Introduction:
This document describes the procedures for deploying an RAVPN setup on the FTD managed by FMC and a Site-to-Site tunnel between FTDs.
Prerequisites:
Basic Requirements
- A foundational understanding of site-to-site VPNs and RAVPN is beneficial.
- Understanding the fundamentals of configuring IKEv2 policy based tunnel on Cisco Firepower platform is essential.
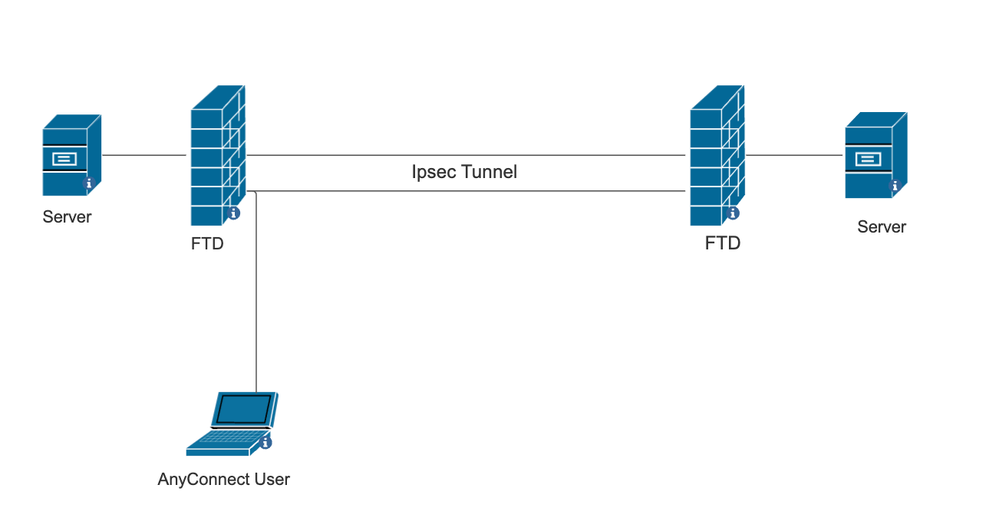
This procedure is for deploying an RAVPN setup on the FTD managed by FMC and a Site-to-Site tunnel between FTDs where AnyConnect user can access the server behind the other FTD peer.
Components Used
- Cisco Firepower Threat Defense for VMware: Version 7.0.0
- Firepower Management Center: Version 7.2.4 (build 169)
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command..
Network Diagram
Configurations on FMC
RAVPN configuration on the FTD managed by FMC.
- Navigate to Devices > Remote Access.
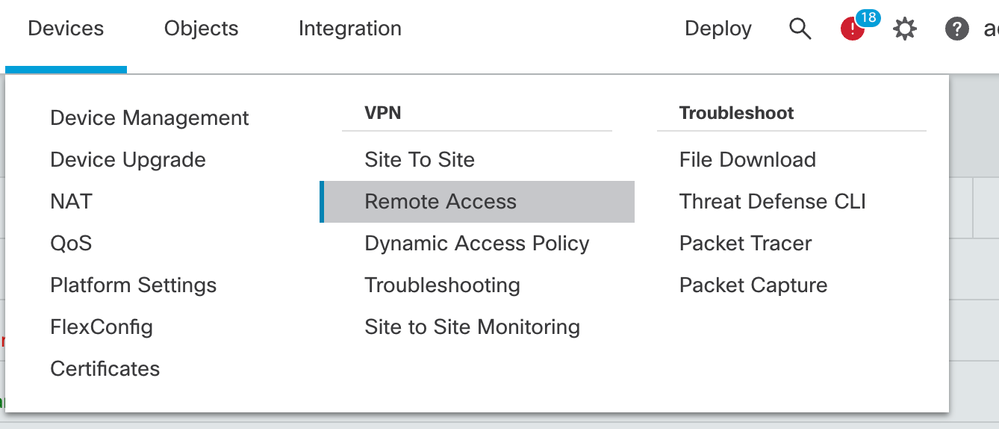
- Click Add.
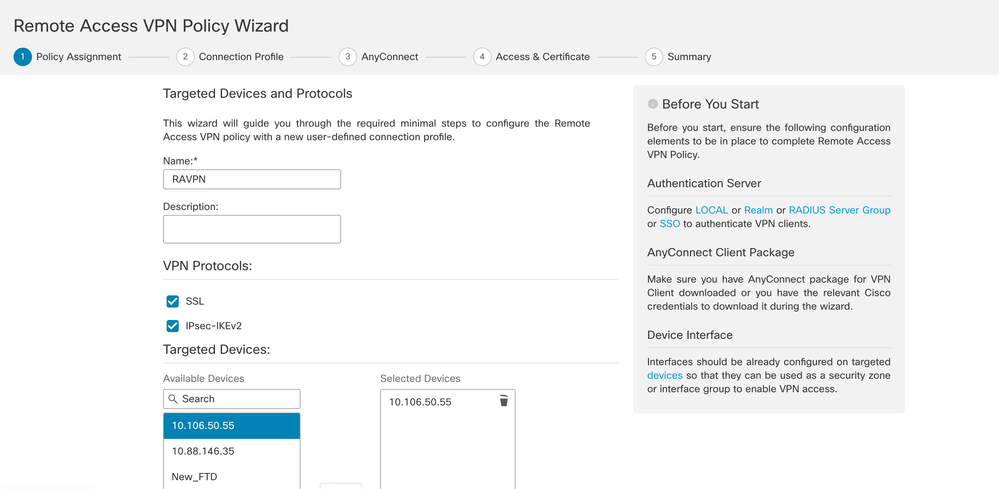
- Configure a name and select the FTD from the available devices and click Next.
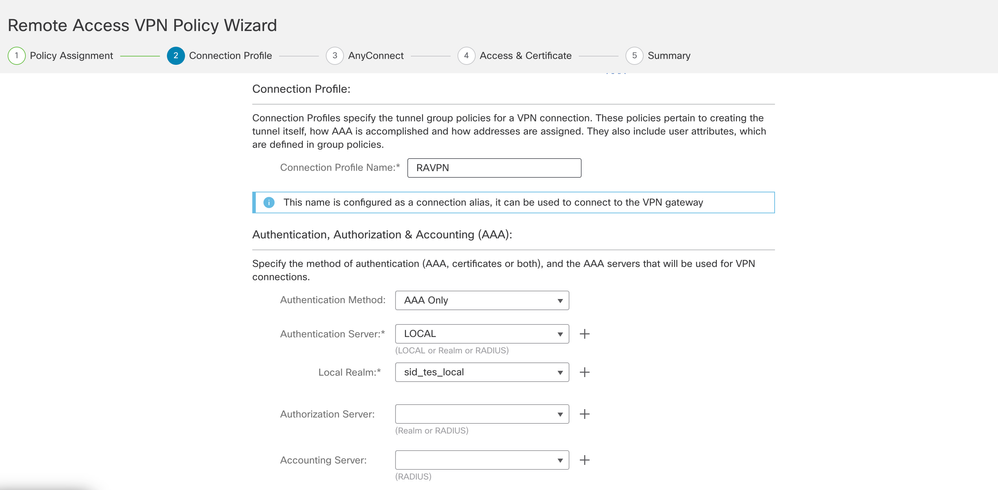
- Configure a connection profile name and choose the authentication method.
NOTE: For this configuration sample we are using AAA only and local authentication. However, configure based on your requirements.
- Configure the VPN pool which is used for IP address assignment for the AnyConnect.
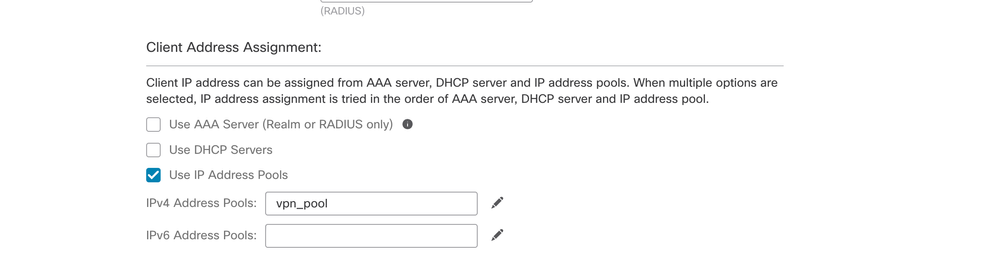
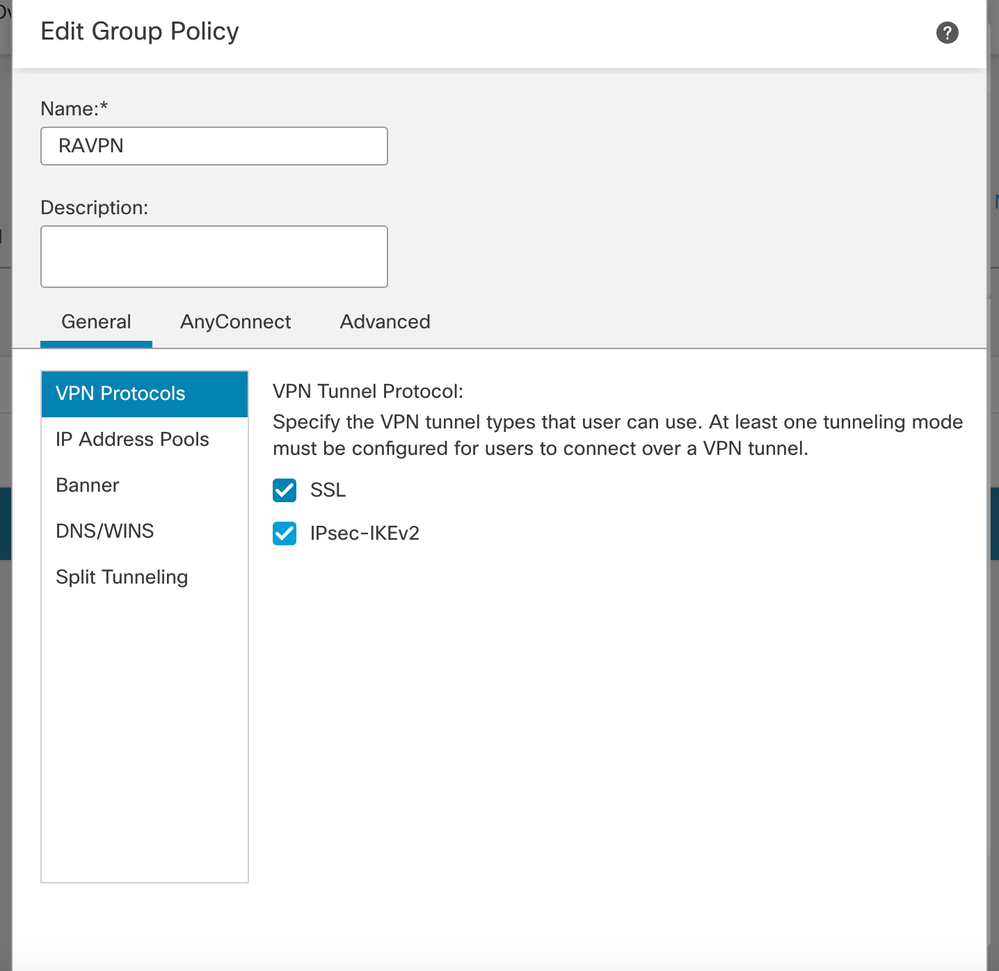
- Create Group-policy. Click + to create a group policy. Add the name of the group policy.
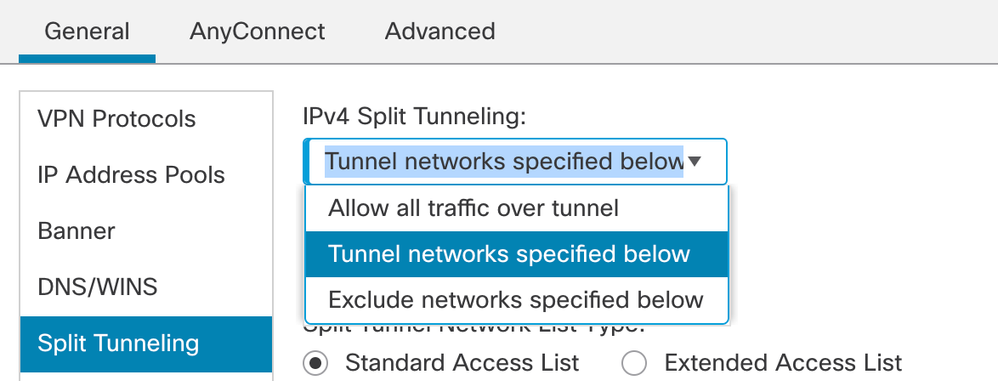
- Go to Split tunnelling. Select the Tunnel networks specified here:
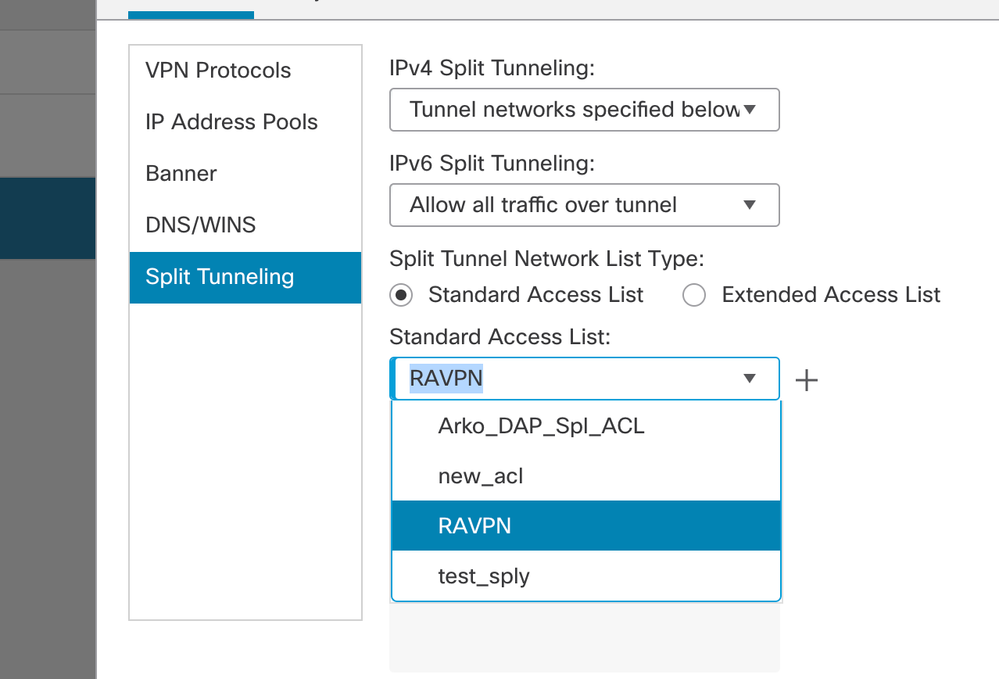
- Select the correct access-list from the drop-down. If an ACL is not already configured: Click on the + icon to add the Standard access-list and create a new one.
Click Save.
- Select the group-policy which is added and click Next.
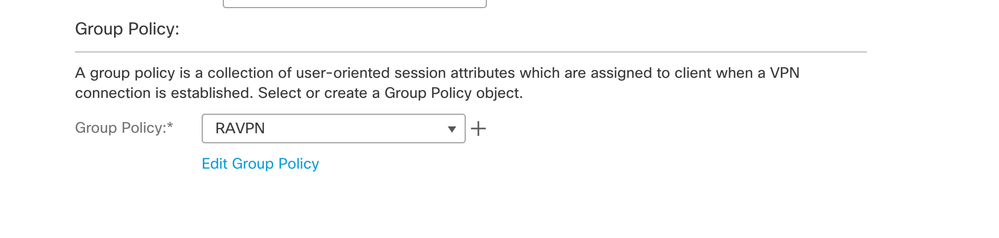
- Select the AnyConnect image.
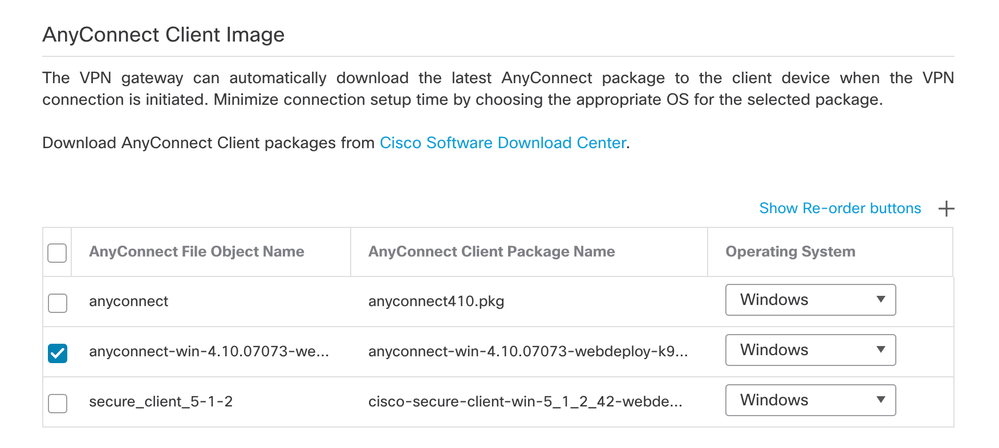
- Select the interface that has to be enabled for AnyConnect connection, add the certificate, select the Bypass Access Control policy for decrypted traffic, and click Next.
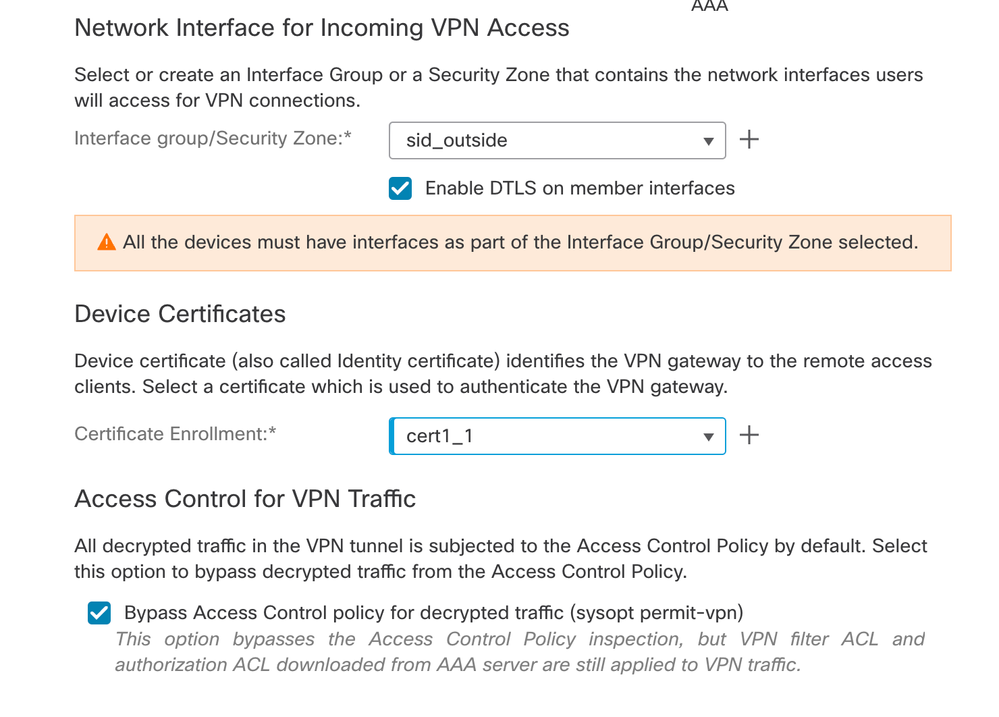
- Review the configuration and click Finish.
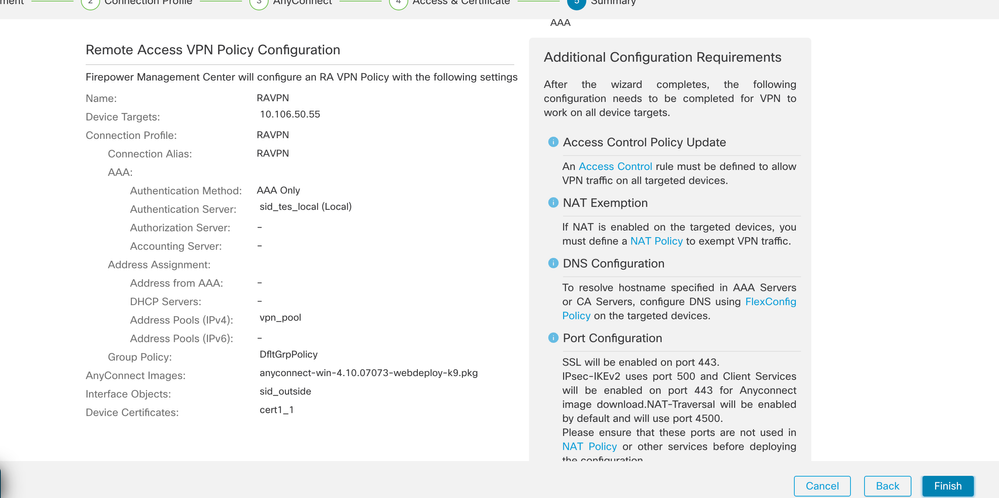
- Click Save and deploy.
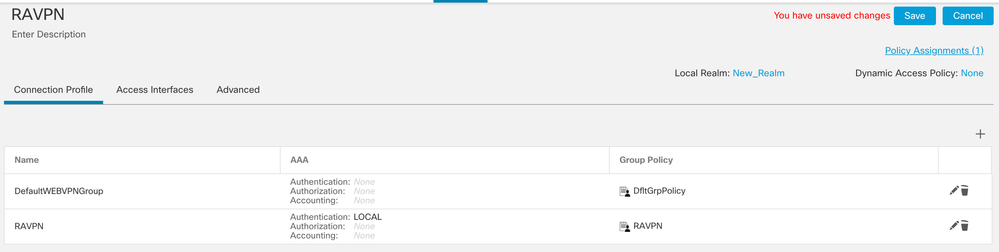
IKEv2 VPN on FTD manage by FMC:
- Navigate to Devices > Site To Site.
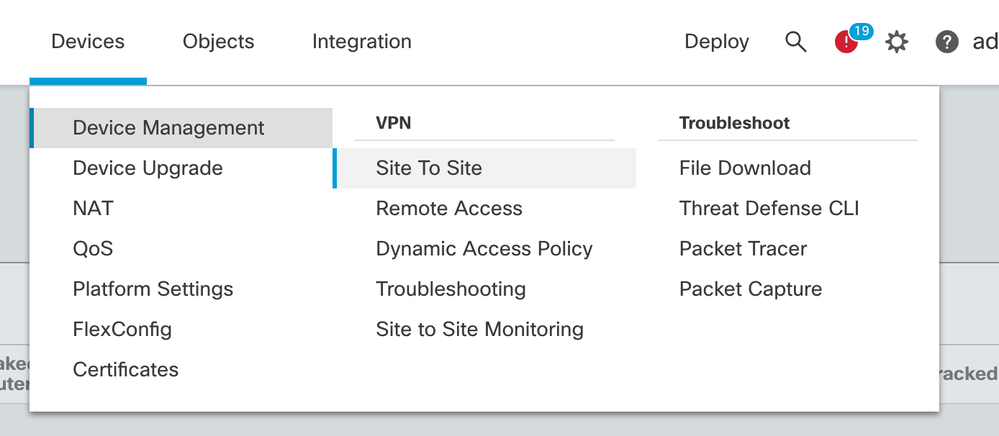
- Click Add.
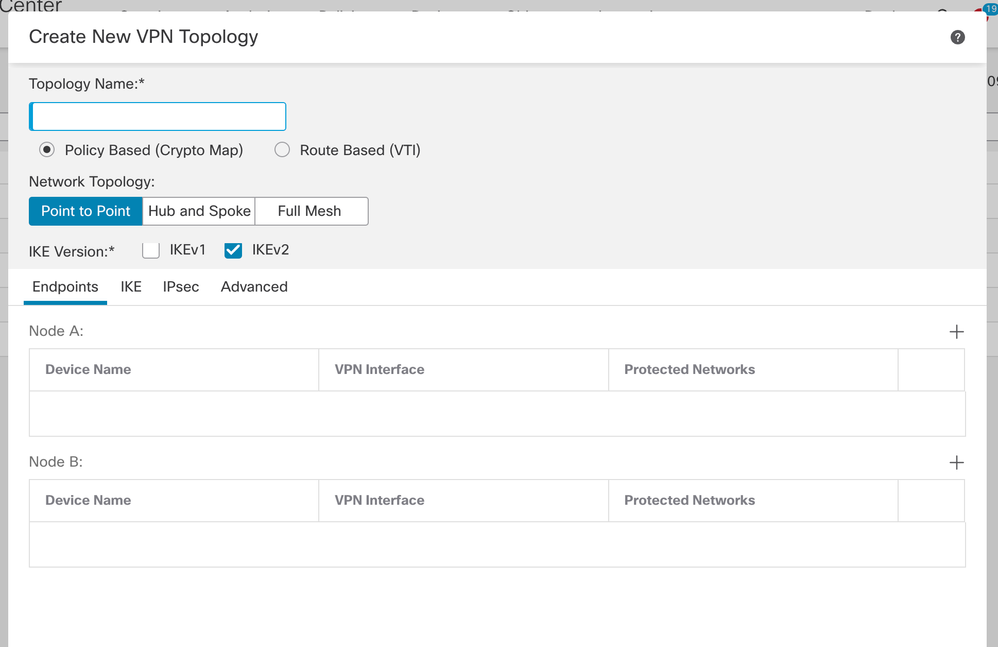
- Click + for Node A:
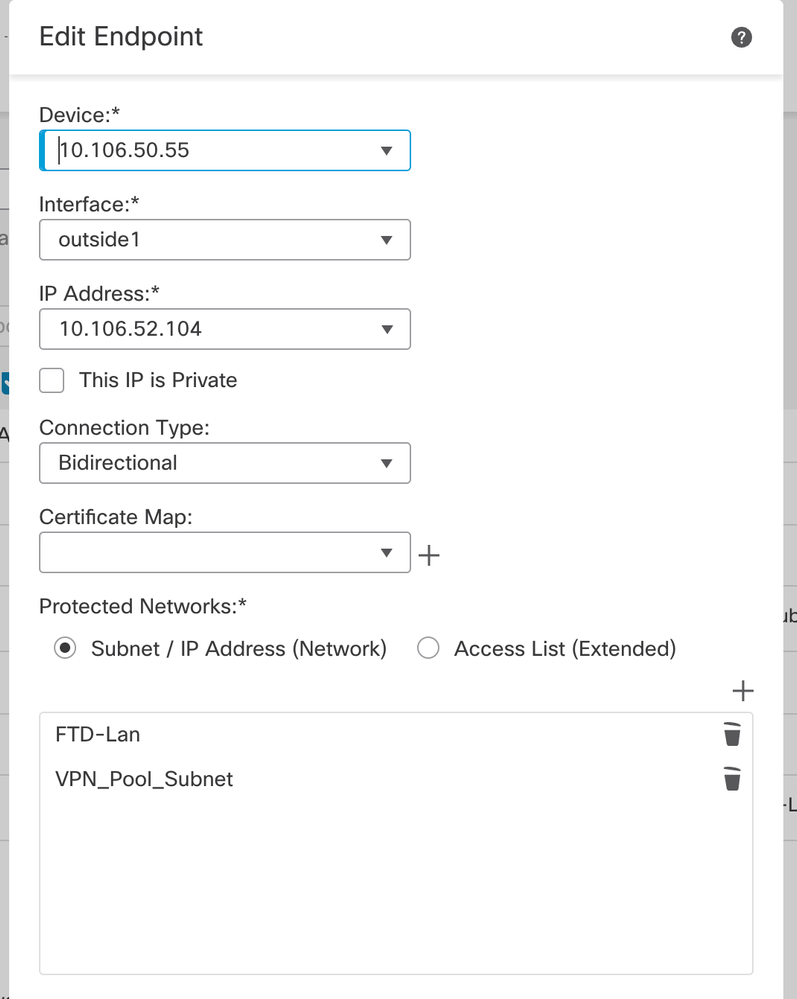
- Select the FTD from the Device, select the interface, add the local subnet that has to be encrypted through the IPSec tunnel (and in this case, also contains the VPN pool addresses), and click OK.
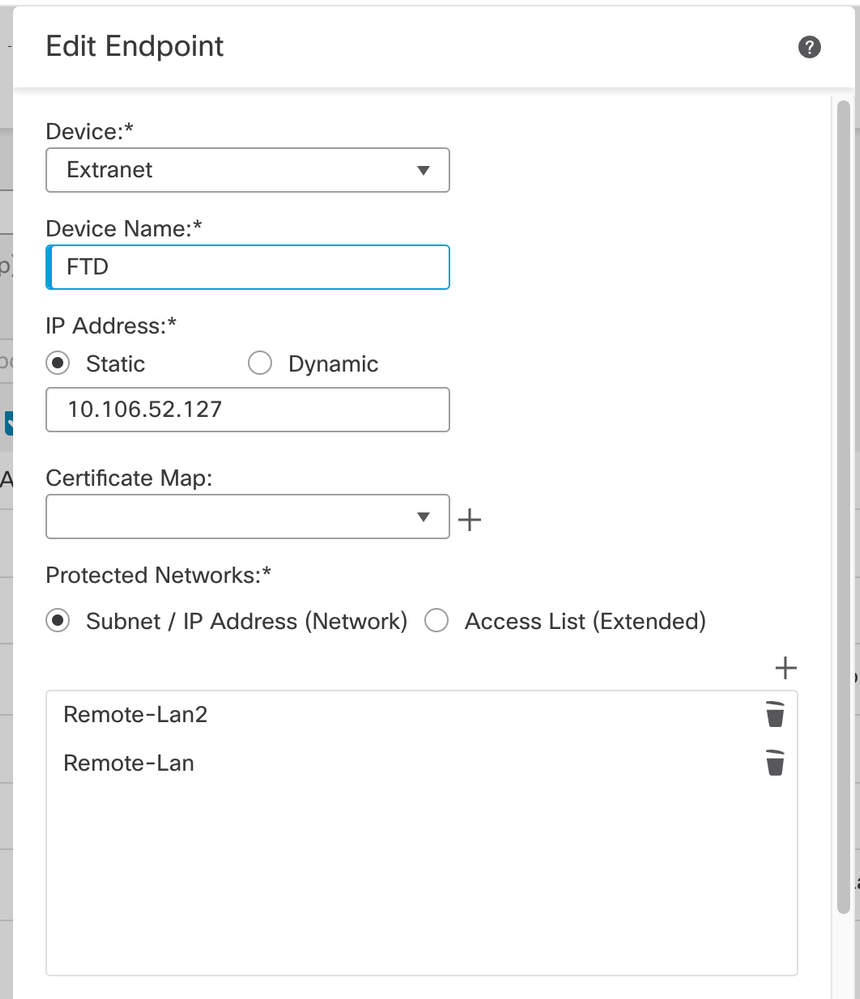
- Click on + for Node B:
> Select the Extranet from the Device, and give the Name of the peer Device.
> Configure the peer details and add the remote subnet that needs to be accessed via the VPN tunnel and click OK.
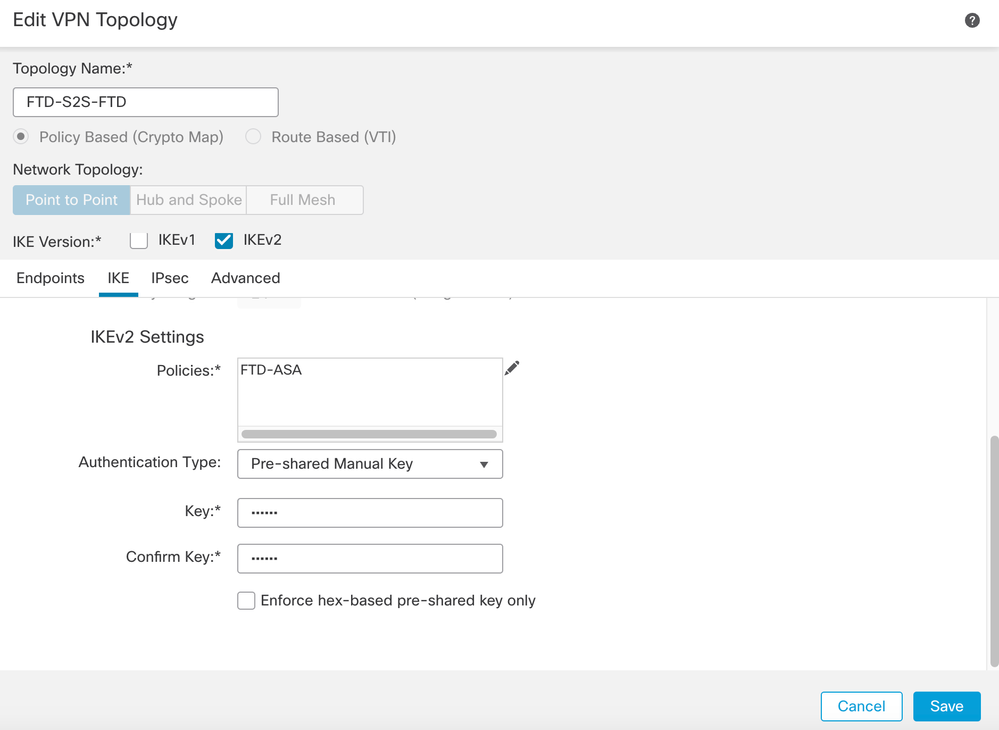
- Click on the IKE tab: Configure the IKEv2 settings as per your requirement
-
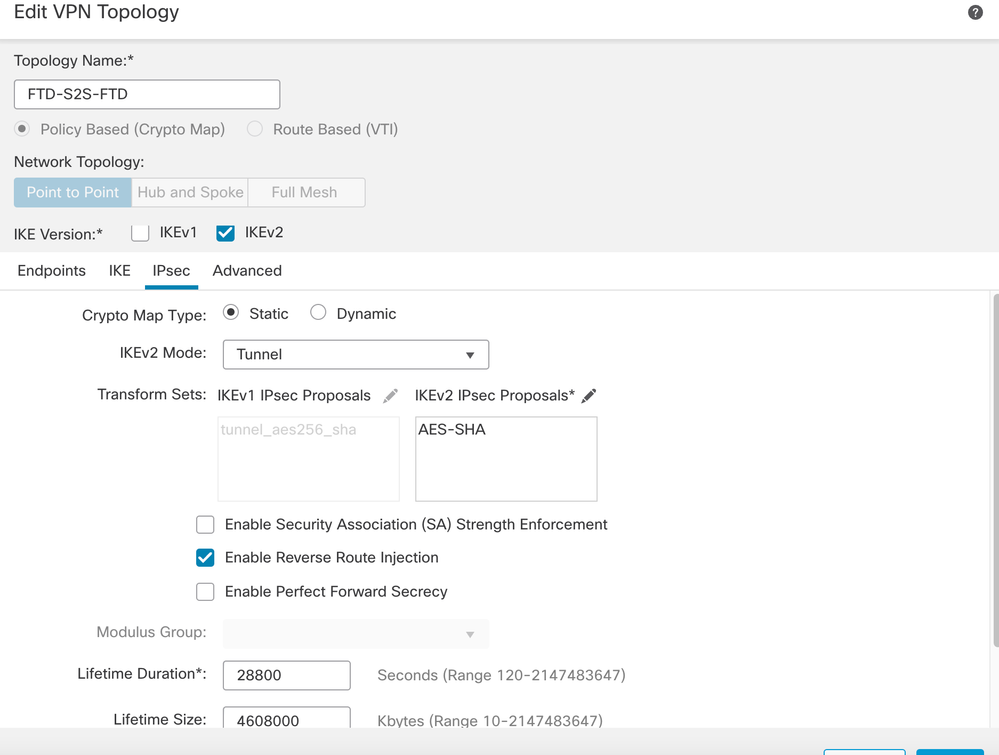
Click on IPsec tab: Configure the IPSec settings as per your requirement.
- Configure Nat-Exempt for your interesting traffic (Optional)
Click on Devices > NAT
- The NAT configured here allows RAVPN and internal users to access servers through the S2S IPSec tunnel.
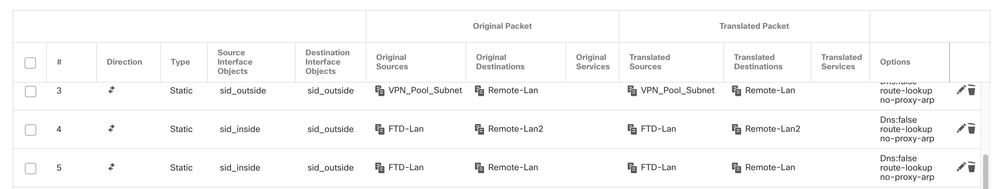
- Similarly do the configuration on the other peer end for the S2S tunnel to come up.
NOTE: The crypto ACL or the interesting traffic subnets have to be mirror copies of each other on both the peers.
Verify
1. To verify the RAVPN connection:
firepower# show vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : test Index : 5869
Assigned IP : 2.2.2.1 Public IP : 10.106.50.179
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel: (1)AES-GCM-256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)SHA384
Bytes Tx : 15470 Bytes Rx : 2147
Group Policy : RAVPN Tunnel Group : RAVPN
Login Time : 03:04:27 UTC Fri Jun 28 2024
Duration : 0h:14m:08s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : 0a6a3468016ed000667e283b
Security Grp : none Tunnel Zone : 0
2. To verify the IKEv2 connection:
firepower# show crypto ikev2 sa
IKEv2 SAs:
Session-id:2443, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
3363898555 10.106.52.104/500 10.106.52.127/500 READY INITIATOR
Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:14, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/259 sec
Child sa: local selector 2.2.2.0/0 - 2.2.2.255/65535
remote selector 10.106.54.0/0 - 10.106.54.255/65535
ESP spi in/out: 0x4588dc5b/0x284a685
3. To verify the IPSec connection:
firepower# show crypto ipsec sa peer 10.106.52.127
peer address: 10.106.52.127
Crypto map tag: CSM_outside1_map, seq num: 2, local addr: 10.106.52.104
access-list CSM_IPSEC_ACL_1 extended permit ip 2.2.2.0 255.255.255.0 10.106.54.0 255.255.255.0
local ident (addr/mask/prot/port): (2.2.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.106.54.0/255.255.255.0/0/0)
current_peer: 10.106.52.127
#pkts encaps: 3, #pkts encrypt: 3, #pkts digest: 3
#pkts decaps: 3, #pkts decrypt: 3, #pkts verify: 3
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 3, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.106.52.104/500, remote crypto endpt.: 10.106.52.127/500
path mtu 1500, ipsec overhead 94(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 0284A685
current inbound spi : 4588DC5B
inbound esp sas:
spi: 0x4588DC5B (1166597211)
SA State: active
transform: esp-aes-256 esp-sha-512-hmac no compression
in use settings ={L2L, Tunnel, IKEv2, }
slot: 0, conn_id: 5882, crypto-map: CSM_outside1_map
sa timing: remaining key lifetime (kB/sec): (3962879/28734)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x0000000F
outbound esp sas:
spi: 0x0284A685 (42247813)
SA State: active
transform: esp-aes-256 esp-sha-512-hmac no compression
in use settings ={L2L, Tunnel, IKEv2, }
slot: 0, conn_id: 5882, crypto-map: CSM_outside1_map
sa timing: remaining key lifetime (kB/sec): (4285439/28734)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Troubleshoot
- To troubleshoot the AnyConnect connection issue collect dart bundle or enable the AnyConnect debugs.
- To troubleshoot the IKEv2 tunnel, use these debugs:
debug crypto condition peer <peer IP address>
debug crypto ikev2 platform 255
debug crypto ikev2 protocol 255
debug crypto ipsec 255
3. To troubleshoot the traffic issue on the FTD take packet capture and check configuration.






















 Feedback
Feedback