Configure EAP Chaining with TEAP
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how to configure ISE and Windows supplicant for Extensible Authentication Protocol (EAP) Chaining with TEAP.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
-
ISE
-
Configuration of windows supplicant
Components Used
The information in this document is based on these software and hardware versions:
- Cisco ISE version 3.0
- Windows 10 build 2004
- Knowledge of protocol Tunnel-based Extensible Authentication Protocol (TEAP)
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
TEAP is a tunnel-based Extensible Authentication Protocol method that establishes a secure tunnel and executes other EAP methods under the protection of that secured tunnel.
TEAP authentication occurs in two phases after the initial EAP identity request/response exchange. In the first phase, TEAP uses the TLS handshake to provide an authenticated key exchange and to establish a protected tunnel. Once the tunnel is established, the second phase begins with the peer and the server engaging in further conversation to establish the required authentications and authorization policies.
Cisco ISE 2.7 and later supports the TEAP Protocol. The type-length-value (TLV) objects are used within the tunnel to transport authentication-related data between the EAP peer and the EAP server.
Microsoft introduced support for TEAP in Windows version 10 2004 released in May 2020.
EAP chaining allows the user and machine authentication within one EAP/Radius session instead of two separate sessions. Previously, to achieve this you needed the Cisco AnyConnect NAM module and use EAP-FAST on the windows supplicant as the native Windows supplicant did not support this. Now, you can use the Windows Native Supplicant to perform EAP Chaining with ISE 2.7 with the use of TEAP.
Configure
Cisco ISE Configuration
Step 1. You need to edit the Allowed Protocols to enable TEAP and EAP Chaining.
Navigate to ISE > Policy > Policy Elements > Results > Authentication > Allowed Protocols > Add New. Check the TEAP and EAP chaining check boxes.
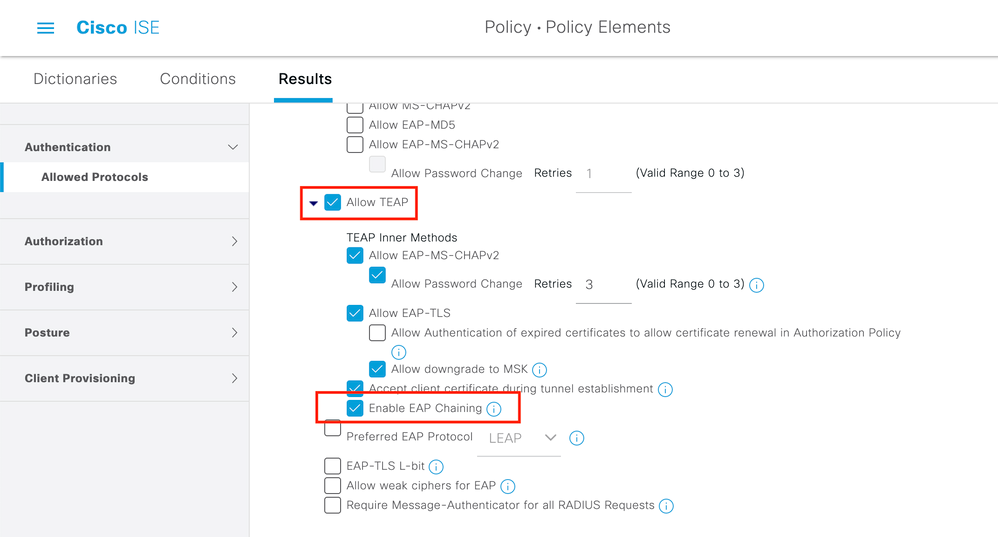
Step 2. Create a certificate profile and add it to the Identity Source Sequence.
Navigate to ISE > Administration > Identities > identity Source Sequence and choose the certificate Profile.
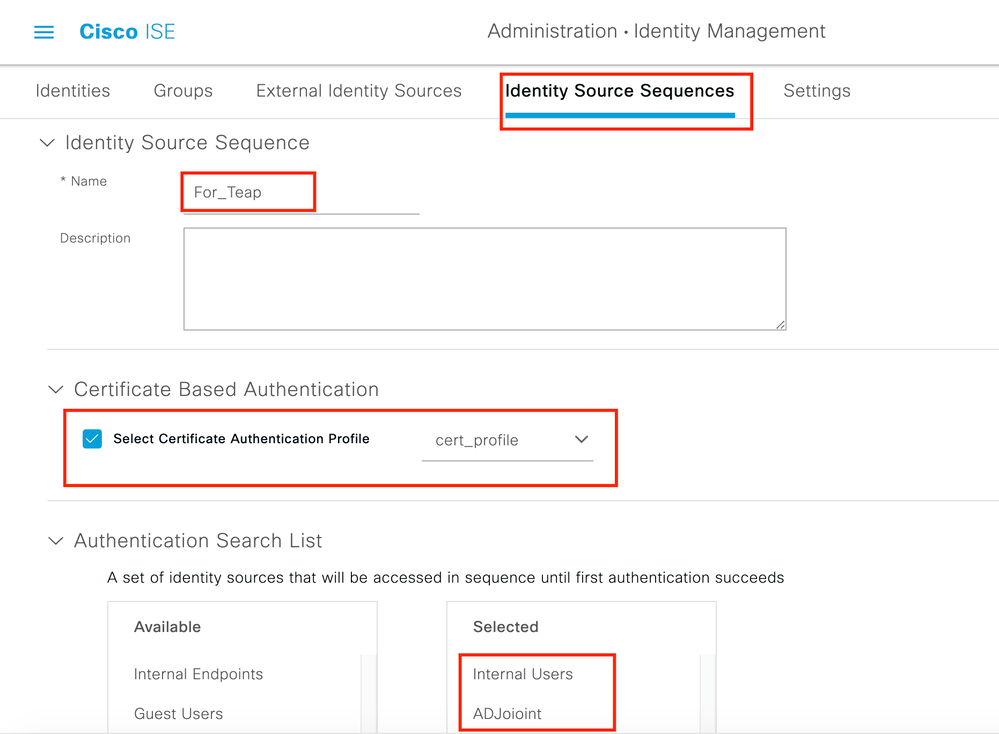
Step 3. You need to call this sequence in the Authentication Policy.
Navigate to ISE > Policy > Policy Sets. Choose the Policy Set forDot1x > Authentication Policy and choose the Identity source sequence created in Step 2.
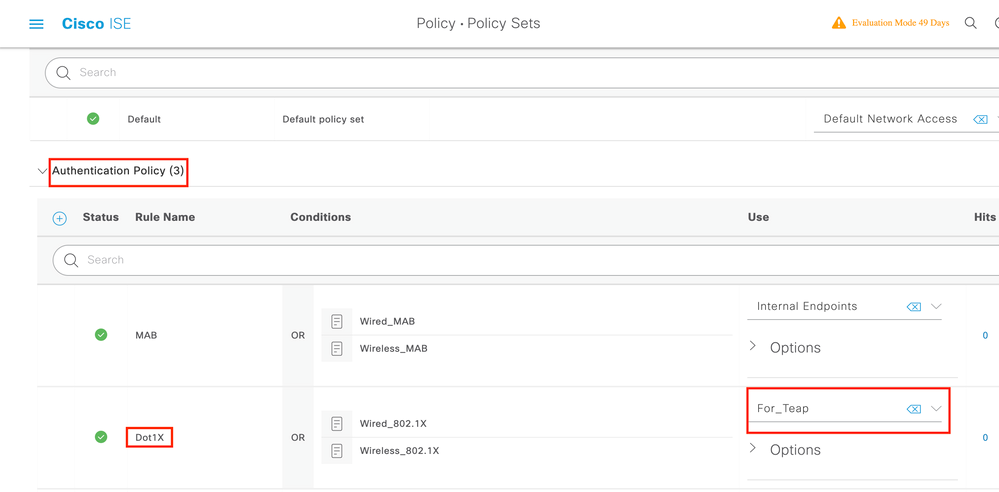
Step 4. Now you need to modify the Authorization Policy under the Dot1x Policy Set.
Navigate to ISE > Policy > Policy Sets. Choose the Policy Set for Dot1x > Authentication Policy.
You need to create two rules. The first rule checks that the machine is authenticated but the user is not. The second rule verifies that both the user and the machine are authenticated.
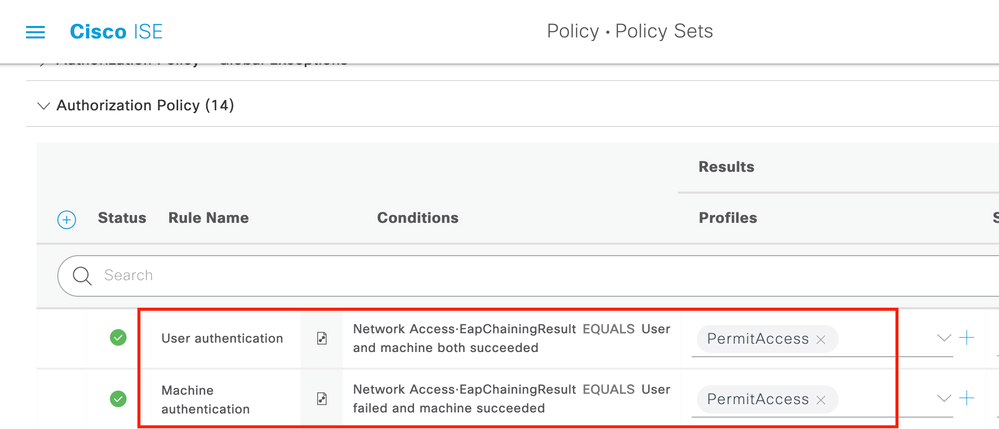
This completes the configuration from the ISE Server side.
Windows Native Supplicant Configuration
Configure the wired authentication setting in this document.
Navigate to Control Panel > Network and Sharing Center > Change Adapter Settings and right-click LAN Connection > Properties. Click the Authentication tab.
Step 1. Click Authenticationdrop-down and choose Microsoft EAP-TEAP.
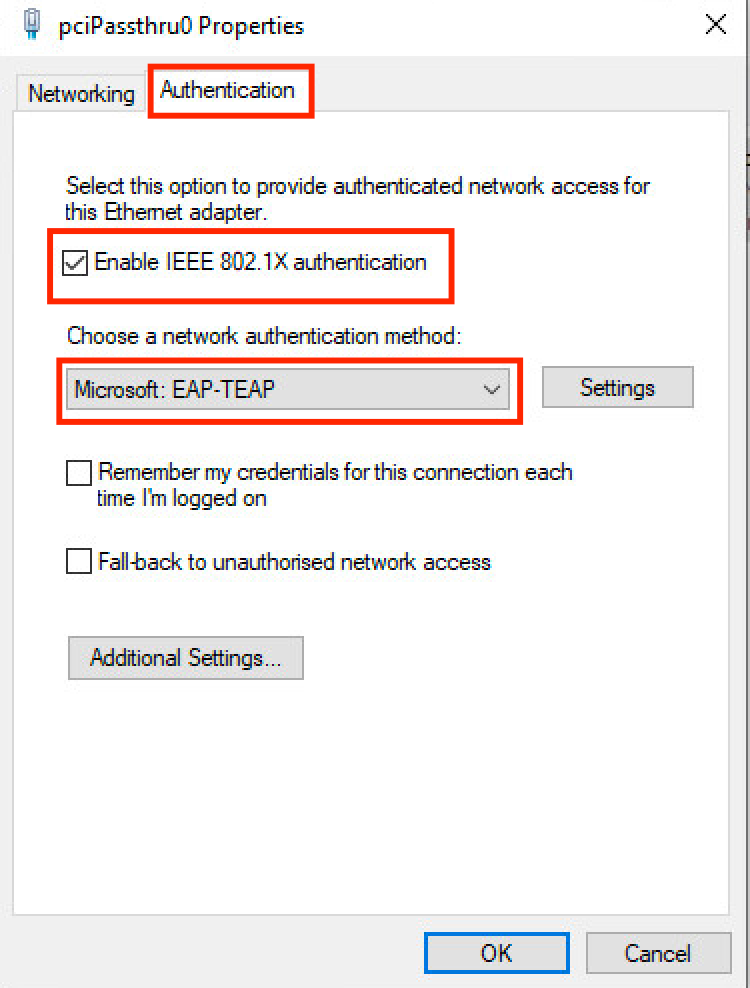
Step 2. Click theSettings button next to TEAP.
- Keep
Enable Identity Privacyenabled withanonymousas the identity. - Put a checkmark next to the root CA server(s) under Trusted Root Certification Authorities that are used to sign the certificate for EAP authentication on the ISE PSN.
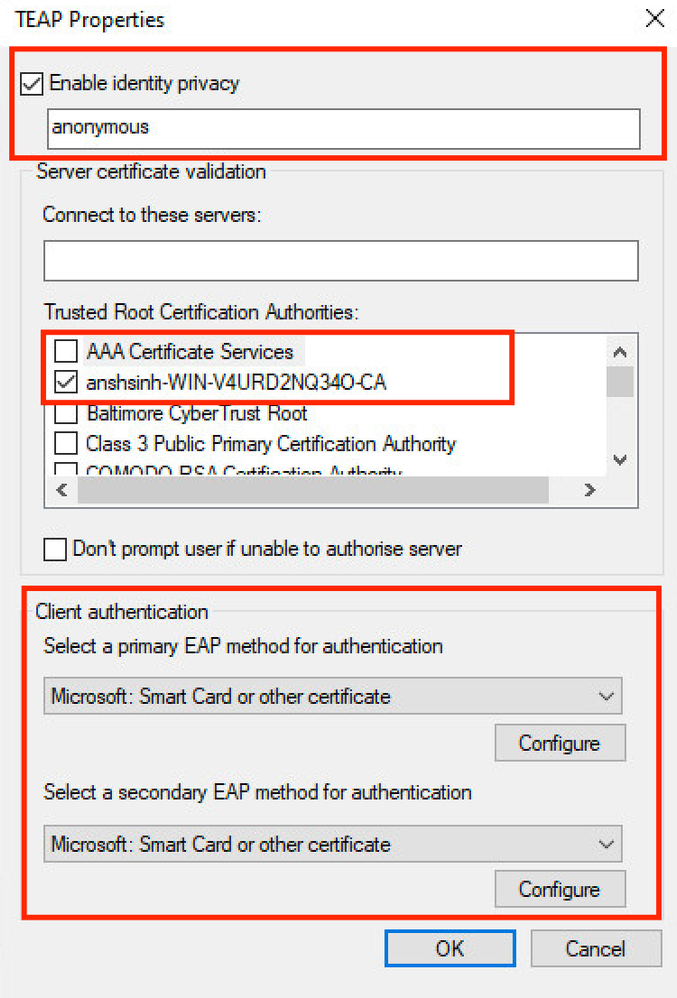
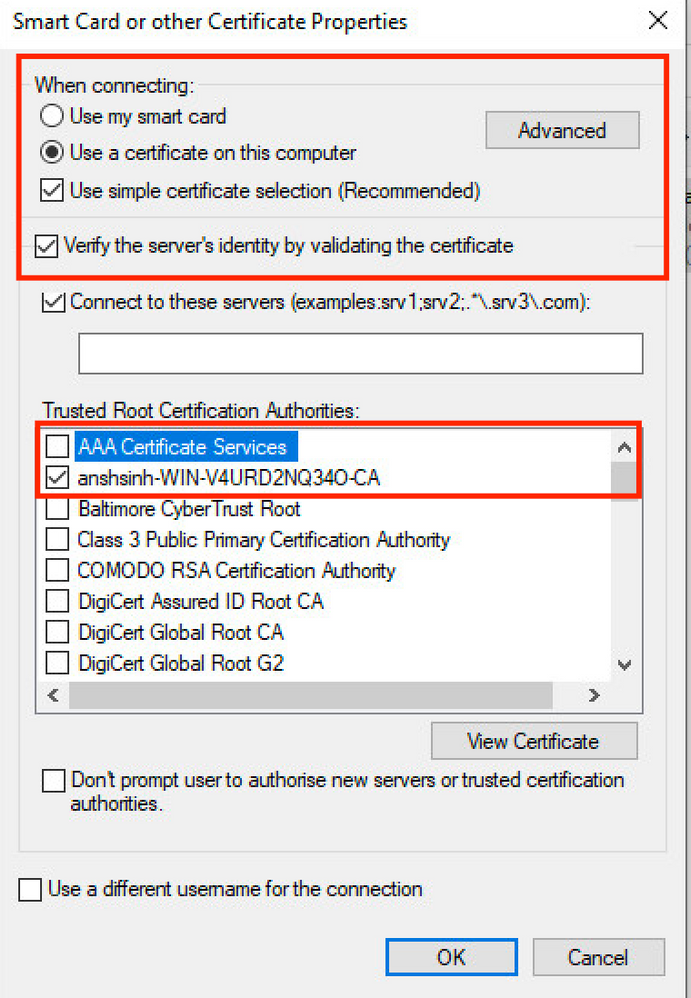
Step 3. Under Client Authentication, choose the EAP method for authentication to Microsoft: Smart Card of other certificate.
Step 4. For each EAP method dropdown, click the Configurebutton and modify as per requirement and click OK.
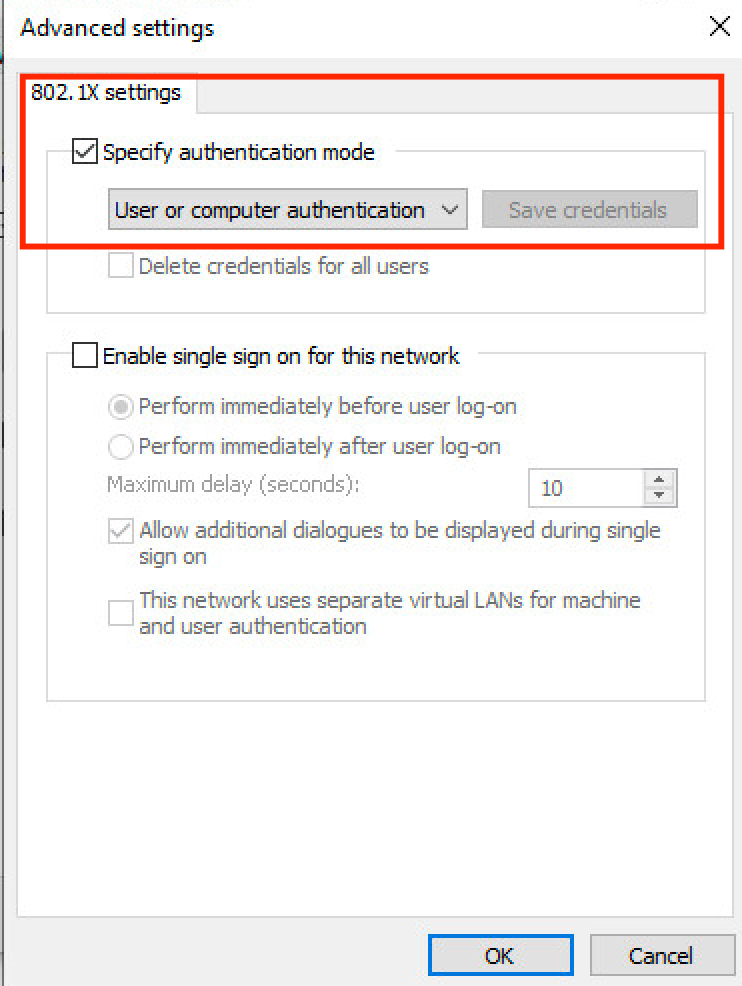
Step 5. Click the Additional Settings button at the bottom.
- Enable Specify authentication mode.
- Set the drop-down to the appropriate setting.
- Choose
User or computer authenticationso that both are authenticated and clickOK.
Verify
You can reboot the Windows 10 machine or you can sign out and then sign in. Whenever the windows log in screen is displayed, machine authentication is triggered.
In the live logs, you see anonymous, host/Administrator (here is the machine name) in the identity field. You see anonymous because you configured supplicant for identity privacy above.
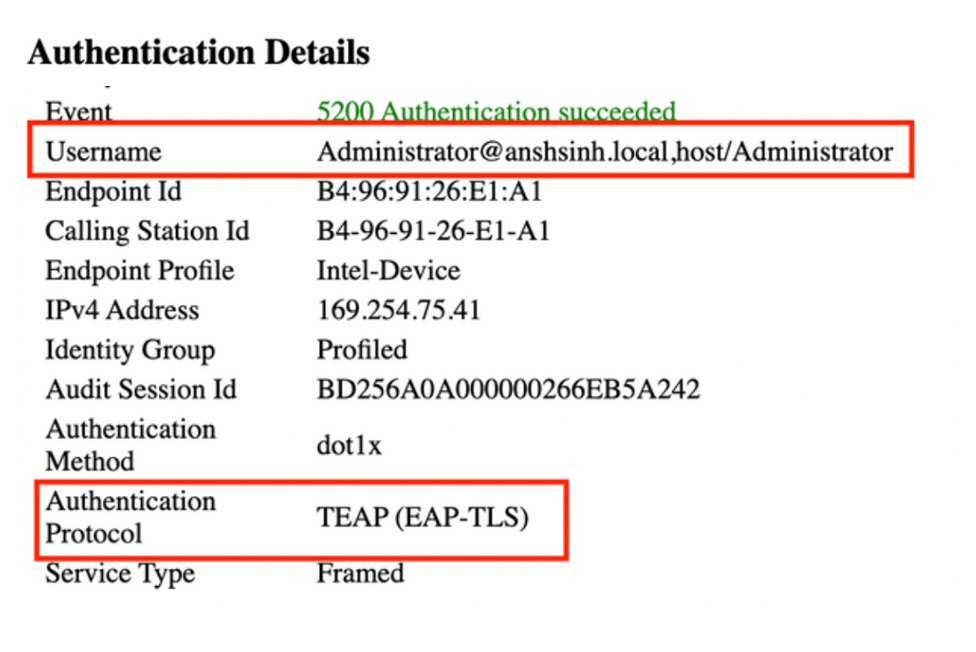
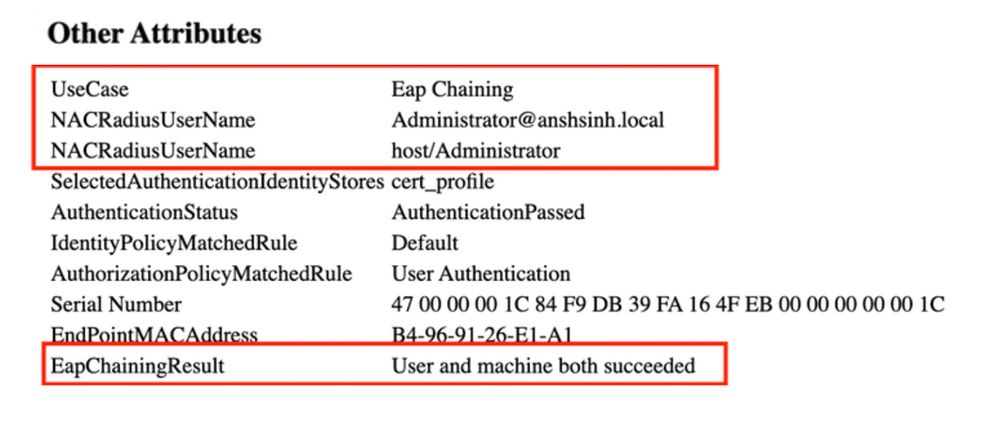
When you log in to the PC with credentials, you can see in the live logs Administrator@example.local, host/Administrator. This is EAP chaining where both user and machine authentication happened in one EAP session.
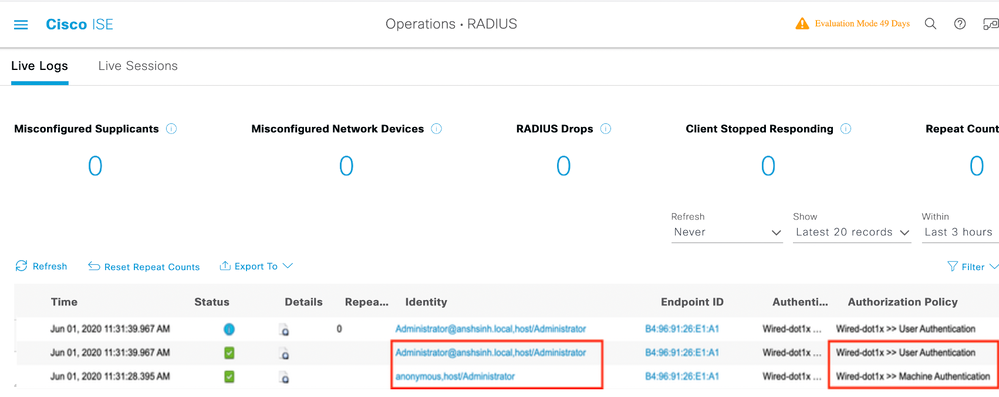
Detailed Authentication Report
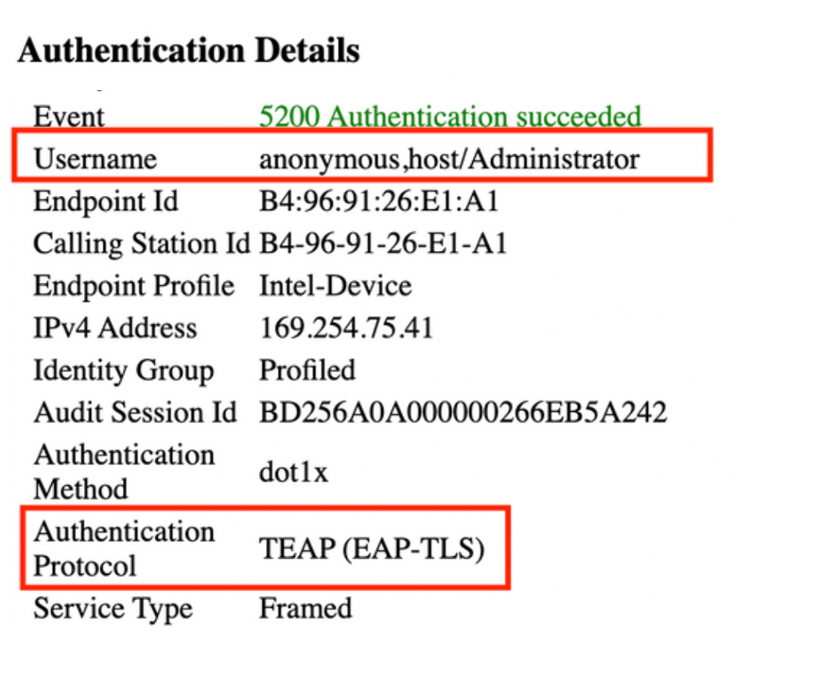
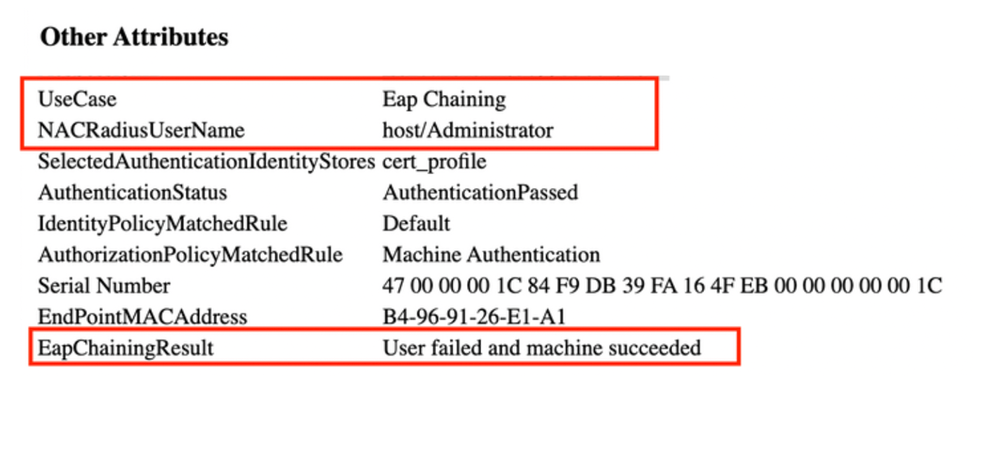
In the Live Log Details, Machine authentications only show a single NACRadiusUsername entry but the chained user and machine authentication shows two entries (one for the user, and one for the machine). Also, you see under the Authentication Details section, that TEAP (EAP-TLS) was used for the Authentication Protocol. If you use MSCHAPv2 for machine and user authentication, the authentication protocol shows TEAP (Microsoft: Secured password (EAP-MSCHAP v2)).
Machine Authentication
User and Machine Authentication
Troubleshoot
You need to enable these debugs on ISE:
runtime-AAAnsfnsf-sessionActive Directory (to troubleshoot between ISE and AD)
On Windows, you can check the Event Viewer logs.
Live Log Analysis
Machine Authentication
11001 Received RADIUS Access-Request 11017 RADIUS created a new session ... ... 11507 Extracted EAP-Response/Identity 12756 Prepared EAP-Request proposing TEAP with challenge ... ... 12758 Extracted EAP-Response containing TEAP challenge-response and accepting TEAP as negotiated 12800 Extracted first TLS record; TLS handshake started 12805 Extracted TLS ClientHello message 12806 Prepared TLS ServerHello message 12807 Prepared TLS Certificate message 12808 Prepared TLS ServerKeyExchange message 12809 Prepared TLS CertificateRequest message ... ... 12811 Extracted TLS Certificate message containing client certificate 12812 Extracted TLS ClientKeyExchange message 12813 Extracted TLS CertificateVerify message 12804 Extracted TLS Finished message 12801 Prepared TLS ChangeCipherSpec message 12802 Prepared TLS Finished message 12816 TLS handshake succeeded ... ... 11559 Client certificate was requested but not received inside the tunnel. Will continue with inner method. 11620 TEAP full handshake finished successfully ... ... 11627 Starting EAP chaining 11573 Selected identity type 'User' 11564 TEAP inner method started 11521 Prepared EAP-Request/Identity for inner EAP method ... ... 11567 Identity type provided by client is equal to requested 11522 Extracted EAP-Response/Identity for inner EAP method 11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge 11596 Prepared EAP-Request with another TEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request ... ... 11515 Supplicant declined inner EAP method selected by Authentication Policy but did not proposed another one; inner EAP negotiation failed 11520 Prepared EAP-Failure for inner EAP method 11566 TEAP inner method finished with failure 22028 Authentication failed and the advanced options are ignored 33517 Sent TEAP Intermediate Result TLV indicating failure 11596 Prepared EAP-Request with another TEAP challenge ... ... 11574 Selected identity type 'Machine' 11564 TEAP inner method started 11521 Prepared EAP-Request/Identity for inner EAP method ... ... 11567 Identity type provided by client is equal to requested 11522 Extracted EAP-Response/Identity for inner EAP method 11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge 11596 Prepared EAP-Request with another TEAP challenge ... ... 12523 Extracted EAP-Response/NAK for inner method requesting to use EAP-TLS instead 12522 Prepared EAP-Request for inner method proposing EAP-TLS with challenge 12625 Valid EAP-Key-Name attribute received 11596 Prepared EAP-Request with another TEAP challenge ... ... 12524 Extracted EAP-Response containing EAP-TLS challenge-response for inner method and accepting EAP-TLS as negotiated 12800 Extracted first TLS record; TLS handshake started 12545 Client requested EAP-TLS session ticket 12546 The EAP-TLS session ticket received from supplicant. Inner EAP-TLS does not support stateless session resume. Performing full authentication 12805 Extracted TLS ClientHello message 12806 Prepared TLS ServerHello message 12807 Prepared TLS Certificate message 12808 Prepared TLS ServerKeyExchange message 12809 Prepared TLS CertificateRequest message 12527 Prepared EAP-Request for inner method with another EAP-TLS challenge ... ... 12571 ISE will continue to CRL verification if it is configured for specific CA - certificate for Users 12811 Extracted TLS Certificate message containing client certificate 12812 Extracted TLS ClientKeyExchange message 12813 Extracted TLS CertificateVerify message 12804 Extracted TLS Finished message 12801 Prepared TLS ChangeCipherSpec message 12802 Prepared TLS Finished message 12816 TLS handshake succeeded 12509 EAP-TLS full handshake finished successfully ... ... 12527 Prepared EAP-Request for inner method with another EAP-TLS challenge 11596 Prepared EAP-Request with another TEAP challenge ... ... 61025 Open secure connection with TLS peer 15041 Evaluating Identity Policy 22072 Selected identity source sequence - forAD1 22070 Identity name is taken from certificate attribute 22037 Authentication Passed 12528 Inner EAP-TLS authentication succeeded 11519 Prepared EAP-Success for inner EAP method 11565 TEAP inner method finished successfully ... ... 33516 Sent TEAP Intermediate Result TLV indicating success 11596 Prepared EAP-Request with another TEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 11595 Extracted EAP-Response containing TEAP challenge-response 11637 Inner method supports EMSK but the client provided only MSK. Allow downgrade as per configuration 11576 TEAP cryptobinding verification passed ... ... 15036 Evaluating Authorization Policy 24209 Looking up Endpoint in Internal Endpoints IDStore - anonymous,host/Administrator 24211 Found Endpoint in Internal Endpoints IDStore 11055 User name change detected for the session. Attributes for the session will be removed from the cache 15048 Queried PIP - Network Access.EapChainingResult 15016 Selected Authorization Profile - PermitAccess 33514 Sent TEAP Result TLV indicating success ... ... 11597 TEAP authentication phase finished successfully 11503 Prepared EAP-Success 11002 Returned RADIUS Access-Accept
User and Machine Authentication
11001 Received RADIUS Access-Request 11017 RADIUS created a new session ... ... 12756 Prepared EAP-Request proposing TEAP with challenge ... ... 12758 Extracted EAP-Response containing TEAP challenge-response and accepting TEAP as negotiated 12800 Extracted first TLS record; TLS handshake started 12805 Extracted TLS ClientHello message 12806 Prepared TLS ServerHello message 12807 Prepared TLS Certificate message 12808 Prepared TLS ServerKeyExchange message 12809 Prepared TLS CertificateRequest message 11596 Prepared EAP-Request with another TEAP challenge ... ... 12811 Extracted TLS Certificate message containing client certificate 12812 Extracted TLS ClientKeyExchange message 12813 Extracted TLS CertificateVerify message 12804 Extracted TLS Finished message 12801 Prepared TLS ChangeCipherSpec message 12802 Prepared TLS Finished message 12816 TLS handshake succeeded 11559 Client certificate was requested but not received inside the tunnel. Will continue with inner method. 11620 TEAP full handshake finished successfully 11596 Prepared EAP-Request with another TEAP challenge ... ... 11595 Extracted EAP-Response containing TEAP challenge-response 11627 Starting EAP chaining 11573 Selected identity type 'User' 11564 TEAP inner method started 11521 Prepared EAP-Request/Identity for inner EAP method 11596 Prepared EAP-Request with another TEAP challenge ... ... 11567 Identity type provided by client is equal to requested 11522 Extracted EAP-Response/Identity for inner EAP method 11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge 11596 Prepared EAP-Request with another TEAP challenge ... ... 12523 Extracted EAP-Response/NAK for inner method requesting to use EAP-TLS instead 12522 Prepared EAP-Request for inner method proposing EAP-TLS with challenge ... ... 11595 Extracted EAP-Response containing TEAP challenge-response 12524 Extracted EAP-Response containing EAP-TLS challenge-response for inner method and accepting EAP-TLS as negotiated 12800 Extracted first TLS record; TLS handshake started 12545 Client requested EAP-TLS session ticket 12546 The EAP-TLS session ticket received from supplicant. Inner EAP-TLS does not support stateless session resume. Performing full authentication 12805 Extracted TLS ClientHello message 12806 Prepared TLS ServerHello message 12807 Prepared TLS Certificate message 12808 Prepared TLS ServerKeyExchange message 12809 Prepared TLS CertificateRequest message 12527 Prepared EAP-Request for inner method with another EAP-TLS challenge ... ... 12526 Extracted EAP-Response for inner method containing TLS challenge-response 12571 ISE will continue to CRL verification if it is configured for specific CA - certificate for Users 12811 Extracted TLS Certificate message containing client certificate 12812 Extracted TLS ClientKeyExchange message 12813 Extracted TLS CertificateVerify message 12804 Extracted TLS Finished message 12801 Prepared TLS ChangeCipherSpec message 12802 Prepared TLS Finished message 12816 TLS handshake succeeded 12509 EAP-TLS full handshake finished successfully 12527 Prepared EAP-Request for inner method with another EAP-TLS challenge ... ... 12526 Extracted EAP-Response for inner method containing TLS challenge-response 61025 Open secure connection with TLS peer 15041 Evaluating Identity Policy 22072 Selected identity source sequence - forAD1 22070 Identity name is taken from certificate attribute 22037 Authentication Passed 12528 Inner EAP-TLS authentication succeeded 11519 Prepared EAP-Success for inner EAP method 11565 TEAP inner method finished successfully 33516 Sent TEAP Intermediate Result TLV indicating success 11596 Prepared EAP-Request with another TEAP challenge ... ... 11595 Extracted EAP-Response containing TEAP challenge-response 11637 Inner method supports EMSK but the client provided only MSK. Allow downgrade as per configuration 11576 TEAP cryptobinding verification passed 11574 Selected identity type 'Machine' 11564 TEAP inner method started ... ... 11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge 11596 Prepared EAP-Request with another TEAP challenge ... ... 12523 Extracted EAP-Response/NAK for inner method requesting to use EAP-TLS instead 12522 Prepared EAP-Request for inner method proposing EAP-TLS with challenge ... ... 12524 Extracted EAP-Response containing EAP-TLS challenge-response for inner method and accepting EAP-TLS as negotiated 12800 Extracted first TLS record; TLS handshake started 12545 Client requested EAP-TLS session ticket 12546 The EAP-TLS session ticket received from supplicant. Inner EAP-TLS does not support stateless session resume. Performing full authentication 12805 Extracted TLS ClientHello message 12806 Prepared TLS ServerHello message 12807 Prepared TLS Certificate message 12808 Prepared TLS ServerKeyExchange message 12809 Prepared TLS CertificateRequest message 12527 Prepared EAP-Request for inner method with another EAP-TLS challenge ... ... 12526 Extracted EAP-Response for inner method containing TLS challenge-response 12571 ISE will continue to CRL verification if it is configured for specific CA - certificate for Users 12811 Extracted TLS Certificate message containing client certificate 12812 Extracted TLS ClientKeyExchange message 12813 Extracted TLS CertificateVerify message 12804 Extracted TLS Finished message 12801 Prepared TLS ChangeCipherSpec message 12802 Prepared TLS Finished message 12816 TLS handshake succeeded 12509 EAP-TLS full handshake finished successfully 12527 Prepared EAP-Request for inner method with another EAP-TLS challenge 11596 Prepared EAP-Request with another TEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 11595 Extracted EAP-Response containing TEAP challenge-response 12526 Extracted EAP-Response for inner method containing TLS challenge-response 61025 Open secure connection with TLS peer 15041 Evaluating Identity Policy 22072 Selected identity source sequence - forAD1 22070 Identity name is taken from certificate attribute 22037 Authentication Passed 12528 Inner EAP-TLS authentication succeeded 11519 Prepared EAP-Success for inner EAP method 11565 TEAP inner method finished successfully 33516 Sent TEAP Intermediate Result TLV indicating success 11596 Prepared EAP-Request with another TEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 11595 Extracted EAP-Response containing TEAP challenge-response 11637 Inner method supports EMSK but the client provided only MSK. Allow downgrade as per configuration 11576 TEAP cryptobinding verification passed 15036 Evaluating Authorization Policy 24209 Looking up Endpoint in Internal Endpoints IDStore - Administrator@example.local,host/Administrator 24211 Found Endpoint in Internal Endpoints IDStore 11055 User name change detected for the session. Attributes for the session will be removed from the cache 15048 Queried PIP - Network Access.EapChainingResult 15016 Selected Authorization Profile - PermitAccess 33514 Sent TEAP Result TLV indicating success 11596 Prepared EAP-Request with another TEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 11595 Extracted EAP-Response containing TEAP challenge-response 11597 TEAP authentication phase finished successfully 11503 Prepared EAP-Success 11002 Returned RADIUS Access-Accept
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
3.0 |
18-Jun-2024 |
Updated Title, Introduction, Alt Text, Machine Translation, and Formatting. |
1.0 |
10-Dec-2020 |
Initial Release |
Contributed by Cisco Engineers
- Anshu SinhaASIC Engineering Technical Leader
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback