Assign PPP Session and Idle Timeouts using RADIUS
Available Languages
Contents
Introduction
This configuration incorporates a Windows 95/98/NT client with a modem that dials over an analog line into an access server. The user's login is authenticated and authorized by the RADIUS server on the router's Ethernet segment. The Cisco Secure UNIX and Windows profiles in this document use the standard Internet Engineering Task Force (IETF) attributes for session and idle timeout. The values are in seconds.
This document does not provide step-by-step configuration instructions on the NAS for dialup access or AAA. For more information, refer to Configuring Basic AAA RADIUS for Dial-in Clients.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on these software and hardware versions:
-
Cisco IOS® Software Release 12.0(5.5)T
-
Cisco Secure UNIX version 2.2.3
-
Cisco Access Server 2511
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
For more information on document conventions, refer to Cisco Technical Tips Conventions.
Configure
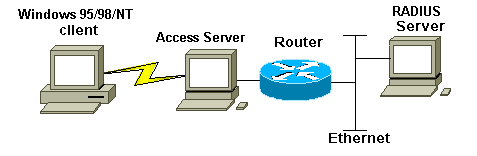
Network Diagram
This document uses the network setup shown in this diagram.
Configurations
This document uses the configurations shown here.
| Cisco Secure UNIX: RADIUS Profile |
|---|
# ./ViewProfile -p 9900 -u radtime
User Profile Information
user = radtime{
profile_id = 99
profile_cycle = 2
member = raj
radius=IETF {
check_items= {
2=cisco
}
reply_attributes= {
6=2
7=1
27=180
28=60
}
}
} |
Cisco Secure ACS for Windows
Complete these steps to configure Cisco Secure for Windows to pass idle timeouts to the NAS.
-
Click the User Setup button in the left bar.
-
Go to the user in question.
-
In the IETF RADIUS Attributes section, select Service-type (attribute 6) = Framed and Framed-Protocol (attribute 7)=PPP from the pull-down menu.
Note: You must also click the checkbox located next to the selected attributes: Service-Type and Framed-Protocol.
-
Click on the Group Setup button in the left bar. Select the Group the user belongs to and click Edit Settings.
-
In the section for Internet Engineering Task Force (IETF) RADIUS Attributes, click on the checkbox located next to Attribute 27 Session-Timeout and Attribute 28 Idle-Timeout. Specify the desired value for each timeout (in seconds) in the box next to each attribute.
| Router A |
|---|
Current configuration: ! version 12.0 service timestamps debug datetime msec service timestamps log uptime no service password-encryption ! hostname router_a ! no logging console !--- AAA configuration. The authorization statement is needed !--- to pass timeout values from ACS to the NAS. aaa new-model aaa authentication ppp default if-needed group radius aaa authorization network default group radius username john password doe enable password cisco ! ip subnet-zero no ip domain-lookup ! cns event-service server ! ! interface Ethernet0 ip address 171.68.201.53 255.255.255.0 no ip directed-broadcast no ip route-cache no ip mroute-cache no cdp enable ! interface Serial0 no ip address no ip directed-broadcast no ip mroute-cache shutdown no fair-queue no cdp enable ! interface Group-Async1 ip unnumbered Ethernet0 no ip directed-broadcast encapsulation ppp no ip route-cache no ip mroute-cache dialer in-band async mode dedicated peer default ip address pool default no cdp enable ppp authentication pap group-range 1 16 ! ip local pool default 10.1.1.1 ip classless ip route 0.0.0.0 0.0.0.0 171.68.201.1 ip route 171.68.0.0 255.255.0.0 171.68.201.1 ! !--- Specify the RADIUS server host and key. radius-server host 171.68.171.9 auth-port 1645 acct-port 1646 radius-server key ontop ! line con 0 exec-timeout 0 0 timeout login response 60 transport input pad v120 telnet rlogin udptn line 1 16 autoselect during-login autoselect ppp modem InOut transport input all speed 115200 line aux 0 timeout login response 60 line vty 0 4 exec-timeout 0 0 timeout login response 5 password cisco ! end |
Verify
This section provides information you can use to confirm your configuration is working properly.
Certain show commands are supported by the Output Interpreter Tool (registered customers only) , which allows you to view an analysis of show command output.
-
show dialer interface async 1—Displays information on the interfaces configured for dial-on-demand routing (DDR) dialer profiles.
-
show interfaces async 1—Displays serial interface information.
This show command output demonstrates how to verify that the session and idle timeouts were downloaded correctly. Cisco recommends that you run the command several times. This allows you to observe the counters decrementing.
router#show dialer interface async 1
Async1 - dialer type = IN-BAND ASYNC NO-PARITY
!--- Check to see that the idletime is 60 seconds for this interface. !--- This was configured in the RADIUS server.
Idle timer (60 sec), Fast idle timer (20 secs)
Wait for carrier (30 secs), Re-enable (15 secs)
Dialer state is data link layer up
Time until disconnect 40 secs (radtime)
Dial String Successes Failures Last DNIS Last status
router#show interface async 1
Async1 is up, line protocol is up
Hardware is Async Serial
Interface is unnumbered. Using address of Ethernet0 (171.68.201.53)
MTU 1500 bytes, BW 115 Kbit, DLY 100000 usec,
reliability 253/255, txload 1/255, rxload 1/255
Encapsulation PPP, loopback not set
Keepalive not set
DTR is pulsed for 5 seconds on reset
!--- The session (absolute) and idletime decreases.
Time to interface disconnect: absolute 00:02:41, idle 00:00:36
LCP Open
Open: IPCP
Last input 00:00:18, output 00:00:18, output hang never
Last clearing of "show interface" counters 3w0d
Input queue: 1/75/0 (size/max/drops); Total output drops: 0
Queueing strategy: weighted fair
Output queue: 0/1000/64/0 (size/max total/threshold/drops)
Conversations 0/1/16 (active/max active/max total)
Reserved Conversations 0/0 (allocated/max allocated)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
3543 packets input, 155629 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
46 input errors, 46 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
1903 packets output, 44205 bytes, 0 underruns
0 output errors, 0 collisions, 44 interface resets
0 output buffer failures, 0 output buffers swapped out
0 carrier transitions
router#show interface async 1
Async1 is up, line protocol is up
Hardware is Async Serial
Interface is unnumbered. Using address of Ethernet0 (171.68.201.53)
MTU 1500 bytes, BW 115 Kbit, DLY 100000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation PPP, loopback not set
Keepalive not set
DTR is pulsed for 5 seconds on reset
!--- The user is disconnected because the session !--- timeout (absolute) is reached.
Time to interface disconnect: absolute 00:00:00, idle 00:00:56
LCP Open
Open: IPCP
Last input 00:00:02, output 00:00:03, output hang never
Last clearing of "show interface" counters 3w0d
Input queue: 1/75/0 (size/max/drops); Total output drops: 0
Queueing strategy: weighted fair
Output queue: 0/1000/64/0 (size/max total/threshold/drops)
Conversations 0/1/16 (active/max active/max total)
Reserved Conversations 0/0 (allocated/max allocated)
5 minute input rate 0 bits/sec, 1 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
3674 packets input, 163005 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
46 input errors, 46 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
1984 packets output, 49146 bytes, 0 underruns
0 output errors, 0 collisions, 44 interface resets
0 output buffer failures, 0 output buffers swapped out
0 carrier transitions
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
Troubleshooting Commands
Note: Before issuing debug commands, refer to Important Information on Debug Commands.
-
debug ppp authentication—Displays authentication protocol messages. These messages include Challenge Authentication Protocol (CHAP) packet exchanges and Password Authentication Protocol (PAP) exchanges.
-
debug ppp negotiation—Displays Point-to-Point Protocol (PPP) packets transmitted during PPP startup, where PPP options are negotiated.
-
debug aaa authorization—Displays information on AAA/RADIUS authorization.
-
debug radius—Displays detailed debugging information associated with the RADIUS.
Router Debugs
This debug output shows the successful connection.
*Mar 22 21:11:02.797: AAA: parse name=tty1 idb type=10 tty=1 *Mar 22 21:11:02.801: AAA: name=tty1 flags=0x11 type=4 shelf=0 slot=0 adapter=0 port=1 channel=0 *Mar 22 21:11:02.801: AAA/MEMORY: create_user (0x57F3A8) user='' ruser='' port='tty1' rem_addr='async' authen_type=ASCII service=LOGIN priv=1 *Mar 22 21:11:02.833: AAA/MEMORY: free_user (0x57F3A8) user='' ruser='' port='tty1' rem_addr='async' authen_type=ASCII service=LOGIN priv=1 *Mar 22 21:11:02.909: As1 IPCP: Install route to 10.1.1.1 *Mar 22 21:11:04.869: As1 LCP: I CONFREQ [Closed] id 0 len 23 *Mar 22 21:11:04.873: As1 LCP: ACCM 0x00000000 (0x020600000000) *Mar 22 21:11:04.877: As1 LCP: MagicNumber 0x00005F22 (0x050600005F22) *Mar 22 21:11:04.877: As1 LCP: PFC (0x0702) *Mar 22 21:11:04.881: As1 LCP: ACFC (0x0802) *Mar 22 21:11:04.881: As1 LCP: Callback 6 (0x0D0306) *Mar 22 21:11:04.885: As1 LCP: Lower layer not up, Fast Starting *Mar 22 21:11:04.889: As1 PPP: Treating connection as a callin *Mar 22 21:11:04.889: As1 PPP: Phase is ESTABLISHING, Passive Open *Mar 22 21:11:04.893: As1 LCP: State is Listen *Mar 22 21:11:04.897: As1 AAA/AUTHOR/FSM: (0): LCP succeeds trivially *Mar 22 21:11:04.901: As1 LCP: O CONFREQ [Listen] id 104 len 24 *Mar 22 21:11:04.901: As1 LCP: ACCM 0x000A0000 (0x0206000A0000) *Mar 22 21:11:04.905: As1 LCP: AuthProto PAP (0x0304C023) *Mar 22 21:11:04.909: As1 LCP: MagicNumber 0x812C7E0C (0x0506812C7E0C) *Mar 22 21:11:04.913: As1 LCP: PFC (0x0702) *Mar 22 21:11:04.913: As1 LCP: ACFC (0x0802) *Mar 22 21:11:04.917: As1 LCP: O CONFREJ [Listen] id 0 len 7 *Mar 22 21:11:04.921: As1 LCP: Callback 6 (0x0D0306) 3w0d: %LINK-3-UPDOWN: Interface Async1, changed state to up *Mar 22 21:11:06.897: As1 LCP: TIMEout: State REQsent *Mar 22 21:11:06.901: As1 LCP: O CONFREQ [REQsent] id 105 len 24 *Mar 22 21:11:06.901: As1 LCP: ACCM 0x000A0000 (0x0206000A0000) *Mar 22 21:11:06.905: As1 LCP: AuthProto PAP (0x0304C023) *Mar 22 21:11:06.909: As1 LCP: MagicNumber 0x812C7E0C (0x0506812C7E0C) *Mar 22 21:11:06.909: As1 LCP: PFC (0x0702) *Mar 22 21:11:06.913: As1 LCP: ACFC (0x0802) *Mar 22 21:11:07.045: As1 LCP: I CONFACK [REQsent] id 105 len 24 *Mar 22 21:11:07.049: As1 LCP: ACCM 0x000A0000 (0x0206000A0000) *Mar 22 21:11:07.053: As1 LCP: AuthProto PAP (0x0304C023) *Mar 22 21:11:07.057: As1 LCP: MagicNumber 0x812C7E0C (0x0506812C7E0C) *Mar 22 21:11:07.057: As1 LCP: PFC (0x0702) *Mar 22 21:11:07.061: As1 LCP: ACFC (0x0802) *Mar 22 21:11:07.821: As1 LCP: I CONFREQ [ACKrcvd] id 0 len 23 *Mar 22 21:11:07.825: As1 LCP: ACCM 0x00000000 (0x020600000000) *Mar 22 21:11:07.829: As1 LCP: MagicNumber 0x00005F22 (0x050600005F22) *Mar 22 21:11:07.829: As1 LCP: PFC (0x0702) *Mar 22 21:11:07.833: As1 LCP: ACFC (0x0802) *Mar 22 21:11:07.833: As1 LCP: Callback 6 (0x0D0306) *Mar 22 21:11:07.837: As1 LCP: O CONFREJ [ACKrcvd] id 0 len 7 *Mar 22 21:11:07.841: As1 LCP: Callback 6 (0x0D0306) *Mar 22 21:11:07.957: As1 LCP: I CONFREQ [ACKrcvd] id 1 len 20 *Mar 22 21:11:07.961: As1 LCP: ACCM 0x00000000 (0x020600000000) *Mar 22 21:11:07.961: As1 LCP: MagicNumber 0x00005F22 (0x050600005F22) *Mar 22 21:11:07.965: As1 LCP: PFC (0x0702) *Mar 22 