Introduction
This document describes how to deploy the Cisco Secure Client Network Access Manager (NAM) profile through Identity Services Engine (ISE).
Background Information
EAP-FAST authentication occurs in two phases. In the first phase, EAP-FAST employs a TLS handshake to provide and authenticate key exchanges using Type-Length-Values (TLV) objects to establish a protected tunnel. These TLV objects are used to convey authentication-related data between the client and server. Once the tunnel is established, the second phase begins with the client and ISE node engaging in further conversations to establish the required authentication and authorization policies.
The NAM configuration profile is set up to use EAP-FAST as the authentication method and is available for administratively defined networks.
In addition, both machine and user connection types can be configured within the NAM configuration profile.
The corporate Windows device gain full corporate access using the NAM with Posture check.
The personal Windows device gain access to a restricted network using the same NAM configuration.
This document provides instructions for deploying the Cisco Secure Client Network Access Manager (NAM) profile via the Identity Services Engine (ISE) Posture Portal using web deployment, along with Posture Compliance Check.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Identity Services Engine (ISE)
- AnyConnect NAM and Profile Editor
- Posture Policy
- Cisco Catalyst configuration for 802.1x services
Components Used
The information in this document is based on these software and hardware versions:
- Cisco ISE, Release 3.3 and later
- Windows 10 with Cisco Secure Mobility Client 5.1.4.74 and later
- Cisco Catalyst 9200 switch with software Cisco IOS® XE 17.6.5 and later
- Active Directory 2016
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Configuration
Network Diagram
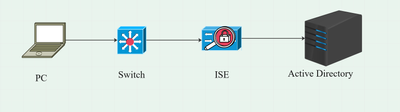
Data Flow
When a PC connects to the network, the ISE provides the authorization policy for redirection to the Posture Portal.
The http traffic on the PC is redirected to the ISE Client Provisioning Page, where the NSA application is downloaded from ISE.
The NSA then installs the Secure Client agent modules on the PC.
After the agent installation is completed, the agent downloads the Posture profile and NAM profile configured on ISE.
The installation of the NAM module triggers a restart on the PC.
After the restart, NAM module performs EAP-FAST authentication based on the NAM profile.
The Posture scan is then triggered and compliance is checked based on the ISE Posture Policy.
Configure Switch
Configure the access switch for dot1x authentication and redirection.
|
aaa new-model
aaa authentication dot1x default group radius
aaa authorization network default group radius
aaa accounting dot1x default start-stop group radius
aaa server radius dynamic-author
client 10.127.197.53 server-key Qwerty123
auth-type any
aaa session-id common
ip radius source-interface Vlan1000
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
radius-server attribute 31 mac format ietf upper-case
radius server RAD1
address ipv4 <ISE server IP> auth-port 1812 acct-port 1813
key <secret-key>
dot1x system-auth-control
|
Configure Redirect ACL for user to be redirected to ISE Client Provisioning Portal.
|
ip access-list extended redirect-acl
10 deny udp any any eq domain
20 deny tcp any any eq domain
30 deny udp any eq bootpc any eq bootps
40 deny ip any host <ISE server IP>
50 permit tcp any any eq www
60 permit tcp any any eq 443
|
Enable device tracking and http redirection on the switch.
|
device-tracking policy <device tracking policy name>
tracking enable
interface <interface name>
device-tracking attach-policy <device tracking policy name>
ip http server
ip http secure-server
|
Download the Secure client Package
Download the Profile Editor, Secure Client windows and Compliance Module webdeploy files manually from software.cisco.com
On the product name search bar type Secure Client 5.
Downloads Home > Security > Endpoint Security > Secure Client (including AnyConnect) > Secure Client 5 > AnyConnect VPN Client Software
- cisco-secure-client-win-5.1.4.74-webdeploy-k9.pkg
- cisco-secure-client-win-4.3.4164.8192-isecompliance-webdeploy-k9.pkg
- tools-cisco-secure-client-win-5.1.4.74-profileeditor-k9.msi
ISE Configuration
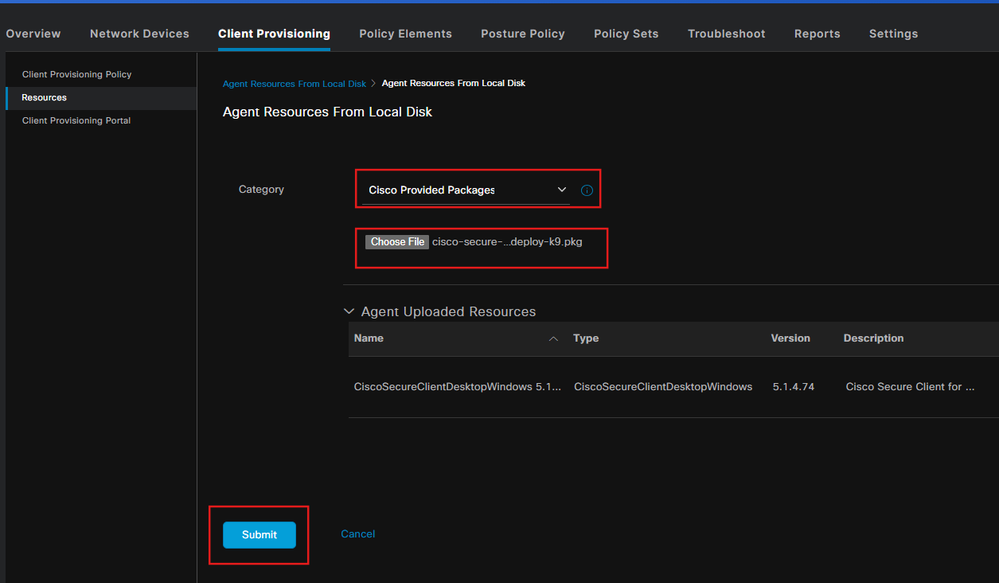
Step 1. Upload the Package on ISE
To upload the Secure Client and Compliance Module webdeploy packages on ISE, Navigate to Workcenter > Posture > Client Provisioning > Resources > Add > Agent Resources from Local Disk.
Step 2. Create a NAM Profile from Profile editor tool
For information on how to configure a NAM profile refer this guide Configure Secure Client NAM Profile .
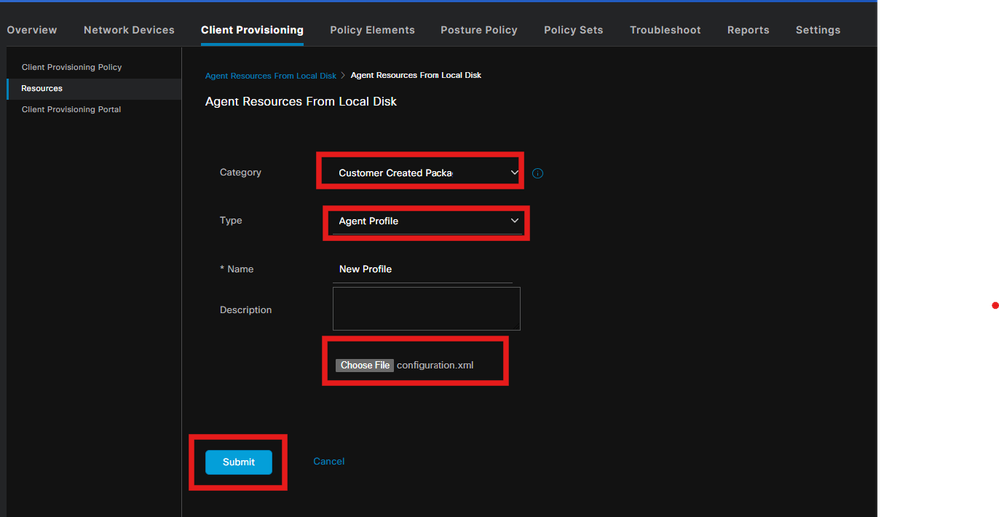
Step 3. Upload the NAM Profile on ISE
To upload the NAM Profile "Configuration.xml" on ISE as Agent Profile, navigate to Client Provisioning > Resources > Agent Resources From Local Disk.
Step 4. Create a Posture Profile
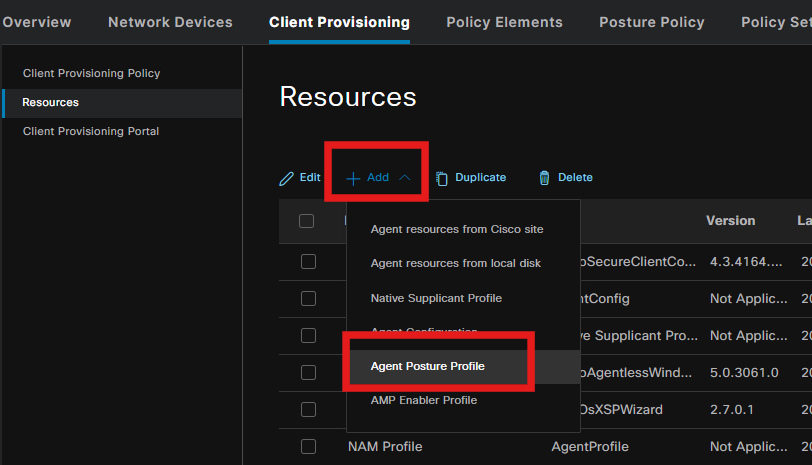
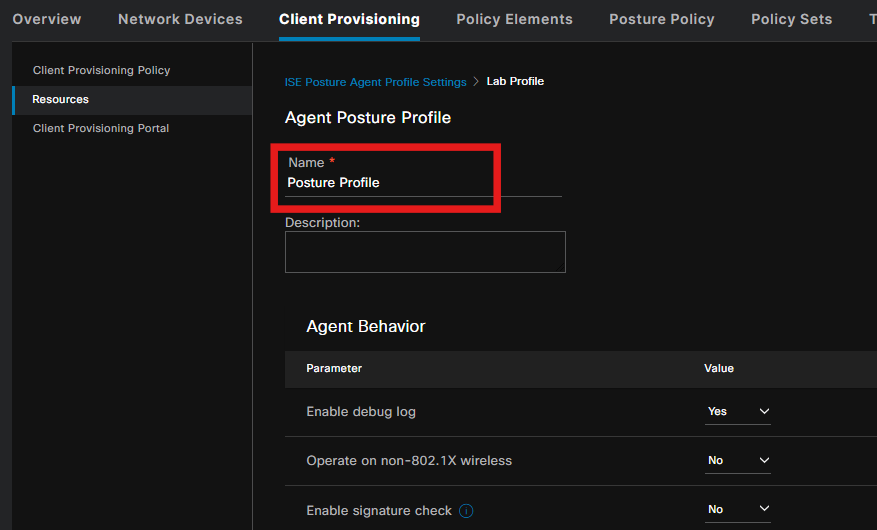
From the Posture Protocol section, do not forget to add * in order to allow the Agent to connect to all servers.
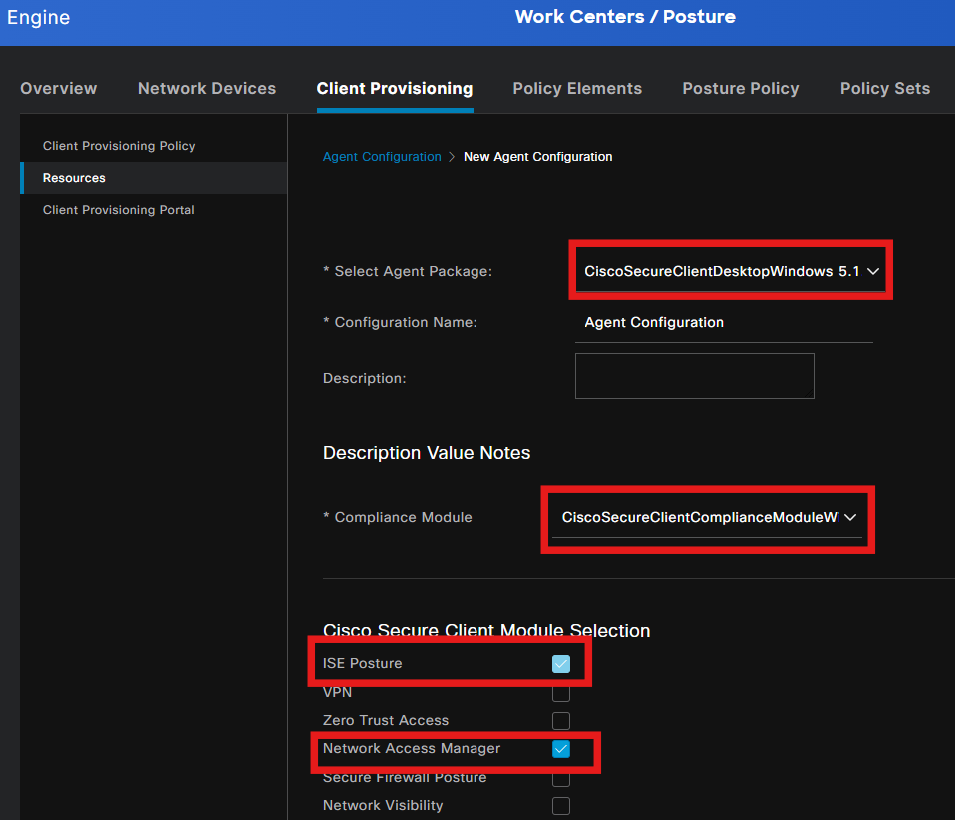
Step 5. Create Agent Configuration
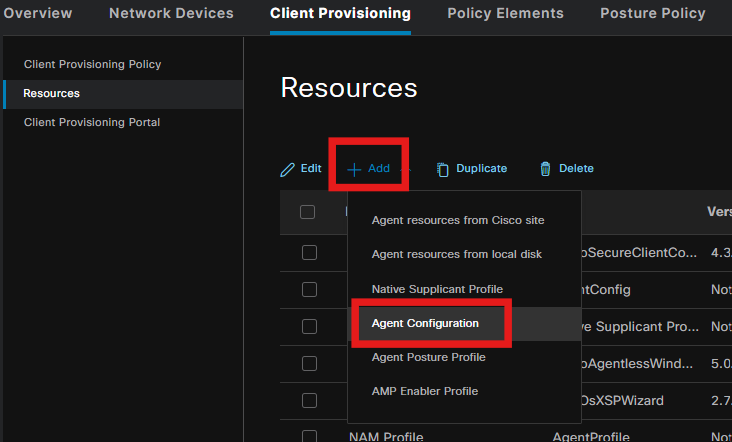
Select the uploaded secure client and compliance module package and under the Module selection, select the ISE Posture, NAM and DART modules
Under Profile select, choose the Posture and NAM Profile and click Submit.
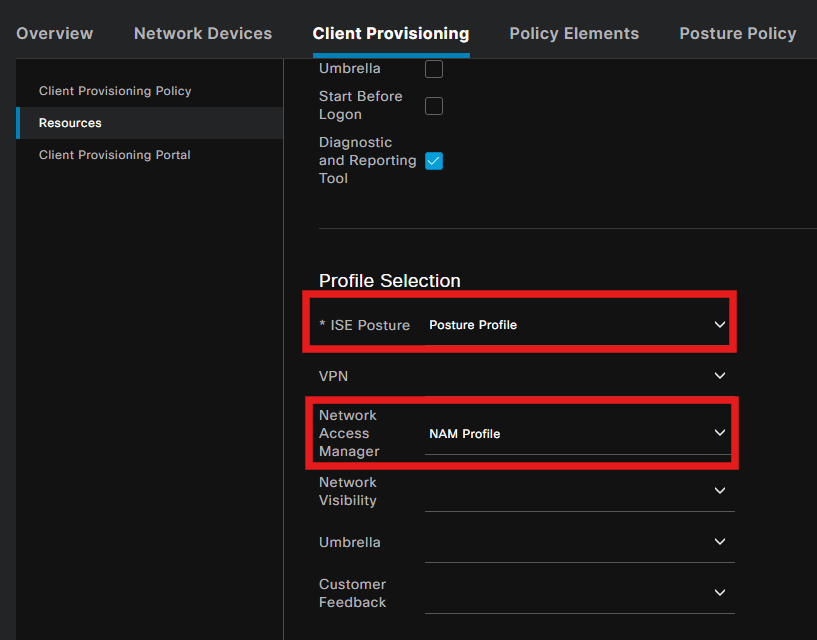
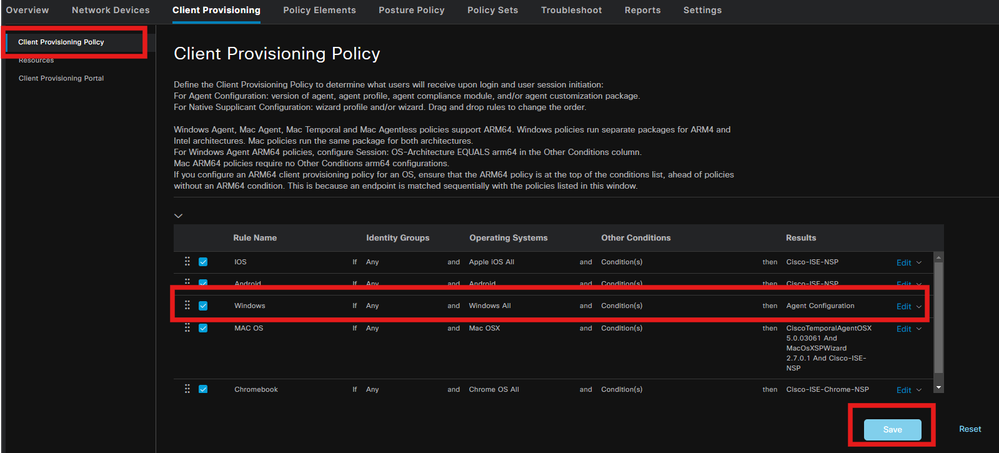
Step 6. Client Provisioning Policy
Create a client Provisioning Policy for Windows operating system and select the Agent Configuration created in the previous step.
Step 7. Posture Policy
For information on how to create the Posture Policy and conditions, refer this guide ISE Posture Prescriptive Deployment Guide .
Step 8. Add Network device
To add the switch IP address and the radius shared secret key, navigate to Administration > Network Resources.
