Introduction
This document describes the configuration steps to integrate Microsoft 365 with Cisco Secure Email for inbound and outbound email delivery.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
Components Used
This document is not restricted to specific software and hardware versions.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
This document can be used for either on-premises Gateways or Cisco Cloud Gateways.
If you are a Cisco Secure Email administrator, your welcome letter includes your Cloud Gateway IP addresses and other pertinent information. In addition to the letter you see here, an encrypted email is sent to you that provides you with additional details on the number of Cloud Gateway (also known as ESA) and Cloud Email and Web Manager (also known as SMA) provisioned for your allocation. If you have not received or do not have a copy of the letter, contact ces-activations@cisco.com with your contact information and domain name under service.
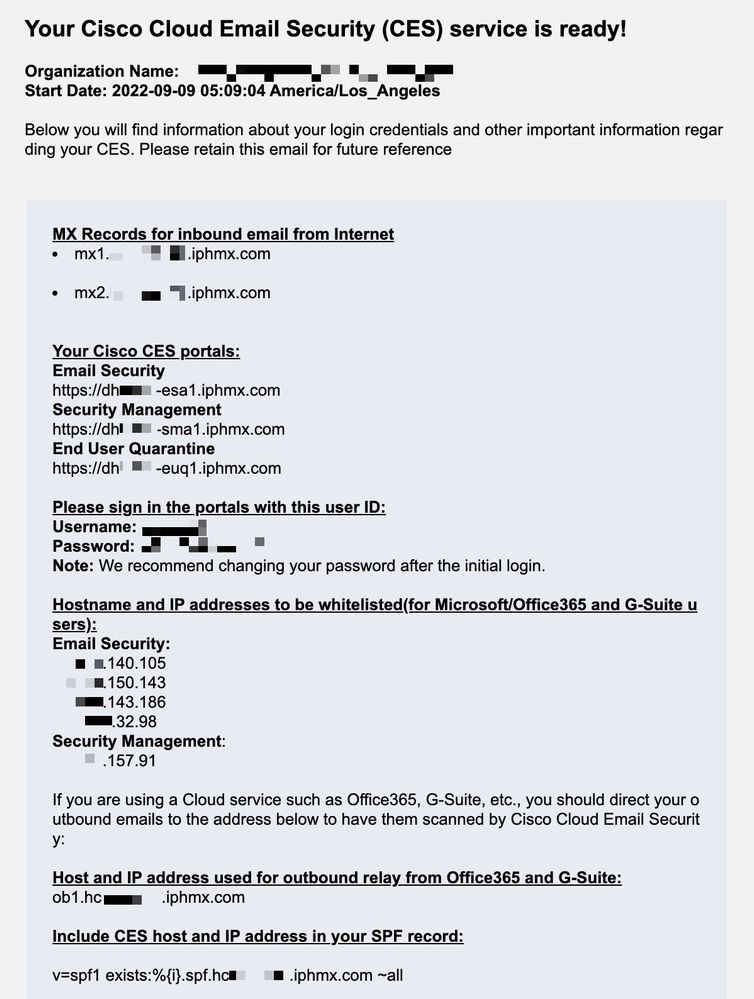
Each client has dedicated IPs. You can use the assigned IPs or hostnames in the Microsoft 365 configuration.
Note: It is highly recommended that you test before any planned production mail cutover because configurations take time to replicate in the Microsoft 365 Exchange console. At a minimum, allow one hour for all changes to take effect.
Note: The IP addresses in the screen capture are proportional to the number of Cloud Gateways provisioned to your allocation. For example, xxx.yy.140.105 is the Data 1 interface IP address for Gateway 1, and xxx.yy.150.1143 is the Data 1 interface IP address for Gateway 2. Data 2 interface IP address for Gateway 1 is xxx.yy.143.186 , and Data 2 interface IP address for Gateway 2 is xxx.yy.32.98. If your welcome letter does not include information for Data 2 (Outgoing interface IPs), contact Cisco TAC to get the Data 2 interface added to your allocation.
Configure Microsoft 365 with Secure Email
Configure Incoming Email in Microsoft 365 from Cisco Secure Email
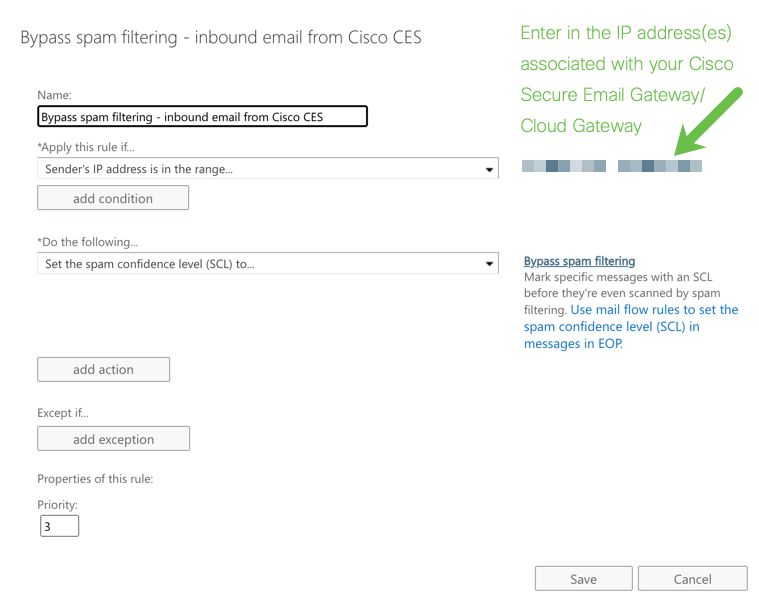
Bypass Spam Filtering Rule
- Log in to the Microsoft 365 Admin Center
- In the left-hand menu, expand
Admin Centers.
- Click
Exchange.
- From the left-hand menu, navigate to
Mail flow > Rules.
- Click
[+] to create a new rule.
- Choose
Bypass spam filtering... from the drop-down list.
- Enter a name for your new rule:
Bypass spam filtering - inbound email from Cisco CES.
- For *Apply this rule if..., choose
The sender - IP address is in any of these ranges or exactly matches.
- For the specify IP address ranges pop-up, add the IP addresses provided in your Cisco Secure Email welcome letter.
- Click
OK.
- For *Do the following..., the new rule has been pre-selected:
Set the spam confidence level (SCL) to... - Bypass spam filtering.
- Click
Save.
An example of how your rule looks:
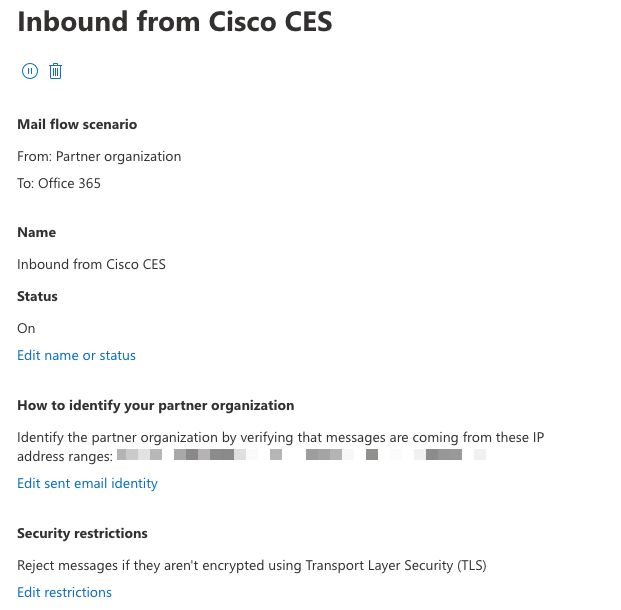
Receiving Connector
- Remain in the Exchange Admin Center.
- From the left-hand menu, navigate to
Mail flow > Connectors.
- Click
[+] to create a new connector.
- In the Select your mail flow scenario pop-up window, choose:
- From:
Partner organization
- To:
Office365
- Click
Next.
- Enter a name for your new connector:
Inbound from Cisco CES.
- Enter a description, if you wish.
- Click
Next.
- Click
Use the sender's IP address.
- Click
Next.
- Click
[+] and enter the IP addresses that are indicated in your Cisco Secure Email welcome letter.
- Click
Next.
- Choose
Reject email messages if they aren't sent over Transport Layer Security (TLS).
- Click
Next.
- Click
Save.
An example of how your connector configuration looks:
Configure Mail from Cisco Secure Email to Microsoft 365
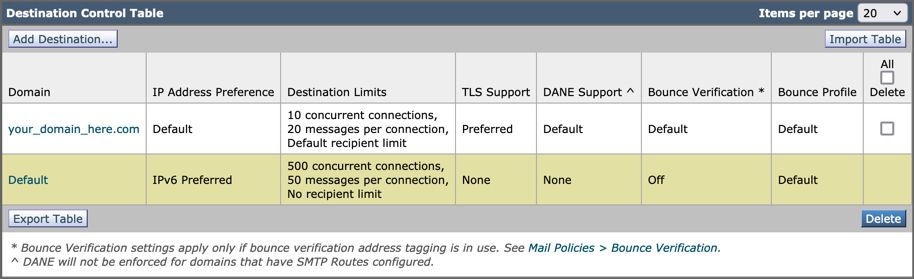
Destination Controls
Impose a self-throttle to a delivery domain in your Destination Controls. Of course, you can remove the throttle later, but these are new IPs to Microsoft 365, and you do not want any throttling by Microsoft due to its unknown reputation.
- Log in to your Gateway.
- Navigate to
Mail Policies > Destination Controls.
- Click
Add Destination.
- Use:
- Destination: enter your domain name
- Concurrent Connections:
10
- Maximum Messages Per Connection:
20
- TLS Support:
Preferred
- Click
Submit.
- Click
Commit Changes in the upper right-hand of the User Interface (UI) to save your configuration changes.
An example of how your Destination Control Table looks:
Recipient Access Table
Next, set the Recipient Access Table (RAT) to accept mail for your domains:
- Navigate to
Mail Policies > Recipient Access Table (RAT).
Note: Make sure the Listener is for Incoming Listener, IncomingMail, or MailFlow, based on the actual name of your Listener for your primary mail flow.
- Click
Add Recipient.
- Add your domains in the Recipient Address field.
- Choose the default action of
Accept.
- Click
Submit.
- Click
Commit Changes in the upper right-hand of the UI to save your configuration changes.
An example of how your RAT entry looks:
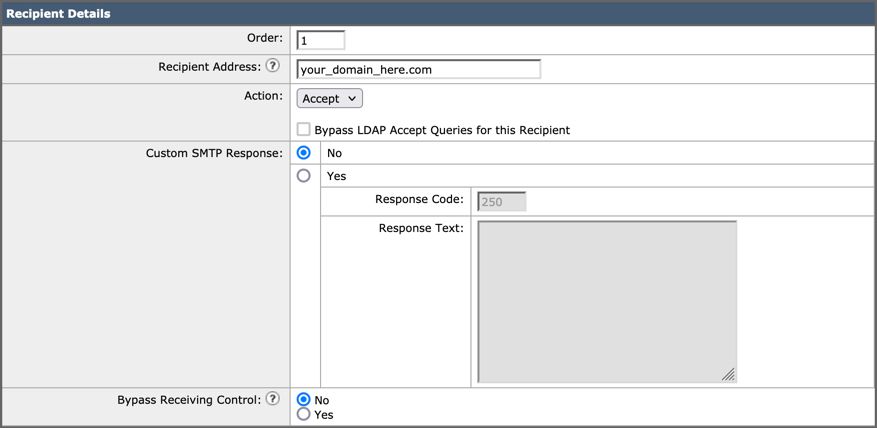
SMTP Routes
Set the SMTP route to deliver mail from Cisco Secure Email to your Microsoft 365 domain:
- Navigate to
Network > SMTP Routes.
- Click
Add Route...
- Receiving Domain: enter your domain name.
- Destination Hosts: add your original Microsoft 365 MX record.
- Click
Submit.
- Click
Commit Changes in the upper right-hand of the UI to save your configuration changes.
An example of how your SMTP Route Settings looks:
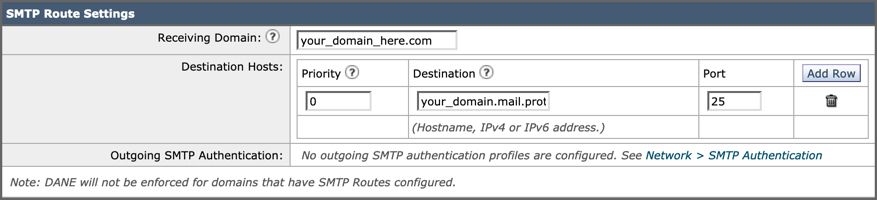
DNS (MX Record) Configuration
You are ready to cut over the domain through a Mail Exchange (MX) record change. Work with your DNS administrator to resolve your MX records to the IP addresses for your Cisco Secure Email Cloud instance, as provided in your Cisco Secure Email welcome letter.
Verify the change to the MX record from your Microsoft 365 console as well:
- Log in to the Microsoft 365 Admin console.
- Navigate to
Home > Settings > Domains.
- Choose your default domain name.
- Click
Check Health.
This provides the current MX Records of how Microsoft 365 looks up your DNS and MX records associated with your domain:
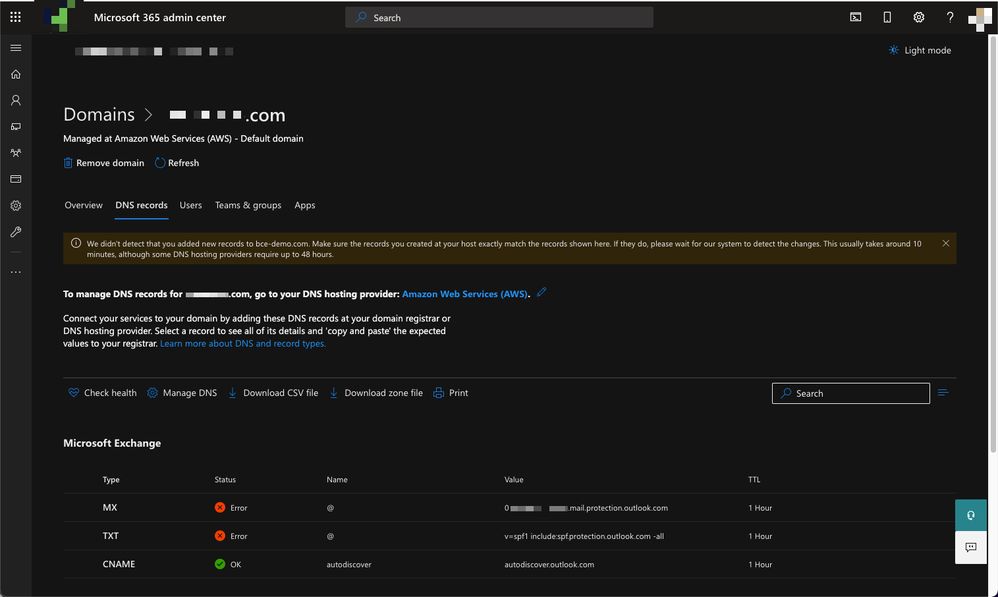
Note: In this example, the DNS is hosted and managed by Amazon Web Services (AWS). As an administrator, expect to see a warning if your DNS is hosted anywhere outside of the Microsoft 365 account. You can ignore warnings like: "We didn't detect that you added new records to your_domain_here.com. Make sure the records you created at your host match those shown here..." The step-by-step instructions reset the MX records to what was initially configured to redirect to your Microsoft 365 account. This removes the Cisco Secure Email Gateway from the incoming traffic flow.
Test Inbound Email
Test inbound mail to your Microsoft 365 email address. Then, check to see that it arrives in your Microsoft 365 email inbox.
Validate the mail logs in Message Tracking on your Cisco Secure Email and Web Manager (also known as SMA) provided with your instance.
To see mail logs on your SMA:
- Log in to your SMA.
- Click
Tracking.
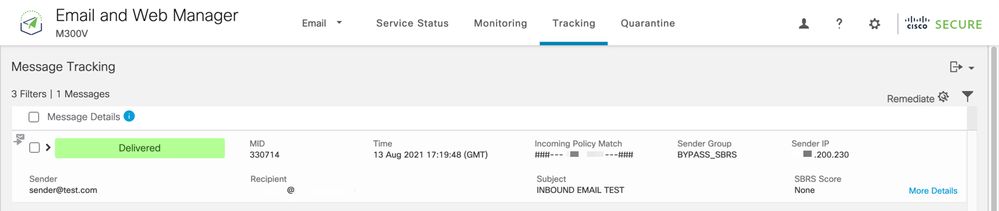
- Enter the needed search criteria and click
Search;and expect to see such results:
To see mail logs in Microsoft 365:
- Log in to the Microsoft 365 Admin Center.
- Expand
Admin Centers.
- Click
Exchange.
- Navigate to
Mail flow > Message trace.
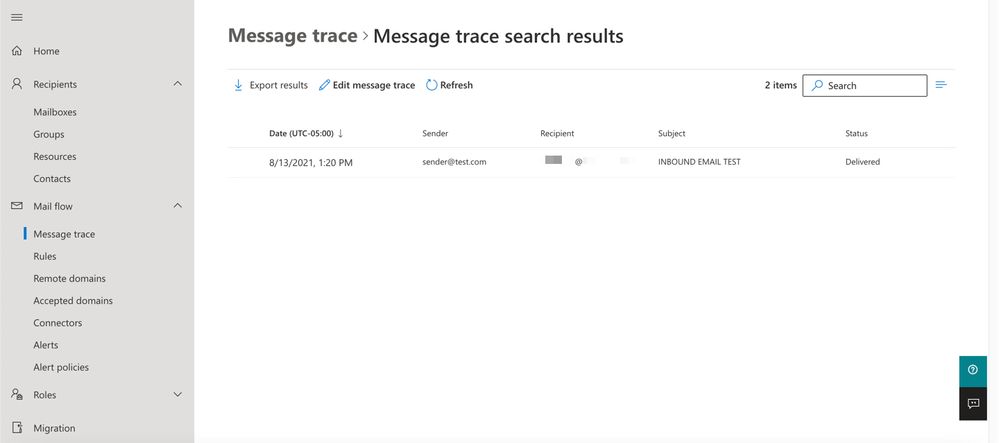
- Microsoft provides Default criteria to search with. For example, choose
Messages received by my primary domain in the last day to start your search query.
- Enter the needed search criteria for recipients and click
Search and expect to see results similar to:
Configure Outgoing Email from Microsoft 365 to Cisco Secure Email
Configure RELAYLIST on Cisco Secure Email Gateway
Refer to your Cisco Secure Email welcome letter. In addition, a secondary interface is specified for outbound messages via your Gateway.
- Log in to your Gateway.
- Navigate to
Mail Policies > HAT Overview.
Note: Make sure the Listener is for Outgoing Listener, OutgoingMail, or MailFlow-Ext, based on the actual name of your Listener for your external/outbound mail flow.
- Click
Add Sender Group...
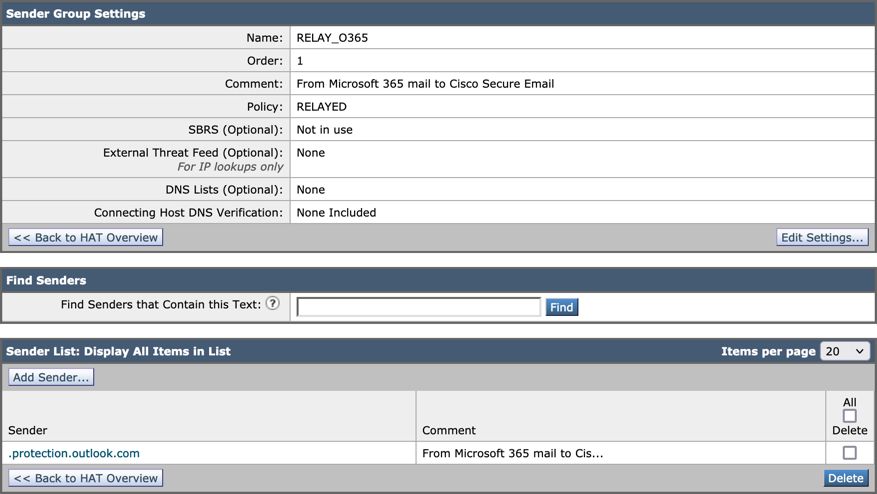
- Configure the Sender Group as:
- Name: RELAY_O365
- Comment: <<enter a comment if you wish to notate your sender group>>
- Policy: RELAYED
- Click
Submit and Add Senders.
- Sender:
.protection.outlook.com
Note: The . (dot) at the beginning of the sender domain name is required.
- Click
Submit.
- Click
Commit Changes in the upper right-hand of the UI to save your configuration changes.
An example of how your Sender Group Settings looks:
Enable TLS
- Click
<<Back to HAT Overview.
- Click the Mail Flow Policy named:
RELAYED.
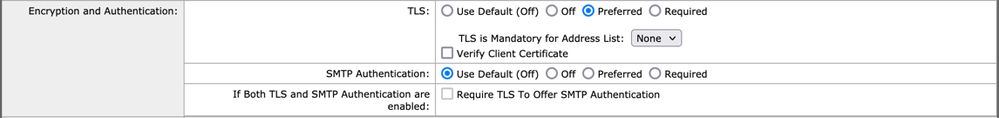
- Scroll down and look in the
Security Features section for Encryption and Authentication.
- For TLS, choose:
Preferred.
- Click
Submit.
- Click
Commit Changes in the upper right-hand of the UI to save your configuration changes.
An example of how your Mail Flow Policy configuration looks:
Configure Mail from Microsoft 365 to CES
- Log in to the Microsoft 365 Admin Center.
- Expand
Admin Centers.
- Click
Exchange.
- Navigate to
Mail flow > Connectors.
- Click
[+] to create a new connector.
- In the Select your mail flow scenario pop-up window, choose:
- From:
Office365
- To:
Partner organization
- Click
Next.
- Enter a name for your new connector:
Outbound to Cisco CES.
- Enter a description, if you wish.
- Click
Next.
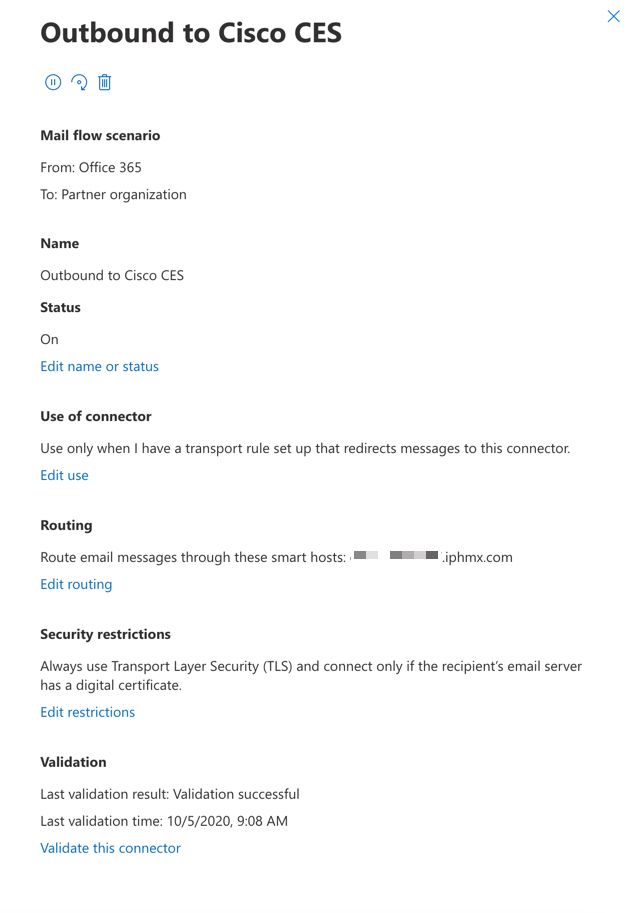
- For When do you want to use this connector?:
- Choose:
Only when I have a transport rule set up that redirects messages to this connector.
- Click
Next.
- Click
Route email through these smart hosts.
- Click
[+] and enter the outbound IP addresses or hostnames provided in your CES welcome letter.
- Click
Save.
- Click
Next.
- For How should Office 365 connect to your partner organization's email server?
- Choose:
Always use TLS to secure the connection (recommended).
- Choose
Any digital certificate, including self-signed certificates.
- Click
Next.
- You are presented with the confirmation screen.
- Click
Next.
- Use
[+] to enter a valid email address and click OK.
- Click
Validate and allow the validation to run.
- Once complete, click
Close.
- Click
Save.
An example of how your Outbound Connector looks:
Create a Mail Flow Rule
- Log in to your Exchange admin center.
- Click
mail flow;be sure to be on the rules tab.
- Click
[+] to add a new rule.
- Choose
Create a new rule.
- Enter a name for your new rule:
Outbound to Cisco CES.
- For *Apply this rule if..., choose:
The sender is located...
- For the select sender location pop-up, choose:
Inside the organization.
- Click
OK.
- Click
More options...
- Click
add condition button and insert a second condition:
- Choose
The recipient...
- Choose:
Is external/internal.
- For the select sender location pop-up, choose:
Outside the organization .
- Click
OK.
- For *Do the following..., choose:
Redirect the message to...
- Select: the following connector.
- And select your Outbound to Cisco CES connector.
- Click OK.
- Return to "*Do the following..." and insert a second action:
- Choose:
Modify the message properties...
- Choose:
set the message header
- Set the message header:
X-OUTBOUND-AUTH.
- Click
OK.
- Set the value:
mysecretkey.
- Click
OK.
- Click
Save.
Note: To prevent unauthorized messages from Microsoft, a secret x-header can be stamped when messages leave your Microsoft 365 domain; this header is evaluated and removed before delivery to the Internet.
An example of how your Microsoft 365 Routing configuration looks:
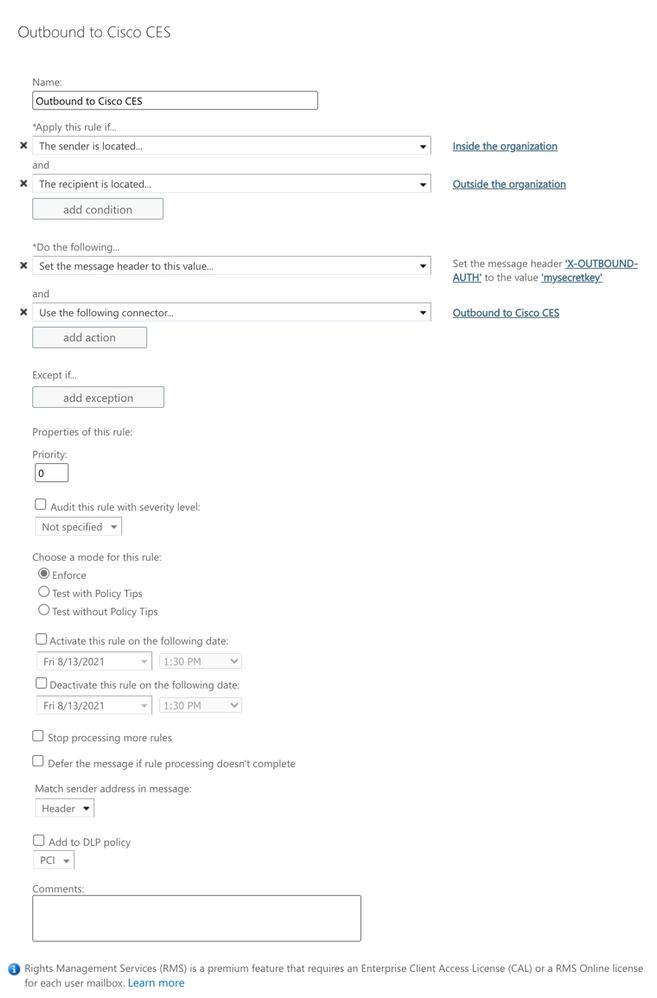
Finally, access the CLI for your Cisco Secure Email Gateway.
Note: Cisco Secure Email Cloud Gateway > Command Line Interface (CLI) Access.
Create a message filter to inspect the presence and value of the x-header and remove the header if it exists. If no header exists, drop the message.
- Log in to your Gateway via the CLI.
- Run the
Filters command.
- If your Gateway is clustered, hit return to edit the filters in Cluster mode.
- Use the
New command to create a Message Filter, copy, and paste:
office365_outbound: if sendergroup == "RELAYLIST" {
if header("X-OUTBOUND-AUTH") == "^mysecretkey$" {
strip-header("X-OUTBOUND-AUTH");
} else {
drop();
}
}
- Hit return one time to create a new, blank line.
- Enter
[.] on the new line to end your new message filter.
- Click
return one time to exit the Filters menu.
- Run the
Commit command to save the changes to your configuration.

Note: Avoid special characters for the secret key. The ^ and $ shown in the message filter are regex characters and use as provided in the example.

Note: Please review the name of how your RELAYLIST is configured. It can be configured with an alternative name, or you can have a specific name based on your relay policy or mail provider.
Test Outbound Email
Test outbound mail from your Microsoft 365 email address to an external domain recipient. You can review Message Tracking from your Cisco Secure Email and Web Manager to ensure it is appropriately routed outbound.
Note: Review your TLS configuration (System Administration > SSL configuration) on the Gateway and the ciphers used for Outbound SMTP. Cisco Best Practices recommends:
HIGH:MEDIUM:@STRENGTH:!aNULL:!eNULL:!LOW:!DES:!MD5:!EXP:!PSK:!DSS:!RC2:!RC4:!SEED:!ECDSA:!ADH:!IDEA:!3DES:!SSLv2:!SSLv3:!TLSv1:-aNULL:-EXPORT:-IDEA
An example of Tracking with successful delivery:
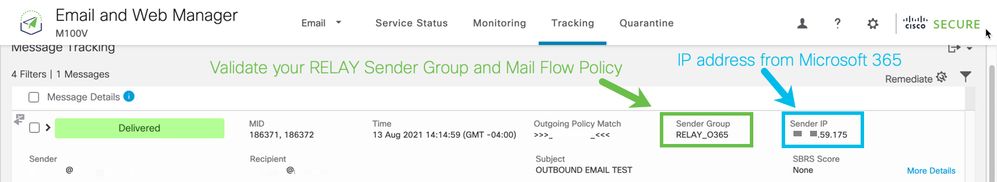
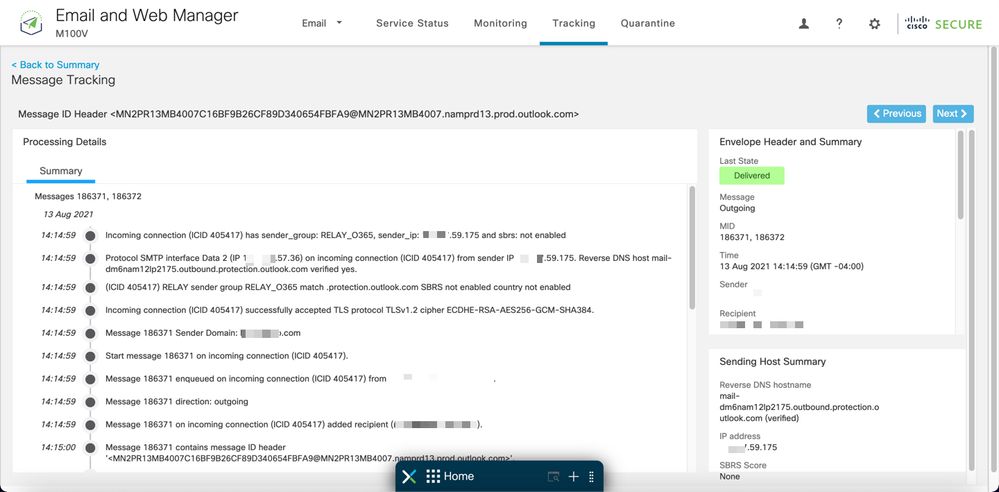
Click More Details to see the complete message details:
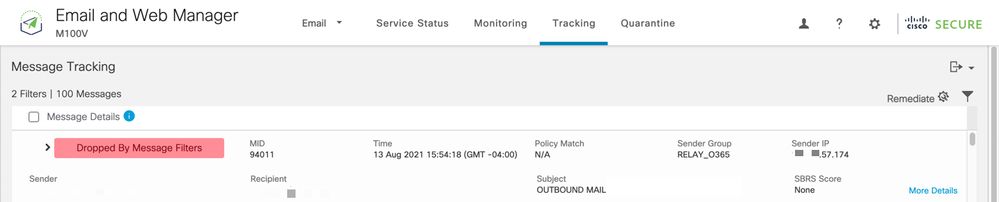
An example of Message Tracking where the x-header does not match:

Related Information
Cisco Secure Email Gateway Documentation
Secure Email Cloud Gateway Documentation
Cisco Secure Email and Web Manager Documentation
Cisco Secure Product Documentation



















 Feedback
Feedback