Introduction
This document describes how to configure a Static IP Address on Cisco AnyConnect Remote Access VPN with Identity Services Engine (ISE) and Active Directory (AD).
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Configuration of Cisco ISE Versions 3.0
- Configuration of Cisco Adaptive Security Appliance (ASA)/Firepower Threat Defense (FTD)
- VPN Authentication flow
Components Used
The information in this document is based on these software and hardware versions:
- Cisco ISE Version 3.0
- Cisco ASA
- Windows 2016
- Windows 10
- Cisco AnyConnect Client
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
When users perform VPN authentication with a Cisco ASA with the AnyConnect VPN Client software, in some instances it is useful to assign the same static IP address to a client. Here, you can configure a static IP address per user account in AD and use this IP address whenever the user connects to the VPN. ISE can be configured with the attribute msRADIUSFramedIPAddress to query AD to fetch the IP address from AD and assign it to the client whenever they connect.
This document only describes how to configure a static IP address on a Cisco AnyConnect Remote Access VPN.
Configure
AD Configuration
Step 1. Select a test account within AD. Modify the Properties of the test account; select the Dial-in tab as shown in the image.
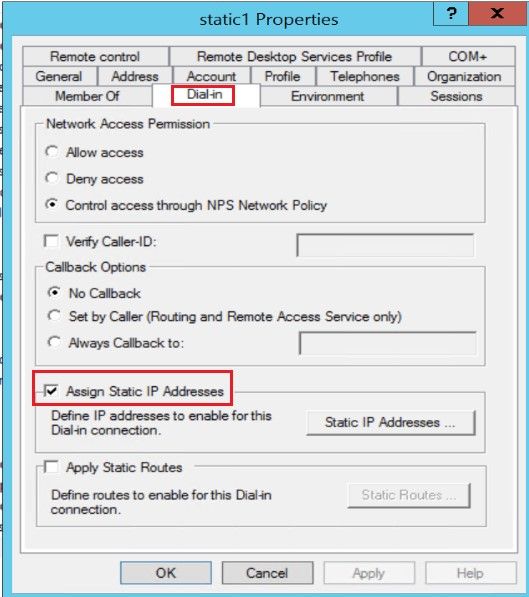
Step 2. Tick the Assign Static IP Addressbox.
Step 3. Click the Static IP Addresses button.
Step 4. Tick the Assign a static IPv4 addressbox and enter an IP Address.
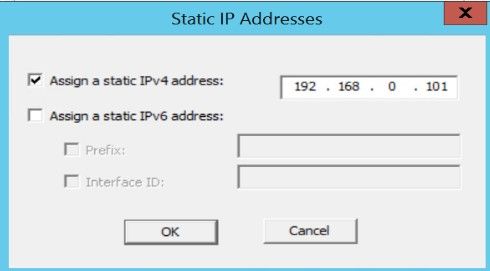

Note: The assigned IP address must not be utilized or included in the DHCP pool.
Step 5. Click OK to complete the configuration.
ISE Configuration
Step 1. Add network Device on ISE and configure RADIUS and shared key. Navigate toISE > Administration > Network Devices > Add Network Device.
Step 2. Integrate ISE with AD. Navigate to ISE > Administration > External Identity Sources > Active Directory > Join ISE to Domain .
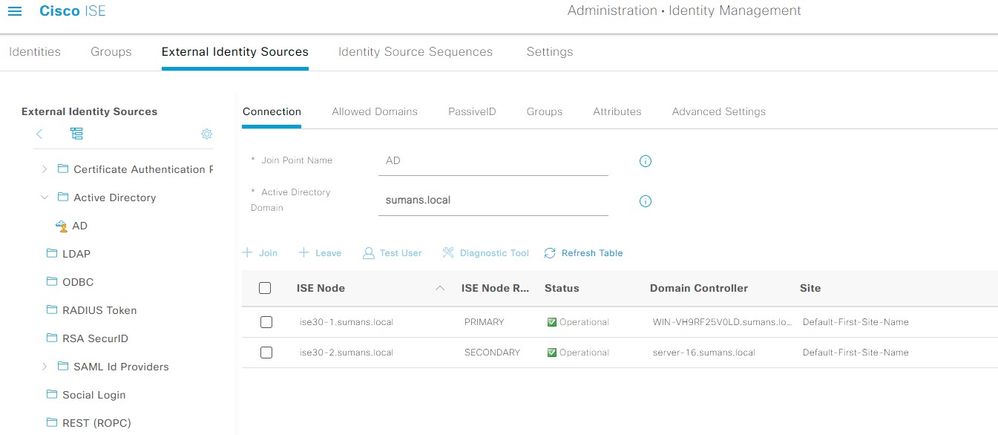
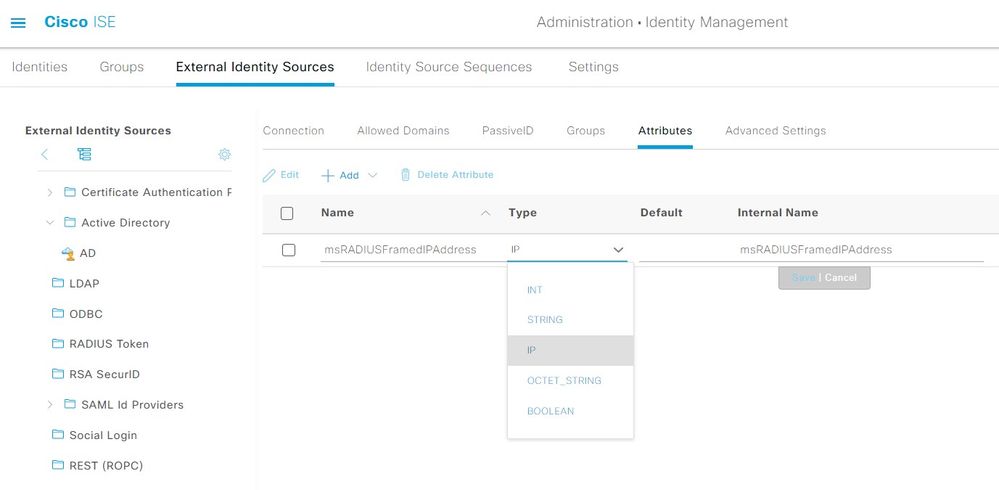
Step 3. Add AD Attribute msRADIUSFramedIPAddress. Navigate to ISE > Administration > External Identity Sources > Active Directory and then select the Joint Point name created. Click on Edit.Then, click the Attributes tab. And, click Add > Select Attributes from Directory.
Enter the name of the test user present on AD to which the Static IP address is assigned and select Retrieve Attributes.
Ensure you tick the box msRADIUSFramedIPAddress and click OK .
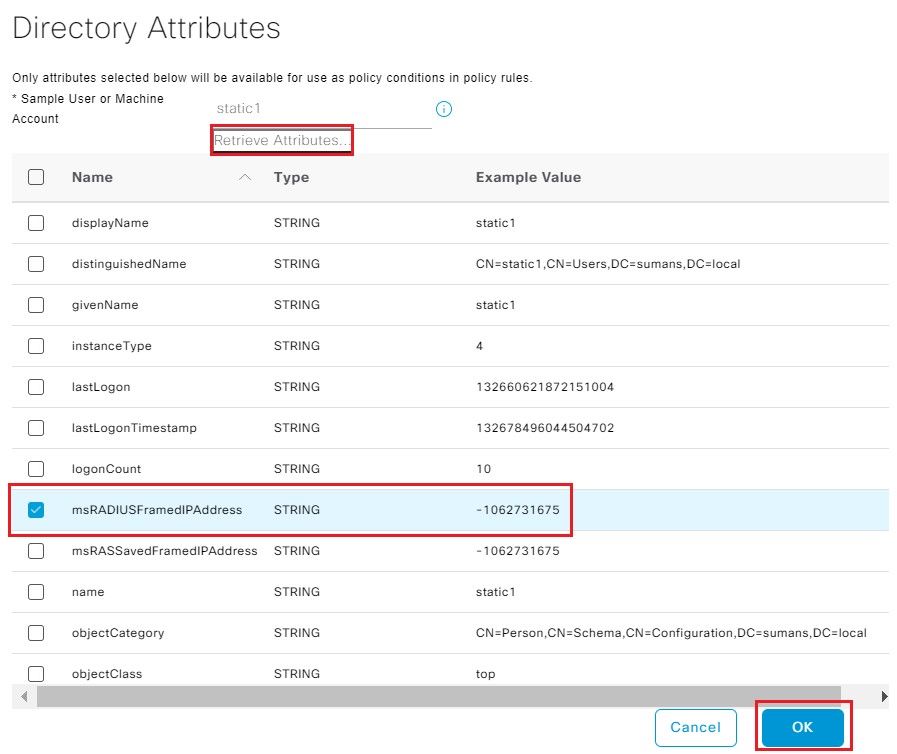
Edit the attribute msRADIUSFramedIPAddress and change the Type value from STRING to IPand click Save.
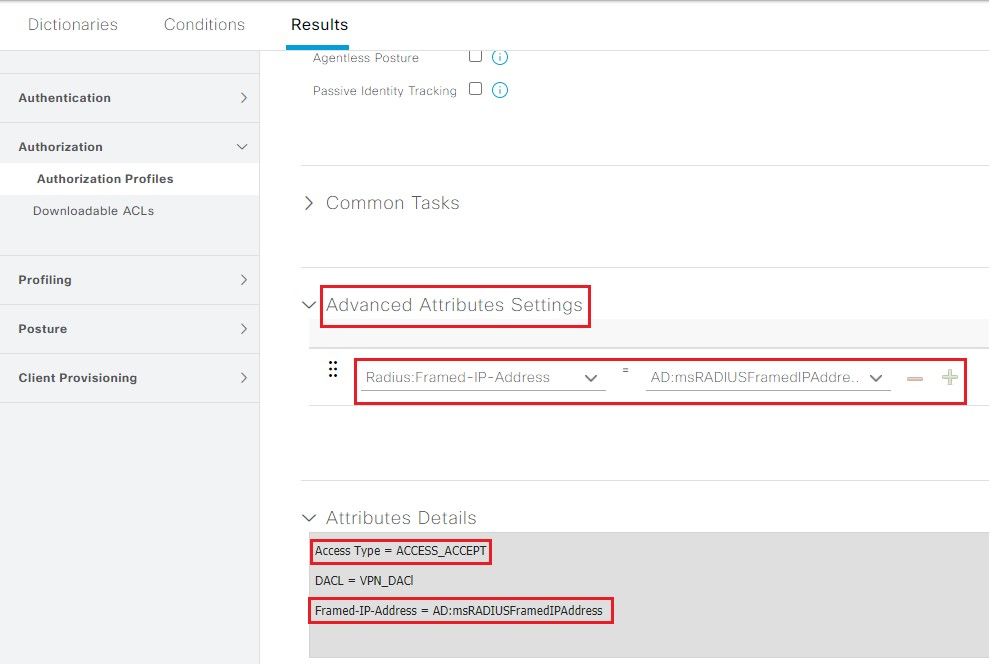
Step 4. Create an Authorization Profile. Navigate to ISE > Policy > Policy Elements > Results > Authorization > Authorization Profiles > Add.
In the Advanced Attributes Settings,add a new value for Radius: Framed-IP-Address and equals the msRADIUSFramedIPAddressvalue previously selected under AD Attributes (in Step 3.).
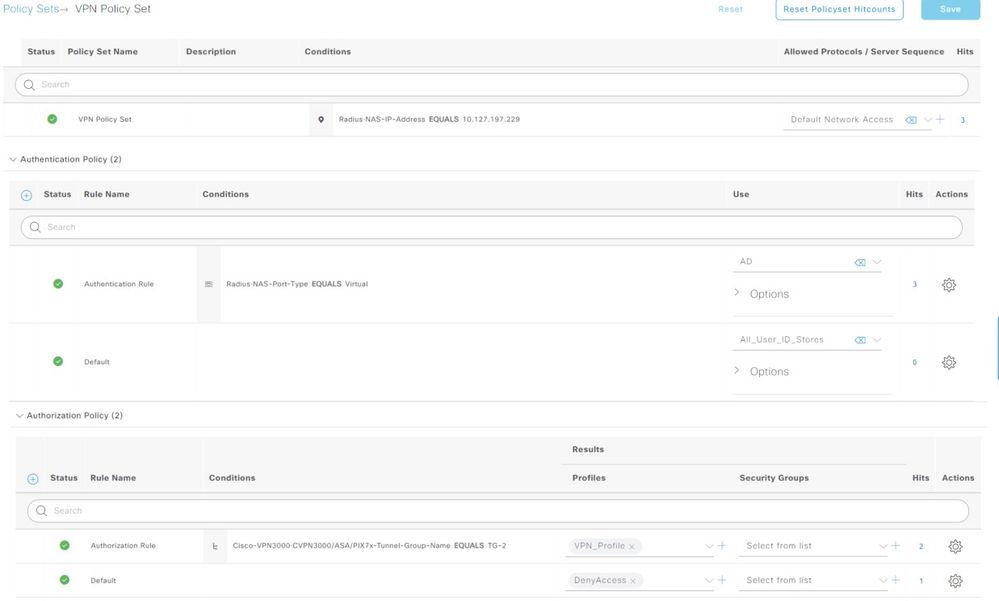
Step 5. Create Policy Set. Navigate to ISE > Policy > Policy Sets. Create a Policy Set and Save. Create an Authentication Policy and select the identity source as Active Directory (joined in Step 2.).Create an Authorization Policy and select the result with the Authorization Profile created (created in Step 4.).
ASA Configuration
Enable WebVPN on the OUTSIDE interface and enable AnyConnect image.
webvpn
enable OUTSIDE
anyconnect image disk0:/anyconnect-win-4.10.00093-webdeploy-k9.pkg 1
anyconnect enable
tunnel-group-list enable
Define AAA Server Group and Server:
aaa-server ISE protocol radius
aaa-server ISE (inside) host 10.127.197.230
key *****
authentication-port 1812
accounting-port 1813
radius-common-pw *****
authorize-only
interim-accounting-update periodic 24
dynamic-authorization
VPN Pool:
ip local pool VPN_POOL 192.168.1.1-192.168.1.50 mask 255.255.255.0
Group Policy:
group-policy GP-1 internal
group-policy GP-1 attributes
dns-server value 10.127.197.254
vpn-tunnel-protocol ssl-client
address-pools value VPN_POOL
Tunnel Group:
tunnel-group TG-2 type remote-access
tunnel-group TG-2 general-attributes
authentication-server-group ISE
default-group-policy GP-1
tunnel-group TG-2 webvpn-attributes
group-alias TG-2 enable
Verify
Use this section in order to confirm that your configuration works properly.
If you have static IP assigned on AD:
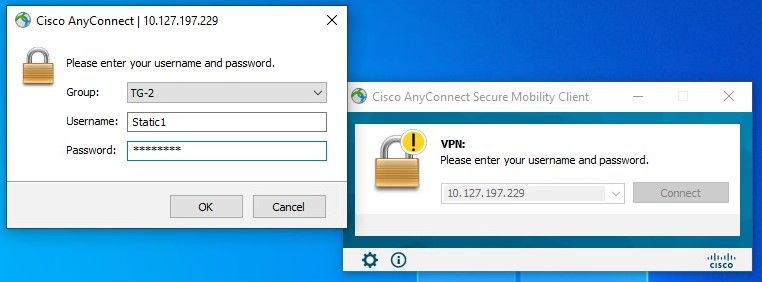
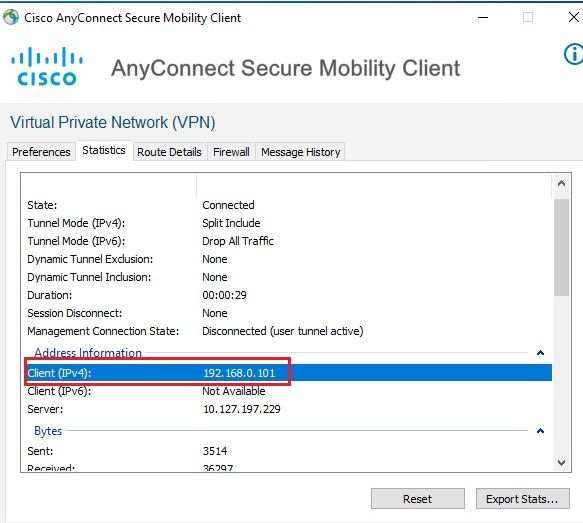
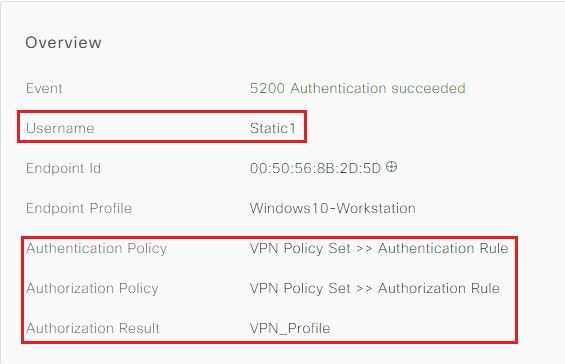
ISE Live logs:
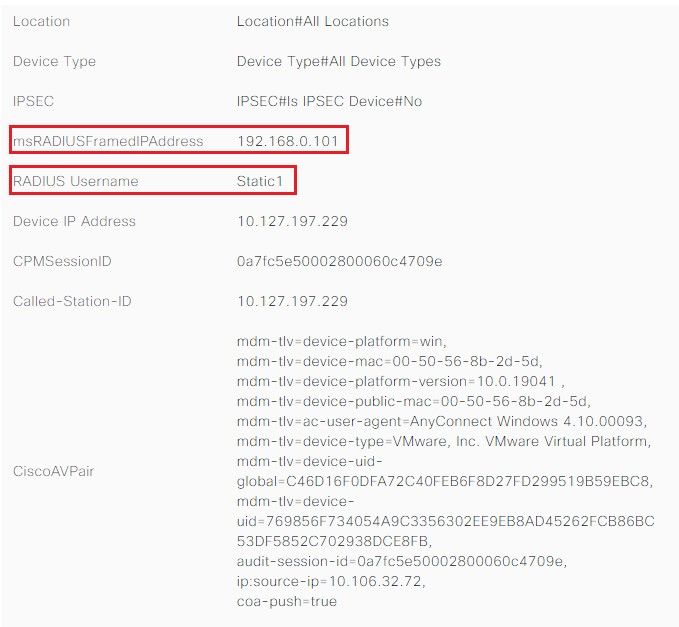
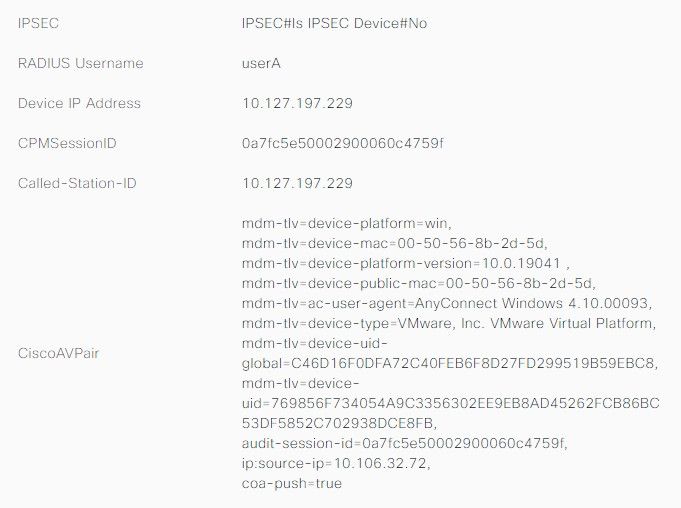
Other Attributes: Here, you can see the attribute msRADIUSFramedIPAddress with an IP address assigned for this user on AD.
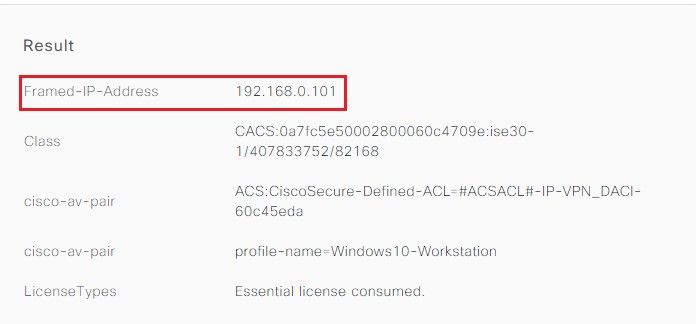
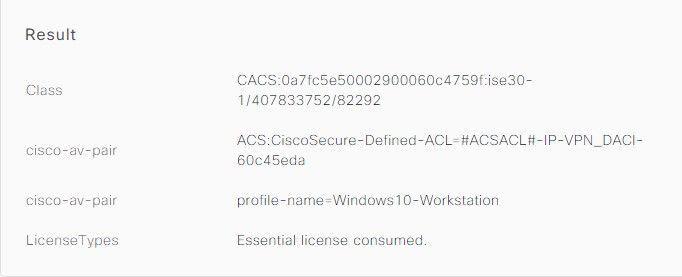
Results: IP Address sent from ISE to ASA.
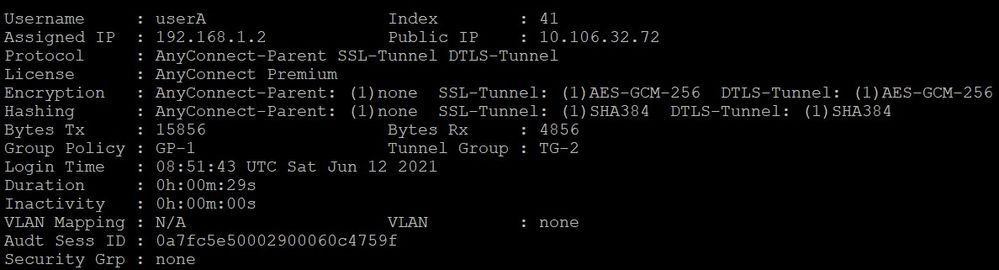
Output from ASA:
Command: show vpn-sessiondb anyconnect
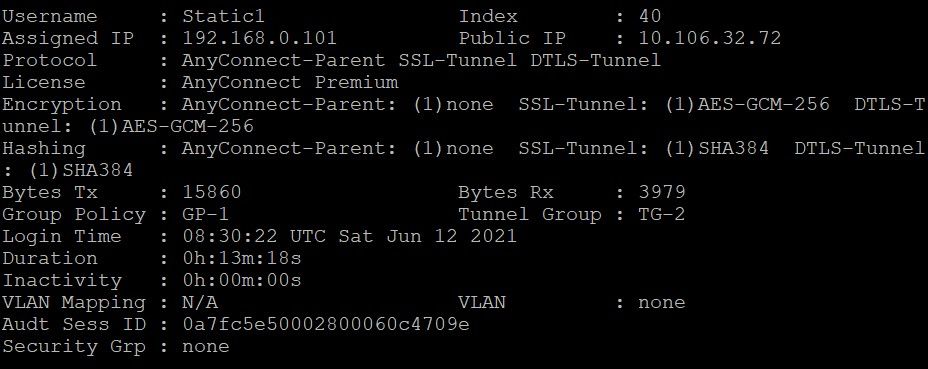
For Users without Static IP Addresses on AD
If the users do not have an IP address assigned on AD, they are assigned with the IP address assigned from local VPN_Pool or DHCP (if configured). Here, the local pool defined on ASA is used.
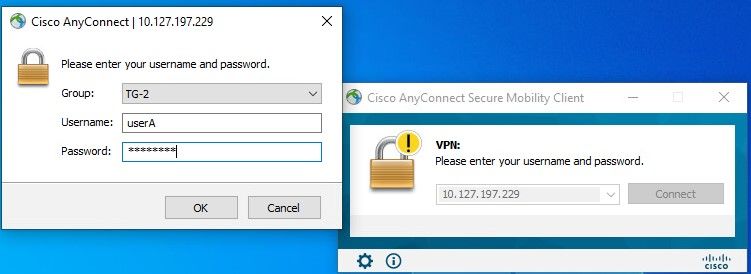
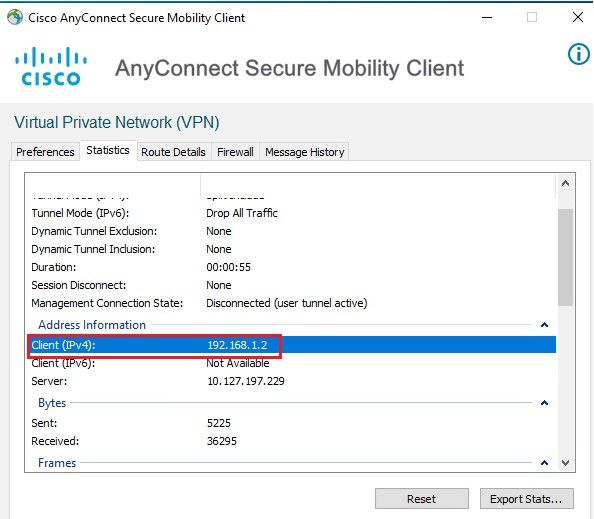
ISE Live logs:
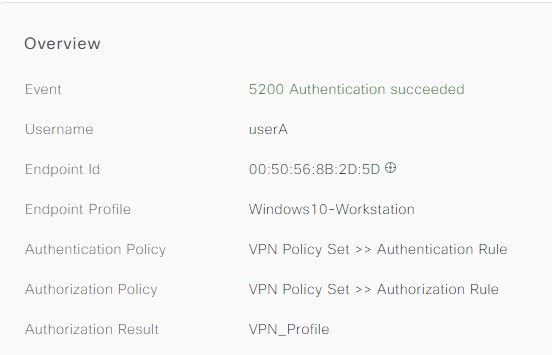
Output from ASA:
Command: show vpn-sessiondb anyconnect
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.





















 Feedback
Feedback