Introduction
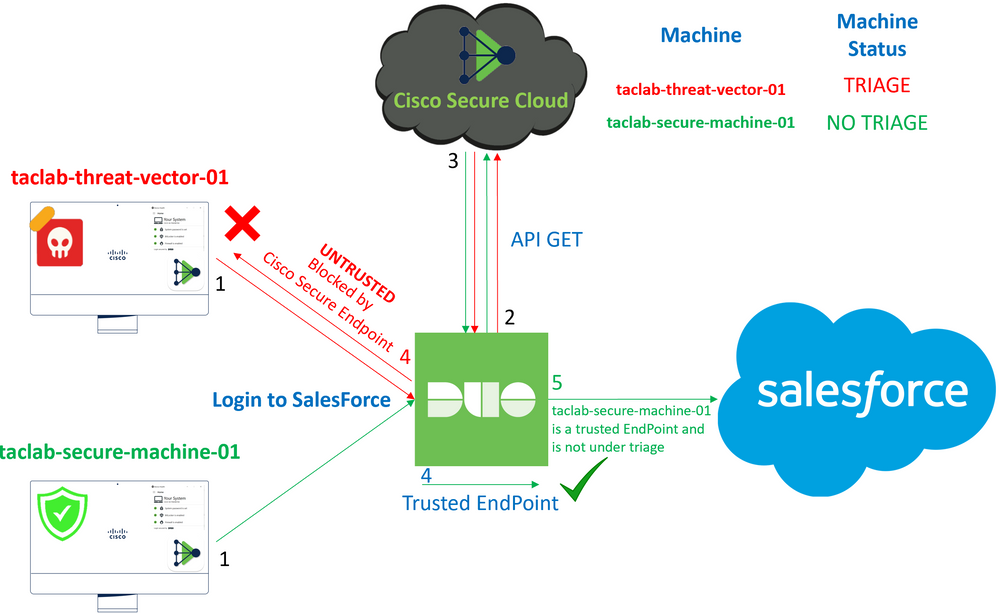
This document describes how to integrate Duo Trusted EndPoints with Cisco Secure EndPoint.
Background Information
The integration between Cisco Secure EndPoint and Duo, allows for effective collaboration in response to threats detected on trusted network devices. This integration is achieved through multiple device management tools that establish the reliability of each device. Some of these tools include:
- Active Directory Domain Services
- Active Directory with Device Health
- Generic with Device Health
- Intune with Device Health
- Jamf Pro with Device Health
- LANDESK Management Suite
- Mac OS X Enterprise Asset Management Tool
- Manual with Device Health
- Windows Enterprise Asset Management Tool
- Workspace ONE with Device Health
Once devices are integrated with a device management tool, it is possible to integrate Cisco Secure EndPoint and Duo by API in the Administration Panel. Subsequently, the appropriate policy must be configured in Duo to execute trusted device verification and detect compromised devices that can affect applications protected by Duo.
Note: In this case, we work with Active Directory and Device Health.
Prerequisites
- Active Directory to make the integration.
- To integrate Duo with Trusted Endpoints, your devices must be registered in the Active Directory domain. This allows Duo to authenticate and authorize access to network resources and services securely.
- Duo Beyond Plan.
Configuration and Use Case
Configure the Integration in Duo
Log in to the Admin Panel and go to:
Trusted EndPoints > Add Integration- Select
Active Directory Domain Services
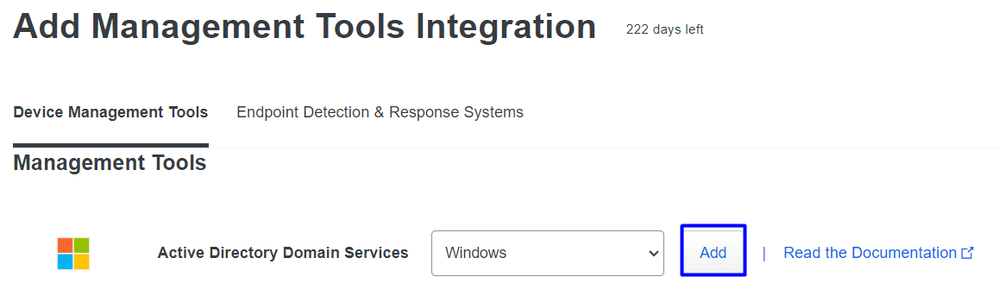
After that, you are redirected to configure the Active Directory and Device Health.
Take into count that this only works with machines in the domain.
Go to the active directory and run the next command in PowerShell:
(Get-ADDomain | Format-Table -Property DomainSID -HideTableHeaders | Out-String).Trim() | clip
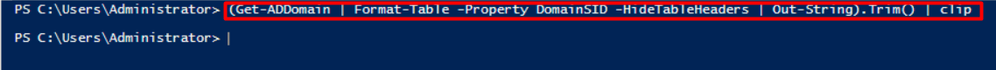
After that, be sure you have copied to the clipboard the security identifier of your Active Directory.
Example
S-1-5-21-2952046551-2792955545-1855548404
This is used in your Active Directory and Device Health Integration.
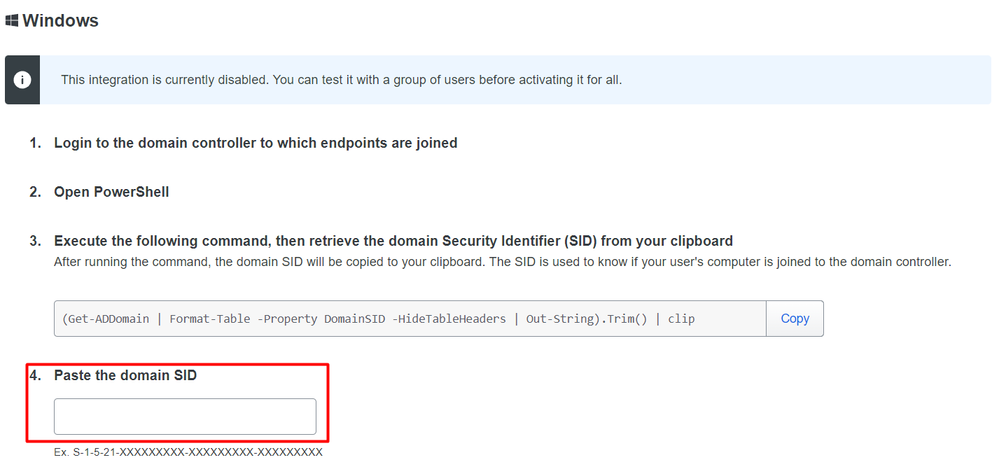
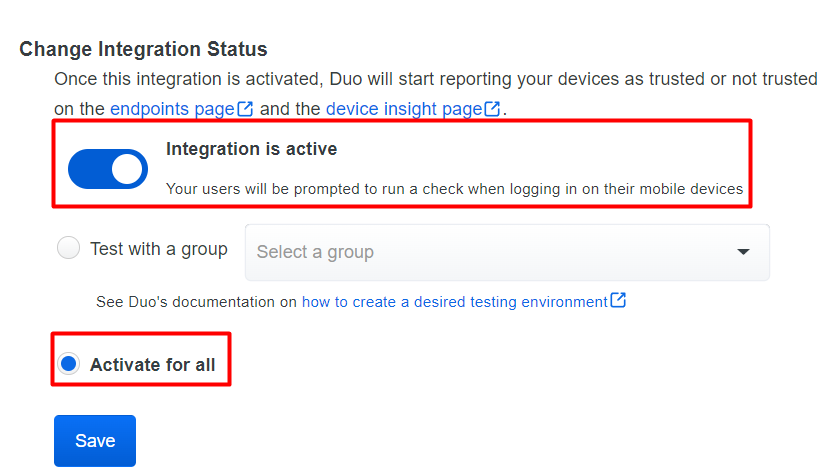
Click Save and enable the integration and Activate for all. Otherwise, you cannot integrate with Cisco Secure EndPoint.
Go to Trusted EndPoints > Select Endpoint Detection & Response System > Add this integration.
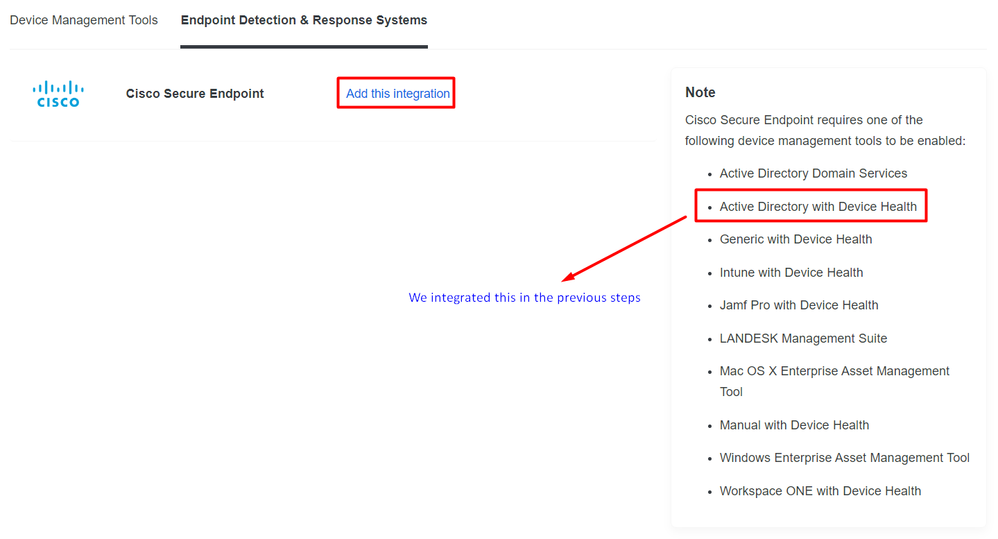
Now you are on the main page of the integration for Cisco Secure EndPoint.
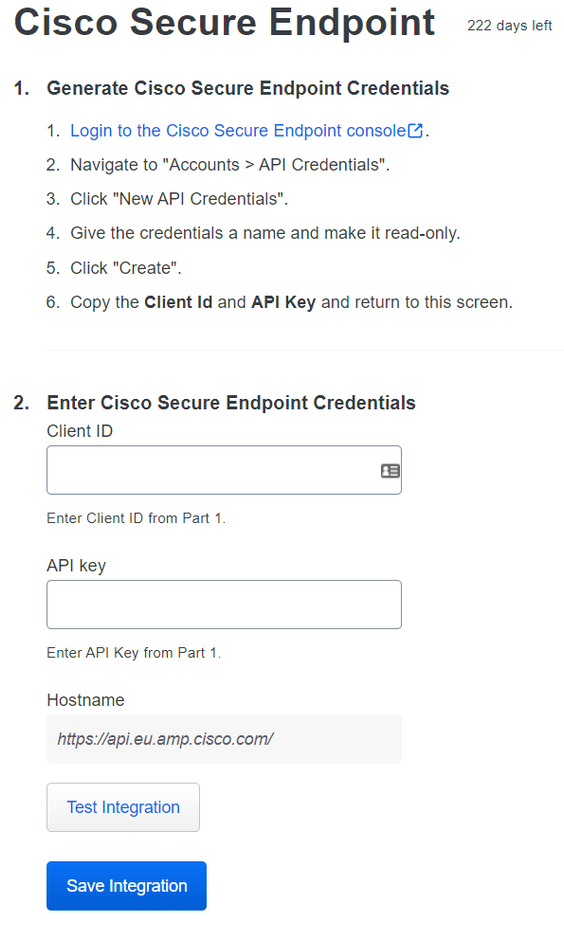
After that, go to the Admin Panel of the Cisco Secure EndPoint.
Configure the Integration in Cisco Secure EndPoint
And navigate to Accounts > API Credentials and select New API Credentials.
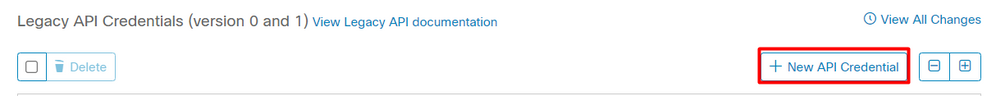
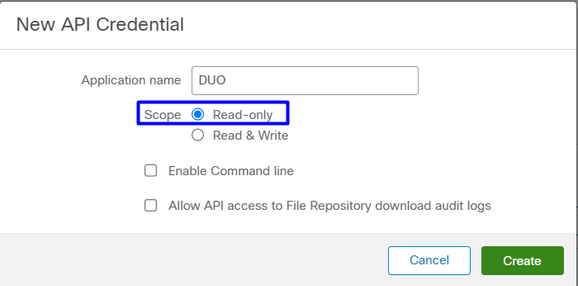
Note: Only Read-only is needed to make this integration because Duo makes GET queries to Cisco Secure EndPoint to know if the device meets the requirements of the policy.
Insert Application Name, Scope,Create.
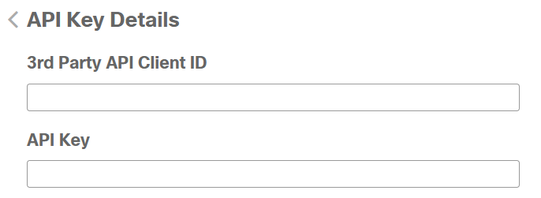
- Copy the
3rd API Party Client ID from Cisco Secure EndPoint to Duo Admin Panel in Client ID.
- Copy the
API Key from Cisco Secure EndPoint to Duo Admin Panel in API Key.
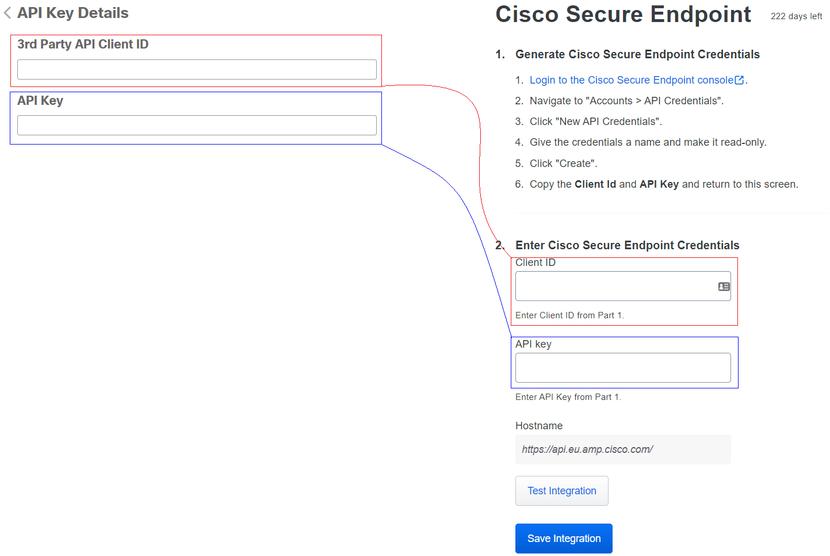
Test the integration, and If everything works well, click Save to save the integration.
Configure Policies in Duo
To configure the policies for your integration, you go through your application:
Navigate to Application > Search for your Application > Select your policy
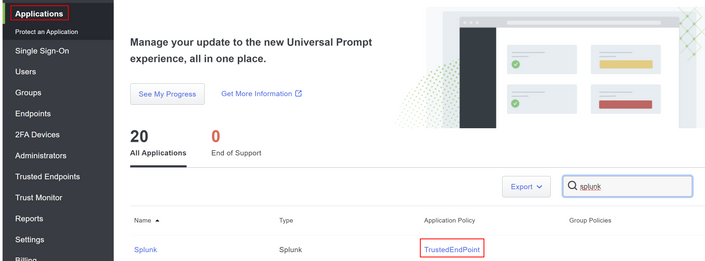
Configure the Policy to Detect a Trusted Device
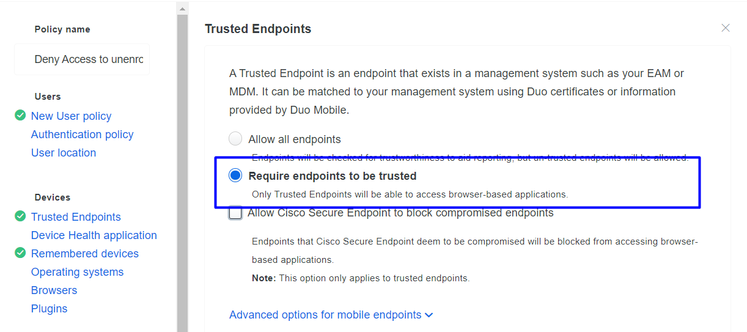
Test Trusted Machines
Machine with Duo Device Health and joined the domain
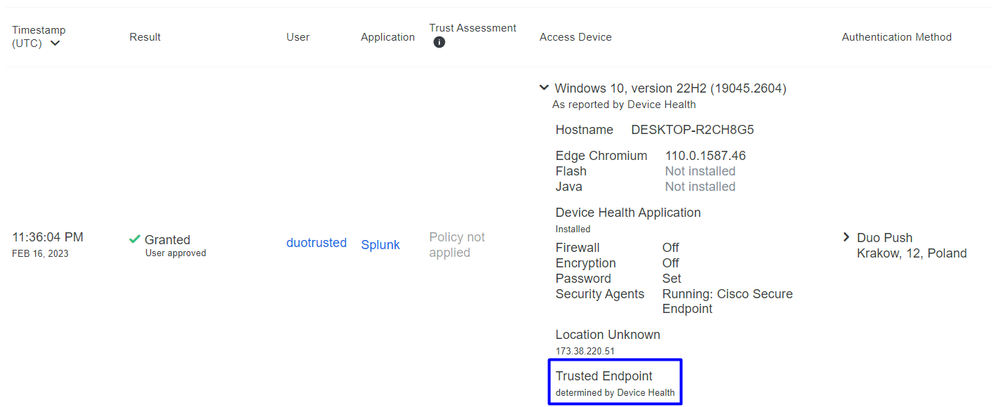
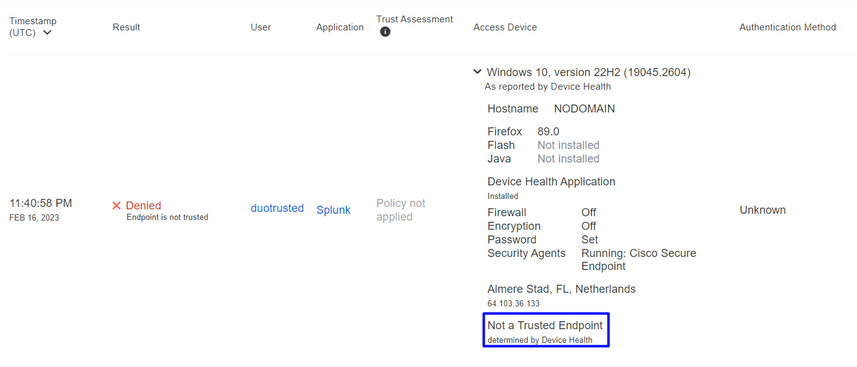
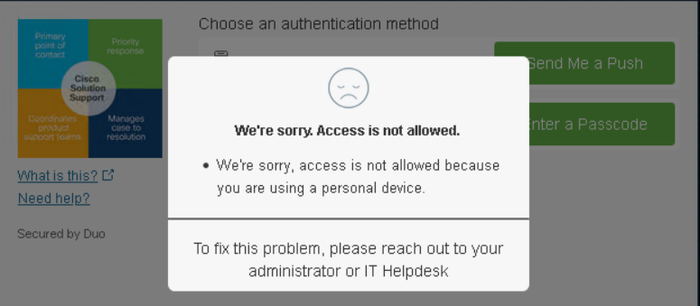
Machine outside the domain without Duo Device Health
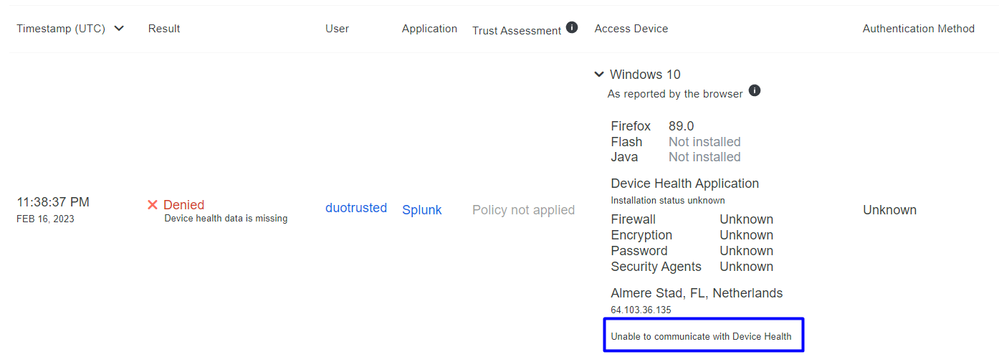
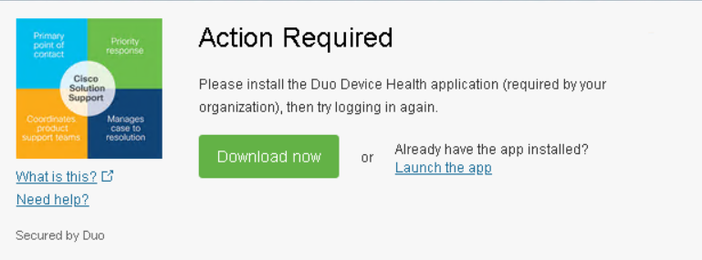
Machine outside the domain with Duo Device Health
Configure the Policy for Cisco Secure EndPoint
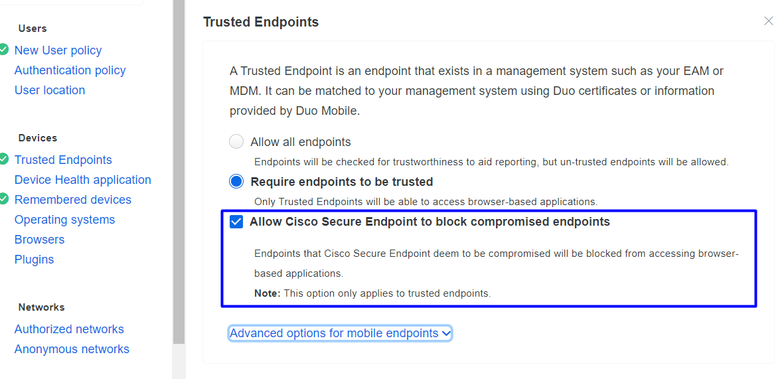
In this policy setup, configure the already trusted device to meet the requirement about threats that can affect your application, so if a device gets infected, or if some behaviors mark that machine with suspicious artifacts or Indicators of Compromise, you can block the machine access to the secured applications.
Test the Trusted Machines with Cisco Secure EndPoint
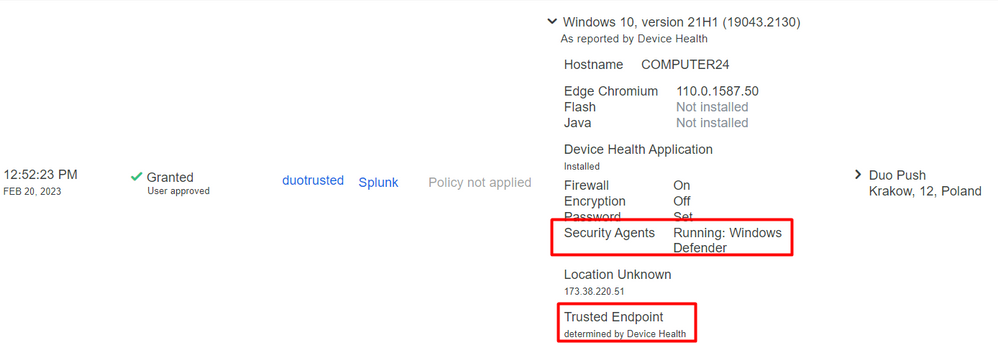
Machine without Cisco Secure Agent Installed
In this case, the machine can pass without AMP verification.
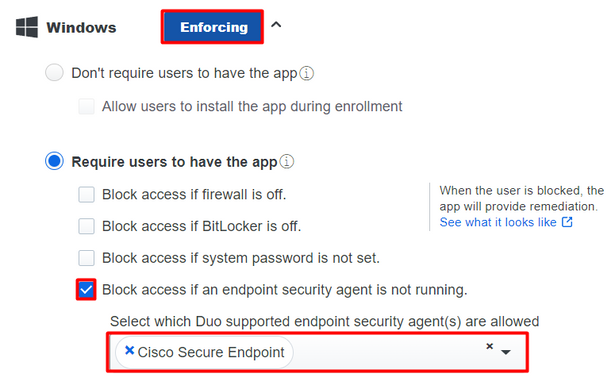
If you want to have a restrictive policy, you can set up the policy to be more restrictive if you modify the Device Health Application policy from Reporting to Enforcing.
And add Block Access if an EndPoint Security Agent is not running.
 Computer without infection
Computer without infection
With a machine, without infection, you can test how Duo with Cisco Secure EndPoint works to exchange information about the machine status and how the events are shown in this case in Duo and Cisco Secure EndPoint.
If you check the status of your machine in Cisco Secure EndPoint:
Navigate to Management > Computers.
When you filter for your machine, you can see the event of that, and in this case, you can determine your machine is clean.
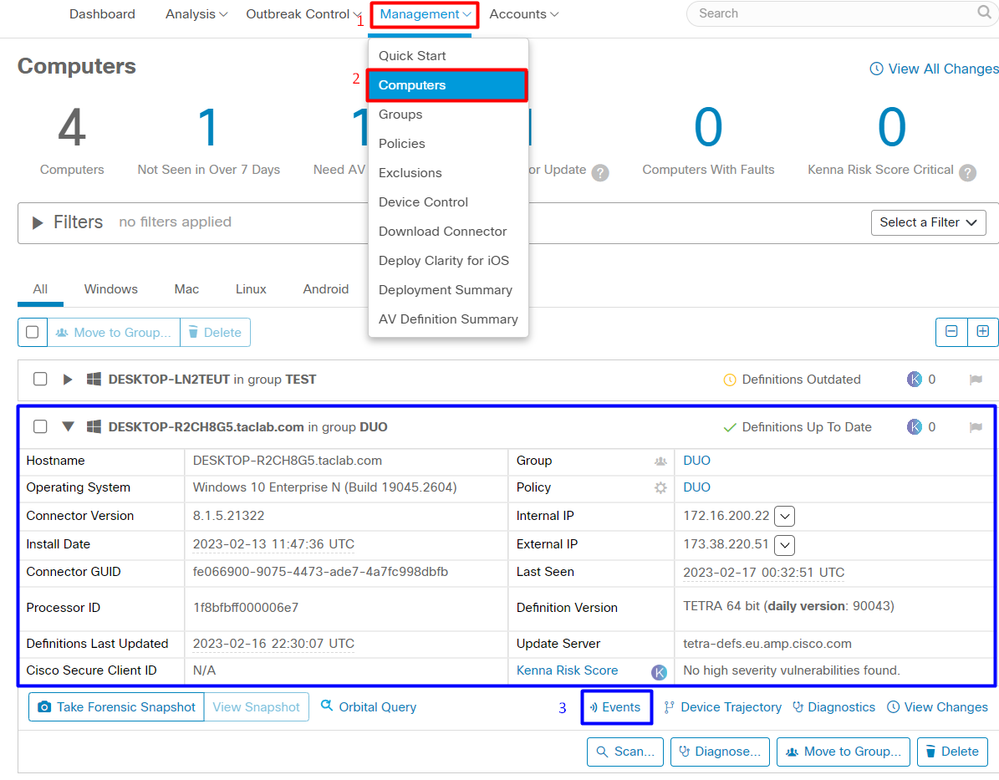
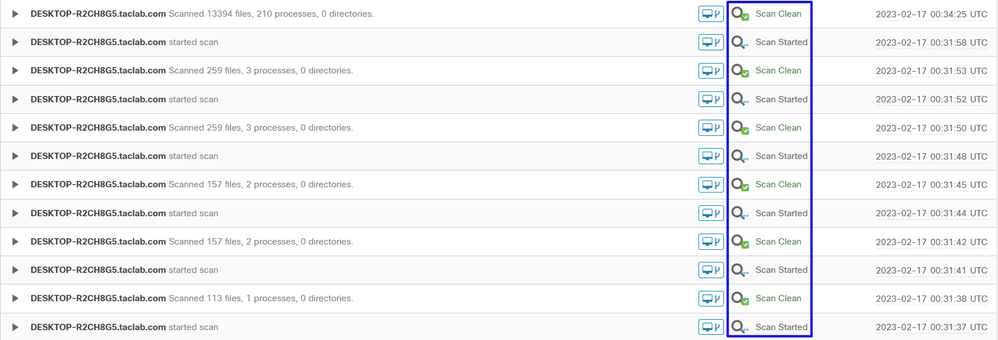
You can see there is no detection for your device, and also it is on a status of clean, which means your machine is not in triage to attend.
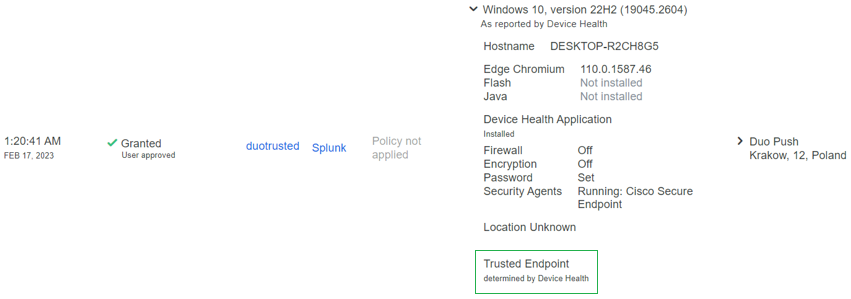
This is how Duo categorizes that machine:
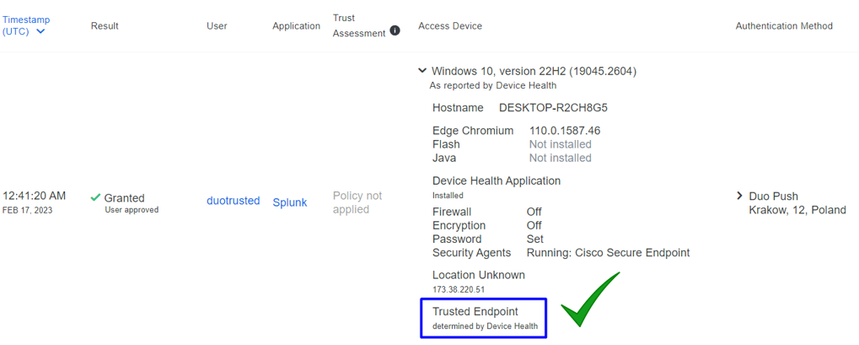
The machine maintains the trusted label.
What happens if the same machine gets infected by a Malicious ActorIndicators of Compromise alerts about this machine?
Computer with infection
To try with an example of EICAR to test the feature, access https://www.eicar.org/, and download a malicious sample.
Note: Do not worry. You can download that EICAR test, it is safe, and it is only a test file.
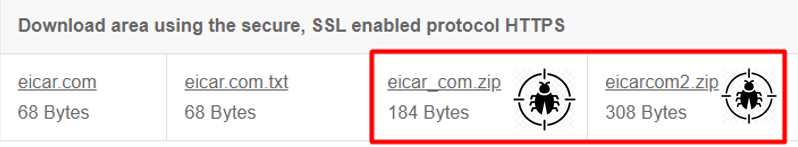
Scroll down and go to the section and download the test file.
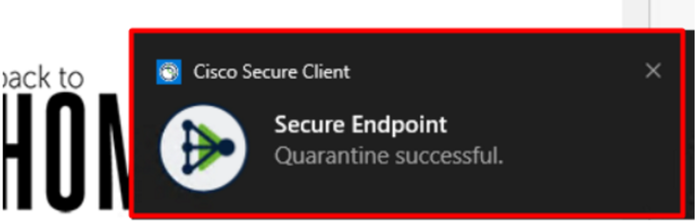
Cisco Secure EndPoint detects the malware and moves it to quarantine.
This is how it changes, as shown in the Cisco Secure EndPoint Admin panel.
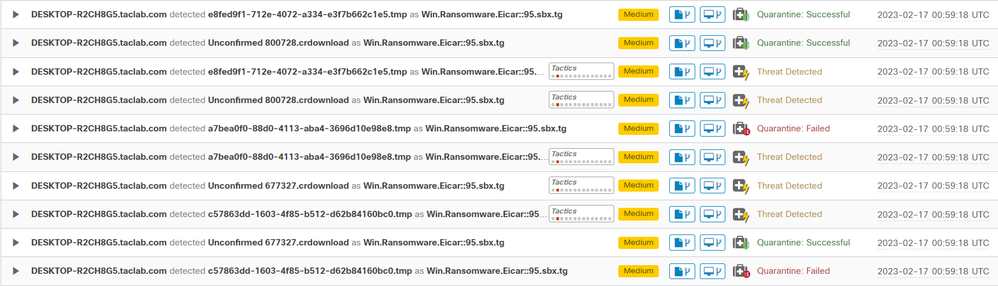
You also have the detection of the malware in the machine, but this means the endpoints are considered to be analyzed under the triage of Cisco Secure EndPoint on the Inbox.
Note: To send an endpoint to triage, it needs to have multiple detections of artifacts or strange behavior that activate some Indicators of Compromise in the endpoint.
Under the Dashboard, click in the Inbox.
Now you have a machine that requires attention.
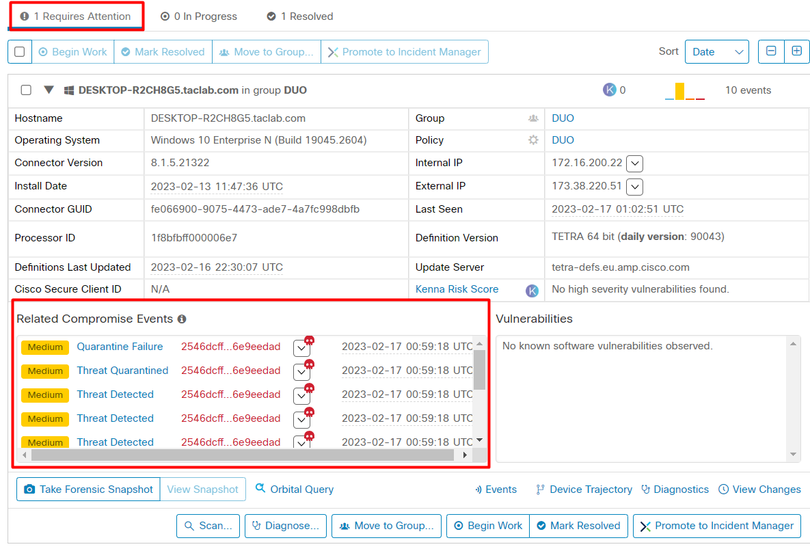
Now, switch to Duo and see what the status is.
Authentication is tried first to see the behavior after the machine was put on the Cisco Secure EndPoint under Require Attention.
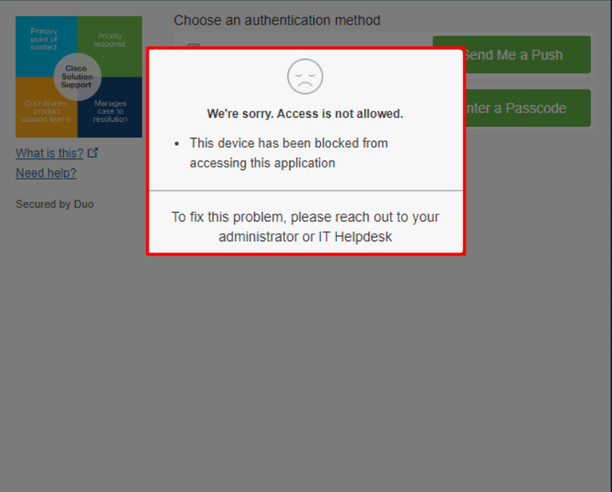
This is how it changes in Duo and how the event under authentication events is shown.