21:11:07.969: As1 LCP: ACFC (0x0802) *Mar 22 21:11:07.969: As1 LCP: O CONFACK [ACKrcvd] id 1 len 20 *Mar 22 21:11:07.973: As1 LCP: ACCM 0x00000000 (0x020600000000) *Mar 22 21:11:07.977: As1 LCP: MagicNumber 0x00005F22 (0x050600005F22) *Mar 22 21:11:07.977: As1 LCP: PFC (0x0702) *Mar 22 21:11:07.981: As1 LCP: ACFC (0x0802) *Mar 22 21:11:07.985: As1 LCP: State is Open *Mar 22 21:11:07.985: As1 PPP: Phase is AUTHENTICATING, by this end *Mar 22 21:11:08.245: As1 LCP: I IDENTIFY [Open] id 2 len 18 magic 0x00005F22 MSRASV4.00 *Mar 22 21:11:08.249: As1 LCP: I IDENTIFY [Open] id 3 len 31 magic 0x00005F22 MSRAS-1-RAJESH-SECURITY *Mar 22 21:11:08.253: As1 PAP: I AUTH-REQ id 30 len 18 from "radtime" *Mar 22 21:11:08.265: As1 PAP: Authenticating peer radtime *Mar 22 21:11:08.269: AAA: parse name=Async1 idb type=10 tty=1 *Mar 22 21:11:08.273: AAA: name=Async1 flags=0x11 type=4 shelf=0 slot=0 adapter=0 port=1 channel=0 *Mar 22 21:11:08.273: AAA/MEMORY: create_user (0x57F3A8) user='radtime' ruser='' port='Async1' rem_addr='async' authen_type=PAP service=PPP priv=1 *Mar 22 21:11:08.281: RADIUS: ustruct sharecount=1 *Mar 22 21:11:08.285: RADIUS: Initial Transmit Async1 id 109 172.16.171.9:1645, Access-Request, len 77 *Mar 22 21:11:08.289: Attribute 4 6 AB44C935 *Mar 22 21:11:08.293: Attribute 5 6 00000001 *Mar 22 21:11:08.293: Attribute 61 6 00000000 *Mar 22 21:11:08.297: Attribute 1 9 72616474 *Mar 22 21:11:08.297: Attribute 2 18 486188E4 *Mar 22 21:11:08.301: Attribute 6 6 00000002 *Mar 22 21:11:08.301: Attribute 7 6 00000001 *Mar 22 21:11:08.329: RADIUS: Received from id 109 172.16.171.9:1645, Access-Accept, len 44 *Mar 22 21:11:08.333: Attribute 6 6 00000002 *Mar 22 21:11:08.333: Attribute 7 6 00000001 *Mar 22 21:11:08.337: Attribute 27 6 000000B4 *Mar 22 21:11:08.337: Attribute 28 6 0000003C
The attribute value pairs (AVPs) from the debug radius command need to be decoded. This helps you to better understand the transaction between the NAS and the RADIUS server.
Note: As of Cisco IOS Software Release 12.2(11)T, the output of the debug radius command is already decoded. It does NOT require the use of the Output Interpreter Tool (registered customers only) to decode the output. Refer to RADIUS Debug Enhancements for more information.
The Output Interpreter Tool (registered customers only) allows you to receive an analysis of the debug radius command output.
The output in italics is the result obtained from the Output Interpreter Tool (registered customers only) :
Access-Request 172.16.171.9:1645 id 109 Attribute Type 4: NAS-IP-Address is 171.68.201.53 Attribute Type 5: NAS-Port is 1 Attribute Type 61: NAS-Port-Type is Asynchronous Attribute Type 1: User-Name is radt Attribute Type 2: User-Password is (encoded) Attribute Type 6: Service-Type is Framed Attribute Type 7: Framed-Protocol is PPP Access-Accept 172.16.171.9:1645 id 109 Attribute Type 6: Service-Type is Framed Attribute Type 7: Framed-Protocol is PPP Attribute Type 27: Session-Timeout is 180 seconds Attribute Type 28: Idle-Timeout is 60 seconds
Note that the session timeout is 180 seconds and idle timeout is 60 seconds.
*Mar 22 21:11:08.345: RADIUS: saved authorization data for user 57F3A8 at 5AB9A4 *Mar 22 21:11:08.349: As1 AAA/AUTHOR/LCP: Authorize LCP *Mar 22 21:11:08.353: As1 AAA/AUTHOR/LCP (2107569326): Port='Async1' list='' service=NET *Mar 22 21:11:08.353: AAA/AUTHOR/LCP: As1 (2107569326) user='radtime' *Mar 22 21:11:08.357: As1 AAA/AUTHOR/LCP (2107569326): send AV service=ppp *Mar 22 21:11:08.357: As1 AAA/AUTHOR/LCP (2107569326): send AV protocol=lcp *Mar 22 21:11:08.361: As1 AAA/AUTHOR/LCP (2107569326): found list "default" *Mar 22 21:11:08.365: As1 AAA/AUTHOR/LCP (2107569326): Method=radius (radius) *Mar 22 21:11:08.369: As1 AAA/AUTHOR (2107569326): Post authorization status = PASS_REPL *Mar 22 21:11:08.369: As1 AAA/AUTHOR/LCP: Processing AV service=ppp !--- The session timeout and idle timeouts are applied to the interface. *Mar 22 21:11:08.373: As1 AAA/AUTHOR/LCP: Processing AV timeout=180 *Mar 22 21:11:08.633: As1 AAA/AUTHOR/LCP: Processing AV idletime=60 *Mar 22 21:11:09.049: As1 PAP: O AUTH-ACK id 30 len 5 *Mar 22 21:11:09.053: As1 PPP: Phase is UP *Mar 22 21:11:09.057: As1 AAA/AUTHOR/FSM: (0): Can we start IPCP? *Mar 22 21:11:09.061: As1 AAA/AUTHOR/FSM (1853995855): Port='Async1' list='' service=NET *Mar 22 21:11:09.061: AAA/AUTHOR/FSM: As1 (1853995855) user='radtime' *Mar 22 21:11:09.065: As1 AAA/AUTHOR/FSM (1853995855): send AV service=ppp *Mar 22 21:11:09.065: As1 AAA/AUTHOR/FSM (1853995855): send AV protocol=ip *Mar 22 21:11:09.069: As1 AAA/AUTHOR/FSM (1853995855): found list "default" *Mar 22 21:11:09.073: As1 AAA/AUTHOR/FSM (1853995855): Method=radius (radius) *Mar 22 21:11:09.077: As1 AAA/AUTHOR (1853995855): Post authorization status = PASS_REPL *Mar 22 21:11:09.077: As1 AAA/AUTHOR/FSM: We can start IPCP *Mar 22 21:11:09.085: As1 IPCP: O CONFREQ [Closed] id 19 len 10 *Mar 22 21:11:09.089: As1 IPCP: Address 171.68.201.53 (0x0306AB44C935) *Mar 22 21:11:09.177: As1 CCP: I CONFREQ [Not negotiated] id 4 len 10 *Mar 22 21:11:09.181: As1 CCP: MS-PPC supported bits 0x00000001 (0x120600000001) *Mar 22 21:11:09.185: As1 LCP: O PROTREJ [Open] id 106 len 16 protocol CCP (0x80FD0104000A120600000001) *Mar 22 21:11:09.189: As1 IPCP: I CONFREQ [REQsent] id 5 len 40 *Mar 22 21:11:09.193: As1 IPCP: CompressType VJ 15 slots CompressSlotID (0x0206002D0F01) *Mar 22 21:11:09.197: As1 IPCP: Address 0.0.0.0 (0x030600000000) *Mar 22 21:11:09.201: As1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000) *Mar 22 21:11:09.205: As1 IPCP: PrimaryWINS 0.0.0.0 (0x820600000000) *Mar 22 21:11:09.209: As1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000) *Mar 22 21:11:09.213: As1 IPCP: SecondaryWINS 0.0.0.0 (0x840600000000) *Mar 22 21:11:09.213: As1 AAA/AUTHOR/IPCP: Start. Her address 0.0.0.0, we want 10.1.1.1 *Mar 22 21:11:09.217: As1 AAA/AUTHOR/IPCP: Processing AV service=ppp *Mar 22 21:11:09.221: As1 AAA/AUTHOR/IPCP: Authorization succeeded *Mar 22 21:11:09.221: As1 AAA/AUTHOR/IPCP: Done. Her address 0.0.0.0, we want 10.1.1.1 *Mar 22 21:11:09.229: As1 IPCP: O CONFREJ [REQsent] id 5 len 34 *Mar 22 21:11:09.229: As1 IPCP: CompressType VJ 15 slots CompressSlotID (0x0206002D0F01) *Mar 22 21:11:09.233: As1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000) *Mar 22 21:11:09.237: As1 IPCP: PrimaryWINS 0.0.0.0 (0x820600000000) *Mar 22 21:11:09.241: As1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000) *Mar 22 21:11:09.245: As1 IPCP: SecondaryWINS 0.0.0.0 (0x840600000000) *Mar 22 21:11:09.249: As1 IPCP: I CONFACK [REQsent] id 19 len 10 *Mar 22 21:11:09.253: As1 IPCP: Address 171.68.201.53 (0x0306AB44C935) *Mar 22 21:11:09.673: As1 IPCP: I CONFREQ [ACKrcvd] id 6 len 10 *Mar 22 21:11:09.677: As1 IPCP: Address 0.0.0.0 (0x030600000000) *Mar 22 21:11:09.681: As1 AAA/AUTHOR/IPCP: Start. Her address 0.0.0.0, we want 10.1.1.1 *Mar 22 21:11:09.685: As1 AAA/AUTHOR/IPCP: Processing AV service=ppp *Mar 22 21:11:09.685: As1 AAA/AUTHOR/IPCP: Authorization succeeded *Mar 22 21:11:09.689: As1 AAA/AUTHOR/IPCP: Done. Her address 0.0.0.0, we want 10.1.1.1 *Mar 22 21:11:09.693: As1 IPCP: O CONFNAK [ACKrcvd] id 6 len 10 *Mar 22 21:11:09.697: As1 IPCP: Address 10.1.1.1 (0x03060A010101) *Mar 22 21:11:09.813: As1 IPCP: I CONFREQ [ACKrcvd] id 7 len 10 *Mar 22 21:11:09.817: As1 IPCP: Address 10.1.1.1 (0x03060A010101) *Mar 22 21:11:09.821: As1 AAA/AUTHOR/IPCP: Start. Her address 10.1.1.1, we want 10.1.1.1 *Mar 22 21:11:09.825: As1 AAA/AUTHOR/IPCP (1344088998): Port='Async1' list='' service=NET *Mar 22 21:11:09.829: AAA/AUTHOR/IPCP: As1 (1344088998) user='radtime' *Mar 22 21:11:09.833: As1 AAA/AUTHOR/IPCP (1344088998): send AV service=ppp *Mar 22 21:11:09.833: As1 AAA/AUTHOR/IPCP (1344088998): send AV protocol=ip *Mar 22 21:11:09.837: As1 AAA/AUTHOR/IPCP (1344088998): send AV addr*10.1.1.1 *Mar 22 21:11:09.837: As1 AAA/AUTHOR/IPCP (1344088998): found list "default" *Mar 22 21:11:09.841: As1 AAA/AUTHOR/IPCP (1344088998): Method=radius (radius) *Mar 22 21:11:09.845: As1 AAA/AUTHOR (1344088998): Post authorization status = PASS_REPL *Mar 22 21:11:09.849: As1 AAA/AUTHOR/IPCP: Reject 10.1.1.1, using 10.1.1.1 *Mar 22 21:11:09.853: As1 AAA/AUTHOR/IPCP: Processing AV service=ppp *Mar 22 21:11:09.857: As1 AAA/AUTHOR/IPCP: Processing AV addr*10.1.1.1 *Mar 22 21:11:09.857: As1 AAA/AUTHOR/IPCP: Authorization succeeded *Mar 22 21:11:09.861: As1 AAA/AUTHOR/IPCP: Done. Her address 10.1.1.1, we want 10.1.1.1 *Mar 22 21:11:09.865: As1 IPCP: O CONFACK [ACKrcvd] id 7 len 10 *Mar 22 21:11:09.869: As1 IPCP: Address 10.1.1.1 (0x03060A010101) *Mar 22 21:11:09.873: As1 IPCP: State is Open *Mar 22 21:11:09.885: As1 IPCP: Install route to 10.1.1.1 3w0d: %LINEPROTO-5-UPDOWN: Line protocol on Interface Async1, changed state to up
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
26-Feb-2008 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback