Introduction
This document describes a problem seen to allow users to get access to the Xbox live online multi-player feature from the Xbox when connected behind an FTD (FirePower Threat Defense) sensor. Every time you try to establish an online multi-player connection from the Xbox, it does not work through the FTD sensor.
This problem is seen after you migrate the firewall services from a Cisco ASA (Adaptive Security Appliance) to a FirePower with FTD.
The main purpose of this document is to explain how to allow the Xbox live online multi-player traffic (Teredo tunnel UDP 3544) to work through the FTD.
Contributed by Christian G. Hernandez R., Cisco TAC Engineer.
Prerequisites
Requirements
Cisco recommends that you have knowledge of the Cisco FirePower pre-filter rules configuration.
Components Used
The information in this document is based on these software and hardware versions:
- Cisco FMC (FirePower Management Center) v6.2.3.1
- Cisco FTD v6.2.3.1
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
The Xbox live online multi-player feature for the Xbox establishes a Teredo tunnel that uses the UDP port 3544, just as confirmed in the next Microsoft Xbox document:
Network ports used by Xbox Live on Xbox One
Problem: Xbox Live Online Multi-Player Traffic (Teredo Tunnel UDP 3544) Blocked By FTD
It is confirmed the FTD sensors block the Xbox live online multi-player traffic (Teredo tunnel UDP 3544) if you don't use the factory default pre-filter rules from the FMC:
Default pre-filter policy seen from the FMC GUI (Graphic User Interface):


Default pre-filter policy seen from an FTD sensor CLI (Command Line Interface):
> show access-list
access-list cached ACL log flows: total 0, denied 0 (deny-flow-max 4096)
alert-interval 300
access-list CSM_FW_ACL_; 8 elements; name hash: 0x4a69e3f3
access-list CSM_FW_ACL_ line 1 remark rule-id 9998: PREFILTER POLICY: Default Tunnel and Priority Policy
access-list CSM_FW_ACL_ line 2 remark rule-id 9998: RULE: DEFAULT TUNNEL ACTION RULE
access-list CSM_FW_ACL_ line 3 advanced permit ipinip any any rule-id 9998 (hitcnt=0) 0xf5b597d6
access-list CSM_FW_ACL_ line 4 advanced permit 41 any any rule-id 9998 (hitcnt=0) 0x06095aba
access-list CSM_FW_ACL_ line 5 advanced permit gre any any rule-id 9998 (hitcnt=0) 0x52c7a066
access-list CSM_FW_ACL_ line 6 advanced permit udp any eq 3544 any range 1025 65535 rule-id 9998 (hitcnt=0) 0x46d7839e
access-list CSM_FW_ACL_ line 7 advanced permit udp any range 1025 65535 any eq 3544 rule-id 9998 (hitcnt=0) 0xaf1d5aa5
Note: The above pre-filter rules from lines 6 and 7, are the default pre-filter rules intended to allow the Teredo tunnel UDP 3544 traffic through the FTD.
But, the problem is that an FTD that does not use the factory default pre-filter rule, blocks or blacklists this Xbox live online multi-player UDP 3544 traffic that comes from the Xbox, this is confirmed with the help of an ASP (Accelerated Security Path) packet capture applied in the FTD, just as follows:
firepower# capture asp type asp-drop all
firepower# show cap asp | i x.x.x.x
50243: 16:23:03.023054 x.x.x.x.3074 > y.y.y.y.3544: udp 61 Drop-reason: (session) Blocked or blacklisted by the session preprocessor
51622: 16:23:04.023253 x.x.x.x.3074 > y.y.y.y.3544: udp 61 Drop-reason: (session) Blocked or blacklisted by the session preprocessor
53990: 16:23:06.023588 x.x.x.x.3074 > y.y.y.y.3544: udp 61 Drop-reason: (session) Blocked or blacklisted by the session preprocessor
58785: 16:23:10.024367 x.x.x.x.3074 > y.y.y.y.3544: udp 61 Drop-reason: (session) Blocked or blacklisted by the session preprocessor
69006: 16:23:18.025145 x.x.x.x.3074 > y.y.y.y.3544: udp 61
89783: 16:23:34.026716 x.x.x.x.3074 > y.y.y.y.3544: udp 61
Note: You can try to permit this traffic through the FTD with an ACP (Access Control Policy) configured to allow the UDP 3544 traffic, after this, you will confirm the same ASP drops will be seen on the FTD CLI.
Solution
To allow the Xbox live online multi-player traffic (Teredo tunnel UDP 3544) through the FTD, you need to configure a pre-filter rule, for this, you have 4 options to configure the pre-filter rule required:
Configure a normal pre-filter rule
Example 1
Configure a normal pre-filter rule with Analyze action to allow the traffic destined to UDP 3544 with Any as the destination:
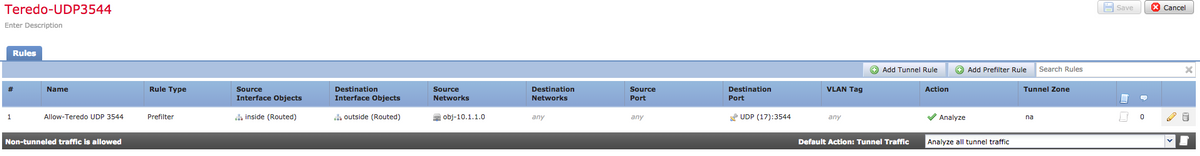
Example 2
Configure a normal pre-filter rule with Fastpath action to allow the traffic destined to UDP 3544 with Any as the destination:

Configure a tunnel pre-filter rule
Example 1
Configure a tunnel pre-filter rule with Analyze action to allow the traffic destined to UDP 3544 with Any as the destination:

Example 2
Configure a tunnel pre-filter rule with Fastpath action to allow the traffic destined to UDP 3544 with Any as the destination:
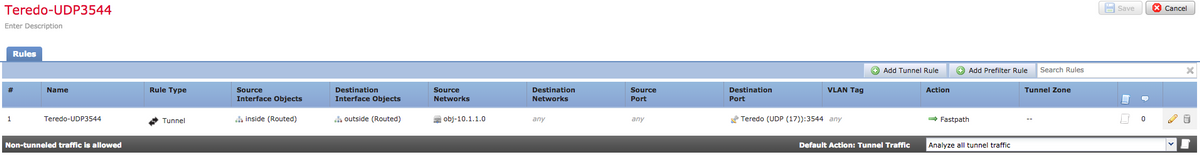
Note: The 4 options mentioned above are confirmed work fine in the TAC lab to allow the Teredo tunnel (UDP 3544) to get established through the FTD. The main intention to use Any as destination IP address for the pre-filter rule configuration is due to the different IP addresses the Xbox can use to connect to the Microsoft online multi-player servers.
Related Information
