Introduction
This document describes the steps required to update the Identity Provider (IdP) certificate with the new Secure Access Service Provider Certificate.
Background Information
The Cisco Secure Access Security Assertion Markup Language (SAML) Certificate used for Virtual Private Network (VPN) Authentication is soon to expire and can be updated in your current IdP used to authenticate VPN Users in the case they do validate this certificate.
More information about this can be found in the Secure Access Announcements section.

Note: Most IdPs do not verify this SAML certificate by default and it is not a requirement, meaning no further action is needed in your IdP. In the case your IdP does validate the Secure Access Certificate, proceed with updating the Secure Access Certificate in your IdP configuration.
This documents covers the steps to confirm if the configured IdPs perform certificate validation: Entra ID (Azure AD), PingIdentity, Cisco DUO, OKTA.
Prerequisites
Requirements
- Access to your Cisco Secure Access Dashboard.
- Access to your IdP dashboard.
Cisco Secure Access Dashboard
|
Note: Make sure that after doing the next step which is activating the New Secure Access certificate, if your IdP is doing this Certificate Validation, update your IdP with the new Certificate; otherwise, the VPN Authentication for Remote Access Users can fail.
If you confirm your IdP is doing this Certificate Validation, we recommend you activate the new certificate in Secure Access and upload it to your IdP during non-working hours.
|
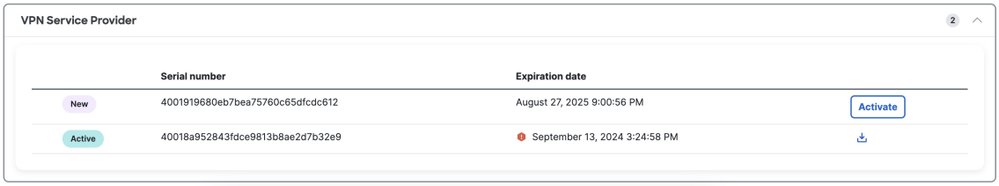
In the Secure Access Dashboard the only action required is go to Secure > Certificates > SAML Authentication > Service Provider certificates, on the "New" certificate click on "Activate".
Once clicked on Activate, you are able to download the New Secure Access certificate to import in your IdP if it is doing the Certificate Validation.
Microsoft Entra ID (Microsoft Azure)
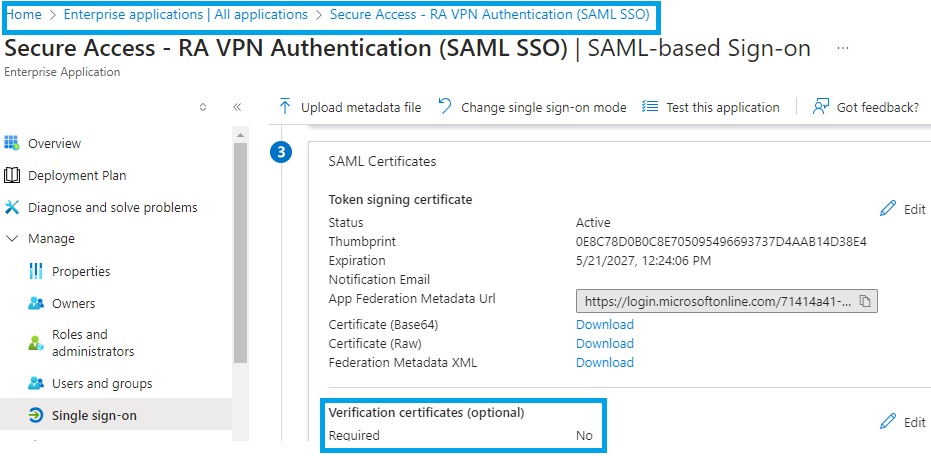
Entra ID (Azure AD) not doing Certificate Validation by default.
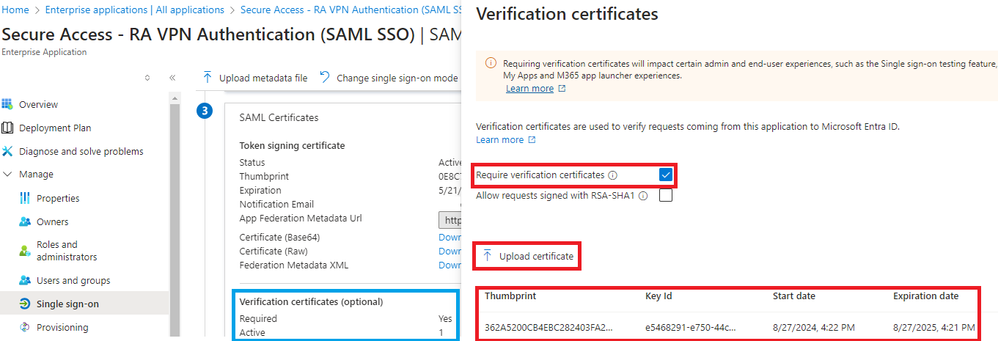
If the IdP Entra ID the value "Verification Certificate (optional) is set to "Required = yes", click on Edit and "Upload certificate" to upload the new Secure Access SAML VPN Certificate.
PingIdentity
PingIdentity not doing Certificate Validation by default.
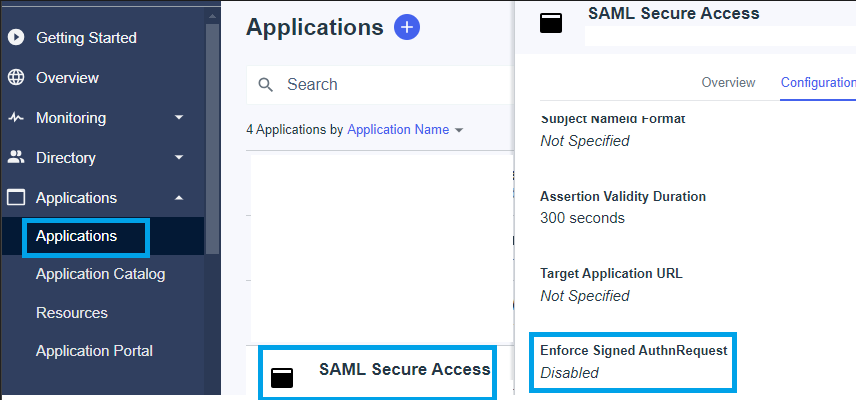
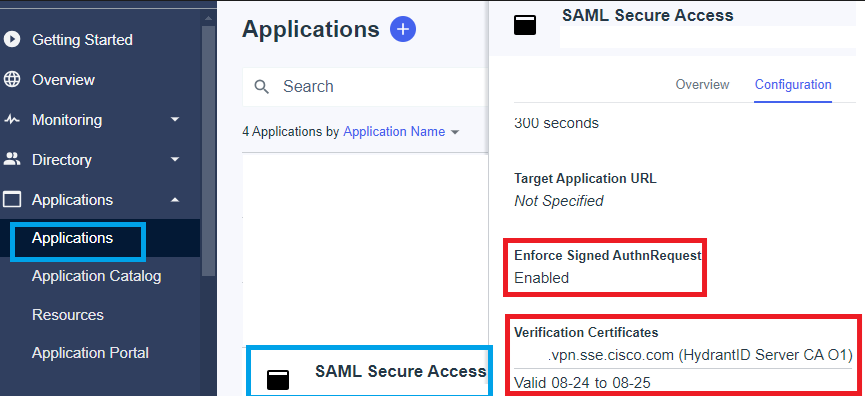
If in the IdP Pingidentity the value Enforce Signed AuthnRequest is set to "Enabled ", click on Edit and upload the new Secure Access SAML VPN Certificate.
Cisco DUO
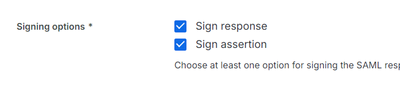
Cisco DUO is doing signing request validation by default, however it does not require an action to be done on DUO itself unless the Assertion Encryption is enabled.
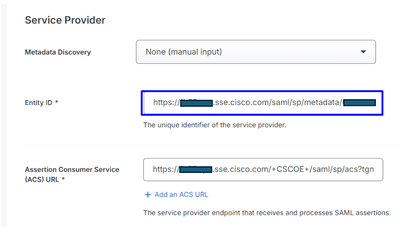
for request signing the DUO can download the new certificate using the metadata Entity ID link provided by the admin.
Signing Response and Assertion Action
Entity ID Settings
No Action is be required in this step, the DUO can pull the new certificate from the Entity ID Link: https://<entry-id>.vpn.sse.cisco.com/saml/sp/metadata/<profile_name>.
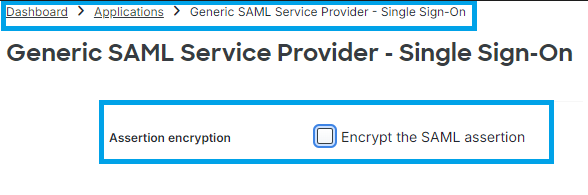
Assertion Encryption
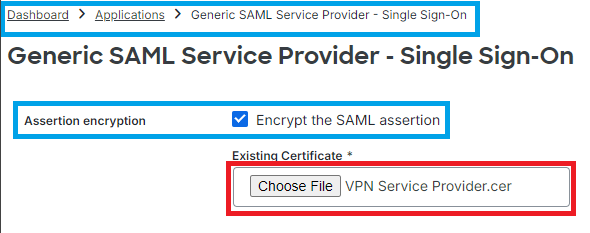
If in the IdP Cisco DUO the value "Assertion encryption" has the "Encrypt the SAML Assertion" marked, click on "choose File" and upload the new Secure Access SAML VPN Certificate.
OKTA
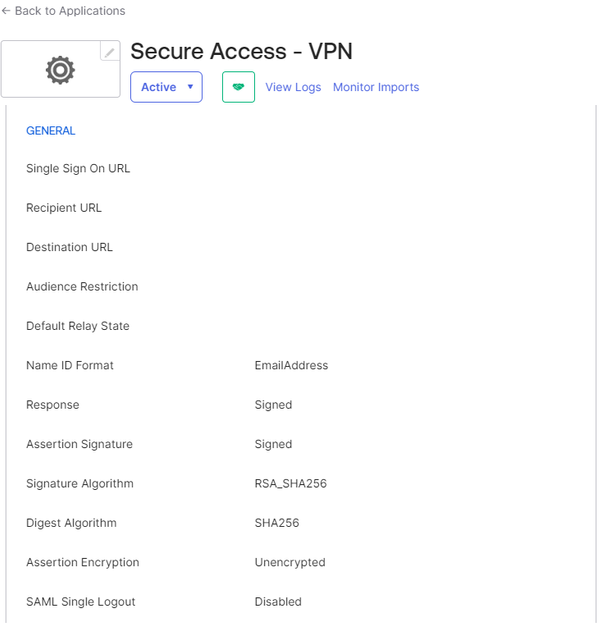
OKTA not doing Certificate Validation by default. There is not an option under General > SAML Settings, that says "Signature Certificate".
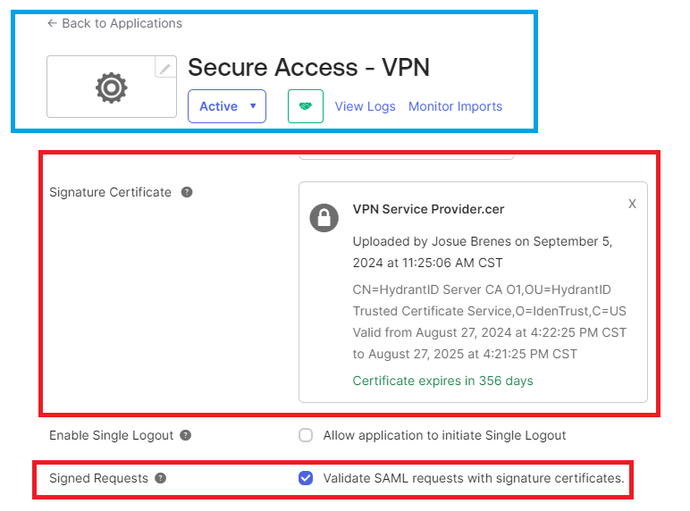
If in the IdP OKTA there is a value under General > SAML Settings, that says "Signature Certificate Assertion encryption" it means OKTA is doing Certificate Validation. Click on "Edit SAML Settings", click on Signature Certificate and upload the new Secure Access SAML VPN Certificate.
Related Information













 Feedback
Feedback