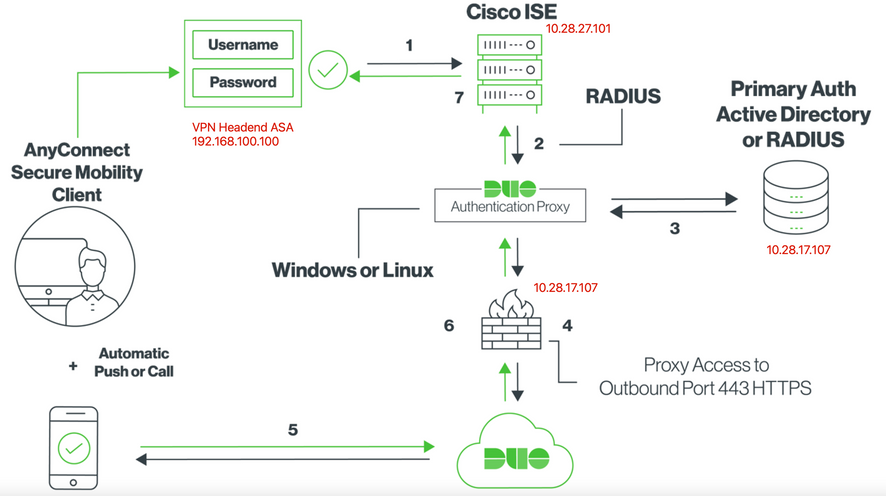
- Primary authentication initiated to Cisco ISE.
- Cisco ASA sends authentication request to the Duo Authentication Proxy.
- Primary authentication uses Active Directory or RADIUS.
- Duo Authentication Proxy connection established to Duo Security over TCP port 443.
- Secondary authentication via Duo Security’s service.
- Duo authentication proxy receives authentication response.
- Cisco ISE access granted.
User Accounts:
- Active Directory Admin: This is used as the directory account to allow the Duo Auth Proxy to bind to the Active Directory server for primary authentication.
- Active Directory test user
- Duo test user for secondary authentication
Active Directory Configurations
Windows server is pre-configured with Active Directory Domain services.
Note: If RADIUS Duo Auth Proxy Manager runs on the same Active Directory host machine, Network Policy Server (NPS) Roles must be uninstalled/deleted. If both RADIUS services run, they can conflict and impact performance.
In order to achieve AD configuration for authentication and user identity on Remote Access VPN users, a few values are required.
All these details must be created or collected on the Microsoft Server before configuration can be done on the ASA and Duo Auth proxy server.
The main values are:
- Domain Name. This is the domain name of the server. In this configuration guide, agarciam.cisco is the domain name.
- Server IP/Fully Qualified Domain Name (FQDN) Address. The IP address or FQDN used to reach the Microsoft server. If an FQDN is used, a DNS server must be configured within ASA and Duo Auth proxy to resolve the FQDN.
In this configuration guide, this value is agarciam.cisco (which resolves to 10.28.17.107).
- Server port. The port used by the LDAP service. By default, LDAP and STARTTLS uses TCP port 389 for LDAP, and LDAP over SSL (LDAPS) uses TCP port 636.
- Root CA. If LDAPS or STARTTLS is used, the root CA used to sign the SSL certificate used by LDAPS is required.
- Directory Username and Password. This is the account used by Duo Auth proxy server to bind to the LDAP server and authenticate users and search for users and groups.
- Base and Group Distinguished Name (DN). The Base DN is the point of departure for Duo Auth proxy and it tells the Active directory to begin the search for and authenticate users.
In this configuration guide, the root domain agarciam.cisco is used as the Base DN and Group DN is Duo-USERS.
1. In order to add a new Duo user, on Windows Server, navigate to Windows icon at the bottom left and click Windows Administrative tools, as shown in the image.
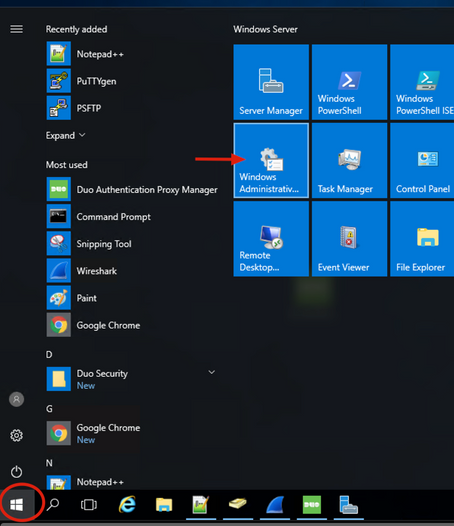
2. On Windows Administrative tools window, navigate to Active Directory Users and Computers.
On the Active Directory Users and Computers panel, expand the domain option and navigate to Users folder.
In this configuration example, Duo-USERS is used as the target group for secondary authentication.
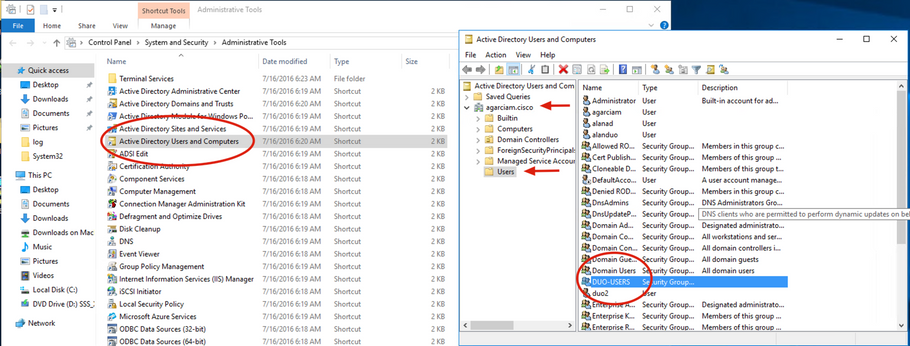
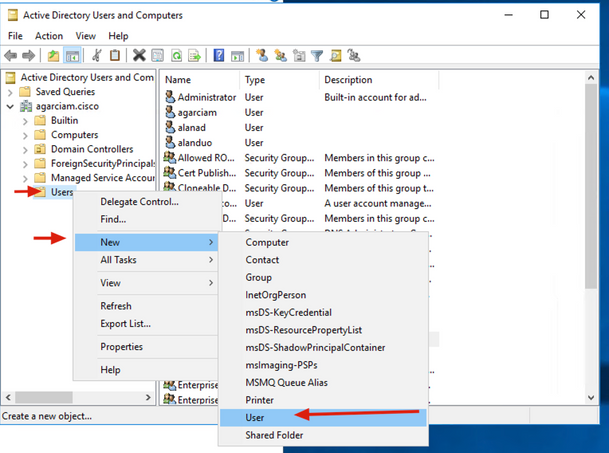
3. Right click on the Users folder and select New > User, as shown in the image.
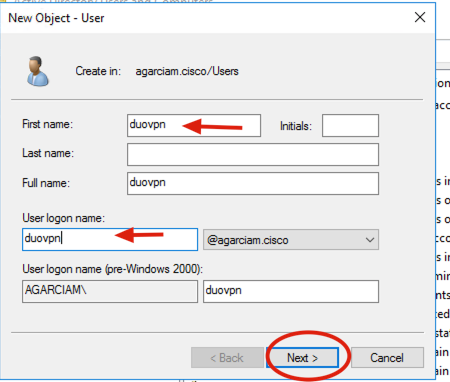
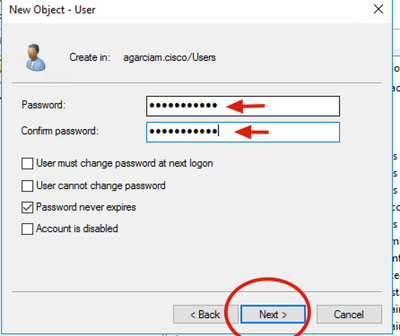
4. On the New Object-User window, specify the identity attributes for this new user and click Next, as shown in the image.
5. Confirm password and click Next, then Finish once user information is verified.
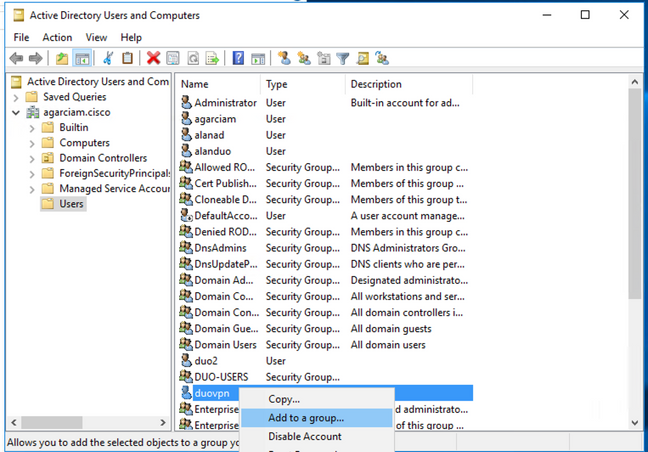
6. Assign the new user to an specific group, right click it and select Add to a group, as shown in the image.
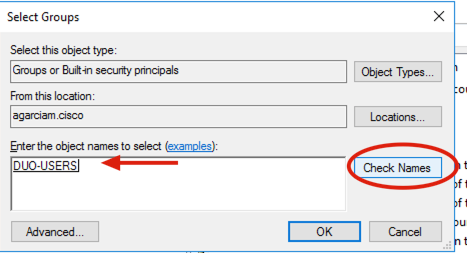
7. On the Select groups panel, type the name of the desired group and click Check names.
Then, select the name that matches your criteria and click Ok.
8. This is the user that is used on this document as an example.
Duo Configurations
1. Log into your Duo Admin portal.
2.On the left side panel, navigate to Users, click Add User and type the name of the user that matches our Active Domain username, then click Add User.
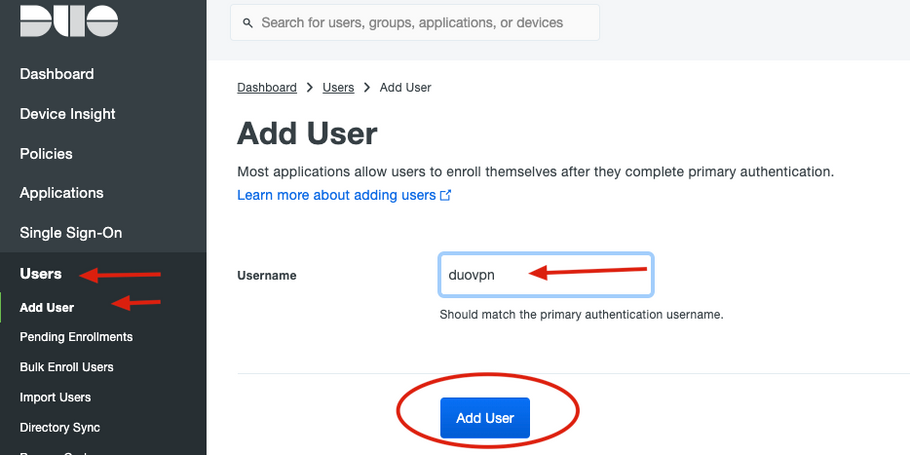
3. On the new user panel, fill in all the necessary information.
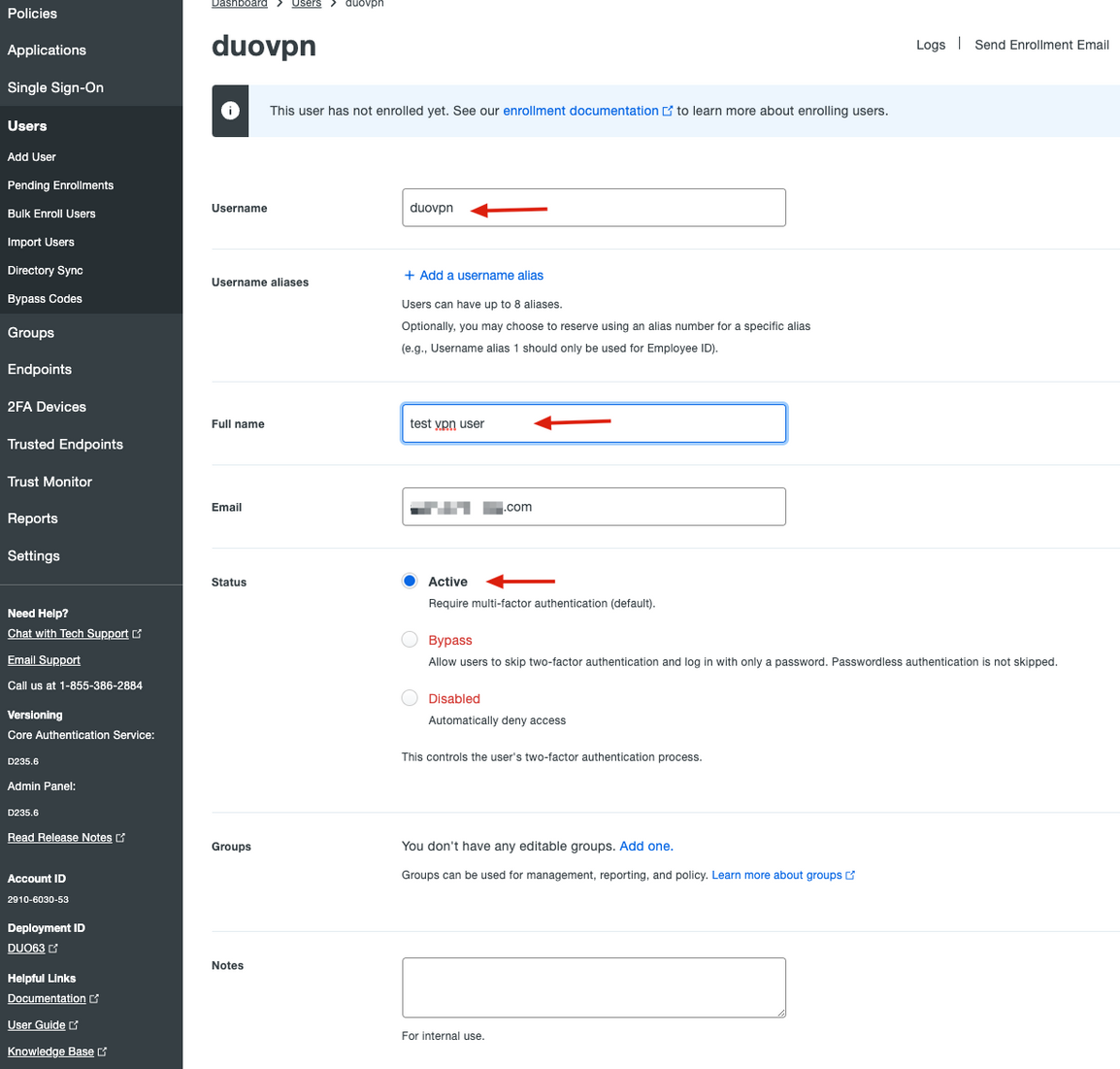
4. Under user devices, specify the secondary authentication method.
Note: In this document, Duo push for mobile devices method is used, so a phone device needs to be added.
Click Add Phone.
5. Type in the user phone number and click Add Phone.
6. On the left Duo Admin panel, navigate to Users and click the new user.
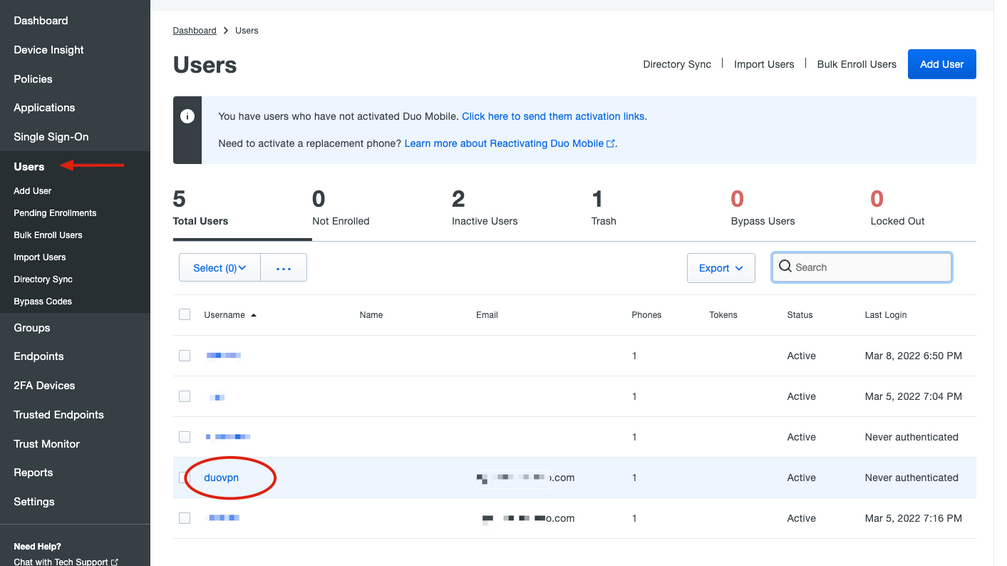
Note: In case you do not have access to your phone at the moment, you can select the email option.
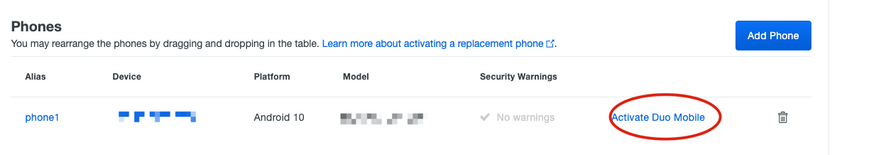
7.Navigate to Phones section and click Activate Duo Mobile.
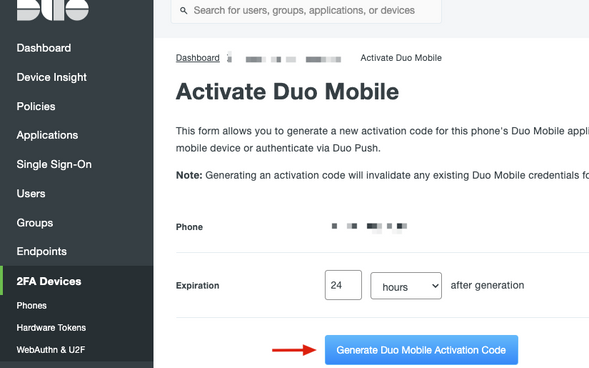
8. Click Generate Duo Mobile Activation Code.
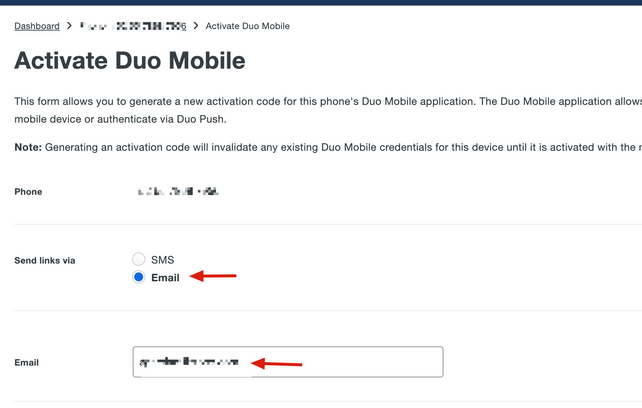
9. Select Email in order to receive the instructions via email, type your email address and click Send Instructions by email.
10. You receive an email with the instructions, as shown in the image.

11. Open the Duo Mobile App from your mobile device and click Add, then select Use QR code and scan the code from the instructions email.
12. New user is added to your Duo Mobile App.
Duo Auth Proxy Configuration
1. Download and Install Duo Auth Proxy Manager from Cisco Duo Authentication
Note: In this document, the Duo Auth Proxy Manager is installed on the same Windows Server that hosts Active Directory services.
2. On the Duo Admin Panel, navigate to Applications and click Protect an Application.
3. On the search bar, look for Cisco ISE Radius.
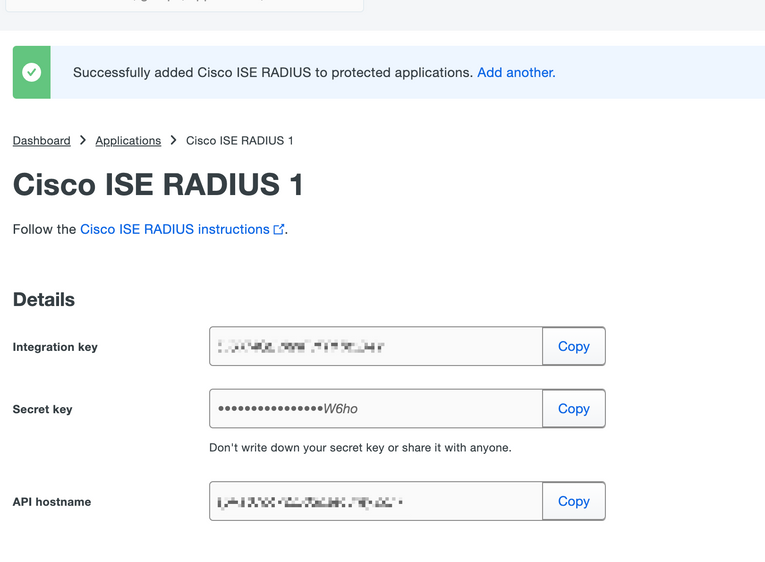
4. Copy the Integration key, Secret key, and the API Hostname. You need this information for the Duo Authentication Proxy configuration.
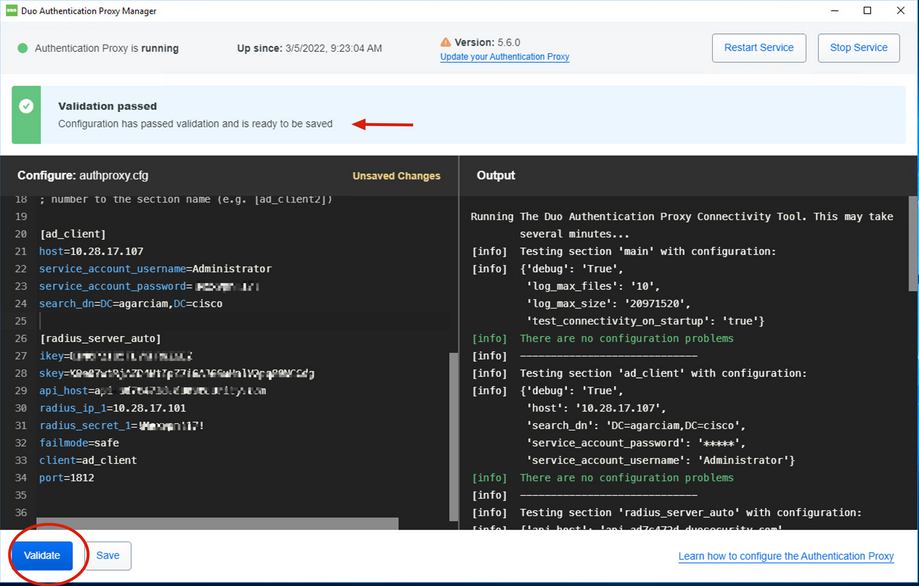
5. Run the Duo Authentication Proxy Manager application and complete the configuration for both Active Directory client and ISE Radius Server and click Validate.
Note: If validation is not successful, refer to the debug tab for details and correct accordingly.
Cisco ISE Configurations
1. Log into the ISE Admin portal.
2.Expand Cisco ISE tab and Navigate to Administration, then click Network Resources, and click External RADIUS Servers.
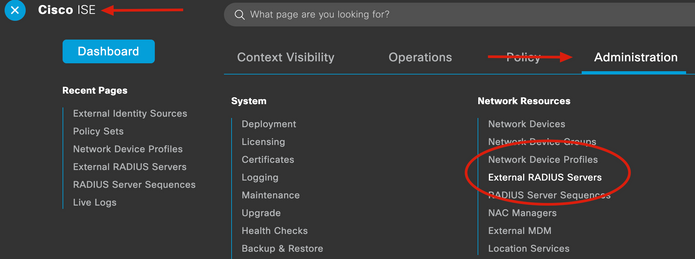
3. On External Radius Servers tab, click Add.
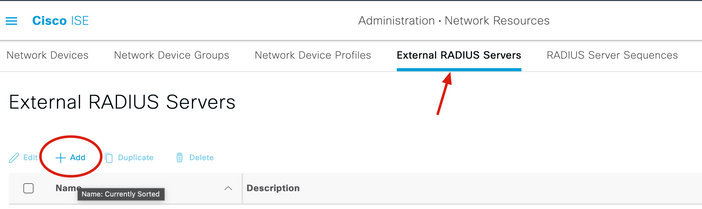
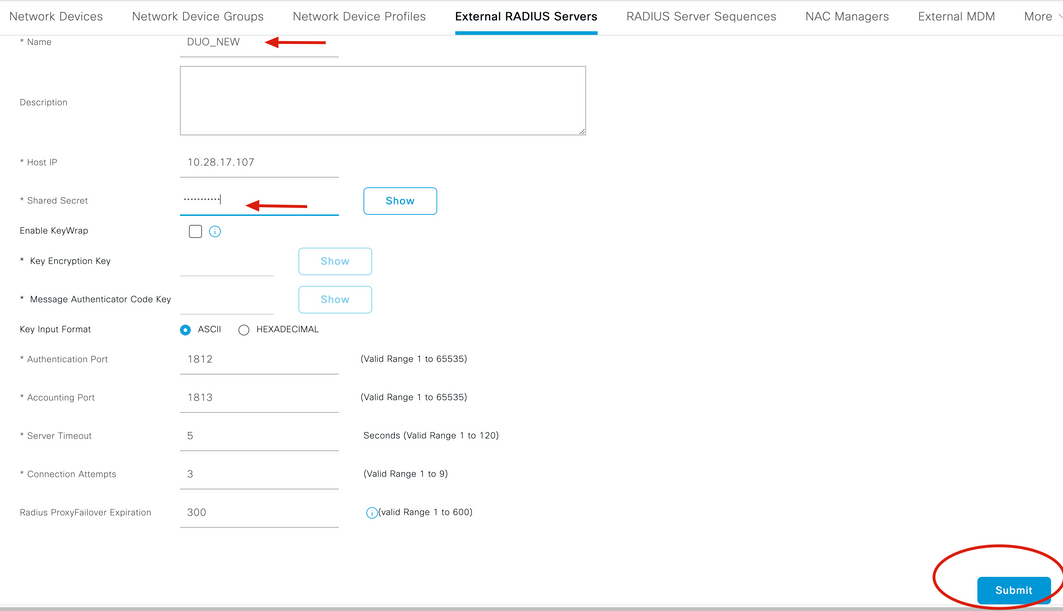
4. Fill in the blank with the RADIUS configuration used in the Duo Authentication Proxy Manager and click Submit.
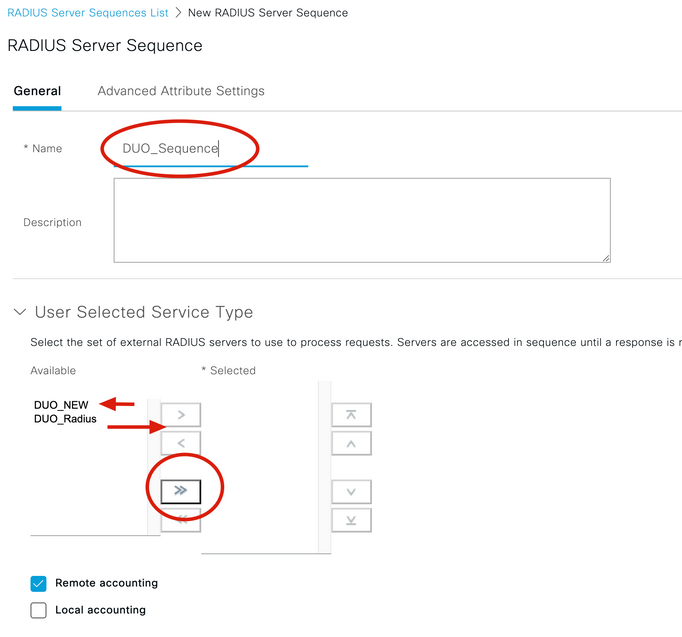
5. Navigate to RADIUS Server Sequences tab and click Add.
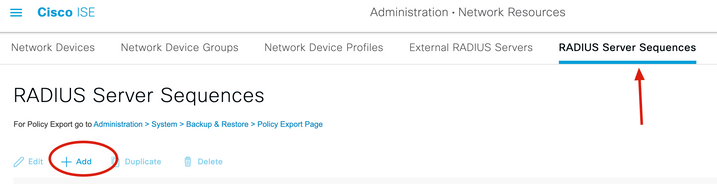
6. Specify the name of the sequence and assign the new RADIUS External server, click Submit.
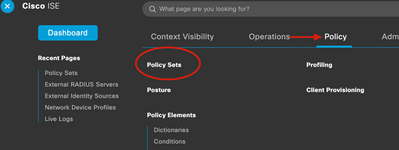
7. Navigate from the Dashboard menu to Policy, and click Policy Sets.
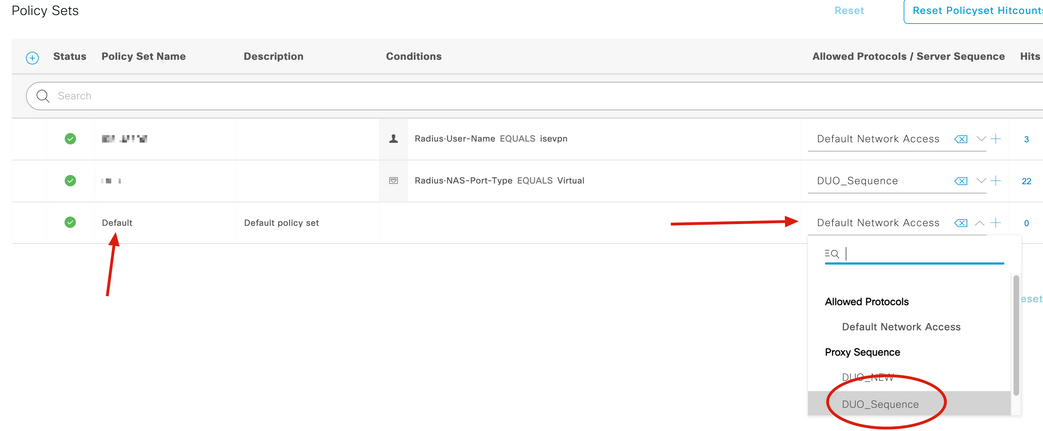
8. Assign the RADIUS Sequence to the default policy.
Note: In this document, the Duo sequence to all of the connections is applied, so Default policy is used. Policy assignment can vary as per requirements.
Cisco ASA RADIUS/ISE Configuration
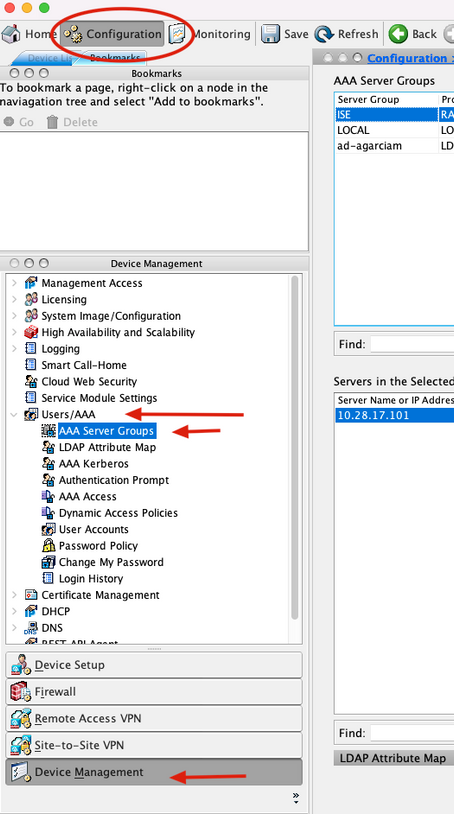
1. To configure ISE RADIUS Server under AAA Server groups, navigate to Configuration, then click Device Management, expand the Users/AAA section, and select AAA Server Groups.
2. On the AAA Server Groups panel, click Add.
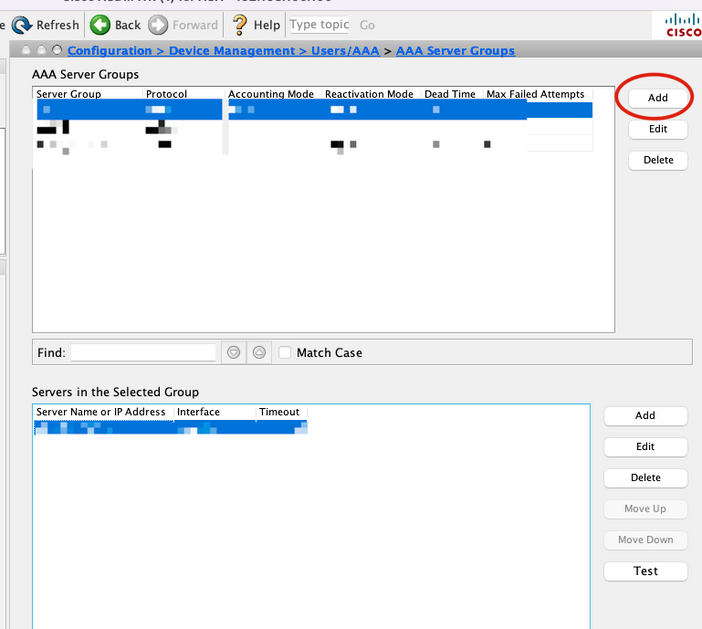
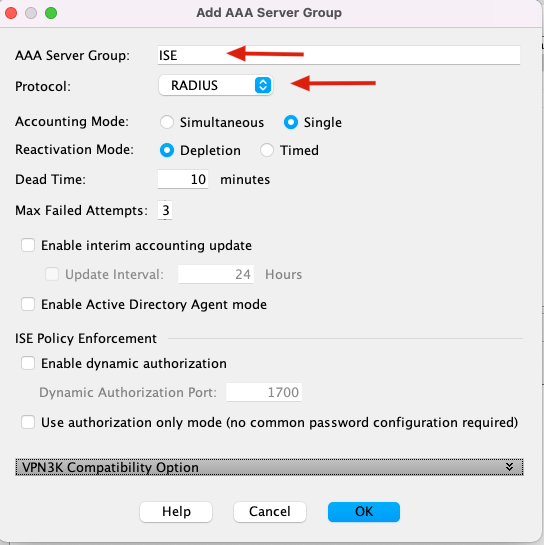
3. Select the name of the Server group and specify RADIUS as the protocol to use, then click Ok.
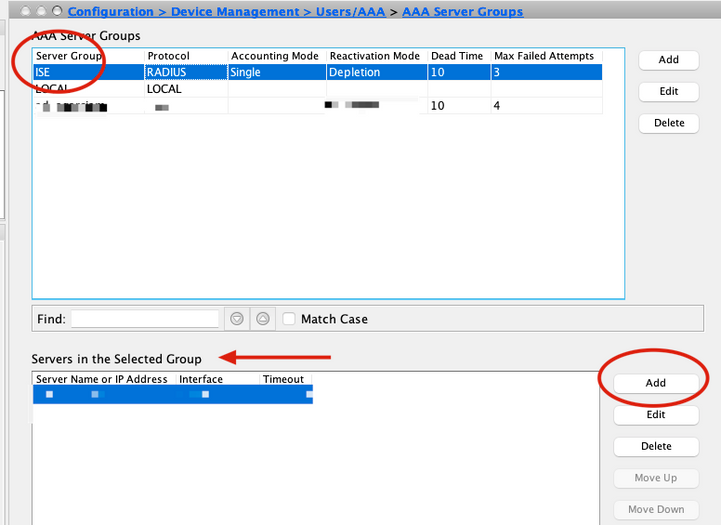
5. Select your new Server group and click Add under the Servers in the Selected Group panel, as shown in the image.
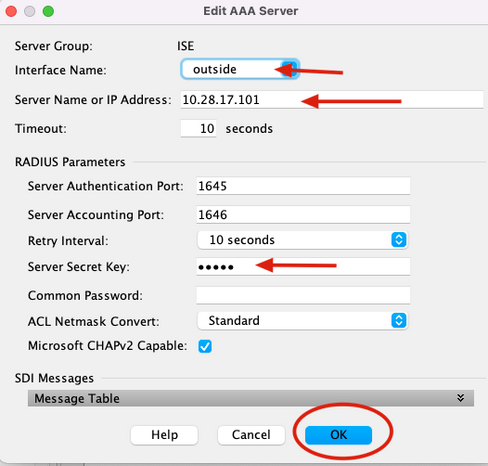
6. On the Edit AAA Server window, select the interface name, specify the IP address of the ISE Server and type the RADIUS secret key, and click Ok.
Note: All this information must match the one specified on the Duo Authentication Proxy Manager.
CLI Configuration
aaa-server ISE protocol radius
dynamic-authorization
aaa-server ISE (outside) host 10.28.17.101
key *****
Cisco ASA Remote Access VPN Configuration
ip local pool agarciam-pool 192.168.17.1-192.168.17.100 mask 255.255.255.0
group-policy DUO internal
group-policy DUO attributes
banner value This connection is for DUO authorized users only!
vpn-tunnel-protocol ikev2 ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split-agarciam
address-pools value agarciam-pool
tunnel-group ISE-users type remote-access
tunnel-group ISE-users general-attributes
address-pool agarciam-pool
authentication-server-group ISE
default-group-policy DUO
tunnel-group ISE-users webvpn-attributes
group-alias ISE enable
dns-group DNS-CISCO
Test
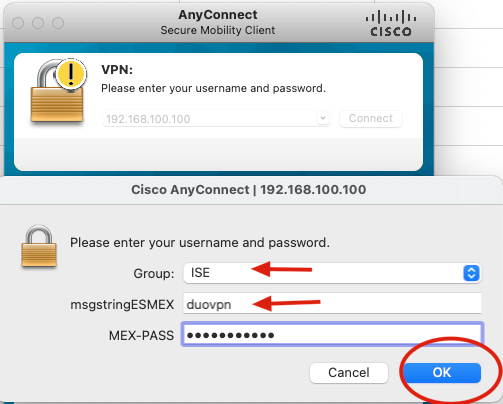
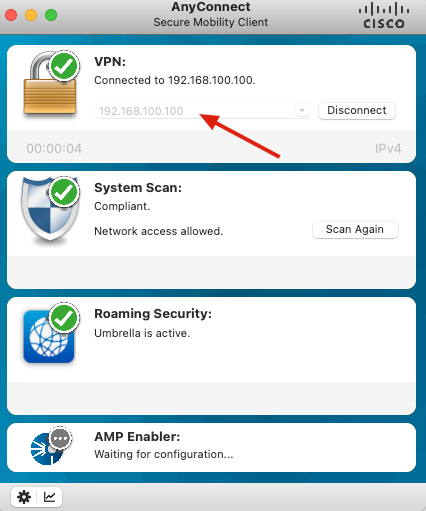
1. Open Anyconnect app on your PC device. Specify the hostname of the VPN ASA Headend and log in with the user created for Duo secondary authentication, and click OK.
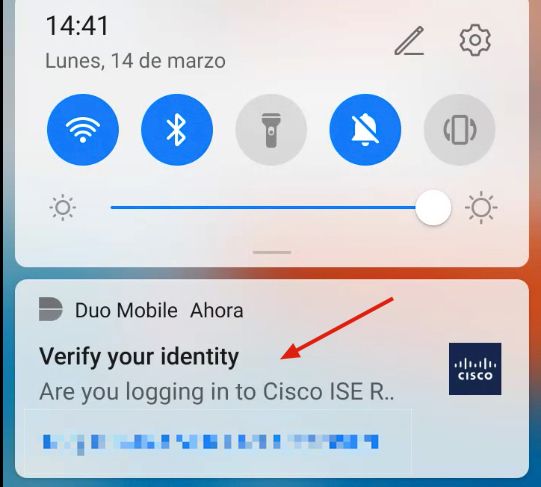
2. You received a Duo push notification on the specified user Duo Mobile device.
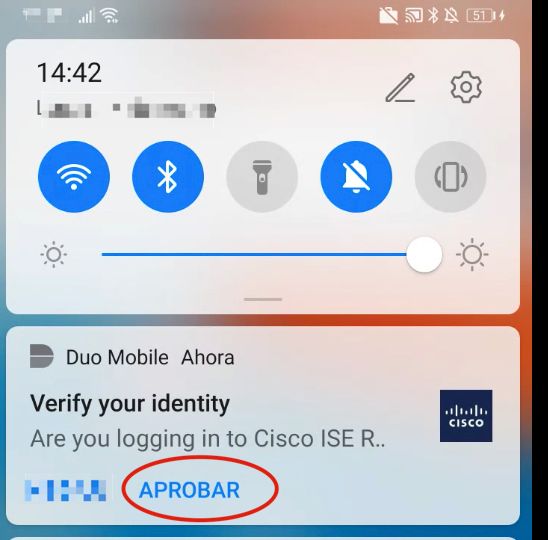
3. Open the Duo Mobile App notification and click Approve.
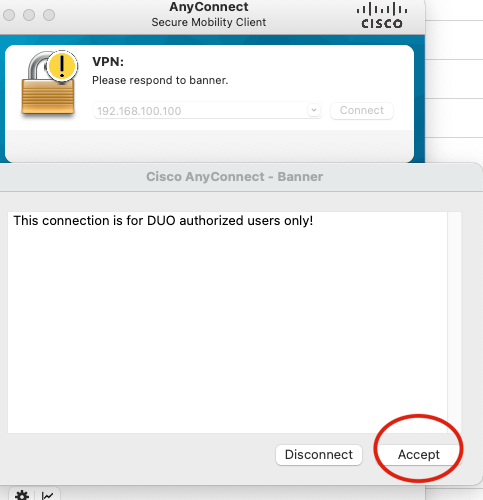
4. Accept the banner, and the connection is established.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
Duo Authentication Proxy comes with a debug tool that displays error and failure reasons.
Work Debugs
Note: The next information is stored in C:\Program Files\Duo Security Authentication Proxy\log\connectivity_tool.log.
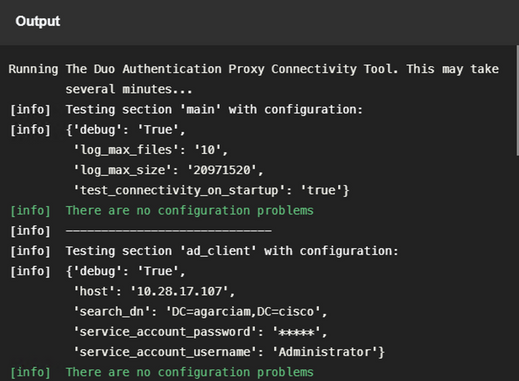
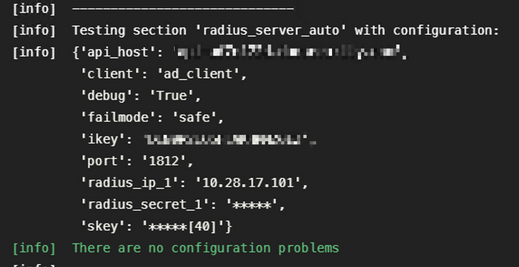
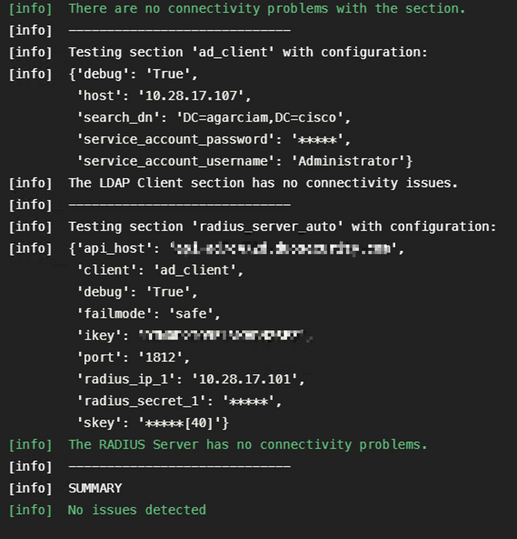
1. Connectivity issues, wrong IP, unresolvable FQDN/Hostname on Active Directory configuration.
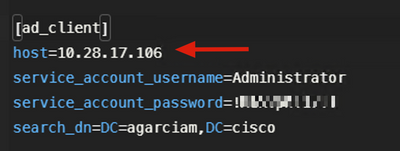
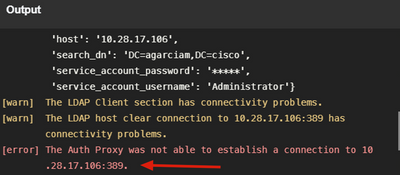
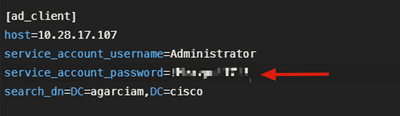
2. Wrong password for Administrator user on Active Directory.
Debugs
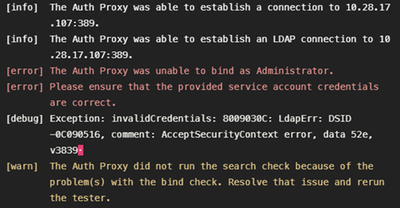
3. Wrong Base Domain
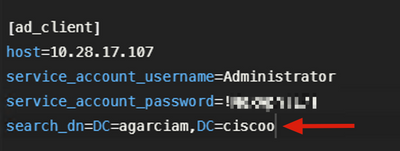
Debugs
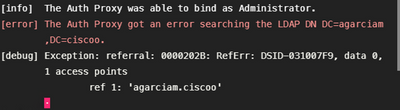
4. Wrong ikey RADIUS value
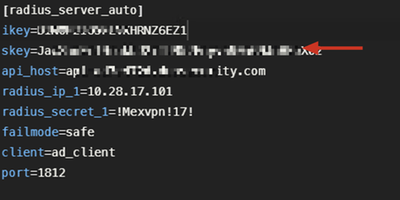
Debugs
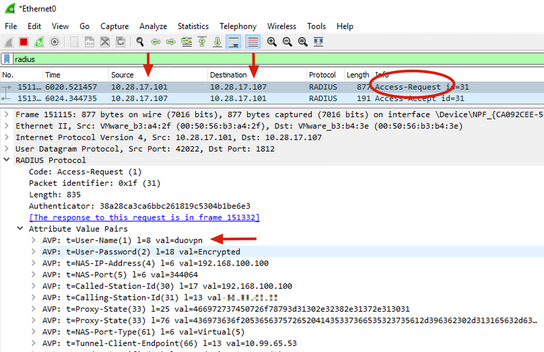
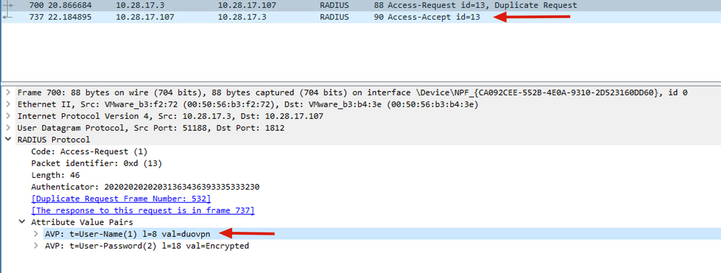
5. Verify ISE Server sends Access-Request packets.
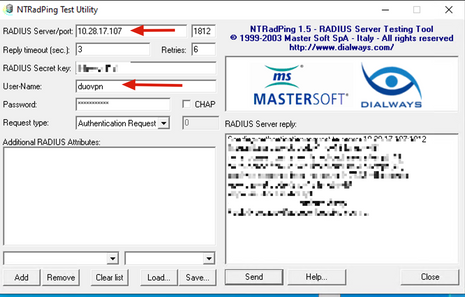
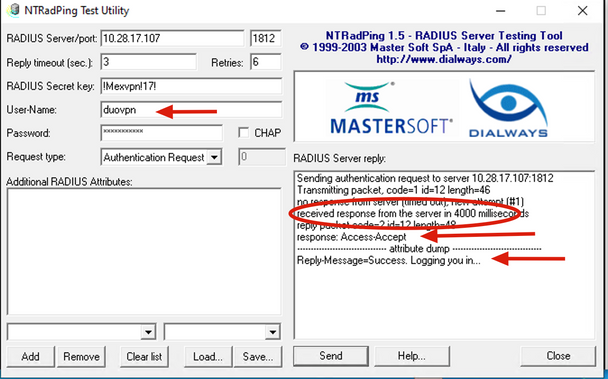
6. In order to confirm Duo Authentication Proxy server works, Duo provides the tool NTRadPing to simulate Access-request packets and response with Duo.
6.1 Install NTRadPing on a different PC and generate traffic.
Note: In this example, the 10.28.17.3 Windows machine is used.
6.2 Configure with the attributes used on ISE Radius configuration.
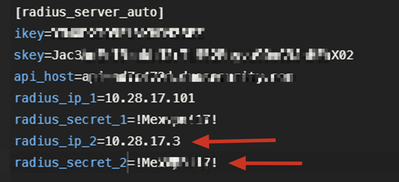
6.3 Configure the Duo Authentication Proxy Manager as follows.
6.4. Navigate to your NTRadPing tool and click Send. You receive a Duo push notification on the assigned mobile device.
























































 Feedback
Feedback