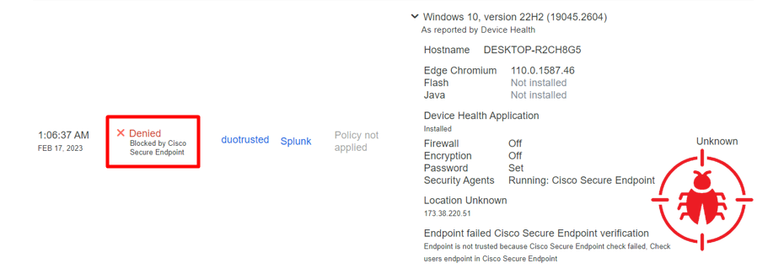
Your machine was detected as not a safety device for your organization.
Permit the Access to a Machine After Review
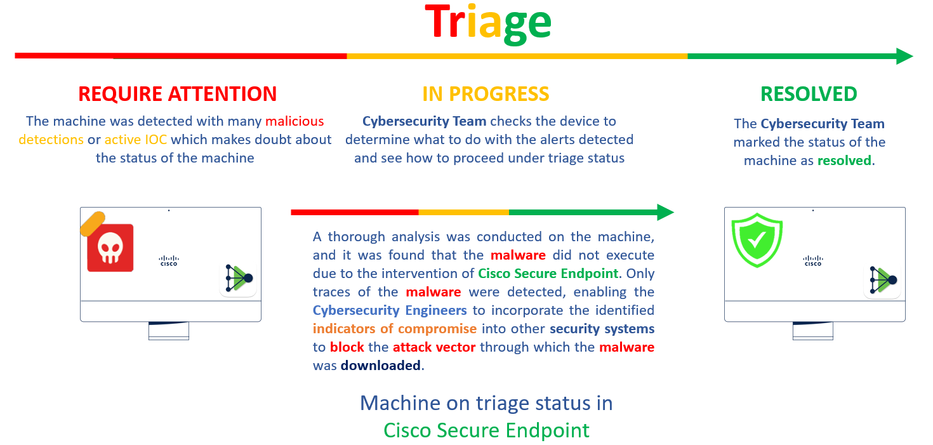
After verification under Cisco Secure EndPoint and by your Cybersecurity Specialist, you can permit access to this machine to your app in Duo.
Now the question is how to permit access again to the app protected by Duo.
You need to go under Cisco Secure EndPoint and in your Inbox, mark this device as resolved to permit access to the application protected by Duo.
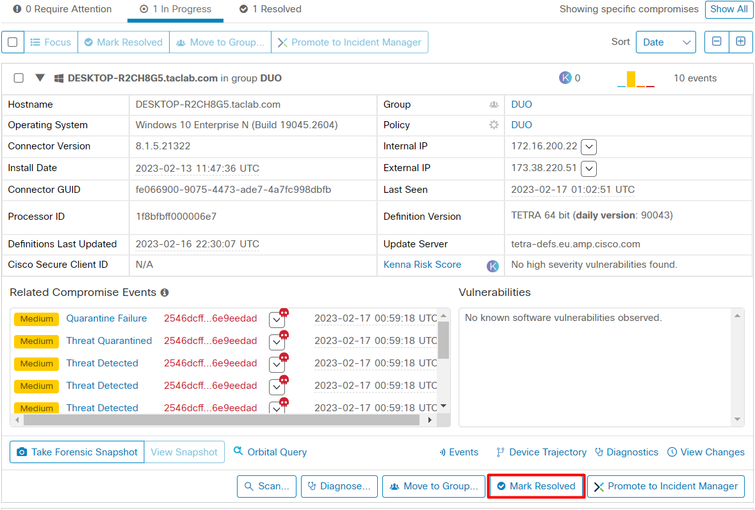
After that, you do not have the machine with the status attention required. This changed to resolved status.
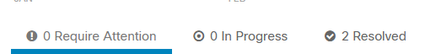
In a few words, now you are prepared to test again the access to our application protected by Duo.
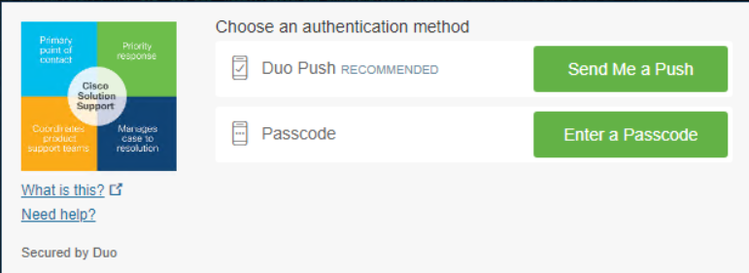
Now you have permission to send the push to Duo, and you are logged into the app.
Triage Workflow








































 Feedback
Feedback