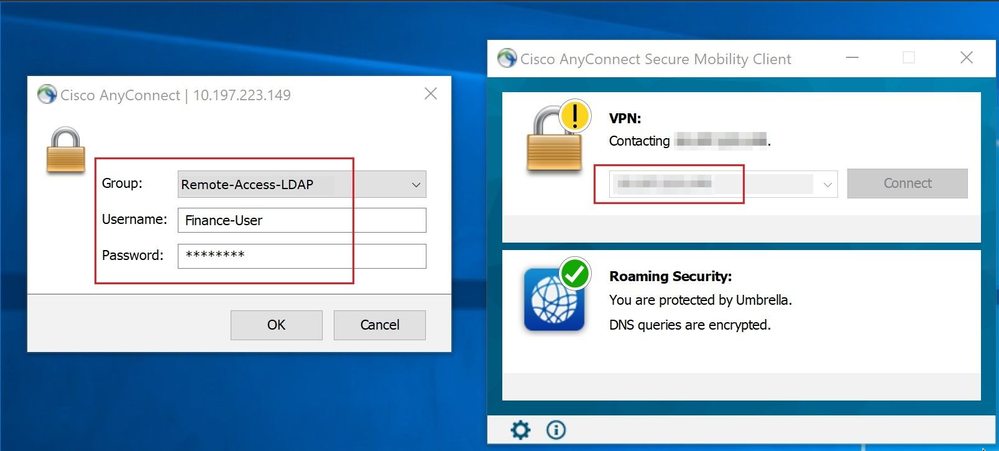
In order to test this configuration, provide the AD credentials in Username and Password fields.
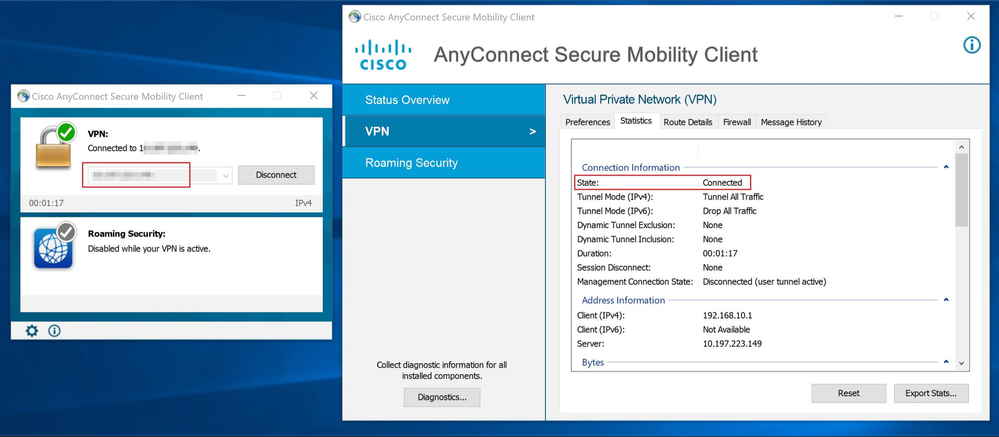
When a user that belongs to the AD group Finance-Group tries to log in, the attempt is successful as expected.
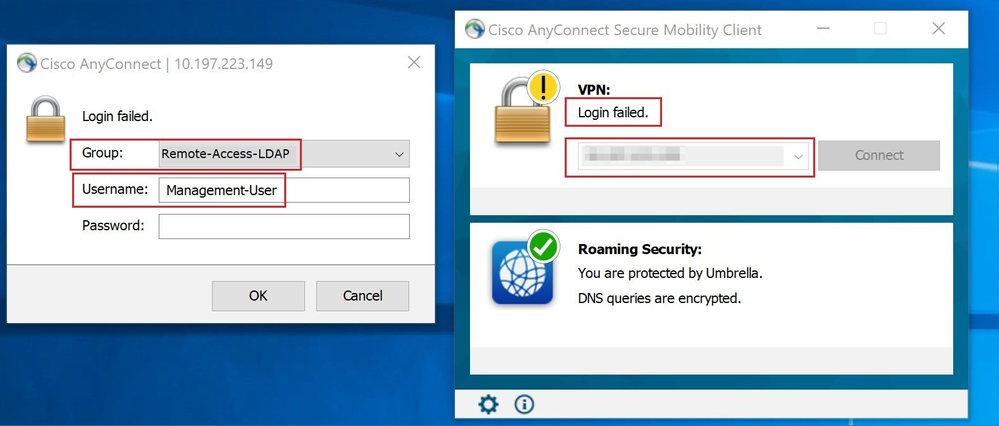
When a user that belongs to the Management-Group in AD tries to connect to Connection-Profile Remote-Access-LDAP, since no LDAP Attribute Map returned a match, the Group-Policy inherited by this user on the FTD is NOACCESS which has vpn-simultaneous-logins set to value 0. Hence, the login attempt for this user fails.
The configuration can be verified with the next show commands from the FTD CLI:
firepower# show vpn-sessiondb anyconnect Session Type: AnyConnect Username : Finance-User Index : 26 Assigned IP : 192.168.10.1 Public IP : 10.1.1.1 Protocol : AnyConnect-Parent SSL-Tunnel License : AnyConnect Premium Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 Bytes Tx : 22491197 Bytes Rx : 14392 Group Policy : Finance-Group-Policy Tunnel Group : Remote-Access-LDAP Login Time : 11:14:43 UTC Sat Oct 12 2019 Duration : 0h:02m:09s Inactivity : 0h:00m:00s VLAN Mapping : N/A VLAN : none Audt Sess ID : 000000000001a0005da1b5a3 Security Grp : none Tunnel Zone : 0
firepower# show run aaa-server LDAP-AD aaa-server LDAP-AD protocol ldap realm-id 3 aaa-server AD1 host 192.168.1.1 server-port 389 ldap-base-dn dc=example, dc=com ldap-scope subtree ldap-login-password ***** ldap-login-dn Administrator@example.com server-type auto-detect ldap-attribute-map Attribute-Map
firepower# show run ldap attribute-map ldap attribute-map Attribute-Map map-name memberOf Group-Policy map-value memberOf CN=Finance-Group,CN=Users,DC=cisco,DC=com Finance-Group-Policy map-value memberOf CN=HR-Group,CN=Users,DC=cisco,DC=com HR-Group-Policy map-value memberOf CN=IT-Group,CN=Users,DC=cisco,DC=com IT-Group-Policy
Troubleshoot
One of the most common issues with configuring REST API is to renew the bearer token from time to time. The token expiry time is given in the Response for the Auth request. If this time expires, an additonal refresh token can be used for a longer time. After the refresh token also expires, a new Auth request has to be sent to retreived a new access token.
Note: Refer to Important Information on Debug Commands before you use debug commands.
You can set various debug levels. By default, level 1 is used. If you change the debug level, the verbosity of the debugs might increase. Do this with caution, especially in production environments.
The following debugs on the FTD CLI would be helpful in troubleshooting problems related to LDAP Attribute Map
debug ldap 255
debug webvpn condition user <username> debug webvpn anyconnect 255
debug aaa common 127
In this example. the next debugs were collected to demonstrate the information received from the AD server when the test users mentioned before connected.
LDAP debugs for Finance-User:
[48] Session Start
[48] New request Session, context 0x00002b0482c2d8e0, reqType = Authentication
[48] Fiber started
[48] Creating LDAP context with uri=ldap://192.168.1.1:389
[48] Connect to LDAP server: ldap://192.168.1.1:389, status = Successful
[48] supportedLDAPVersion: value = 3
[48] supportedLDAPVersion: value = 2
[48] LDAP server192.168.1.1 is Active directory
[48] Binding as Administrator@cisco.com
[48] Performing Simple authentication for Administrator@example.com to192.168.1.1
[48] LDAP Search:
Base DN = [dc=cisco, dc=com]
Filter = [sAMAccountName=Finance-User]
Scope = [SUBTREE]
[48] User DN = [CN=Finance-User,OU=Finance,OU=VPN,DC=cisco,DC=com]
[48] Talking to Active Directory server 192.168.1.1
[48] Reading password policy for Finance-User, dn:CN=Finance-User,OU=Finance,OU=VPN,DC=cisco,DC=com
[48] Read bad password count 0
[48] Binding as Finance-User
[48] Performing Simple authentication for Finance-User to 192.168.1.1
[48] Processing LDAP response for user Finance-User
[48] Message (Finance-User):
[48] Authentication successful for Finance-User to 192.168.1.1
[48] Retrieved User Attributes:
[48] objectClass: value = top
[48] objectClass: value = person
[48] objectClass: value = organizationalPerson
[48] objectClass: value = user
[48] cn: value = Finance-User
[48] givenName: value = Finance-User
[48] distinguishedName: value = CN=Finance-User,OU=Finance,OU=VPN,DC=cisco,DC=com
[48] instanceType: value = 4
[48] whenCreated: value = 20191011094454.0Z
[48] whenChanged: value = 20191012080802.0Z
[48] displayName: value = Finance-User
[48] uSNCreated: value = 16036
[48] memberOf: value = CN=Finance-Group,CN=Users,DC=cisco,DC=com
[48] mapped to Group-Policy: value = Finance-Group-Policy
[48] mapped to LDAP-Class: value = Finance-Group-Policy
[48] memberOf: value = CN=Users,CN=Builtin,DC=cisco,DC=com
[48] mapped to Group-Policy: value = CN=Users,CN=Builtin,DC=cisco,DC=com
[48] mapped to LDAP-Class: value = CN=Users,CN=Builtin,DC=cisco,DC=com
[48] uSNChanged: value = 16178
[48] name: value = Finance-User
[48] objectGUID: value = .J.2...N....X.OQ
[48] userAccountControl: value = 512
[48] badPwdCount: value = 0
[48] codePage: value = 0
[48] countryCode: value = 0
[48] badPasswordTime: value = 0
[48] lastLogoff: value = 0
[48] lastLogon: value = 0
[48] pwdLastSet: value = 132152606948243269
[48] primaryGroupID: value = 513
[48] objectSid: value = .............B...a5/ID.dT...
