Introduction
This document describes an example of Adaptive Security Appliance (ASA) to Firepower Threat Defense (FTD) migration on FPR4145.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Basic knowledge of ASA
- Knowledge of Firepower Management Center (FMC) and FTD
Components Used
The information in this document is based on these software and hardware versions:
- ASA Version 9.12(2)
- FTD Version 6.7.0
- FMC Version 6.7.0
- Firepower Migration Tool version 2.5.0
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
Export the ASA configuration file in .cfg or .txt format. FMC must be deployed with FTD registered under it.
Configure
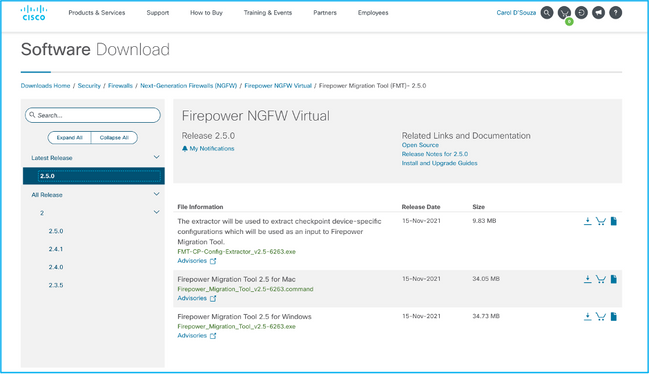
1. Download the Firepower Migration Tool from software.cisco.com as shown in the image.
2. Review and verify the requirements for the Firepower Migration Tool section.
3. If you are planning to migrate a large configuration file, configure sleep settings so the system does not go to sleep during a migration push.
3.1. For Windows, navigate to Power Options in the Control Panel. Click Change Plan Settings next to your current power plan and then toggle Put the computer to sleep to Never. Click Save Changes.
3.2. For MAC, navigate to System Preferences > Energy Saver. Tick the box next to Prevent the Computer from Sleeping Automatically when the display is off and drag the Turn Display Off after slider to Never.
Note: This warning, dialog pops up when MAC users try to open the downloaded file. Ignore this and follow Step 4.1.
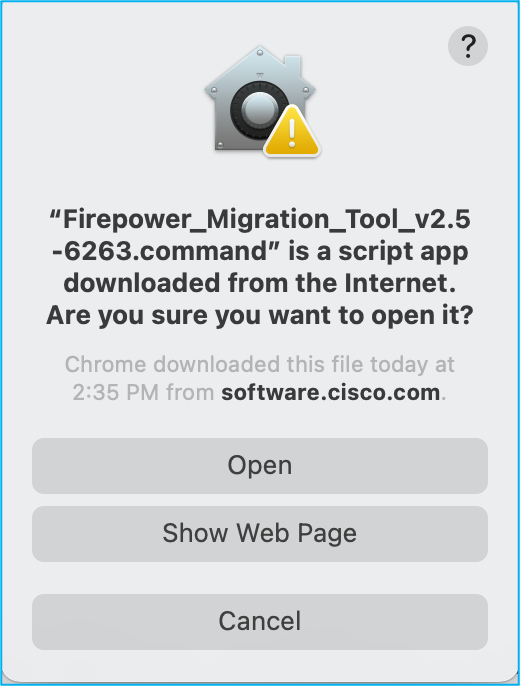
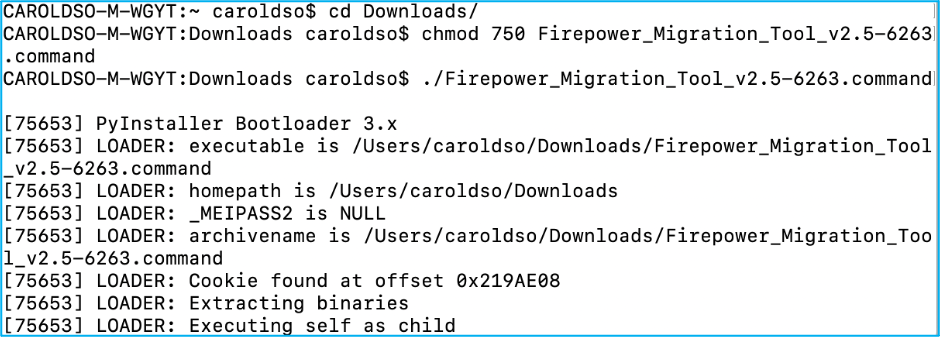
4.1. For MAC - Use the terminal and run these commands:
4.2. For Windows - double-click the Firepower Migration Tool in order to launch it in a Google Chrome browser.
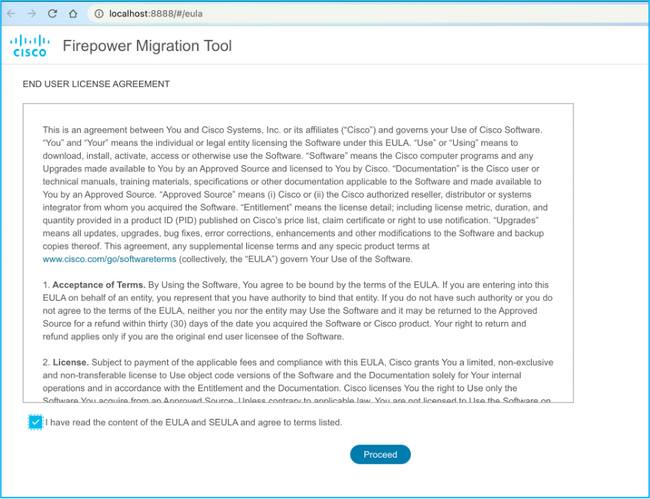
5. Accept the license as shown in the image:
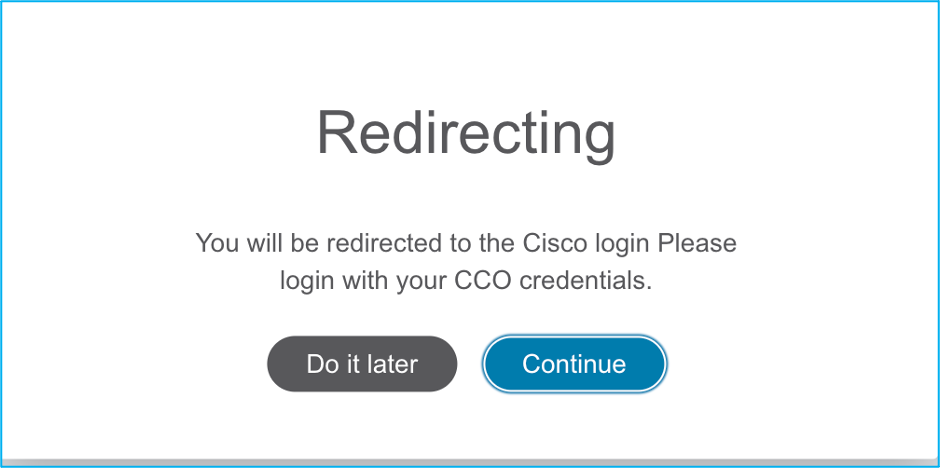
6. On the login page of the Firepower Migration Tool, click the login with Cisco Connection Online (CCO) link in order to log in to your Cisco.com account with your single-sign-on credentials.
Note: If you do not have a Cisco.com account, create it on the Cisco.com login page. Log in with these default credentials: Username—admin and Password—Admin123.
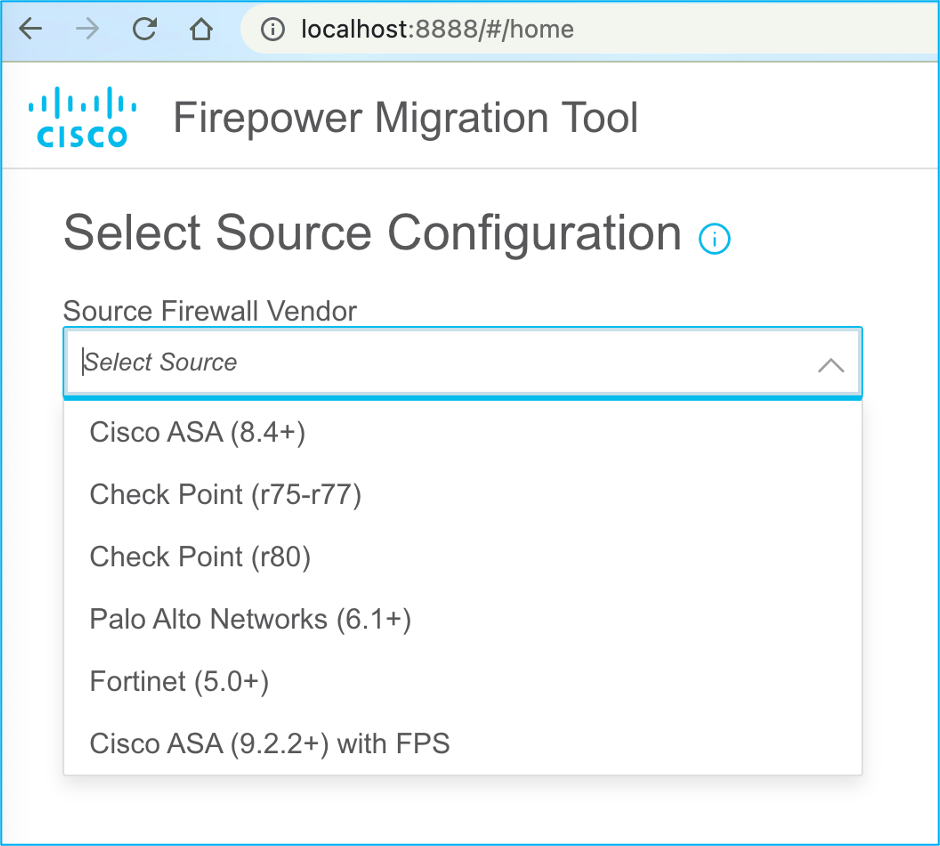
7. Choose the source configuration. In this scenario, it is Cisco ASA (8.4+).
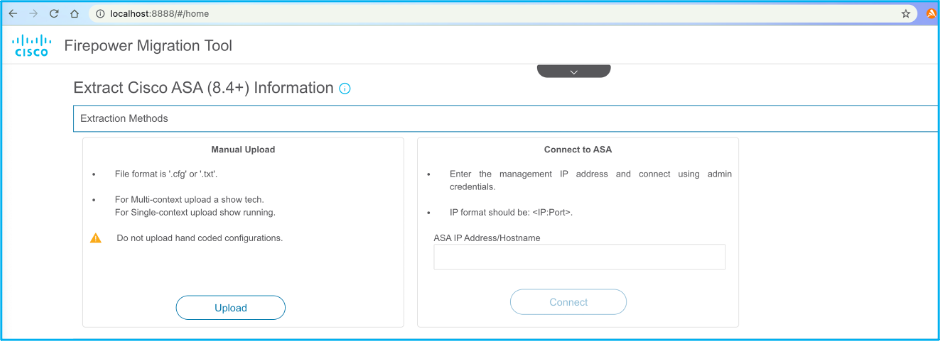
8. Choose Manual Upload if you do not have connectivity to the ASA. Otherwise, you can retrieve the running configuration from the ASA and enter the management IP and login details. In this scenario, a manual upload was performed.
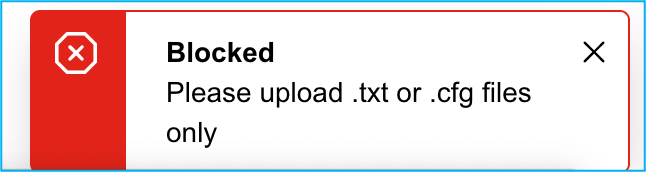
Note: This error is seen if the file is not supported. Ensure to change the format to plain text. (Error is seen despite having extension .cfg.)
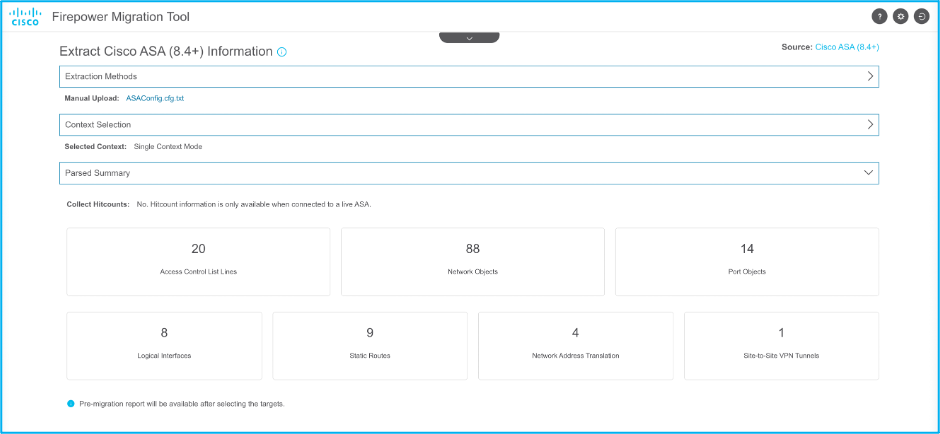
9. After the file is uploaded, the elements are parsed providing a summary as shown in the image:
10. Enter the FMC IP and login credentials to which the ASA configuration is to be migrated. Ensure that the FMC IP is reachable from your workstation.
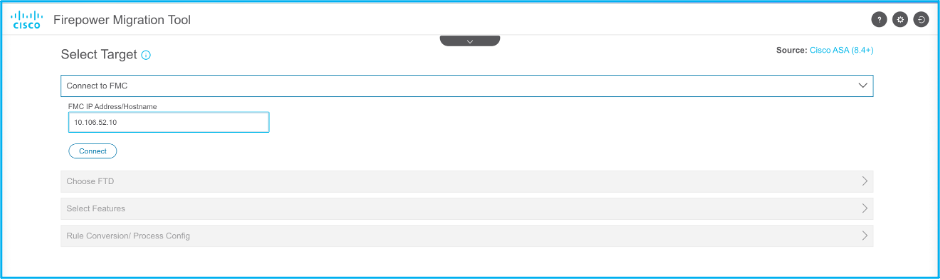
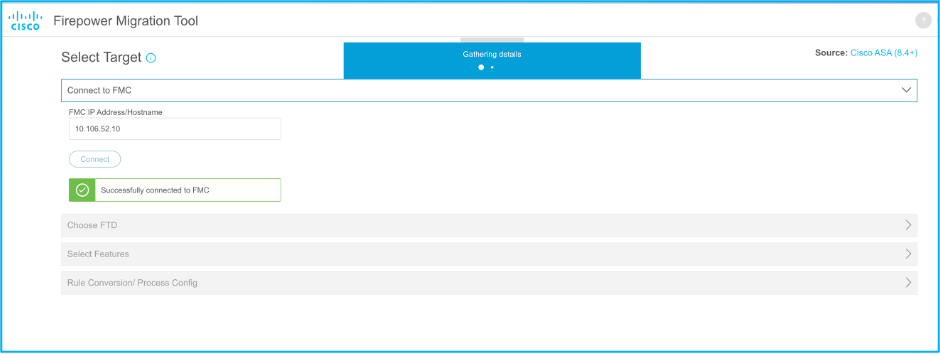
11. Once the FMC is connected, the managed FTDs under it are displayed.
12. Choose the FTD to which you want to perform the migration of the ASA configuration.
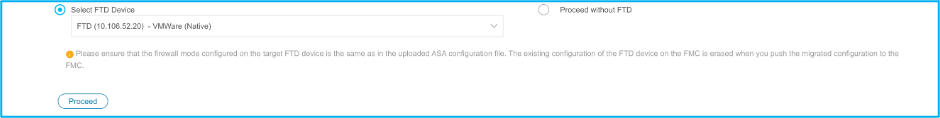
Note: It is recommended to choose the FTD device, else interfaces, routes, and site-to-site VPN configuration must be done manually.
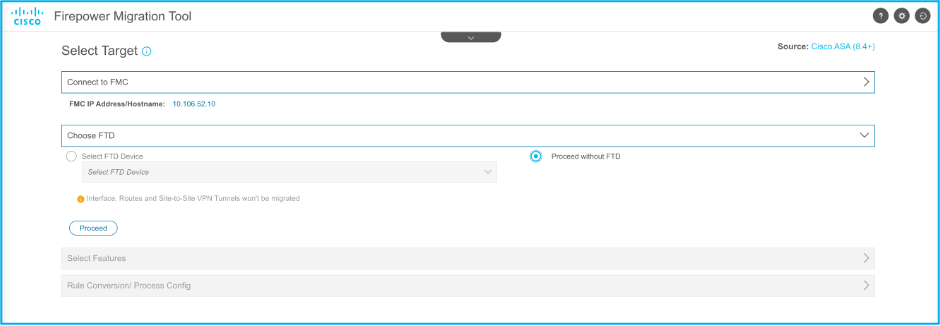
13. Choose the features required to be migrated as shown in the image:
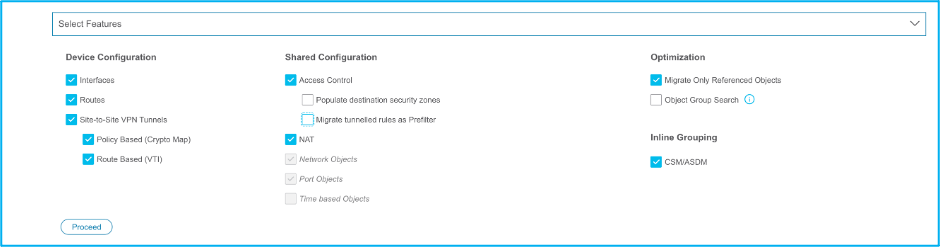
14. Choose Start Conversion in order to initiate the pre-migration which populates the elements pertaining to FTD configuration.
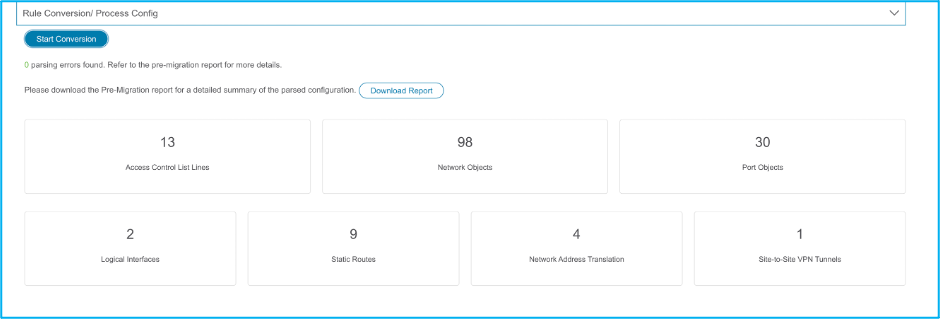
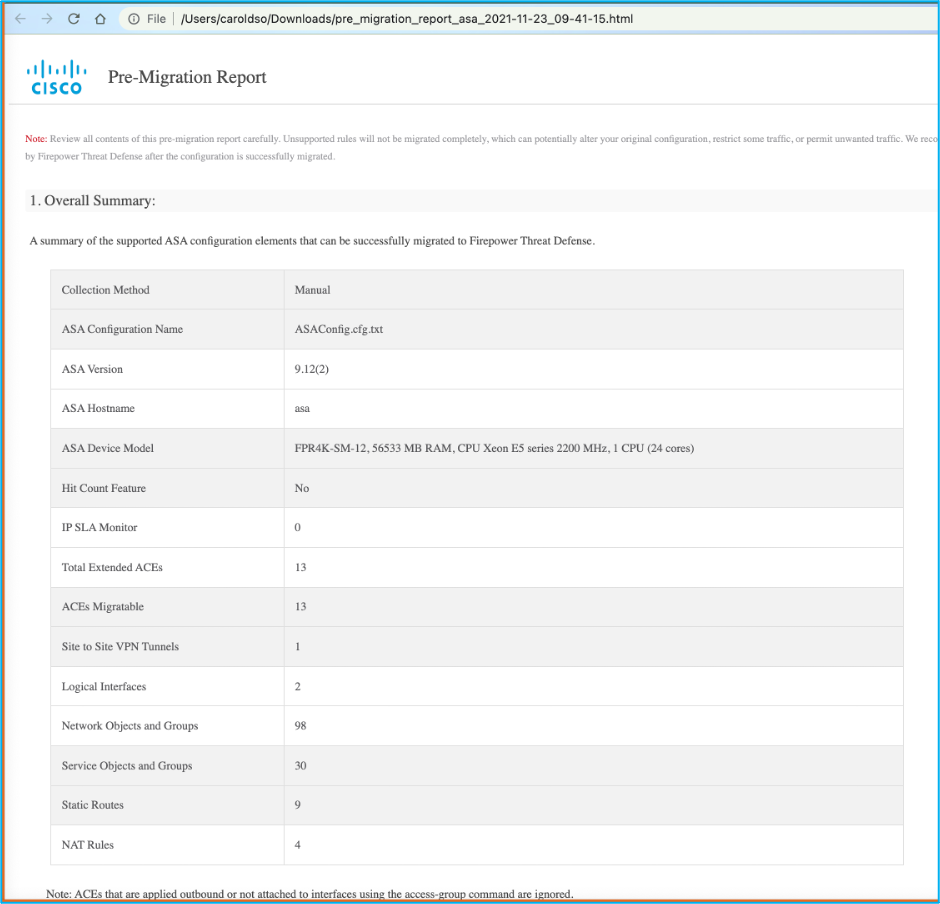
15. Click Download Report seen previously in order to view the Pre-Migration Report which is as shown in the image:
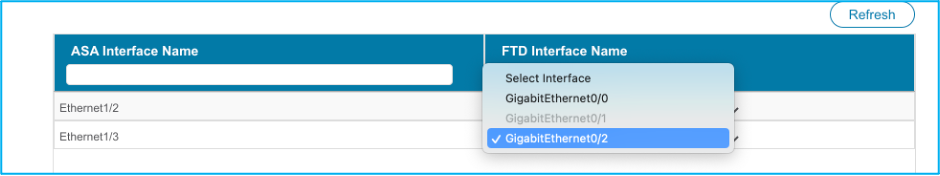
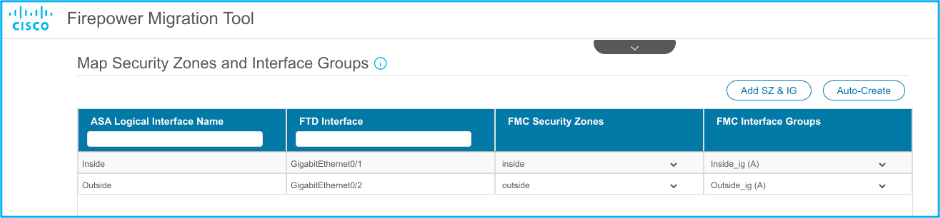
16. Map ASA interfaces to FTD interfaces as required as shown in the image:
17. Assign security zones and interface groups to the FTD interfaces.
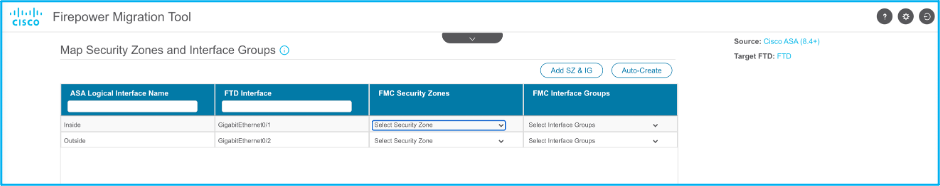
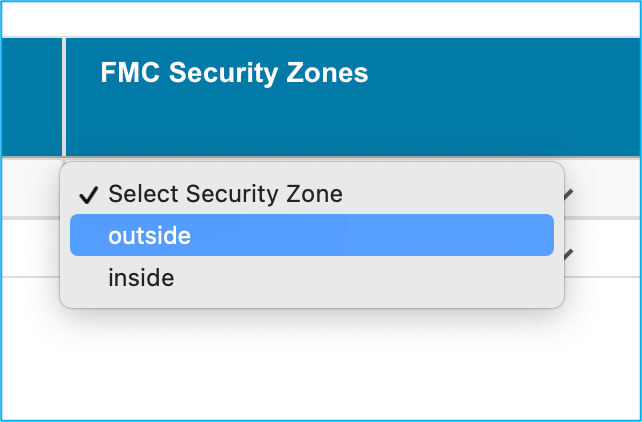
17.1. If the FMC has security zones and interface groups already created, you can choose them as needed:
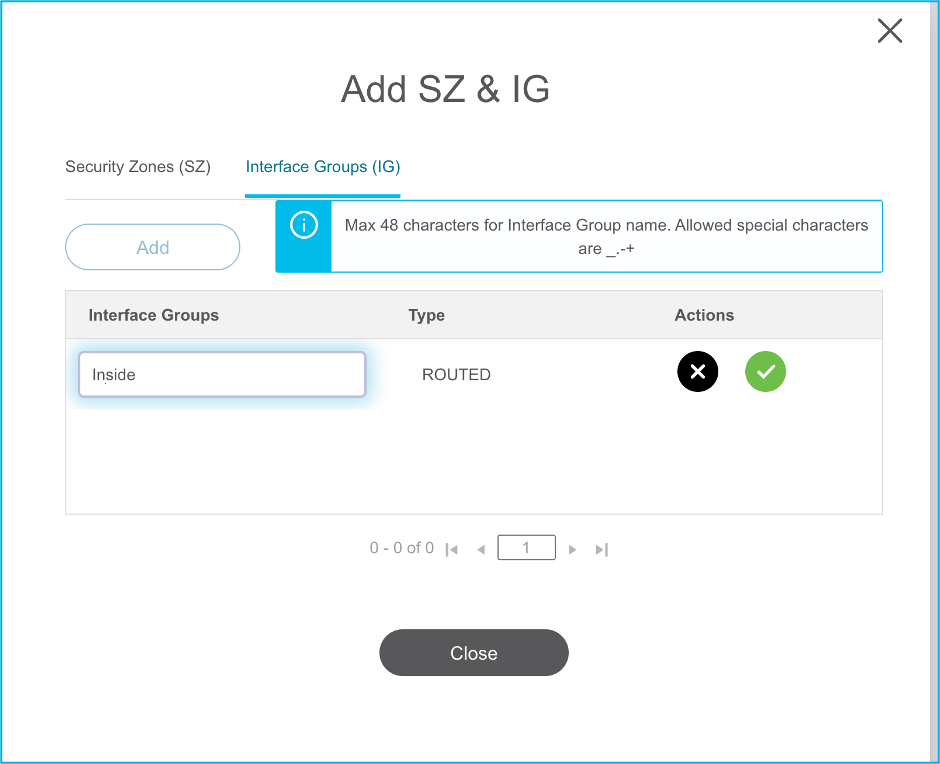
17.2. If there is a need to create security zones and an Interface group, click Add SZ & IG as shown in the image:
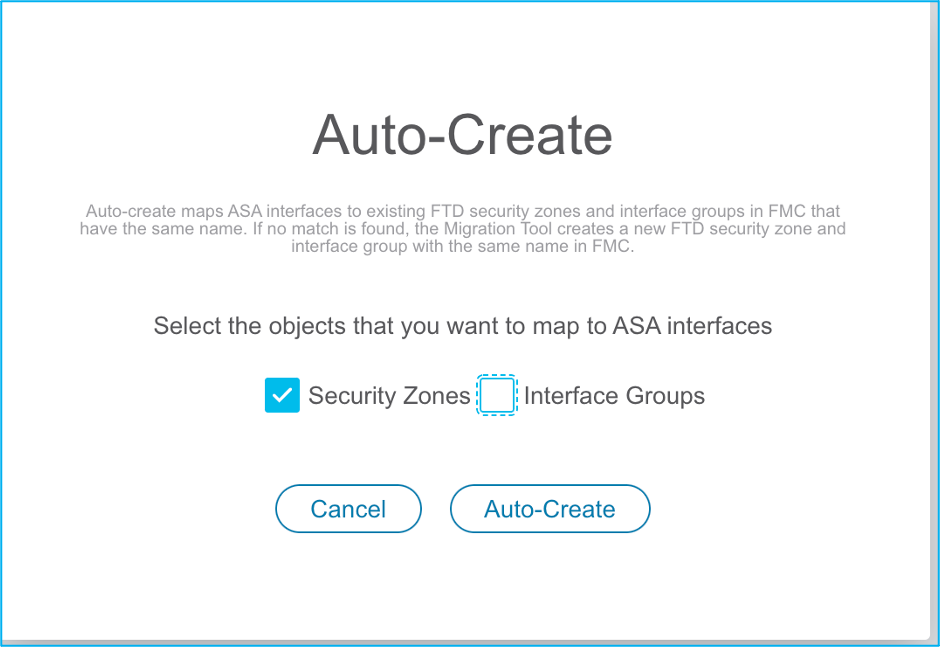
17.3. Otherwise, you can proceed with the option Auto-Create which creates security zones and interface groups with the name ASA logical interface_sz and ASA logical interface_ig respectively.
18. Review and validate each of the FTD elements created. Alerts are seen in red as shown in the image:
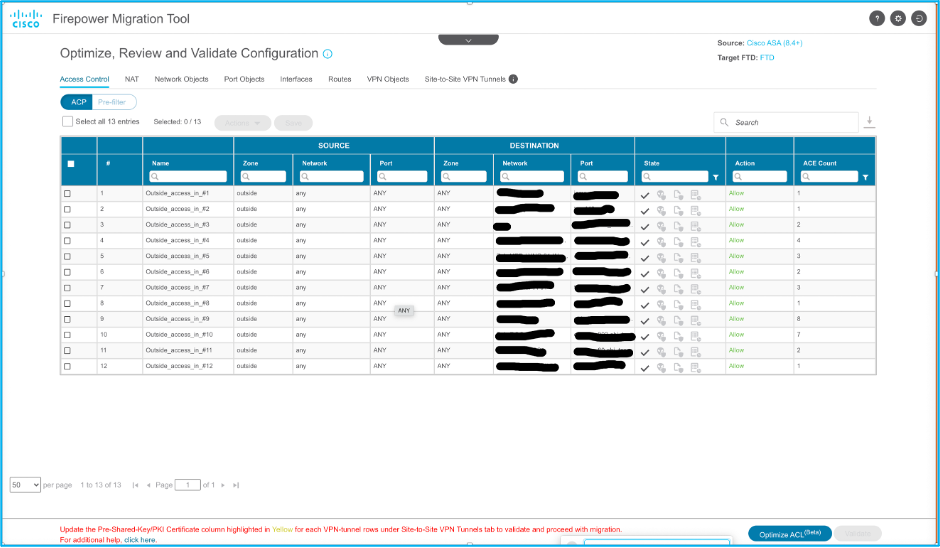
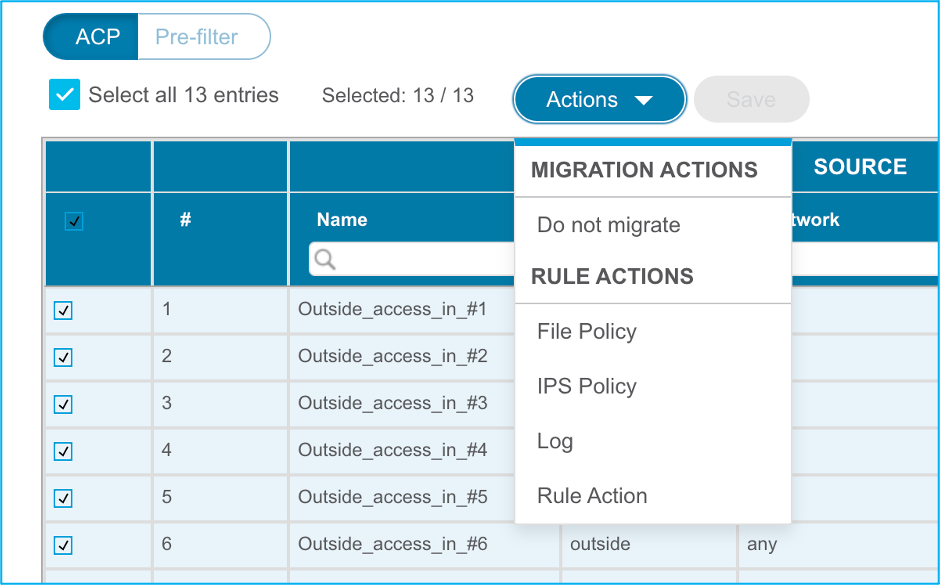
19. The migration actions can be chosen as shown in the image if you want to edit any rule. FTD features of adding files and IPS policy can be done at this step.
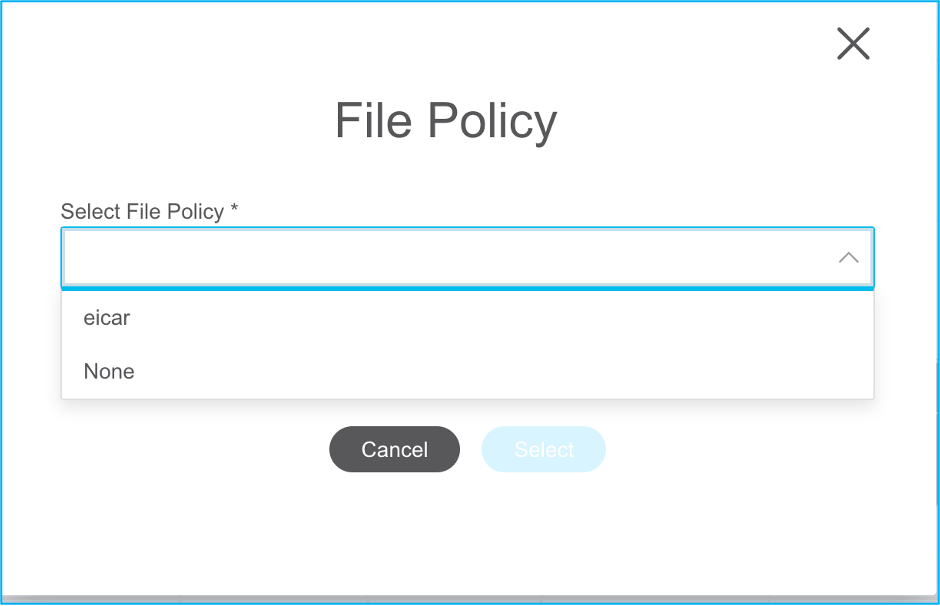
Note: If File Policies already exist in the FMC, they are populated as shown in the image. The same holds true for IPS policies along with the default policies.
Log configuration can be done for the required rules. Syslog server configuration existing on the FMC can be chosen at this stage.
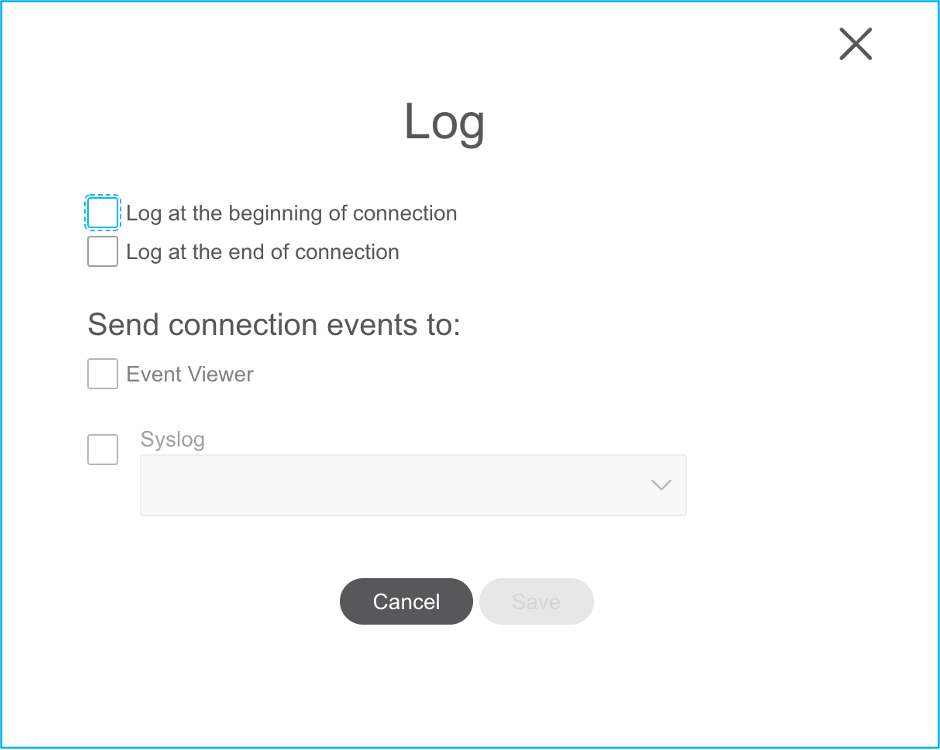
The rule actions chosen are highlighted accordingly for each rule.
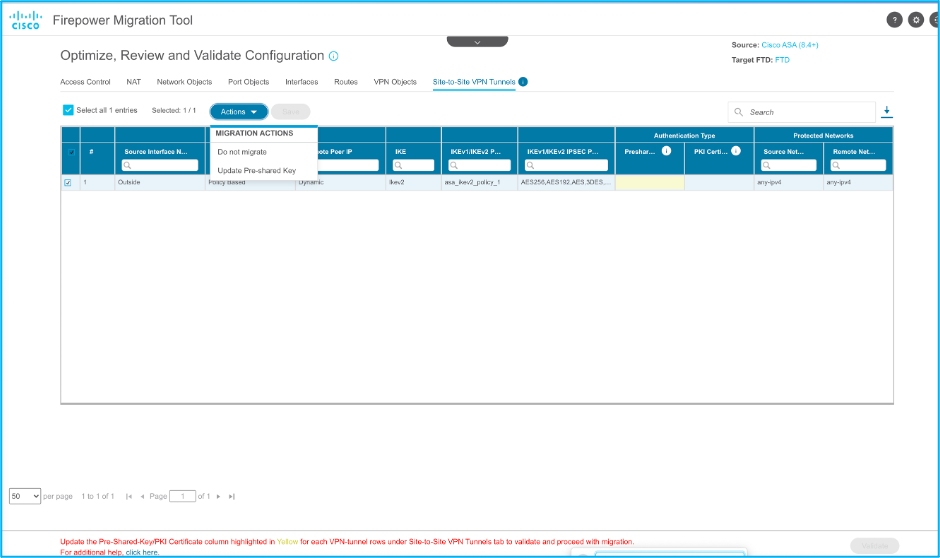
20. Similarly, Network Address Translation (NAT), Network Objects, Port Objects, Interfaces, Routes, VPN Objects, Site-to-Site VPN Tunnels, and other elements as per your configuration can be reviewed step by step.
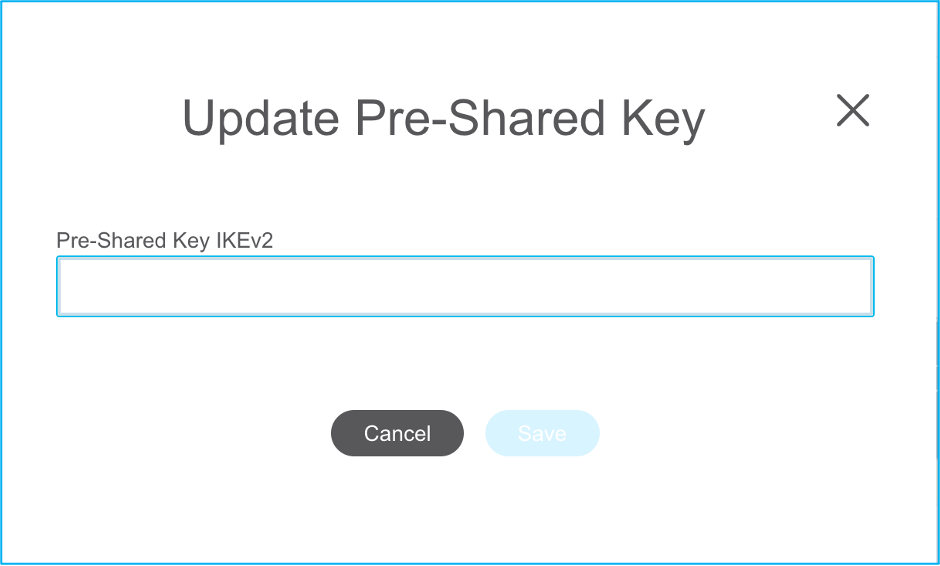
Note: Alert is notified as shown in the image in order to update the pre-shared key since it does not get copied in the ASA configuration file. Navigate to Actions > Update Pre-Shared Key in order to enter the value.
21. Finally, click the Validate icon at the bottom right of the screen as shown in the image:

22. Once the validation is successful, click Push Configuration as shown in the image:
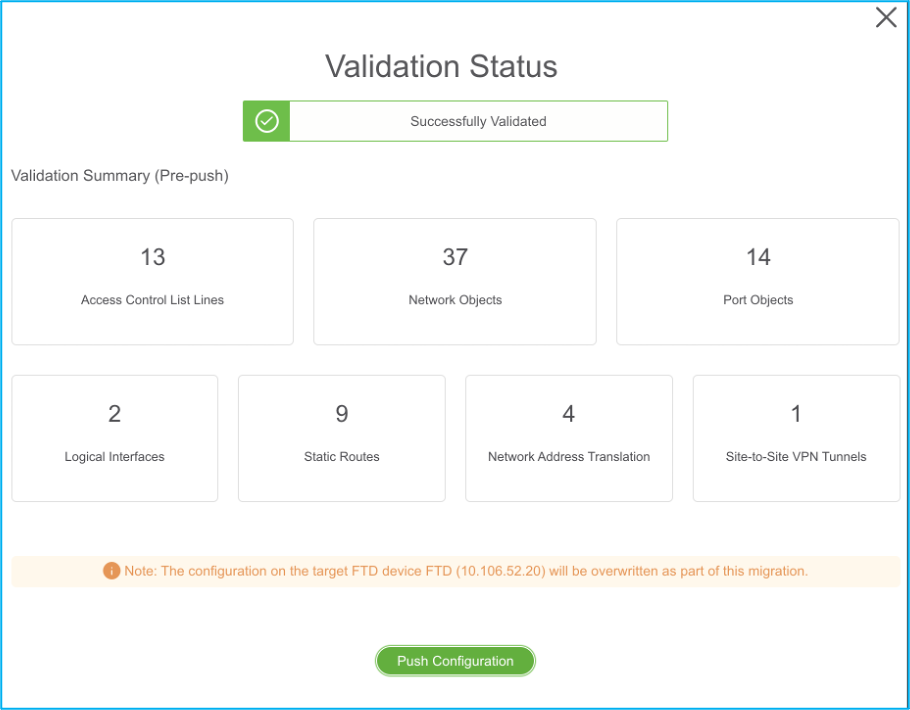
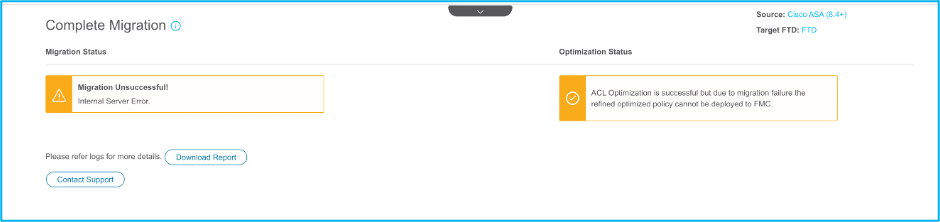
23. Once the migration is successful, the message that is displayed is shown in the image.
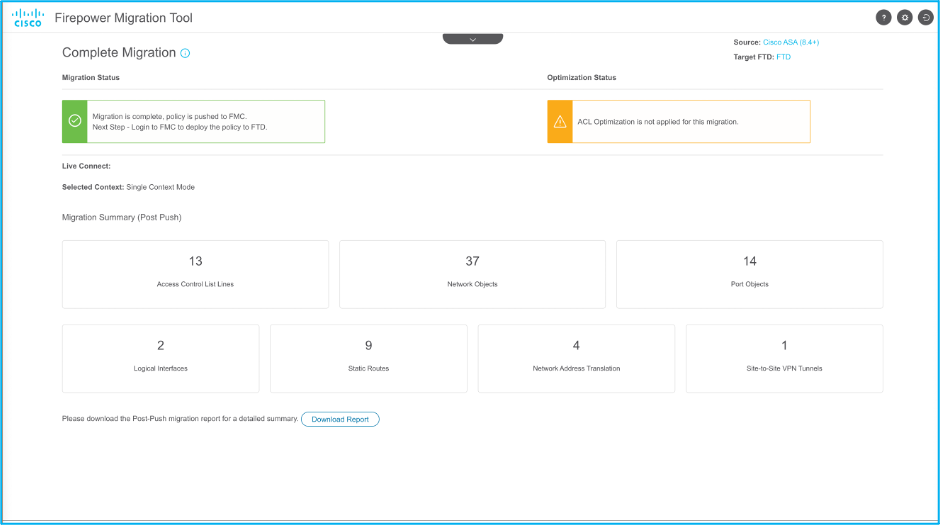
Note: If the migration is unsuccessful, click Download Report in order to view the Post-migration report.
Verify
Use this section in order to confirm that your configuration works properly.
Validation on the FMC:
- Navigate to
Policies > Access Control > Access Control Policy > Policy Assignment in order to confirm that the selected FTD is populated.
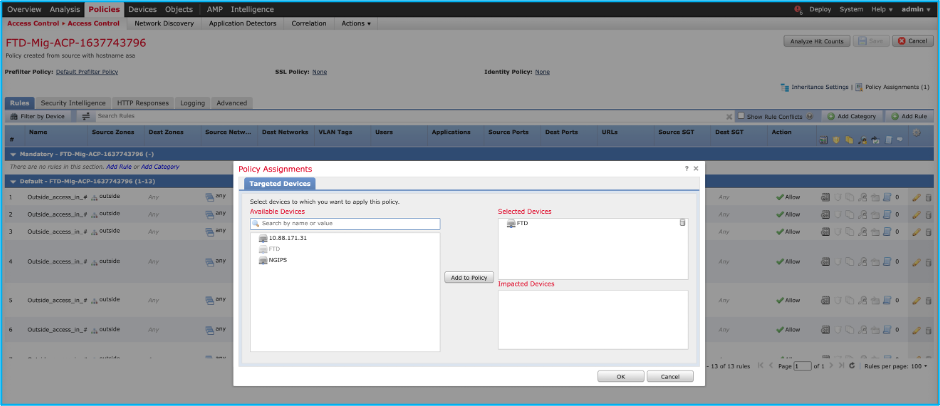
Note: The migration access control policy has a name with the prefix FTD-Mig-ACP. If no FTD was selected earlier, the FTD must be selected on the FMC.
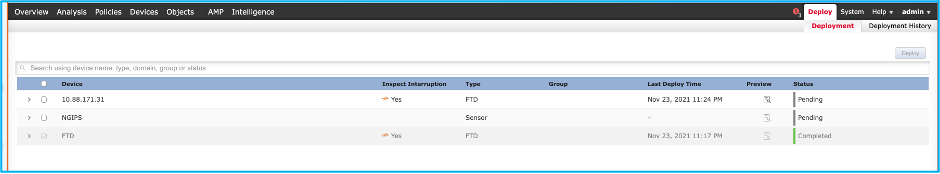
2. Push the policy to the FTD. Navigate to Deploy > Deployment > FTD Name > Deploy as shown in the image:
Known Bugs Related to the Firepower Migration Tool
- Cisco bug ID CSCwa56374 - FMT tool hangs on zone mapping page with error with high memory utilization
- Cisco bug ID CSCvz88730 - Interface push failure for FTD Port-channel Management interface type
- Cisco bug ID CSCvx21986 - Port-Channel migration to Target Platform - Virtual FTD is not supported
- Cisco bug ID CSCvy63003 - Migration Tool must disable the interface feature if FTD is already part of the Cluster
- Cisco bug ID CSCvx08199 - ACL needs to split when the application reference is more than 50
Related Information









































 Feedback
Feedback