Perform Endpoint IOC Scans with AMP for Endpoints or FireAMP
Available Languages
Contents
Introduction
This document describes how to create an Indication of Compromise (IOC) signature file via the Mandiant IOC editor, how to upload it to the Cisco FireAMP dashboard, and how to initiate an endpoint IOC scan.
Prerequisites
Requirements
Cisco recommends that you have at least one gigabyte of free drive space before you attempt to run the endpoint IOC scans.
Components Used
The information in this document is based on the endpoint IOC scanner, which is available in the Cisco FireAMP Windows Connector Versions 4.0.2 and later.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
The endpoint IOC scanner feature is a powerful incident response tool that is used in order to scan post-compromise indicators across multiple computers.
IOC Signature Files
The IOC signature file is an extensible XML schema for the description of technical characteristics that identify a known threat, an attacker methodology, or other evidence of compromise.
You can import endpoint IOCs through the console from OpenIOC-based files that are written in order to trigger on file properties such as name, size, and hash, as well as other attributes and system properties such as process information, running services, and Microsoft Windows Registry entries. The IOC syntax can be used by incident responders in order to find specific artifacts or in order to use logic to create sophisticated, correlated detections for families of malware.
Run a Scan on an IOC Signature File
There are three steps that you must complete in order to run a scan on a IOC signature file:
- Create an IOC signature file.
- Upload the IOC signature file.
- Initiate a scan.
These steps are expanded upon in the sections that follow.
Create an IOC Signature File
Complete these steps in order to create an IOC signature file:
- Open the IOCe and navigate to File > New > Indicator. This provides a blank workspace so that you can begin to build an IOC.
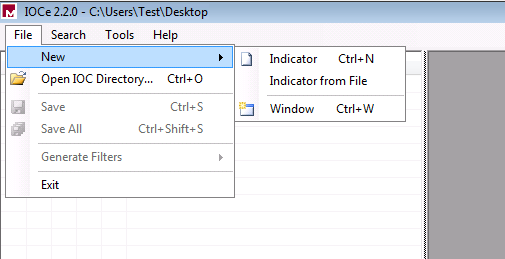
- Click the Items drop-down menu in order to add operators. The first property that you should add is File Extension contains. Find the property in the Items tree menu and click it.
- After you add a property, click the small icon on the far right side of the screen in order to open the Configuration pane. Within this pane, use the Content field in order to match a file extension. For example, add txt in order to match the test.txt text file:

- You must now add a logic operator. In this example, you will match the test text file. In order to match this, use an AND operator and add the next property. Locate the file name and select it from the Items tree menu. In the Properties pane, add the name of the file that you want to find. For example, add test in the Content field:

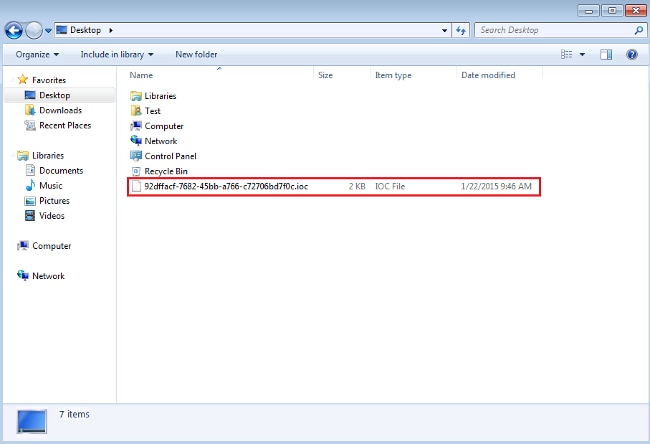
- Since no additional properties are necessary for this simple IOC, you can now save the file. Click File > Save, and a signature file with a .ioc extension is saved on the system:
Upload an IOC Signature File
In order to perform a scan, you must upload an IOC file to the FireAMP dashboard. You can use an IOC signature file, an XML file, or a zip archive that contains multiple IOC files. The dashboard decompresses and parses the file with the IOC signatures. You are notified if an incorrect syntax or an unsupported property is used.
Complete these steps in order to upload the IOC signature file to the FireAMP dashboard:
- Log into the FireAMP Cloud Console and navigate to Outbreak Control > Installed Endpoint IOC.
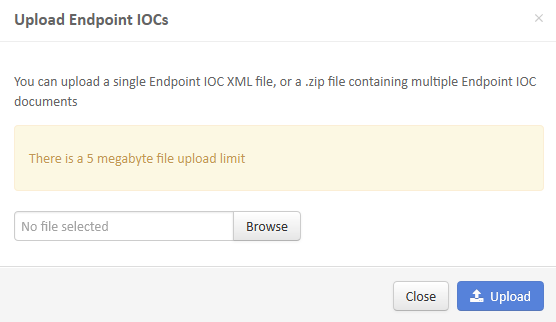
- Click Upload, and the Upload Endpoint IOCs window appears:
After an IOC signature file is uploaded successfully, the signature appears on the list: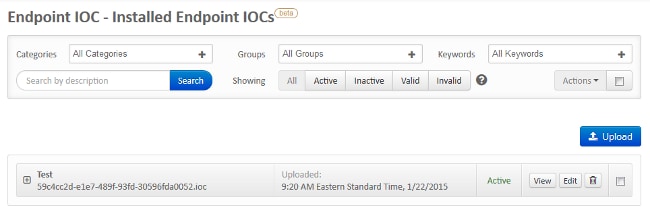
- Click View in order to view the actual XML data of the signature:
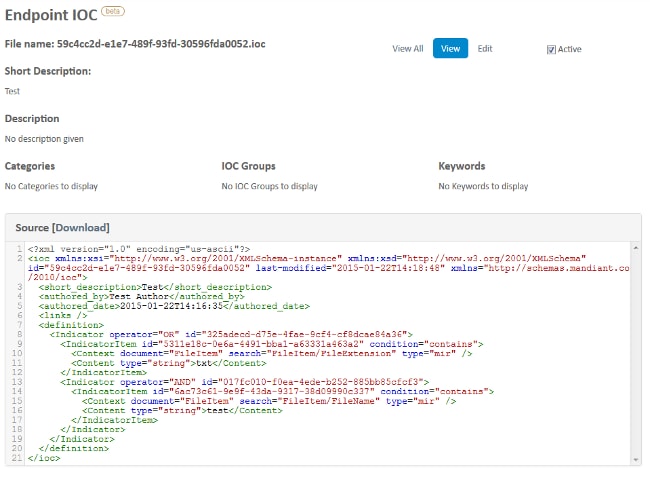
Initiate a Scan
After you upload a signature file, perform a full scan. The first scan must be a full scan because it must build a catalog of metadata for the entire computer, which can take 1–2 hours. You can perform a flash scan after the system is cataloged through a full scan.
There are two different methods that you can use in order to run an IOC scan. The first method is to perform an immediate scan from an event or from the dashboard. This is triggered the next time that a PC sends a heartbeat to the Cloud.
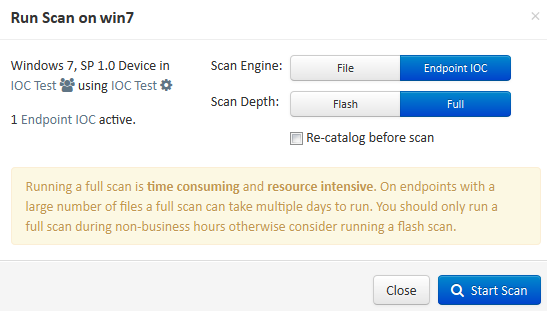
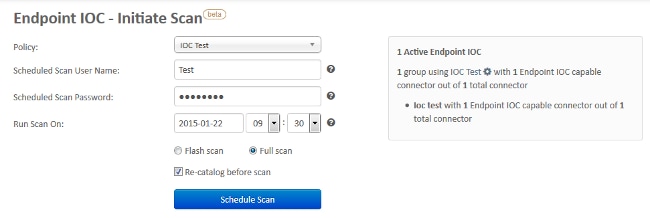
The second method is to create a scheduled endpoint IOC scan from the Outbreak Control menu of the dashboard. This option might be ideal when you desire to perform scans during off-peak hours. You must provide the credentials of an account that has permission on the given computer in order to create scheduled tasks and allow the Log on as Batch group policy permission.
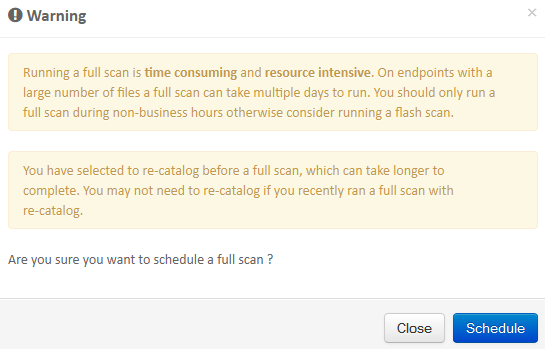
When you schedule an endpoint IOC scan, this warning message appears:
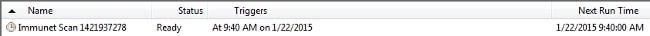
The next time that your PC sends a heartbeat, and if your credentials are valid, you should see a job similar to this in the Windows Task Scheduler:
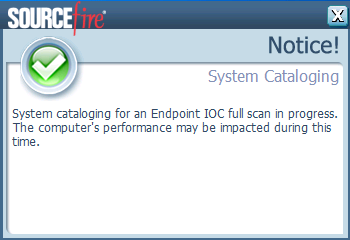
When the scan begins, this message appears:
When the scan is complete, you are able to view the Endpoint IOC Scan Detection Summary. This example shows a match for the test.txt IOC signature file:

Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
08-Apr-2015 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)







 Feedback
Feedback