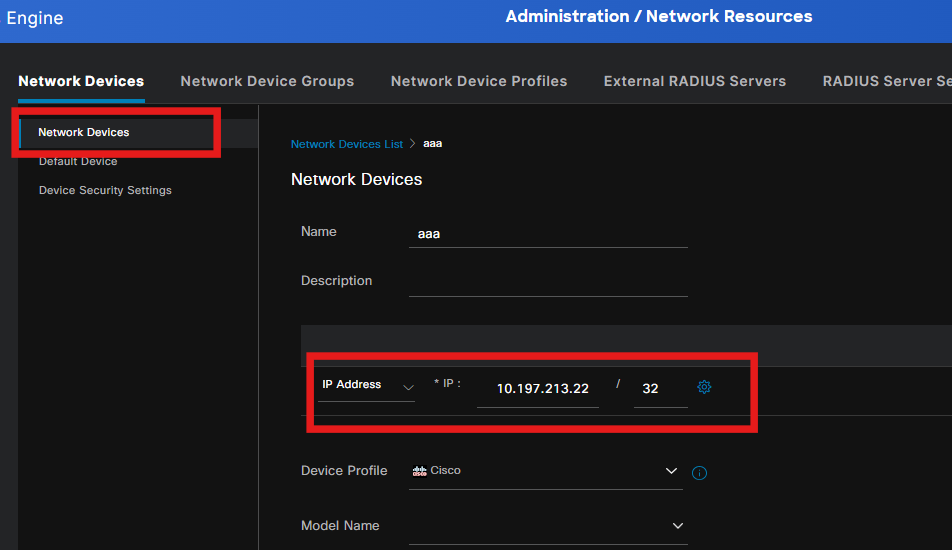
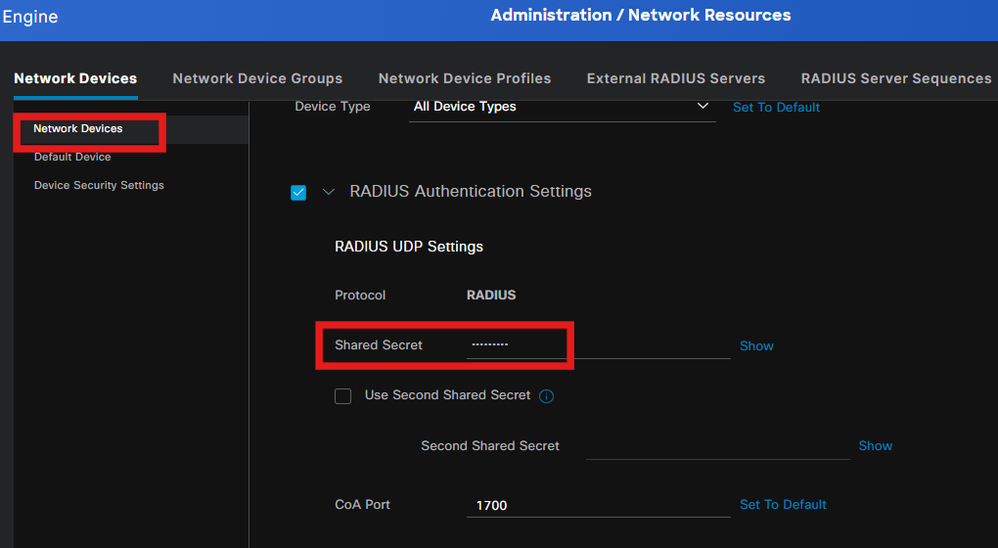
Step 9. Authorization Profile
To create a Posture redirection profile, navigate to Policy > Policy Elemets > Results.
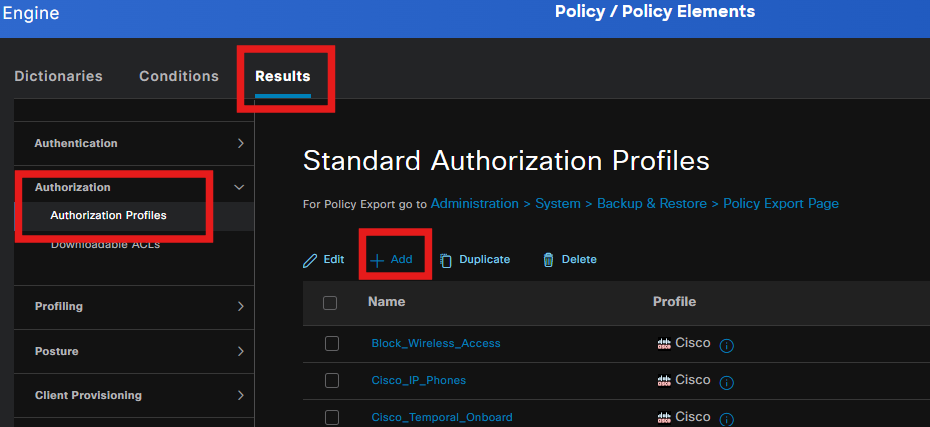
Under command task, select the client Provisioning Portal with redirect ACL.
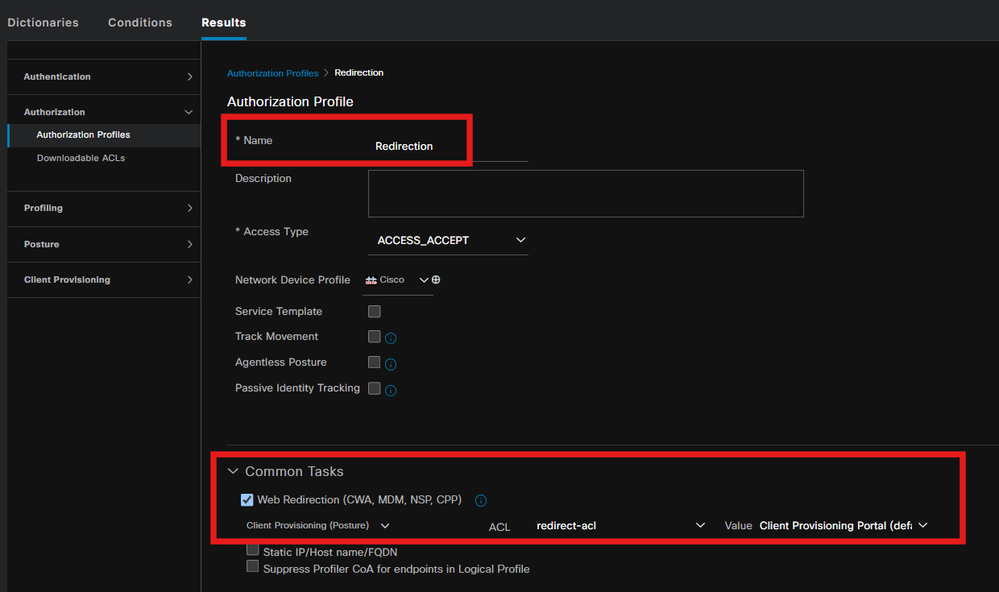
Step 10. Allowed Protocals
Navigate to Policy > Policy elements > Results > Authentication > Allowed Protocols, Selsct the EAP Chaining settings,
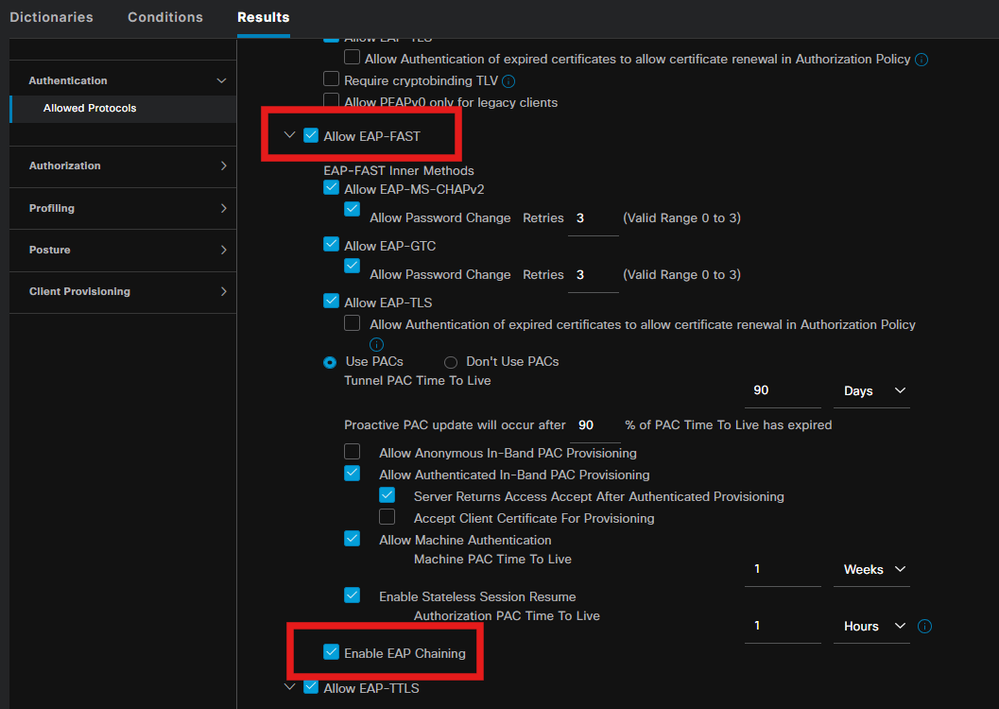
Step 11. Active Directory
Validate ISE is joined with Active directory domain and the domain groups are selected if needed for the authorization conditions.
Administration > Identity Management > External Identity Sources > Active Directory
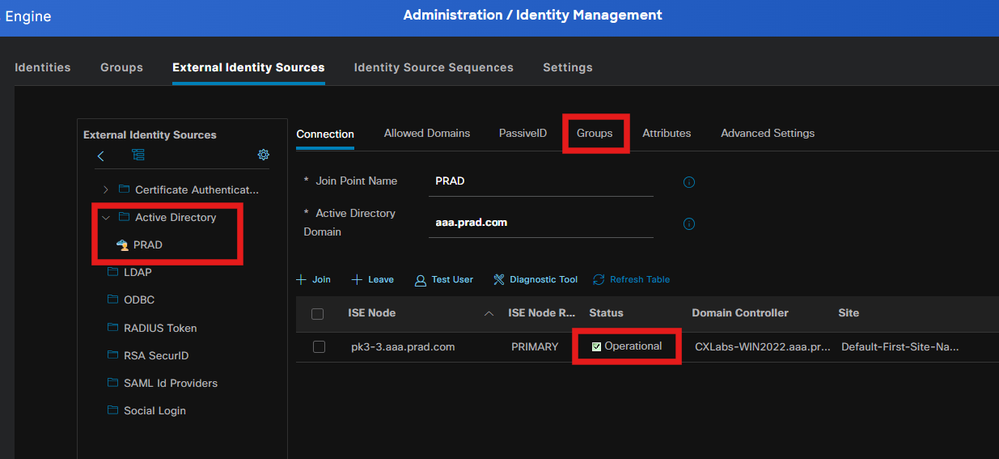
Step 12. Policy sets
Create a Policy set on ISE to authenticate the dot1x request. Navigate to Policy > Policy sets .
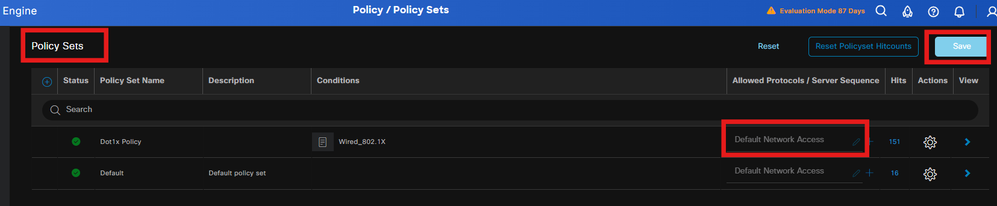
Select the Active directory as identity source for Authentication Policy.
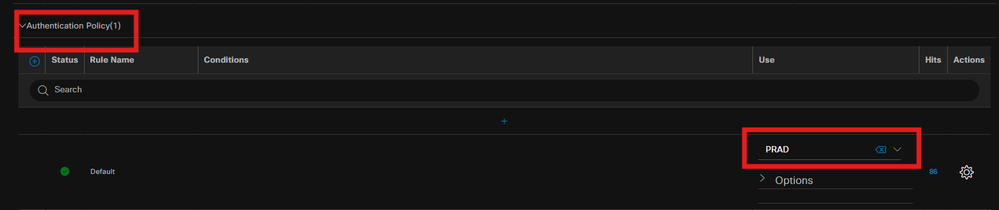
Configure different Authorization rules based on posture status unknown, non-compliant and compliant.
In this use case.
- Initial Access : Redirection to ISE Client Provisioning Portal to install Secure client agent and NAM Profile
- Unknown Access: Access to Client Provisioning Portal for redirection based Posture discovery
- Compliant Access: Full network access
- Non-Compliant: Deny Access
Verify
Step 1. Download and Install Secure Client Posture/NAM module from ISE
Select the endpoint authenticated through dot1x, hitting "Initial Access" Authorization rule. Navigate to Operations > Radius > Live Logs
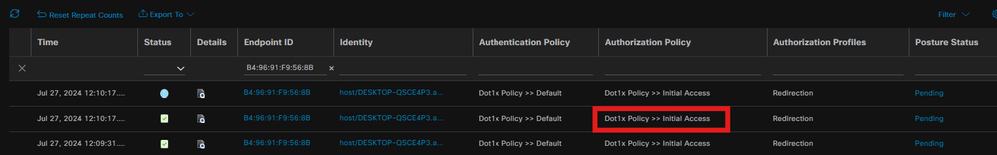
On Switch, specify the redirection URL and ACL getting applied for the Endpoint.
|
Switch#show authentication session interface te1/0/24 details
Interface: TenGigabitEthernet1/0/24
IIF-ID: 0x19262768
MAC Address: x4x6.xxxx.xxxx
IPv6 Address: Unknown
IPv4 Address: <client-IP>
User-Name: host/DESKTOP-xxxxxx.aaa.prad.com
Status: Authorized
Domain: DATA
Oper host mode: single-host
Oper control dir: both
Session timeout: N/A
Common Session ID: 16D5C50A0000002CF067366B
Acct Session ID: 0x0000001f
Handle: 0x7a000017
Current Policy: POLICY_Te1/0/24
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Security Policy: Should Secure
Security Status: Link Unsecured
Server Policies:
URL Redirect ACL: redirect-acl
URL Redirect: https://ise33.aaa.prad.com:8443/portal/gateway?sessionId=16D5C50A0000002CF067366A&portal=ee39fd08-7180-4995-8aa2-9fb282645a8f&action=cpp&token=518f857900a37f9afc6d2da8b6fe3bc2
ACS ACL: xACSACLx-IP-PERMIT_ALL_IPV4_TRAFFIC-57f6b0d3
Method status list:
Method State
dot1x Authc Success
Switch#sh device-tracking database interface te1/0/24
Network Layer Address Link Layer Address Interface vlan prlvl age state Time left
ARP X.X.X.X b496.91f9.568b Te1/0/24 1000 0005 4mn REACHABLE 39 s try 0
|
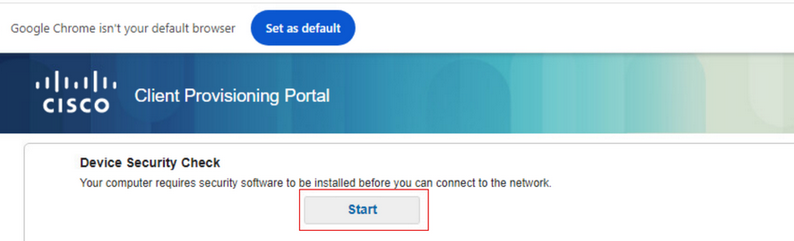
On the Endpoint, verify the traffic redirected to ISE Posture Posture and click Start to download the Network Setup Assistant on the Endpoint.
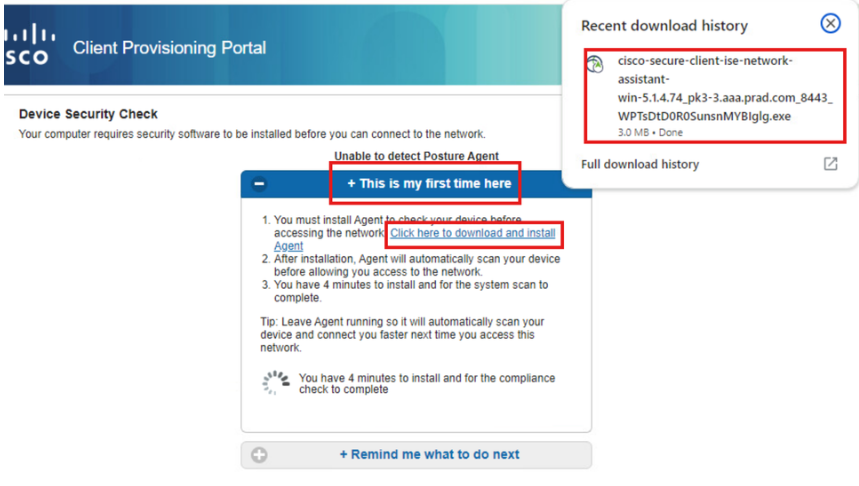
Click Run to install the NSA application.
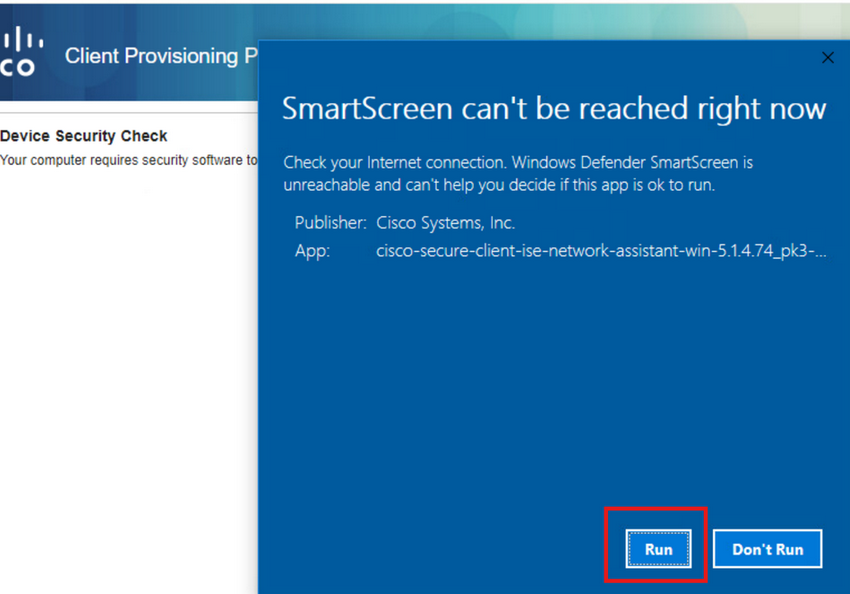
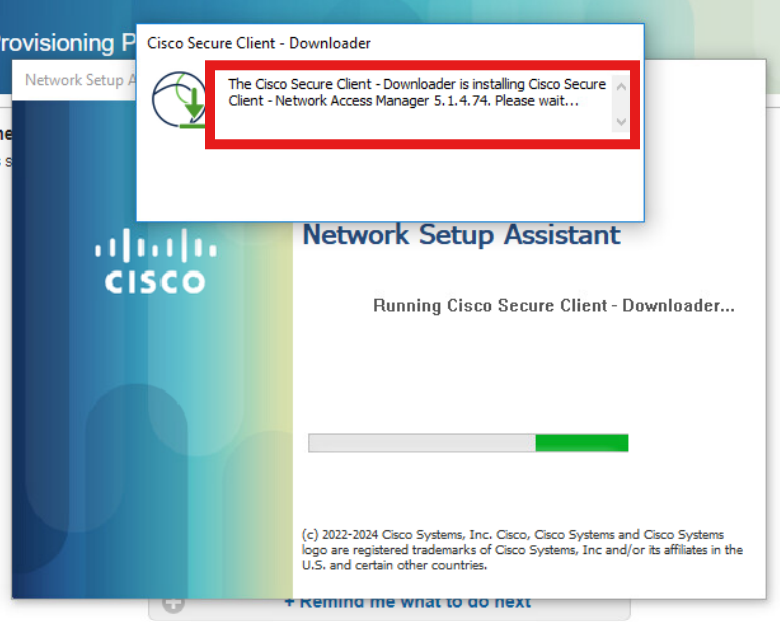
Now, the NSA invokes the Secure Client Agent download from ISE and installs the Posture, NAM module, and NAM Profile configuration.xml .
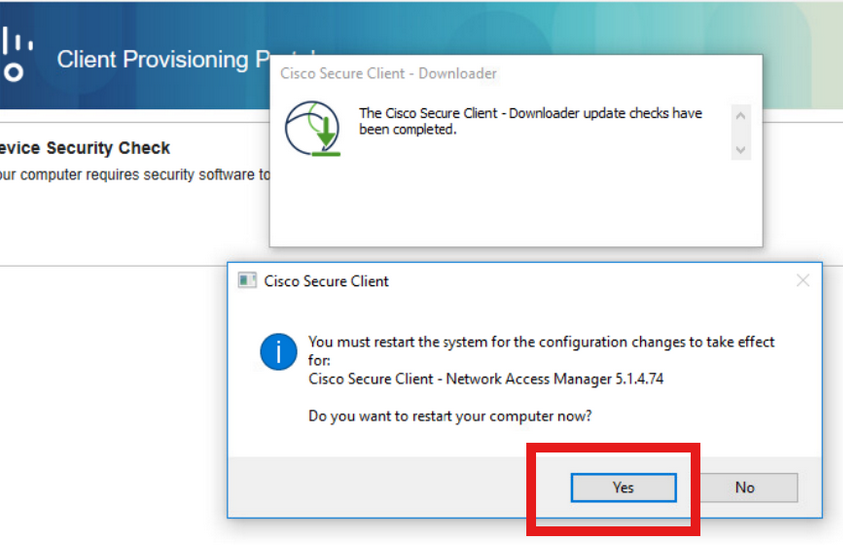
A restart prompt triggered after NAM installation. Click Yes.
Step 2. EAP-FAST
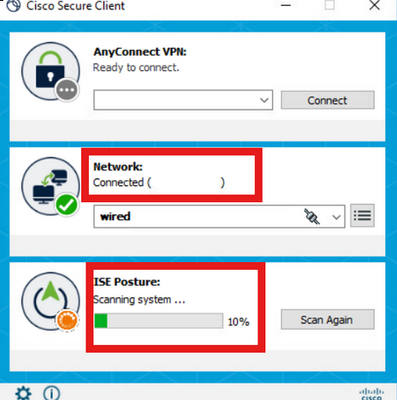
Once the PC restarted and the user logged in, the NAM authenticates both user and machine through EAP-FAST.
If the endpoint authenticates correctly, NAM displays that it is connected and the Posture Module triggers the Posture Scan.
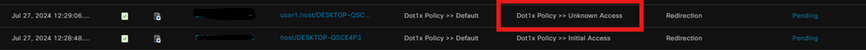
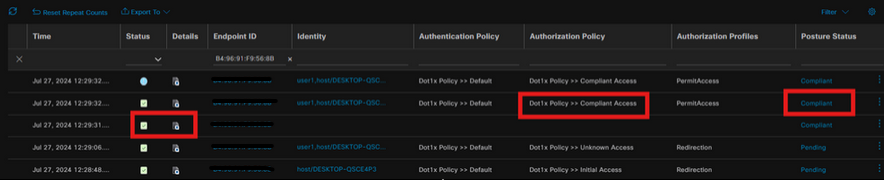
On ISE Live Logs, the Endpoint is now hitting the Unknown Access Rule.
Now the Authentication Protocol is EAP-FAST based on the NAM Profile configuration and EAP-Chaining result is "Success".
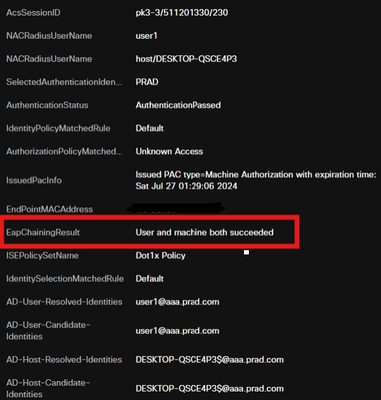
Step 3. Posture Scan
The Secure Client Posture Module triggers the Posture Scan and is marked as Complaint based on the ISE Posture Policy.
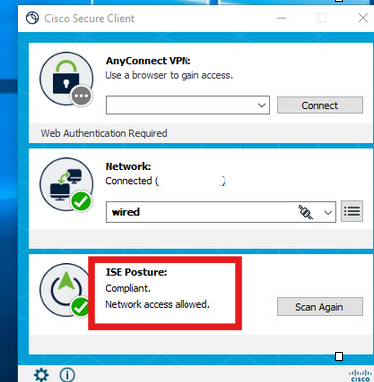
The CoA is triggered after the Posture Scan and now the Endpoint hits the Complaint Access Policy.
Troubleshoot
Step 1. NAM Profile
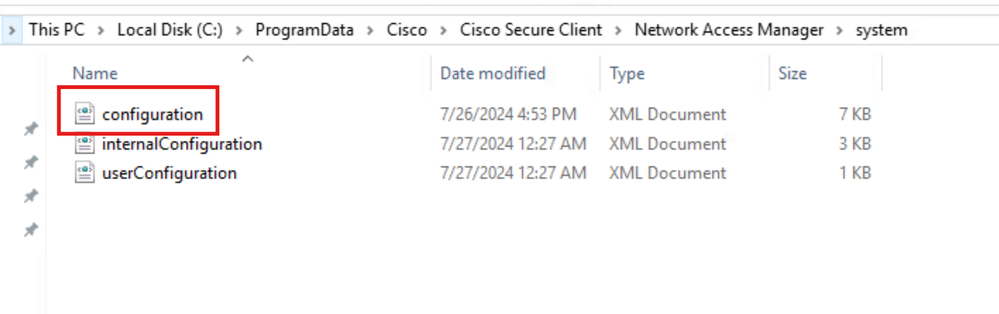
Verify the NAM Profile configuration.xml is present in this path on the PC after the NAM module installation.
C:\ProgramData\Cisco\Cisco Secure Client\Network Access Manager\system
Step 2. NAM Extended Logging
Click on the Secure Client Icon from task bar and select "settings" icon.
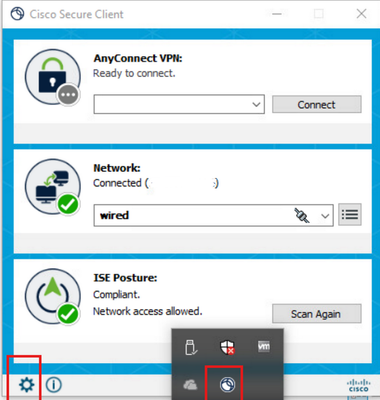
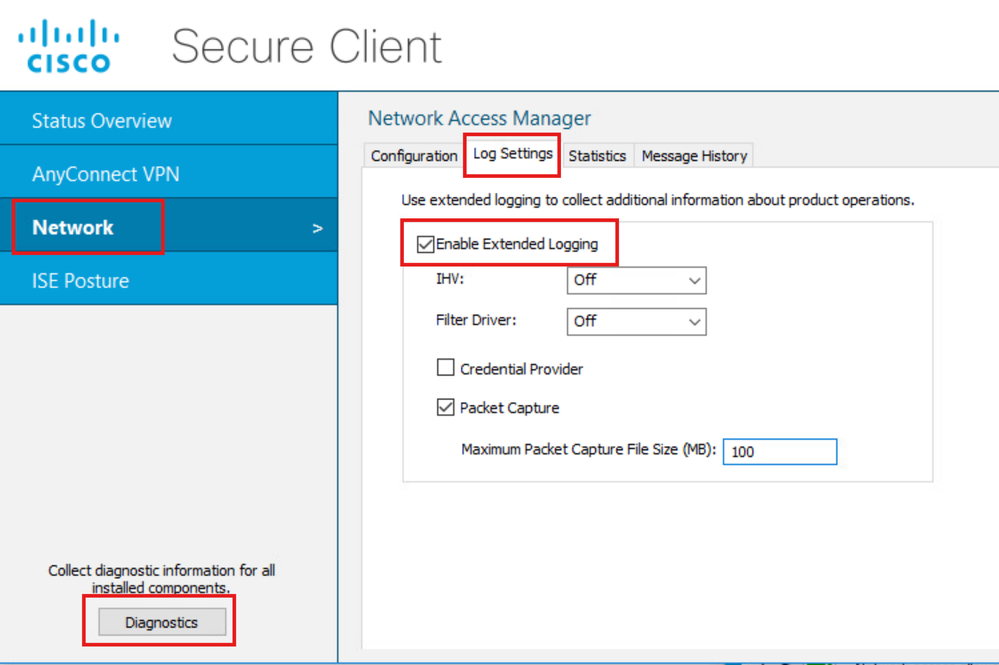
Navigate to the Network > Log Settings tab. Check the Enable Extended Logging checkbox.
Set the Packet Capture File Size to 100 MB.
After reproducing the issue, click on Diagnostics to create the DART Bundle on the Endpoint.
The Message History section displays the details of every step that NAM performed.
Step 3. Debugs on Switch
Enable these debugs on the switch to troubleshoot dot1x and redirection flow.
debug ip http all
debug ip http transactions
debug ip http url
set platform software trace smd switch active R0 aaa debug
set platform software trace smd switch active R0 dot1x-all debug
set platform software trace smd switch active R0 radius debug
set platform software trace smd switch active R0 auth-mgr-all debug
set platform software trace smd switch active R0 eap-all debug
set platform software trace smd switch active R0 epm-all debug
set platform software trace smd switch active R0 epm-redirect debug
set platform software trace smd switch active R0 webauth-aaa debug
set platform software trace smd switch active R0 webauth-httpd debug
To view the logs
show logging
show logging process smd internal
Step 4. Debugs on ISE
Collect the ISE support bundle with these atributes to be set at the debug level:
- posture
- portal
- provisioning
- runtime-AAA
- nsf
- nsf-session
- swiss
- client-webapp
Related Information
Configure Secure Client NAM
ISE Posture Prescriptive Deployment Guide
Troubleshoot Dot1x on Catalyst 9000 Series Switches



































 Feedback
Feedback