Introduction
This document provided the information on the Cisco Success Network feature which would be available as part of the AsyncOS 13.5.1 release for the Cisco Email Security Appliance (ESA). Cisco Success Network (CSN) is a user-enabled cloud service. When CSN is enabled, a secure connection is established between the ESA and the Cisco cloud (Using the CTR Connection), to stream feature status information. Streaming CSN data provides a mechanism to select data of interest from the ESA and to transmit it in a structured format to remote management stations.
Benefits
- To inform the customer regarding available unused features that can improve the effectiveness of the product.
- To inform the customer regarding additional technical support services and monitoring that might be available for the product.
- To help Cisco improve the product.
Information Collected
These are the list of feature information that is collected as part of this feature once configured on the ESA device:
- Device Model (x90, x95, 000v,100v, 300v, 600v)
- Device Serial Number (UDI)
- UserAccountID (VLN id number or SLPIID)
- Software Version
- Install Date
- slVAN (Virtual Account Name in Smart Licensing)
- Deployment Mode
- IronPort Anti-Spam
- Graymail Safe Unsubscribe
- Sophos
- McAfee
- File Reputation
- File Analysis
- Data Loss Prevention
- External Threat Feeds
- Ironport Image Analysis
- Outbreak filters
- Cisco IronPort Email Encryption Settings (envelope encryption)
- PXE encryption
- Domain Reputation
- URL Filtering
- Block Page Customization
- Message Tracking
- Policy, Virus and Outbreak Quarantines
- Spam Quarantine
Prerequisites
Requirements
To configure this feature, these are some of the requirements which must be fulfilled:
- CTR (Cisco Threat Response) account
Firewall Related Configuration
The Firewall configuration needed to get CSN functional is currently dependent on the CTR communication and please refer to this document for more information: Integrating ESA with CTR
Components Used
The information in this document is based on these software and hardware versions:
- Email Security Appliance (ESA) AsyncOS Version 13.5.1.x and above.
Configure
You can configure this feature using both the ESA UI or the CLI. Details on both the steps are shown below.
CSN and CTR dependencies
CSN Feature depends on the CTR Feature connectivity for its successful operation and this table provides more information on the relationship between these two processes.
| Threat Response |
CSN |
SSE Connector |
CSN Process |
| Disabled |
Disabled |
Down |
Disabled |
| Disabled (De-register) |
Enabled |
Down |
Down |
| Disabled (registered) |
Enabled |
Up |
Up |
| Enabled |
Disabled Manually |
Up |
Down |
| Enabled |
Enabled |
Up |
Up |
CSN Configuration using the UI
1) Login into the ESA UI.
2) Browse to Network >> Cloud Service Settings (I will assume that CTR was disabled before we started with the upgrade to 13.5.1.x). Before the upgrade, If CTR was enabled, then CSN will also be enabled by default. If CTR was disabled, then CSN will also be disabled.
Note: We will assume CTR was disabled before the upgrade as CTR in a Centralized Deployment is supposed to be disabled as it is enabled only on the SMA for sending out the reporting information to CTR.
3) This is what you would observe as default on the ESA Device: -
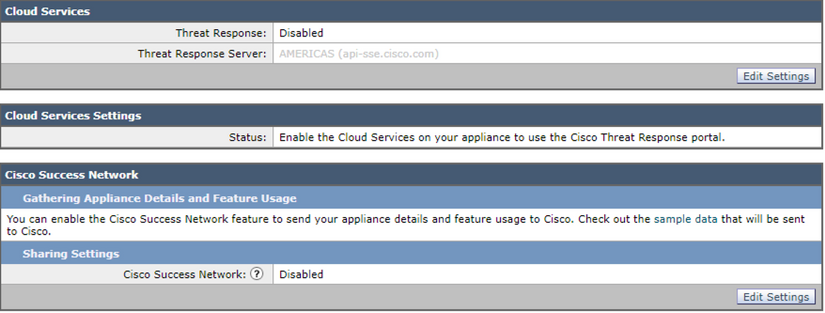
4) We will now register this ESA by first enabling the CTR Services on the ESA and "Submit" the changes.

5) It would show this Status on the CTR Page "The Cisco Cloud Service is busy. Navigate back to this page after some time to check the appliance status." Commit the changes to the device.
6) You would then move ahead and get the CTR Token and register the device to CTR:

7) You should see this status once the registration is successful:
Success — A request to register your appliance with the Cisco Threat Response portal is initiated. Navigate back to this page after some time to check the appliance status.
8) Once you refresh the page, you would see the CTR Registered and CSN Enabled:

9) As Discussed, CTR in this scenario needs to be disabled as this ESA is Centralized and you would still see CSN enabled as expected. In case, this ESA is not managed by SMA (Non-Centralized), you can keep the CTR enabled.

This should be the final state of the configuration. This step should be followed for every ESA as this setting is Machine Level.
CSN Configuration using the CLI
(Machine esa )> csnconfig
You can enable the Cisco Success Network feature to send your appliance details and feature usage to Cisco.
Choose the operation you want to perform:
- ENABLE - To enable the Cisco Success Network feature on your appliance.
[]> enable
The Cisco Success Network feature is currently enabled on your appliance.
Changes would need to be committed as part of enabling this using the CLI.
Troubleshoot
To troubleshoot this feature, there is a PUB (/data/pub/csn_logs) Log available that would have the information on this feature. The sample below is the log at the time when the registration was completed on the device:
(Machine ESA) (SERVICE)> tail
Currently configured logs:
Log Name Log Type Retrieval Interval
---------------------------------------------------------------------------------
1. API API Logs Manual Download None
2. amp AMP Engine Logs Manual Download None
3. amparchive AMP Archive Manual Download None
4. antispam Anti-Spam Logs Manual Download None
5. antivirus Anti-Virus Logs Manual Download None
6. asarchive Anti-Spam Archive Manual Download None
7. authentication Authentication Logs Manual Download None
8. avarchive Anti-Virus Archive Manual Download None
9. bounces Bounce Logs Manual Download None
10. cli_logs CLI Audit Logs Manual Download None
11. csn_logs CSN Logs Manual Download None
12. ctr_logs CTR Logs Manual Download None
13. dlp DLP Logs Manual Download None
14. eaas Advanced Phishing Protection Logs Manual Download None
15. encryption Encryption Logs Manual Download None
16. error_logs IronPort Text Mail Logs Manual Download None
17. euq_logs Spam Quarantine Logs Manual Download None
18. euqgui_logs Spam Quarantine GUI Logs Manual Download None
19. ftpd_logs FTP Server Logs Manual Download None
20. gmarchive Graymail Archive Manual Download None
21. graymail Graymail Engine Logs Manual Download None
22. gui_logs HTTP Logs Manual Download None
23. ipr_client IP Reputation Logs Manual Download None
24. mail_logs IronPort Text Mail Logs Manual Download None
25. remediation Remediation Logs Manual Download None
26. reportd_logs Reporting Logs Manual Download None
27. reportqueryd_logs Reporting Query Logs Manual Download None
28. s3_client S3 Client Logs Manual Download None
29. scanning Scanning Logs Manual Download None
30. sdr_client Sender Domain Reputation Logs Manual Download None
31. service_logs Service Logs Manual Download None
32. smartlicense Smartlicense Logs Manual Download None
33. sntpd_logs NTP logs Manual Download None
34. status Status Logs Manual Download None
35. system_logs System Logs Manual Download None
36. threatfeeds Threat Feeds Logs Manual Download None
37. trackerd_logs Tracking Logs Manual Download None
38. unified-2 Consolidated Event Logs Manual Download None
39. updater_logs Updater Logs Manual Download None
40. upgrade_logs Upgrade Logs Manual Download None
41. url_rep_client URL Reputation Logs Manual Download None
Enter the number of the log you wish to tail.
[]> 11
Press Ctrl-C to stop.
Sun Apr 26 18:16:13 2020 Info: Begin Logfile
Sun Apr 26 18:16:13 2020 Info: Version: 13.5.1-177 SN: 564D2E7007BA223114B8-786BB6AB7179
Sun Apr 26 18:16:13 2020 Info: Time offset from UTC: -18000 seconds
Sun Apr 26 18:16:13 2020 Info: System is coming up.
Sun Apr 26 18:16:13 2020 Info: DAEMON: Watchdog thread started
Sun Apr 26 18:16:16 2020 Info: The appliance is uploading CSN data
Sun Apr 26 18:16:16 2020 Info: The appliance has successfully uploaded CSN data






 Feedback
Feedback