[48] accountExpires: value = 9223372036854775807
[48] logonCount: value = 0
[48] sAMAccountName: value = Finance-User
[48] sAMAccountType: value = 805306368
[48] userPrincipalName: value = Finance-User@cisco.com
[48] objectCategory: value = CN=Person,CN=Schema,CN=Configuration,DC=cisco,DC=com
[48] dSCorePropagationData: value = 20191011094757.0Z
[48] dSCorePropagationData: value = 20191011094614.0Z
[48] dSCorePropagationData: value = 16010101000000.0Z
[48] lastLogonTimestamp: value = 132153412825919405
[48] Fiber exit Tx=538 bytes Rx=2720 bytes, status=1
[48] Session EndLDAP debugs for Management-User:
[51] Session Start
[51] New request Session, context 0x00002b0482c2d8e0, reqType = Authentication
[51] Fiber started
[51] Creating LDAP context with uri=ldap://192.168.1.1:389
[51] Connect to LDAP server: ldap://192.168.1.1:389, status = Successful
[51] supportedLDAPVersion: value = 3
[51] supportedLDAPVersion: value = 2
[51] LDAP server 192.168.1.1 is Active directory
[51] Binding as Administrator@cisco.com
[51] Performing Simple authentication for Administrator@example.com to 192.168.1.1
[51] LDAP Search:
Base DN = [dc=cisco, dc=com]
Filter = [sAMAccountName=Management-User]
Scope = [SUBTREE]
[51] User DN = [CN=Management-User,OU=Management,OU=VPN,DC=cisco,DC=com]
[51] Talking to Active Directory server 192.168.1.1
[51] Reading password policy for Management-User, dn:CN=Management-User,OU=Management,OU=VPN,DC=cisco,DC=com
[51] Read bad password count 0
[51] Binding as Management-User
[51] Performing Simple authentication for Management-User to 192.168.1.1
[51] Processing LDAP response for user Management-User
[51] Message (Management-User):
[51] Authentication successful for Management-User to 192.168.1.1
[51] Retrieved User Attributes:
[51] objectClass: value = top
[51] objectClass: value = person
[51] objectClass: value = organizationalPerson
[51] objectClass: value = user
[51] cn: value = Management-User
[51] givenName: value = Management-User
[51] distinguishedName: value = CN=Management-User,OU=Management,OU=VPN,DC=cisco,DC=com
[51] instanceType: value = 4
[51] whenCreated: value = 20191011095036.0Z
[51] whenChanged: value = 20191011095056.0Z
[51] displayName: value = Management-User
[51] uSNCreated: value = 16068
[51] memberOf: value = CN=Management-Group,CN=Users,DC=cisco,DC=com
[51] mapped to Group-Policy: value = CN=Management-Group,CN=Users,DC=cisco,DC=com
[51] mapped to LDAP-Class: value = CN=Management-Group,CN=Users,DC=cisco,DC=com
[51] memberOf: value = CN=Users,CN=Builtin,DC=cisco,DC=com
[51] mapped to Group-Policy: value = CN=Users,CN=Builtin,DC=cisco,DC=com
[51] mapped to LDAP-Class: value = CN=Users,CN=Builtin,DC=cisco,DC=com
[51] uSNChanged: value = 16076
[51] name: value = Management-User
[51] objectGUID: value = i._(.E.O.....Gig
[51] userAccountControl: value = 512
[51] badPwdCount: value = 0
[51] codePage: value = 0
[51] countryCode: value = 0
[51] badPasswordTime: value = 0
[51] lastLogoff: value = 0
[51] lastLogon: value = 0
[51] pwdLastSet: value = 132152610365026101
[51] primaryGroupID: value = 513
[51] objectSid: value = .............B...a5/ID.dW...
[51] accountExpires: value = 9223372036854775807
[51] logonCount: value = 0
[51] sAMAccountName: value = Management-User
[51] sAMAccountType: value = 805306368
[51] userPrincipalName: value = Management-User@cisco.com
[51] objectCategory: value = CN=Person,CN=Schema,CN=Configuration,DC=cisco,DC=com
[51] dSCorePropagationData: value = 20191011095056.0Z
[51] dSCorePropagationData: value = 16010101000000.0Z
[51] Fiber exit Tx=553 bytes Rx=2688 bytes, status=1
[51] Session EndRelated Information
For additional assistance, please contact Cisco Technical Assistance Center (TAC). A valid support contract is required: Cisco Worldwide Support Contacts.
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
07-Jul-2023 |
Initial Release |
Contributed by Cisco Engineers
- Tazy KhanTAC Engineer
- Sindhuja RaoTAC Engineer
- Angel OrtizTechnical Leader
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback