Introduction
This document describes how to configure Secure Access with Palo Alto Firewall.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Palo Alto 11.x Version Firewall
- Secure Access
- Cisco Secure Client - VPN
- Cisco Secure Client - ZTNA
- Clientless ZTNA
Components Used
The information in this document is based on:
- Palo Alto 11.x Version Firewall
- Secure Access
- Cisco Secure Client - VPN
- Cisco Secure Client - ZTNA
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
 Secure Access - Palo Alto
Secure Access - Palo Alto
Cisco has designed Secure Access to protect and provide access to private applications, both on-premise and cloud-based. It also safeguards the connection from the network to the internet. This is achieved through the implementation of multiple security methods and layers, all aimed at preserving the information as they access it via the cloud.
Configure
Configure the VPN on Secure Access
Navigate to the admin panel of Secure Access.
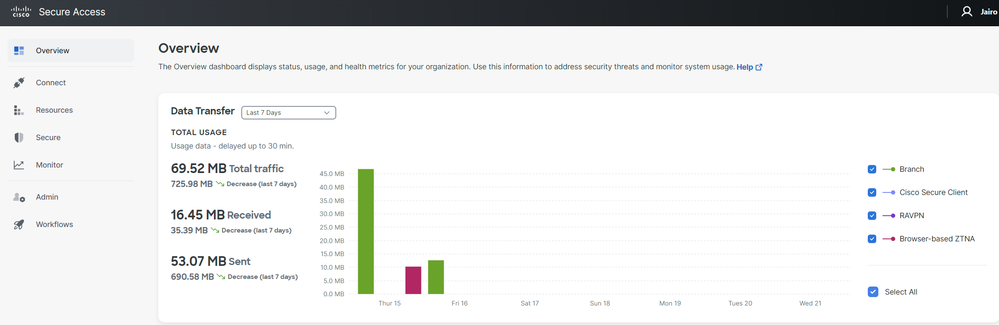 Secure Access - Main Page
Secure Access - Main Page
- Click on
Connect > Network Connections
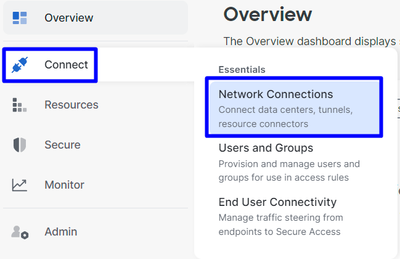 Secure Access - Network Connections
Secure Access - Network Connections
- Under
Network Tunnel Groups click on + Add
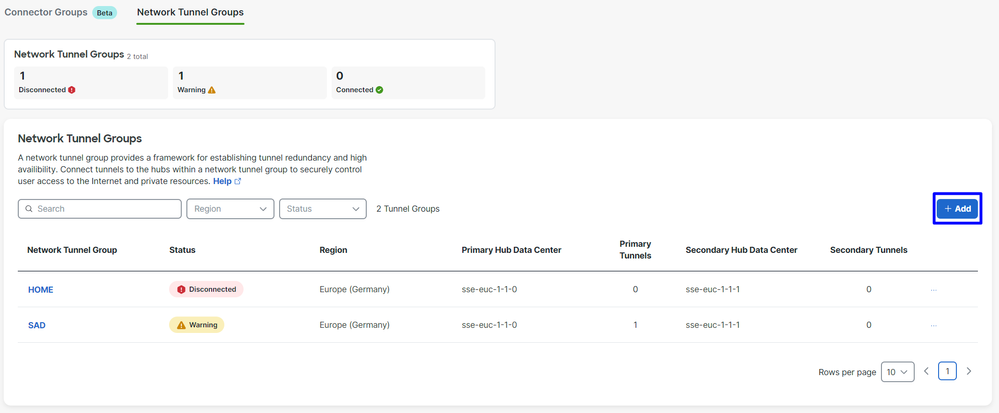 Secure Access - Network Tunnel Groups
Secure Access - Network Tunnel Groups
- Configure
Tunnel Group Name, Region and Device Type
- Click
Next
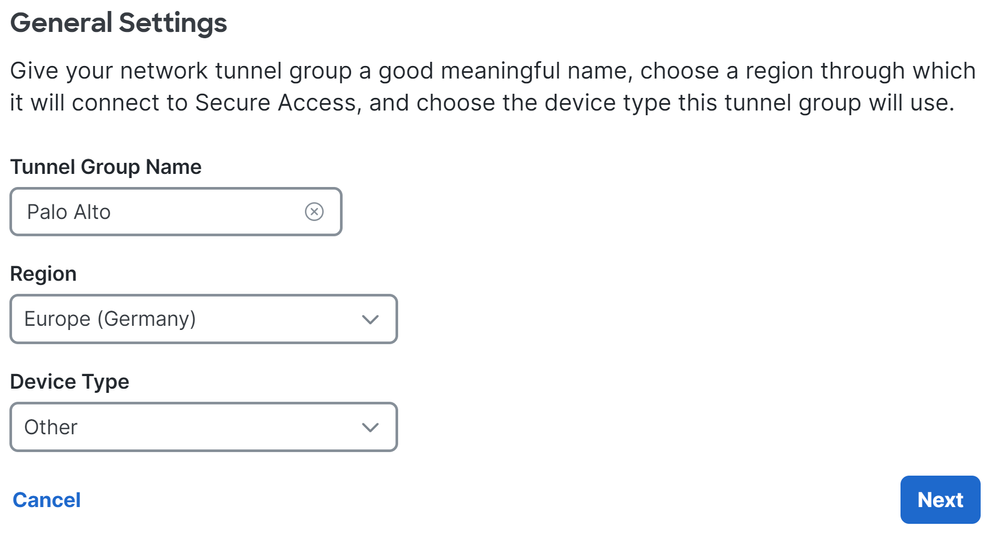

Note: Choose the region nearest to the location of your firewall.
- Configure the
Tunnel ID Format and Passphrase
- Click
Next
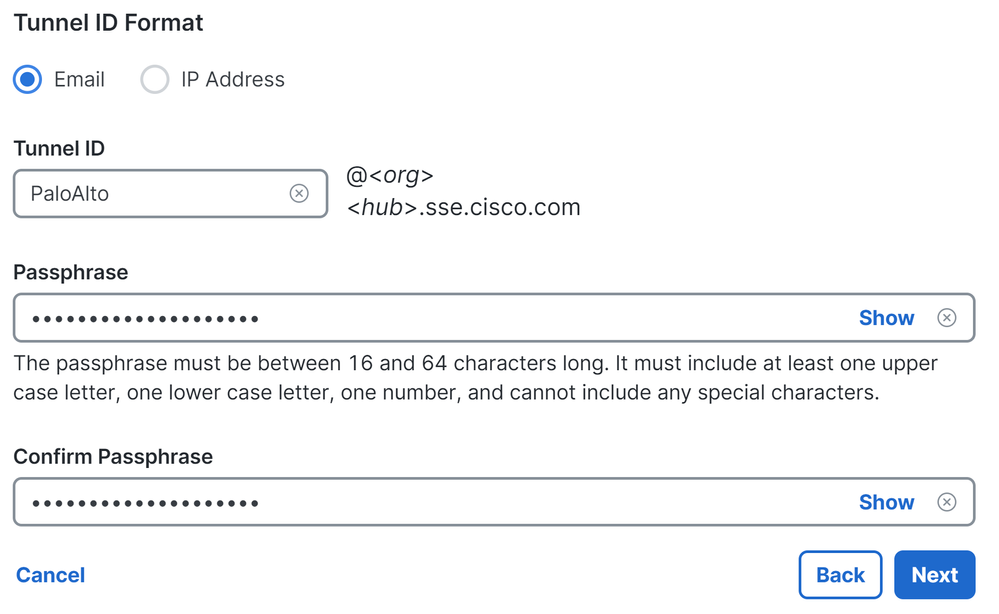
- Configure the IP address ranges or hosts that you have configured on your network and want to pass the traffic through Secure Access
- Click
Save
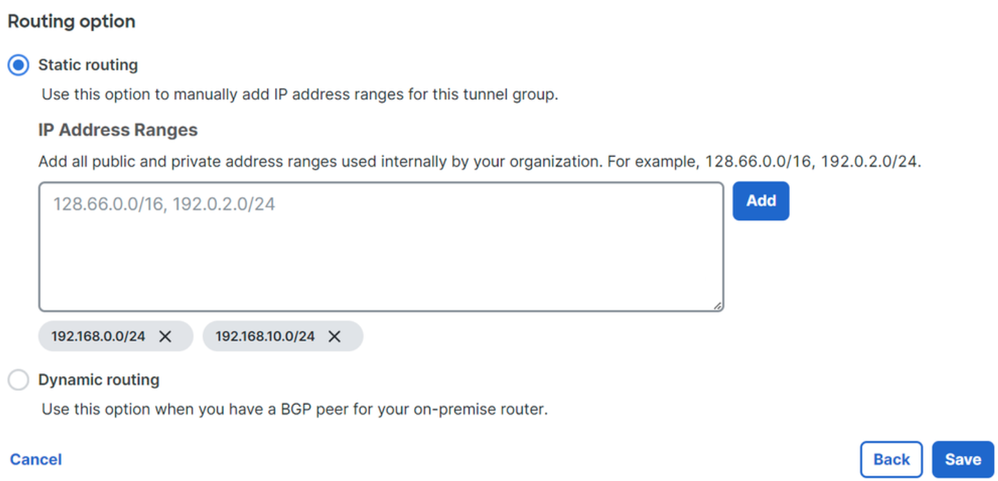 Secure Access - Tunnel Groups - Routing Options
Secure Access - Tunnel Groups - Routing Options
After you click on Save the information about the tunnel gets displayed, please save that information for the next step, Configure the tunnel on Palo Alto.
Tunnel Data
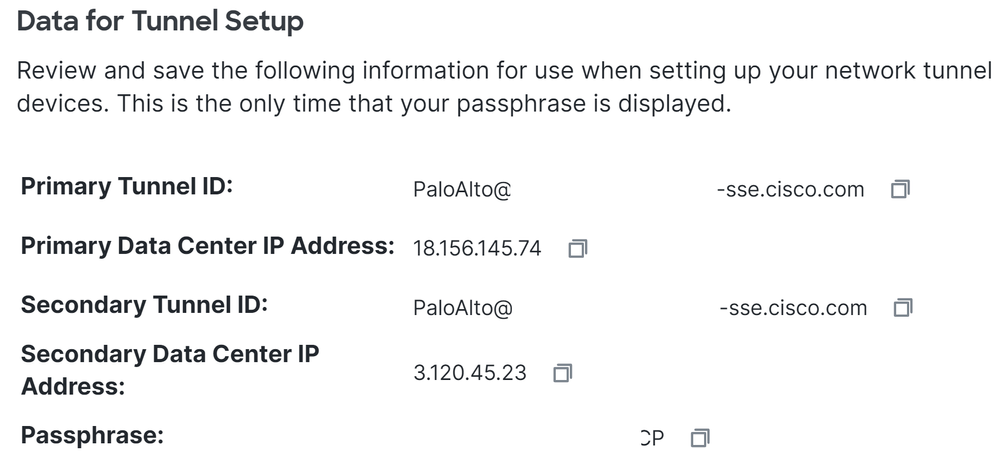
Configure the tunnel on Palo Alto
Configure the Tunnel Interface
Navigate to the Palo Alto Dashboard.
Network > Interfaces > TunnelClick Add
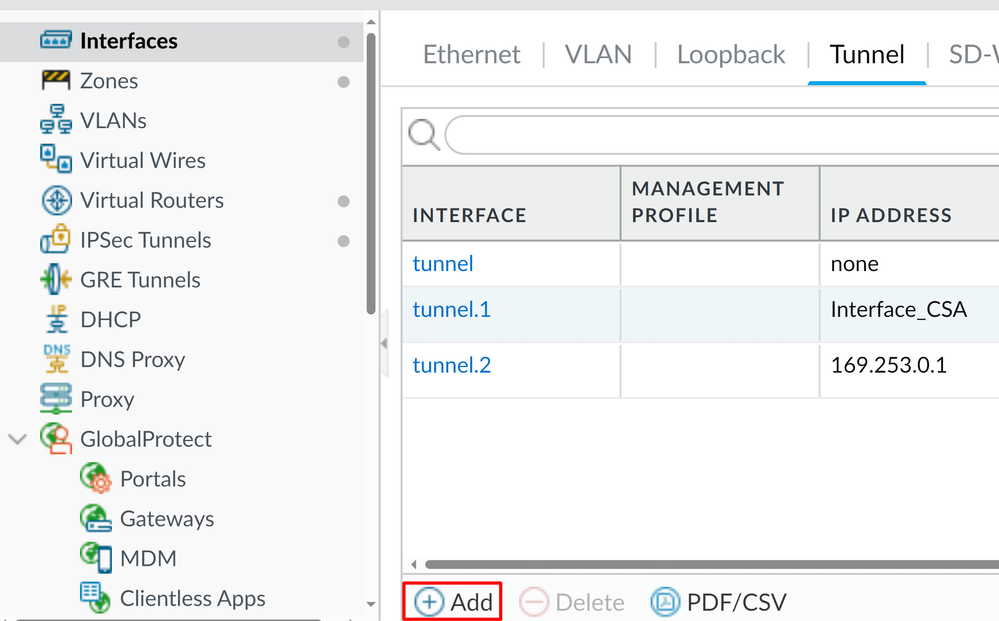
- Under
Config menu, configure the Virtual Router, Security Zone, and assign aSuffix Number
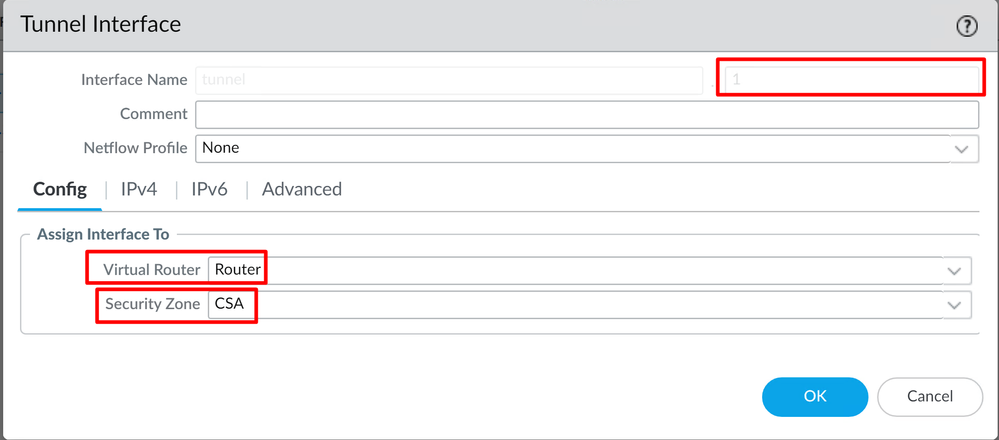
- Under
IPv4, configure a non-routable IP. For example, you can use 169.254.0.1/30
- Click
OK
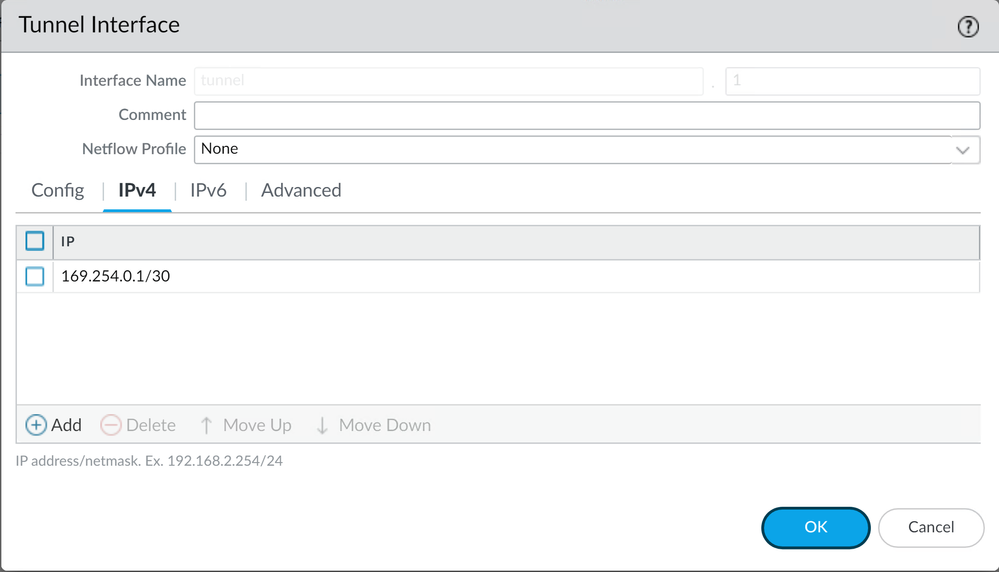
After that, you can have something like this configured:
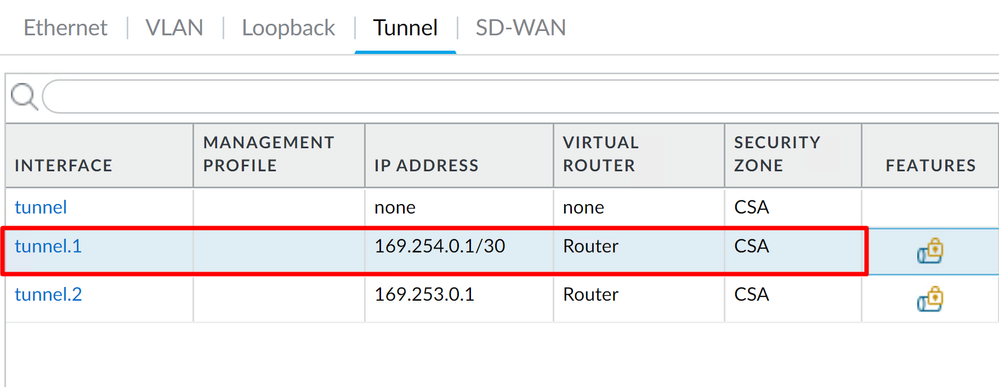
If you have it configured like this, you can click on Commit to save the configuration and continue with the next step, Configure IKE Crypto Profile.
Configure IKE Crypto Profile
To configure the crypto profile, navigate to:
Network > Network Profile > IKE Crypto - Click
Add
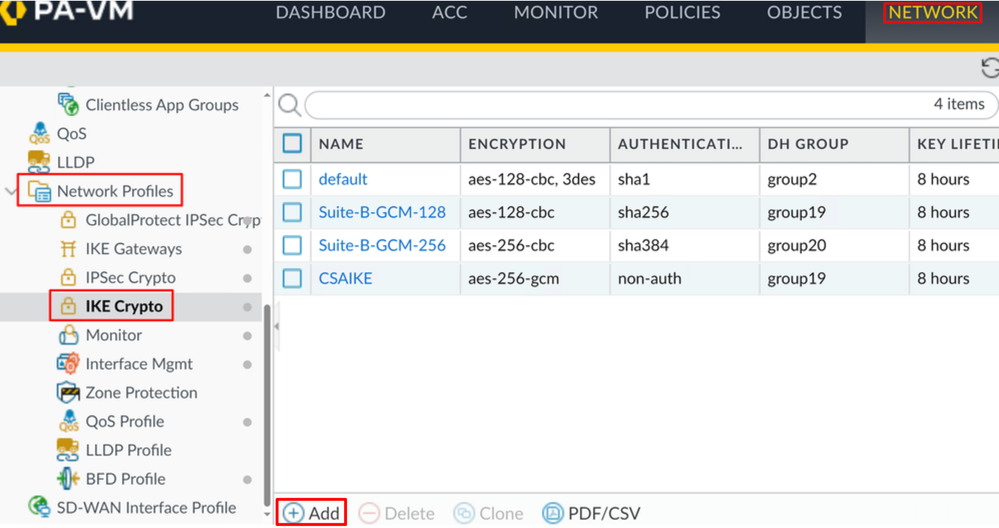
- Configure the next parameters:
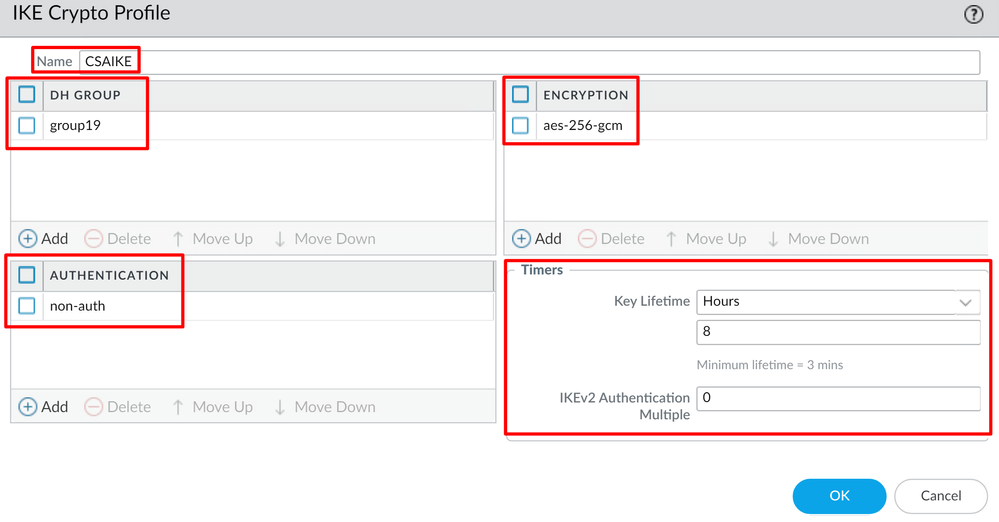
Name: Configure a name to identify the profile.DH GROUP: group19AUTHENTICATION: non-authENCRYPTION: aes-256-gcmTimers
Key Lifetime: 8 HoursIKEv2 Authentication: 0
- After you have everything configured, click
OK
If you have it configured like this, you can click on Commit to save the configuration and continue with the next step, Configure IKE Gateways.
Configure IKE Gateways
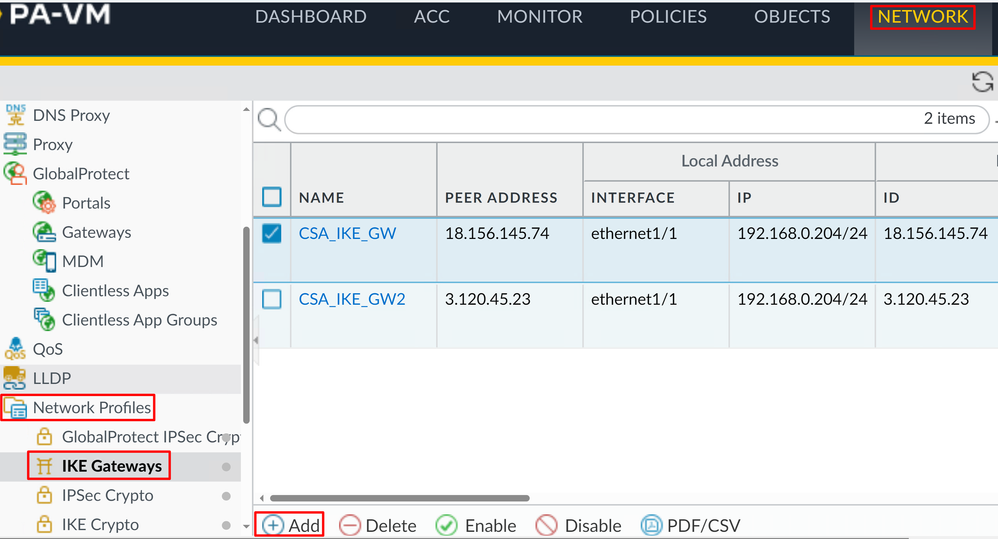
To configure IKE Gateways
Network > Network Profile > IKE Gateways- Click
Add
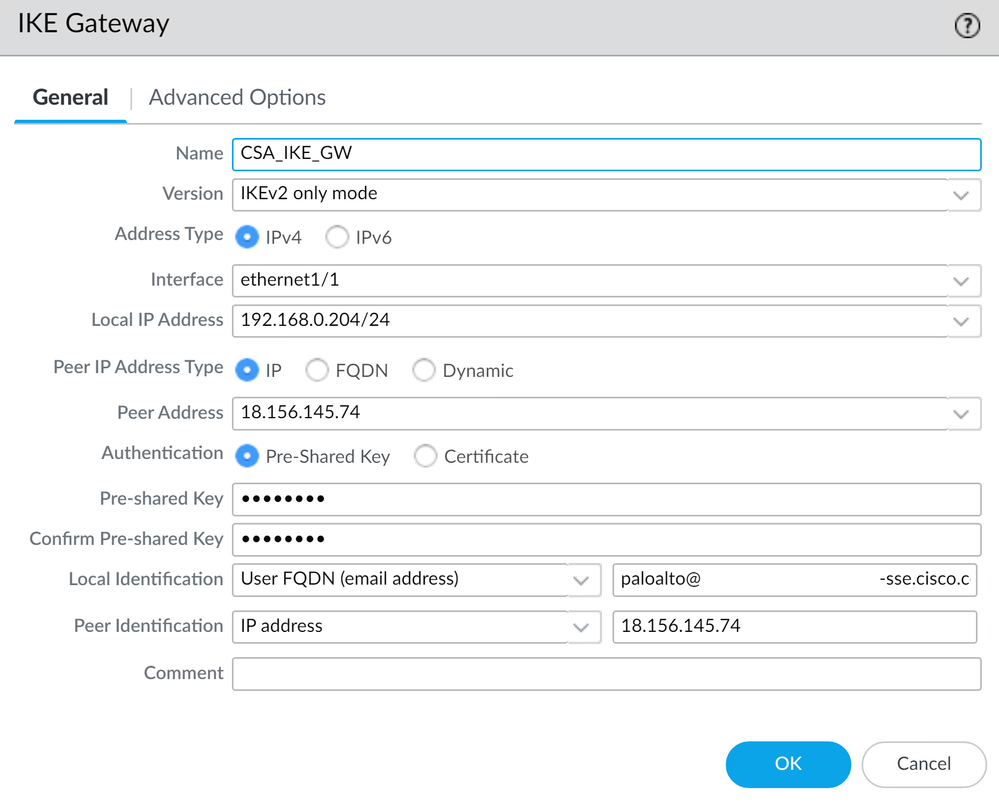
- Configure the next parameters:
Name: Configure a name to identify the Ike Gateways.Version : IKEv2 only modeAddress Type : IPv4Interface : Select your Internet WAN interface.Local IP Address: Select the IP of your Internet WAN Interface.Peer IP Address Type : IPPeer Address: Use the IP of Primary IP Datacenter IP Address, given in the step Tunnel Data.Authentication: Pre-Shared KeyPre-shared Key : Use the passphrase given in the step Tunnel Data.Confirm Pre-shared Key : Use the passphrase given in the step Tunnel Data.Local Identification : Choose User FQDN (Email address) and use the Primary Tunnel ID given in the step, Tunnel Data.Peer Identification : ChooseIP Addressand use the Primary IP Datacenter IP Address.
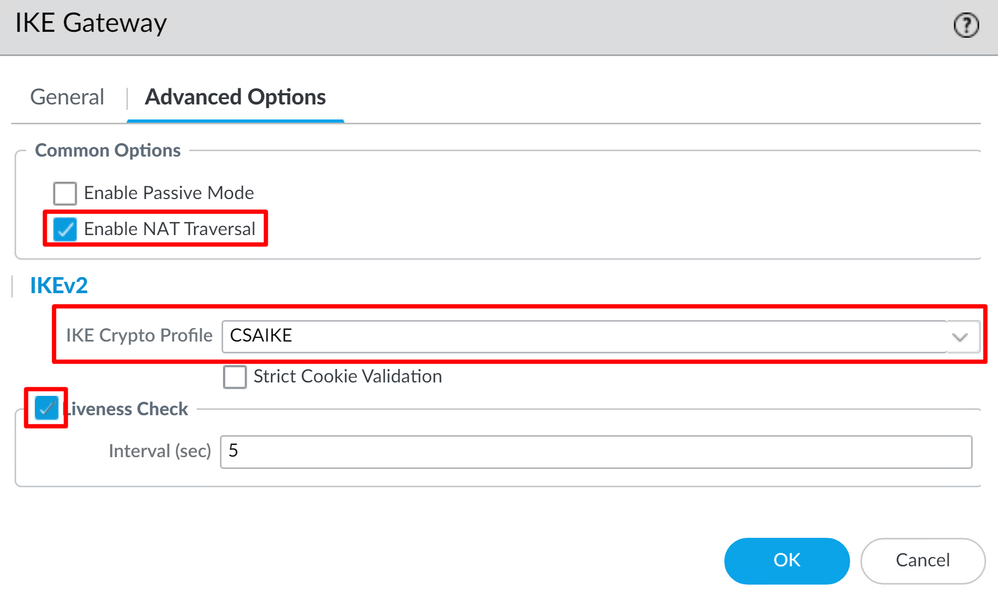
- Click
Advanced Options
Enable NAT Traversal- Select the
IKE Crypto Profile created on the step, Configure IKE Crypto Profile
- Mark the checkbox for
Liveness Check
- Click
OK
If you have it configured like this, you can click on Commit to save the configuration and continue with the next step, Configure IPSEC Crypto.
Configure IPSEC Crypto Profile
To configure IKE Gateways, Navigate to Network > Network Profile > IPSEC Crypto
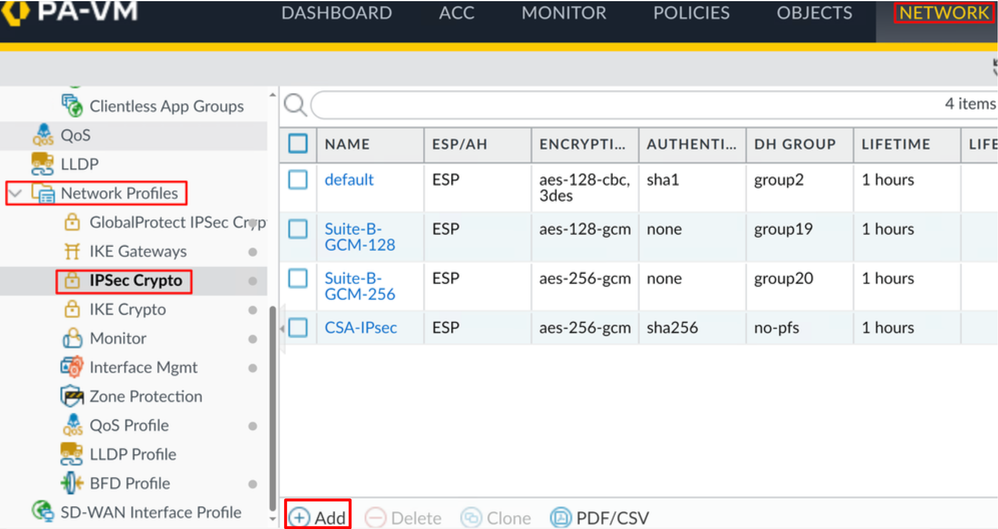
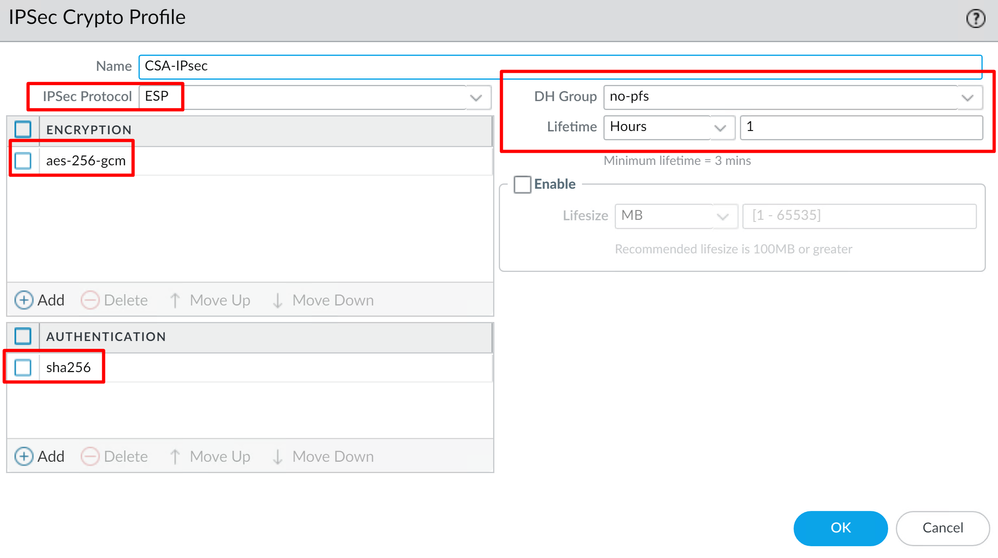
- Configure the next parameters:
Name: Use a name to identify the Secure Access IPsec ProfileIPSec Protocol: ESPENCRYPTION: aes-256-gcmDH Group: no-pfs, 1 Hour
- Click
OK
If you have it configured like this, you can click on Commit to save the configuration and continue with the next step, Configure IPSec Tunnels.
Configure IPSec Tunnels
To configure IPSec Tunnels, navigate to Network > IPSec Tunnels.
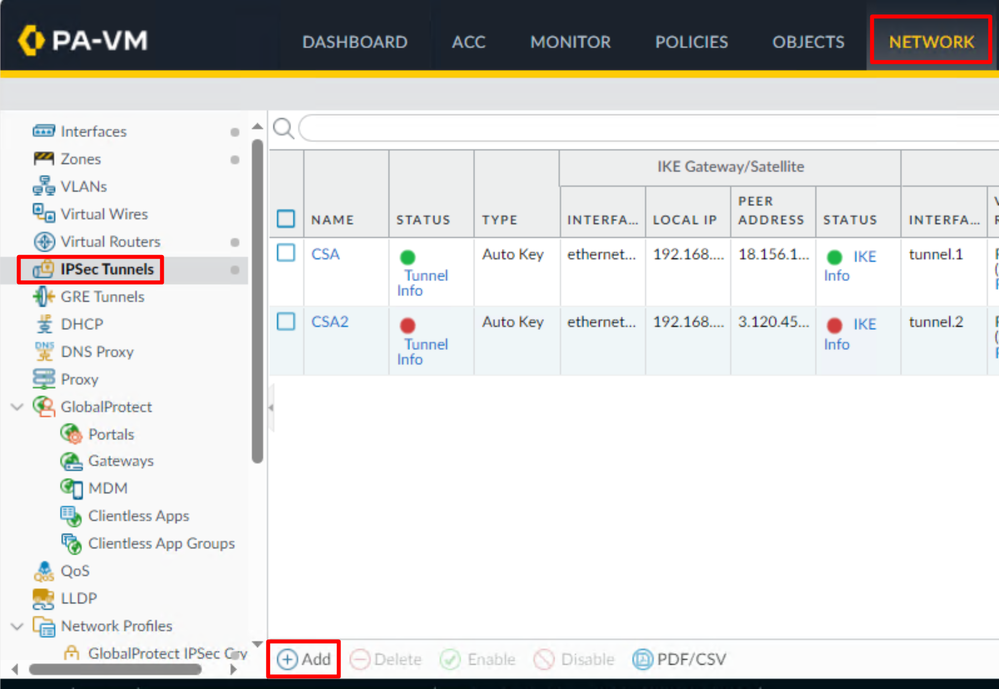
- Configure the next parameters:
Name: Use a name to identify the Secure Access tunnelTunnel Interface: Choose the tunnel interface configured on the step, Configure the tunnel interfaceType: Auto KeyAddress Type: IPv4IKE Gateways: Choose the IKE Gateways configured on the step, Configure IKE Gateways.IPsec Crypto Profile: Choose the IKE Gateways configured on the step, Configure IPSEC Crypto Profile- Mark the checkbox for
Advanced Options
IPSec Mode Tunnel: Choose Tunnel.
- Click
OK
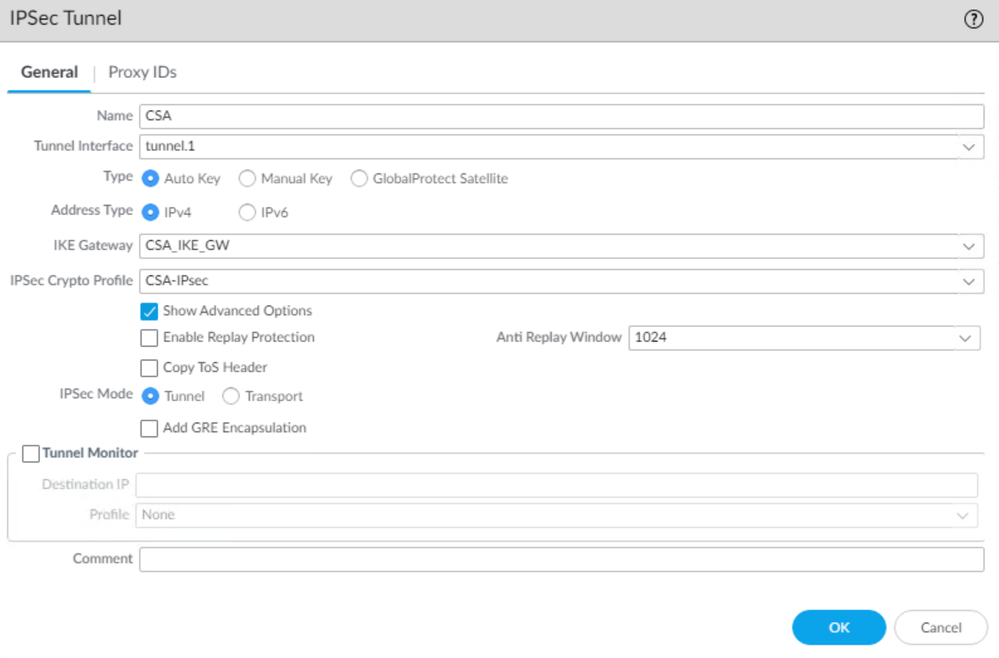
Now your VPN is successfully created, you can proceed with the step, Configure Policy Based Forwarding.
Configure Policy Based Forwarding
To configure Policy Based Forwarding, navigate to Policies > Policy Based Forwarding.
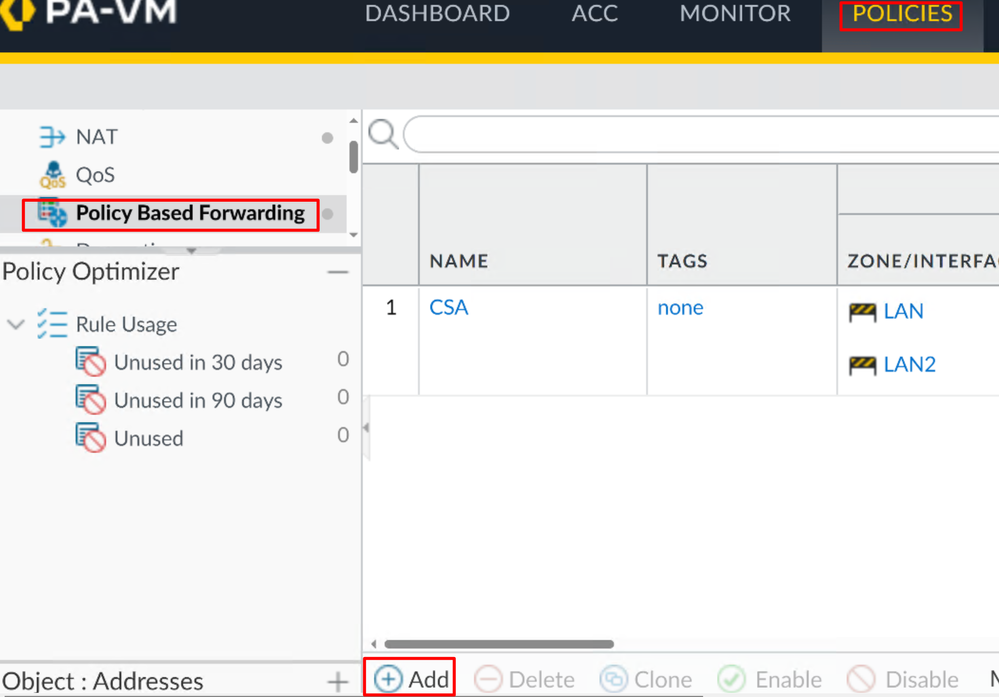
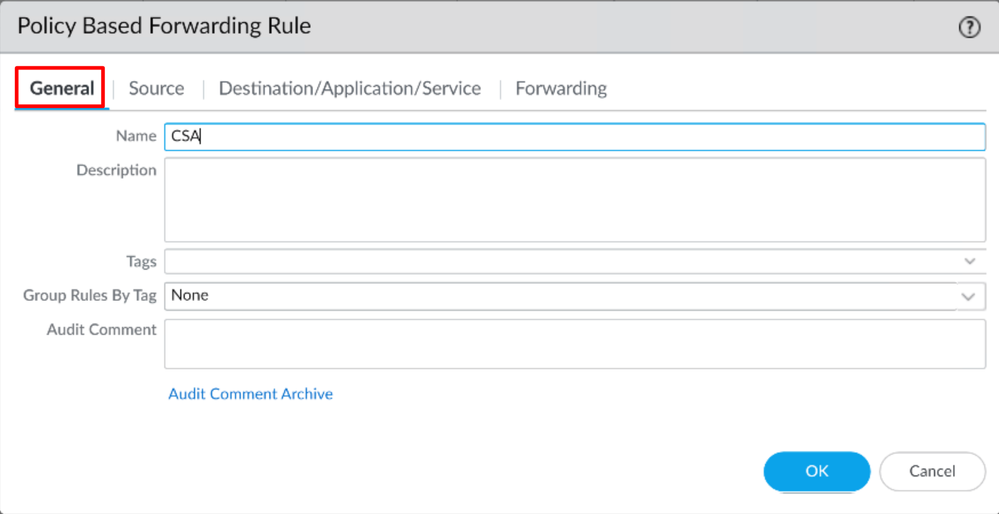
- Configure the next parameters:
General
Name: Use a name to identify the Secure Access, Policy Base Forwarding (Routing by origin)
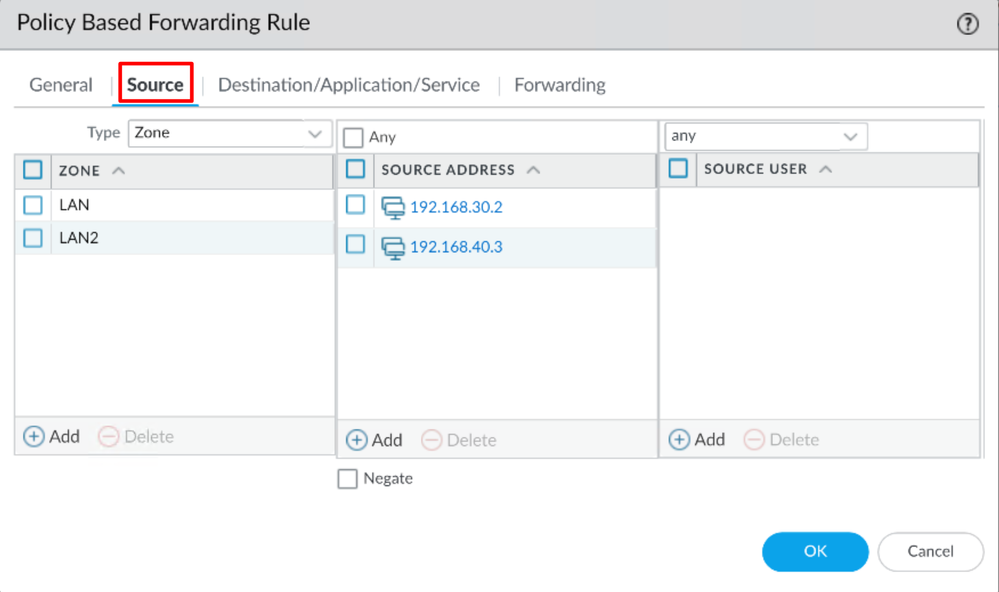
Source
Zone: Select the Zones from where you have plans to route the traffic based on the originSource Address: Configure the host or networks that you want to use as a source.Source Users: Configure the users that you want to route the traffic (Only if applicable)
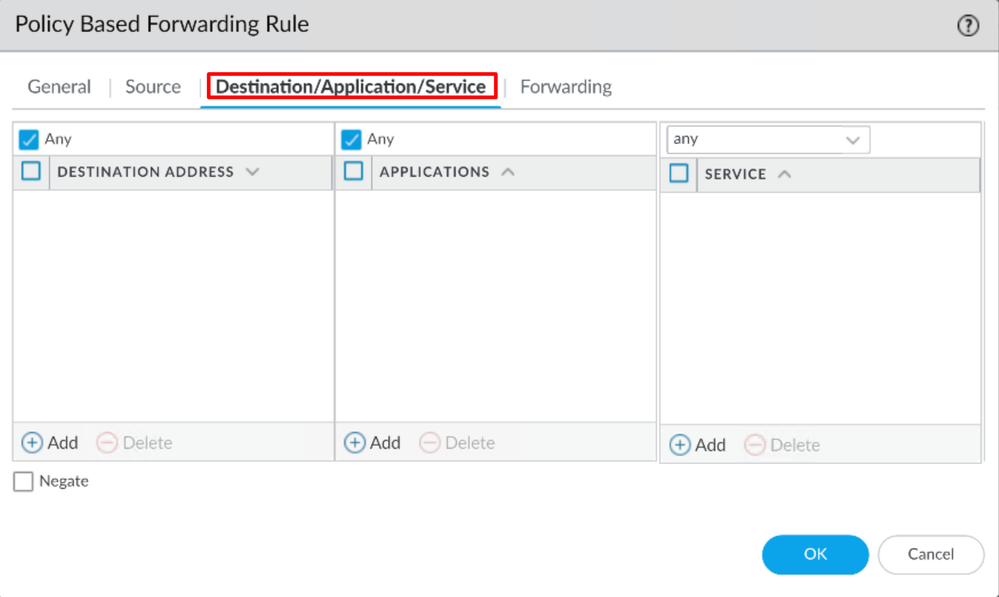
Destination/Application/Service
Destination Address: You can leave it as Any, or you can specify the ranges of addresses of Secure Access (100.64.0.0/10)
Forwarding
- Click
OK and Commit
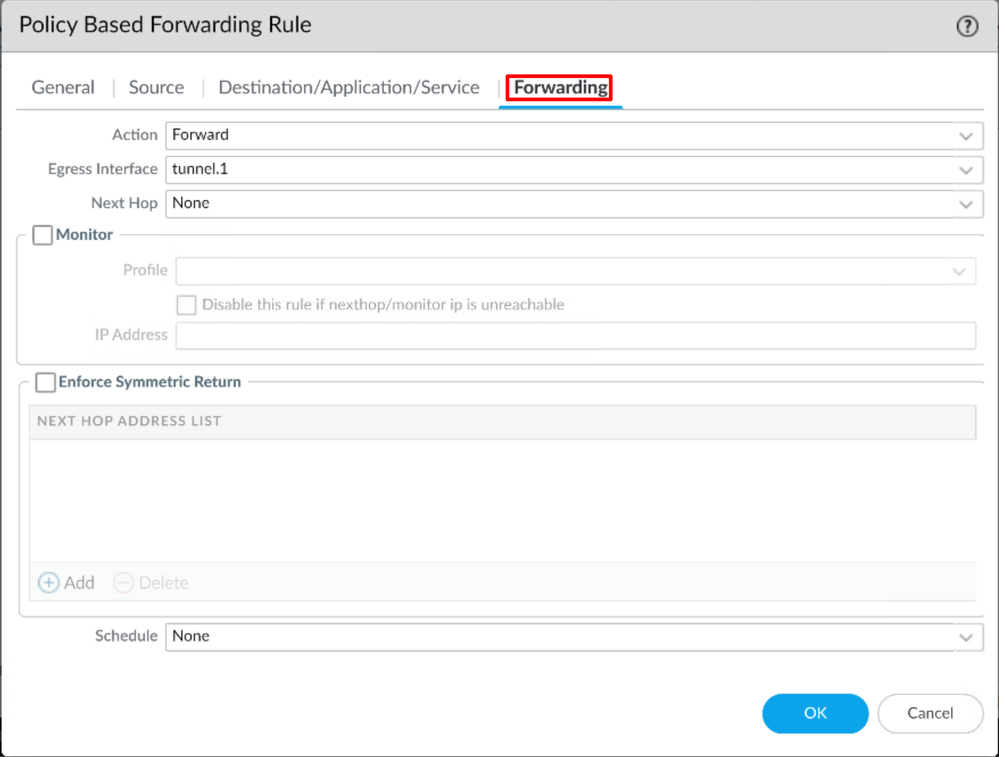
Now you have everything configured on Palo Alto; after you configure the route, the tunnel can be established, and you need to continue configuring the RA-VPN, Browser-Based ZTA, or Client Base ZTA on Secure Access Dashboard.




























 Feedback
Feedback