Introduction
This document describes how to configure Windows Browser proxies for Cisco Secure Client connected to FTD Managed by FDM.
Prerequisites
Requirements
Cisco recommends that you have knowledge on these topics:
- Cisco Secure Firewall Device Manager (FDM)
- Cisco Firepower Threat Defense (FTD)
- Cisco Secure Client (CSC)
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Secure Firewall Device Manager Version 7.3
- Cisco Firepower Threat Defense Virtual Appliance Version 7.3
- Cisco Secure Client Version 5.0.02075
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
The term "proxy" refers to a service that is located between the user and the resource you want to reach. Web browser proxies, specifically, are servers that transmit web traffic so, when navigating to a website, the Secure Client prompts the proxy server to request the site instead of doing it directly.
Proxies can be used to achieve different objectives such as content filtering, traffic handling, and traffic tunneling.
Configure
Configurations
In this document, it is assumed that you already have a working Remote Access VPN configuration.
In the FDM, navigate to Remote Access VPN > Group Policies, click the Edit button on the Group Policy where you want to configure the browser proxy, and navigate to the Windows Browser Proxy section.
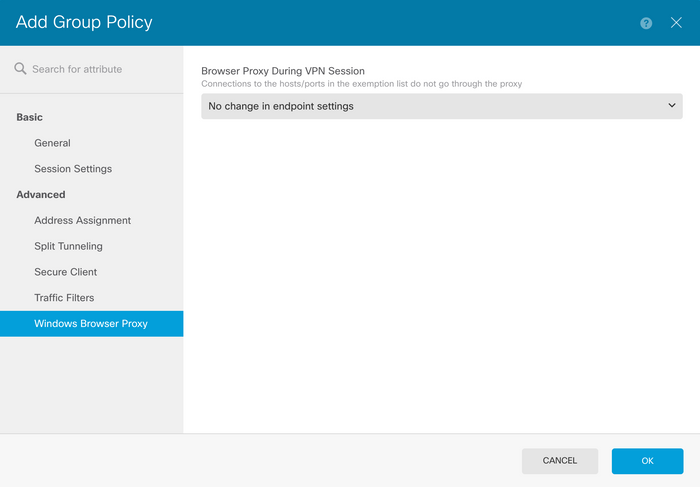
From the Browser Proxy During VPN Session dropdown, select Use custom settings.
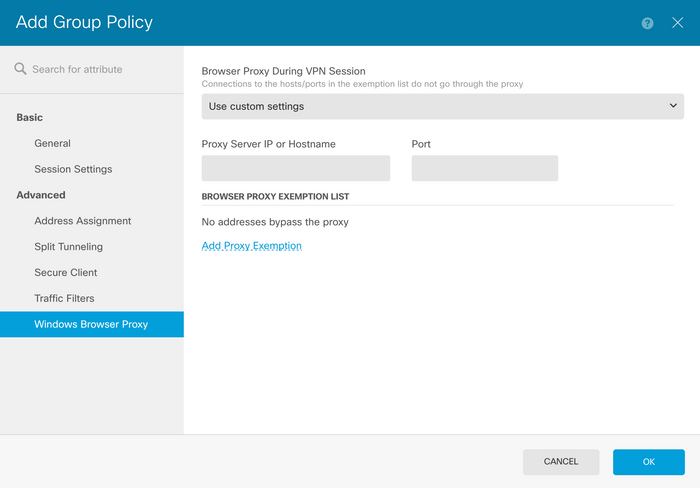
On the Proxy Server IP or Hostname box, enter the proxy server information and on the Port box, enter the port to reach the server.
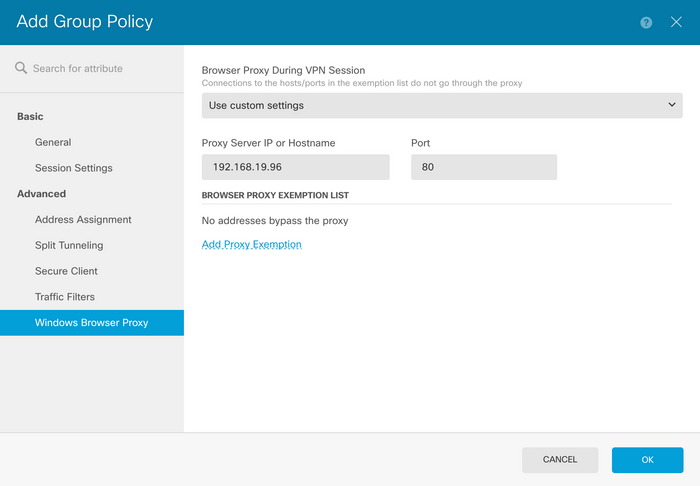
If there is an address or hostname that you do not want to reach through the proxy, click the Add Proxy Exemption button and add it here.

Note: Specifying a port on the Browser Proxy Exemption List is optional.
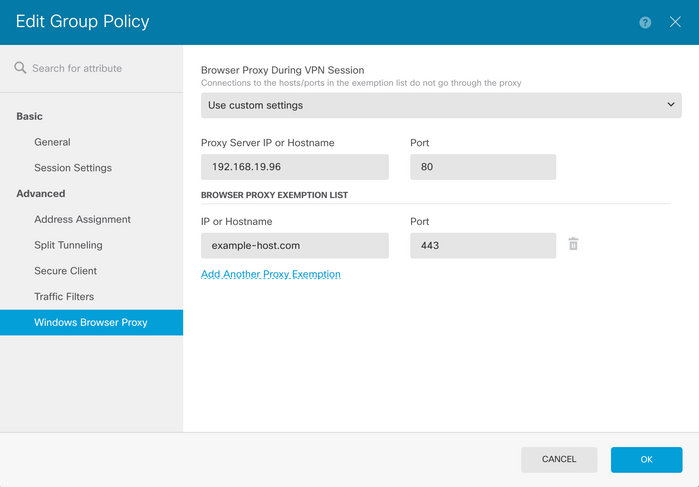
Click Ok and deploy the configuration.
Verify
To verify if the configuration was applied successfuly, you can use the CLI of the FTD.
firepower# show running-config group-policy
group-policy ProxySettings internal
group-policy ProxySettings attributes
dns-server value 10.28.28.1
dhcp-network-scope none
vpn-simultaneous-logins 3
vpn-idle-timeout 30
vpn-idle-timeout alert-interval 1
vpn-session-timeout none
vpn-session-timeout alert-interval 1
vpn-filter none
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelall
ipv6-split-tunnel-policy tunnelall
split-dns none
split-tunnel-all-dns disable
client-bypass-protocol disable
msie-proxy server value 192.168.19.96:80
msie-proxy method use-server
msie-proxy except-list value example-host.com:443
msie-proxy local-bypass enable
vlan none
address-pools value AC_Pool
ipv6-address-pools none
webvpn
anyconnect ssl dtls none
anyconnect mtu 1406
anyconnect ssl keepalive none
anyconnect ssl rekey time none
anyconnect ssl rekey method none
anyconnect dpd-interval client none
anyconnect dpd-interval gateway none
anyconnect ssl compression none
anyconnect dtls compression none
anyconnect modules none
anyconnect profiles none
anyconnect ssl df-bit-ignore disable
always-on-vpn profile-setting
Troubleshoot
You can collect a DART bundle and verify that the VPN profile has been applied:
******************************************
Date : 07/20/2023
Time : 21:50:08
Type : Information
Source : csc_vpnagent
Description : Current Profile: none
Received VPN Session Configuration Settings:
Keep Installed: enabled
Rekey Method: disabled
Proxy Setting: bypass-local, server
Proxy Server: 192.168.19.96:80
Proxy PAC URL: none
Proxy Exceptions: example-host.com:443
Proxy Lockdown: enabled
IPv4 Split Exclude: disabled
IPv6 Split Exclude: disabled
IPv4 Dynamic Split Exclude: 3 excluded domain(s)
IPv6 Dynamic Split Exclude: disabled
IPv4 Split Include: disabled
IPv6 Split Include: disabled
IPv4 Dynamic Split Include: disabled
IPv6 Dynamic Split Include: disabled
IPv4 Split DNS: disabled
IPv6 Split DNS: disabled
Tunnel all DNS: disabled
IPv4 Local LAN Wildcard: disabled
IPv6 Local LAN Wildcard: disabled
Firewall Rules: none
Client Address: 172.16.28.1
Client Mask: 255.255.255.0
Client IPv6 Address: FE80:0:0:0:ADSD:3F37:374D:3141 (auto-generated)
Client IPv6 Mask: FFFF:FFFF:FFFF:FFFF:FFFF:FFFF:FFFF:FFFC
TLS MTU: 1399
TLS Compression: disabled
TLS Keep Alive: disabled
TLS Rekey Interval: none
TLS DPD: 0 seconds
DTLS: disabled
DTLS MTU: none
DTLS Compression: disabled
DTLS Keep Alive: disabled
DTLS Rekey Interval: none
DTLS DPD: 30 seconds
Session Timeout: none
Session Timeout Alert Interval: 60 seconds
Session Timeout Remaining: none
Disconnect Timeout: 1800 seconds
Idle Timeout: 1800 seconds
Server: ASA (9.19(1))
MUS Host: unknown
DAP User Message: n
Quarantine State: disabled
Always On VPN: not disabled
Lease Duration: 1209600 seconds
Default Domain: unknown
Home page: unknown
Smart Card Removal Disconnect: enabled
License Response: unknown
SG TCP Keep Alive: enabled
Peer's Local IPv4 Address: N/A
Peer's Local IPv6 Address: N/A
Peer's Remote IPv4 Address: N/A
Peer's Remote IPv6 Address: N/A
Peer's host name: firepower
Client Protocol Bypass: false
Tunnel Optimization: enabled
******************************************






 Feedback
Feedback