Configuring the VPN Client 3.x to Get a Digital Certificate
Available Languages
Contents
Introduction
This document demonstrates how to configure the Cisco VPN Client 3.x to get a digital certificate.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on a PC that runs Cisco VPN Client 3.x.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Configure the VPN Client
Complete these steps to configure the VPN Client.
-
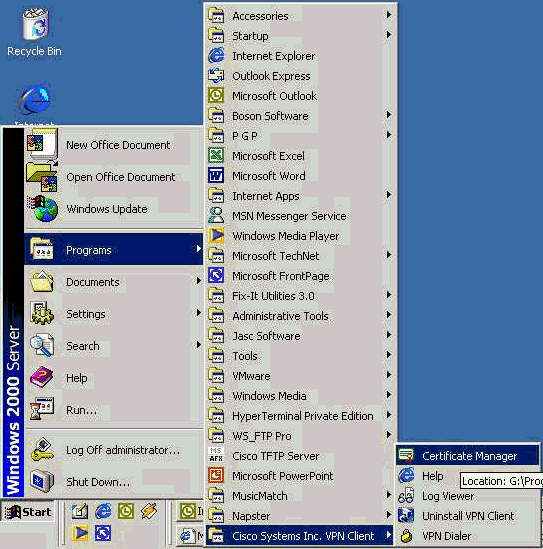
Select Start > Programs > Cisco Systems Inc. VPN client > Certificate Manager to launch the VPN Client Certificate Manager.
-
Select the Personal Certificates tab and click New.
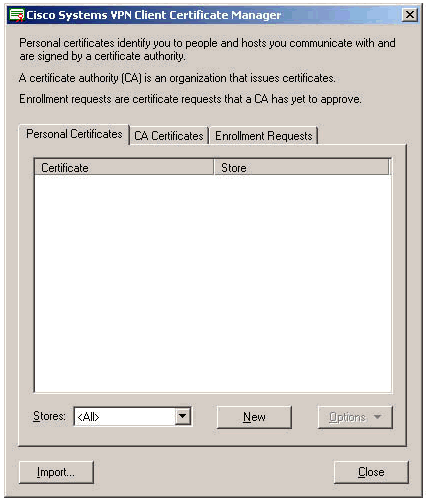
Note: Machine certificates to authenticate users for VPN connections cannot be done with IPsec.
-
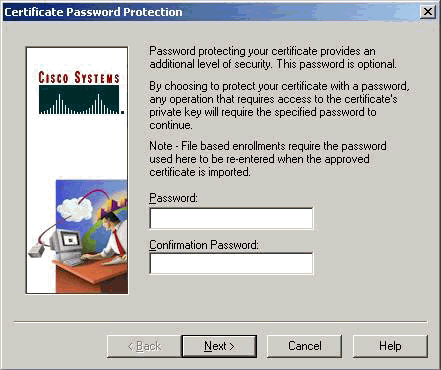
When the VPN Client prompts you for a password, specify a password to protect the certificate. Any operation that requires access to the certificate's private key requires the specified password to continue.
-
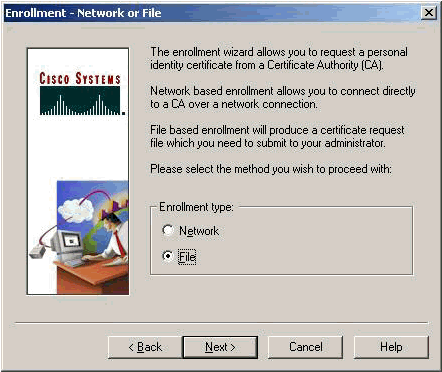
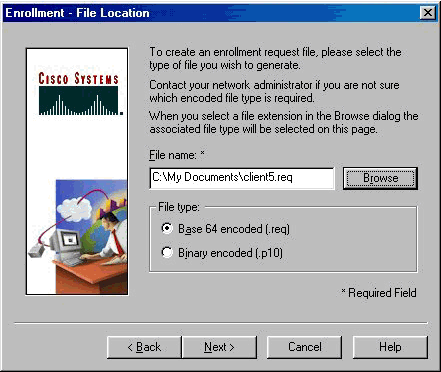
Select File to request a certificate using PKCS #10 format on the Enrollment page. Then click Next.
-
Click Browse, and specify a filename for the certificate request file. For the file type, select PEM Encoded Request File (*.req) and click Save.
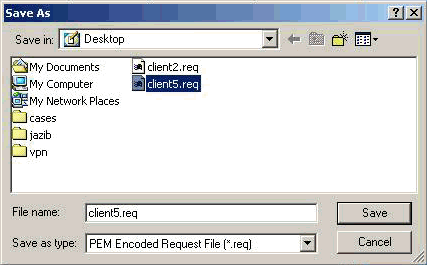
-
Click Next on the VPN Client Enrollment page.
-
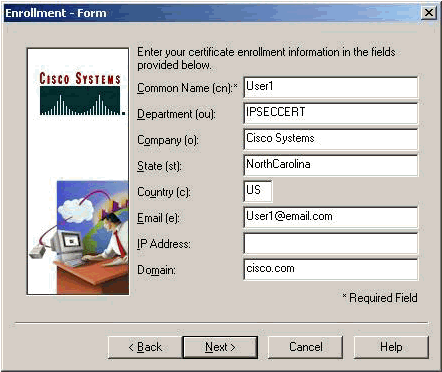
Fill out the fields on the Enrollment Form.
This example shows the fields:
-
Common Name = User1
-
Department = IPSECCERT (This should match the organizational unit (OU) and the group name on the VPN 3000 Concentrator.)
-
Company = Cisco Systems
-
State = NorthCarolina
-
Country = US
-
Email = User1@email.com
-
IP Address = (optional; used to specify the IP address on the certificate request )
-
Domain = cisco.com
Click Next when you are done.
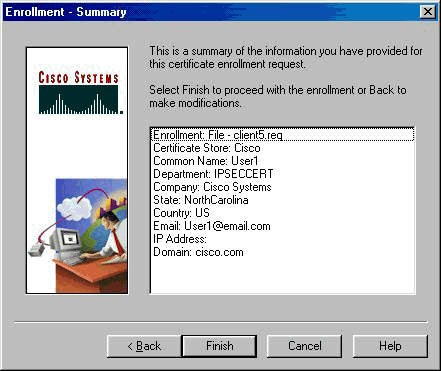
-
-
Click Finish to proceed with the enrollment.
-
Select the Enrollment Requests tab to check the request on the VPN Client Certificate Manager.
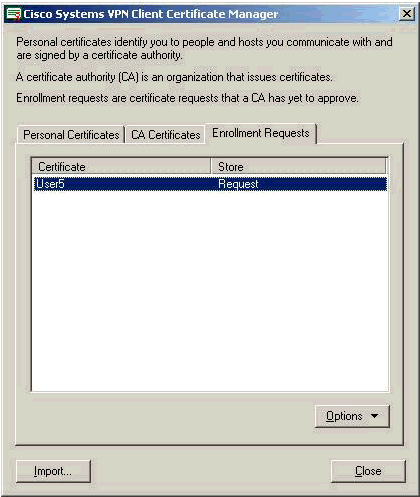
-
Bring up the Certification Authority (CA) server and the VPN Client interfaces concurrently to submit the request.
-
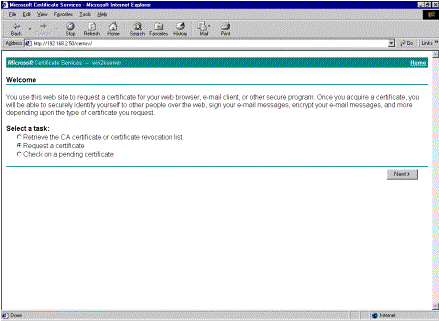
Select Request a certificate and click Next on the CA server.
-
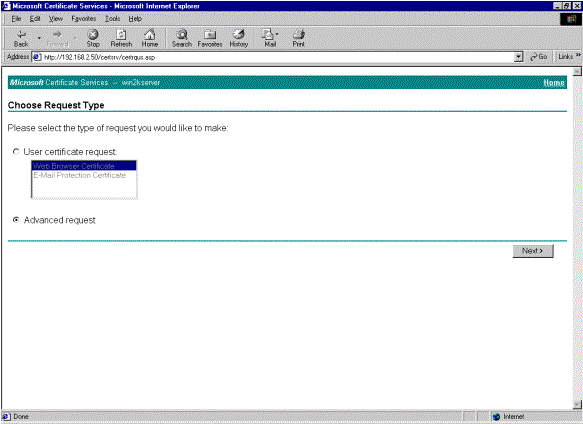
Select Advanced request for the type of request and click Next.
-
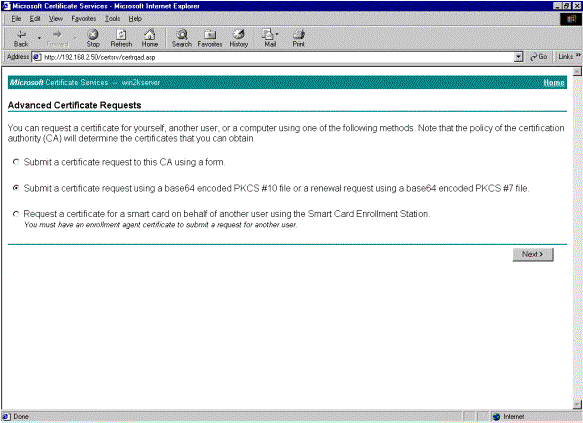
Select Submit a certificate request using a base64 encoded PKCS #10 file or a renewal request using a base64 encoded PKCS #7 file under Advanced Certificate Requests, and then click Next.
-
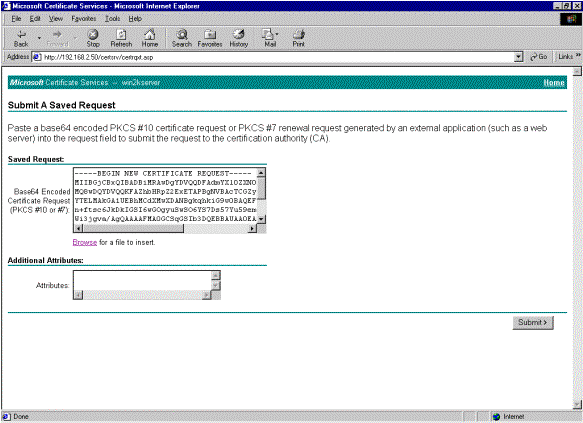
Highlight the VPN Client request file, and paste it to the CA server under Saved Request. Then click Submit.
-
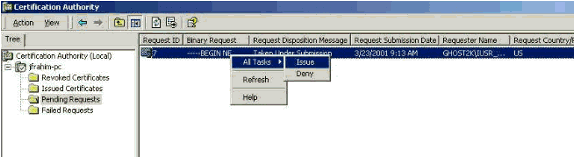
On the CA server, issue the identity certificate for the VPN Client request.
-
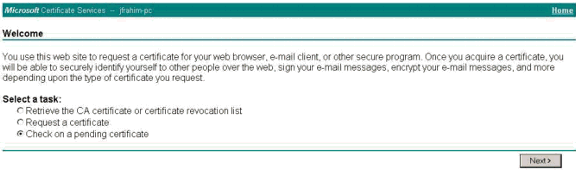
Download the root and identity certificates to the VPN Client. On the CA server, select Check on a pending certificate, and then click Next.
-
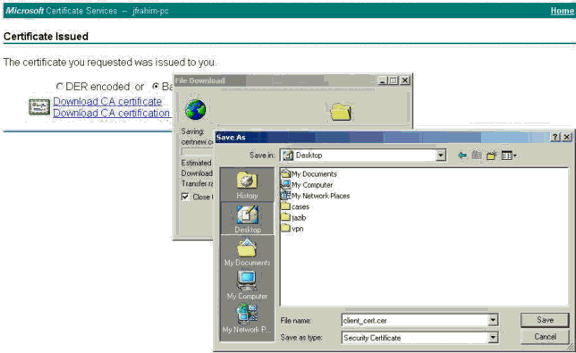
Select Base 64 encoded. Then click Download CA certificate on the CA server.
-
Select a file to download from the Retrieve the CA Certificate or Certificate Revocation List page to get the root certificate on the CA server. Then click Next.
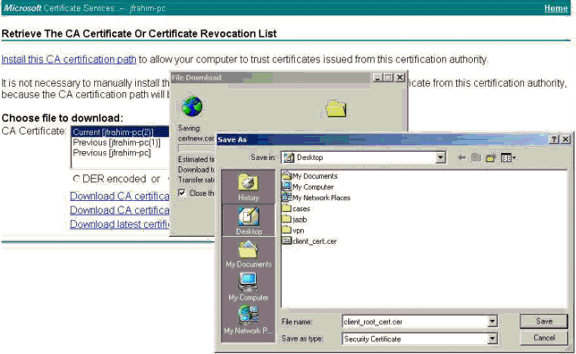
-
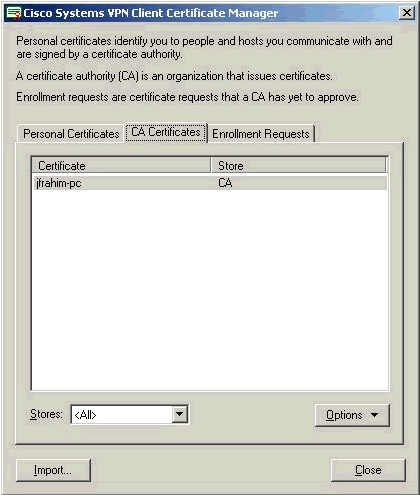
Select Certificate Manager > CA Certificate > Import on the VPN Client , and then select the root CA file to install the root and identity certificates.
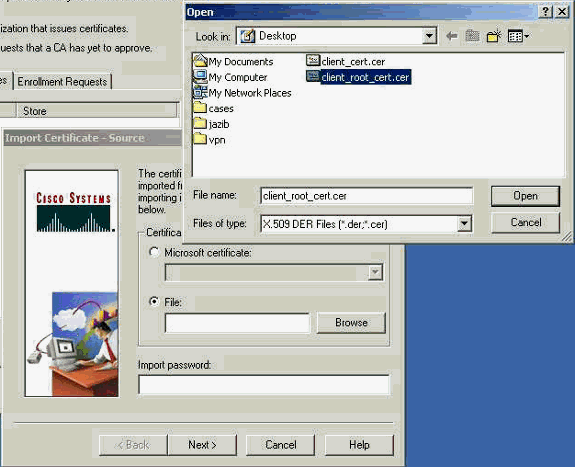
-
Select Certificate Manager > Personal Certificates > Import, and choose the identity certificate file.
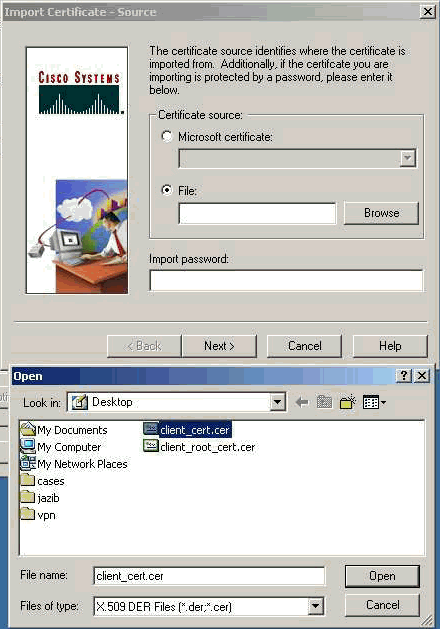
-
Ensure that the identity certificate appears under the Personal Certificates tab.
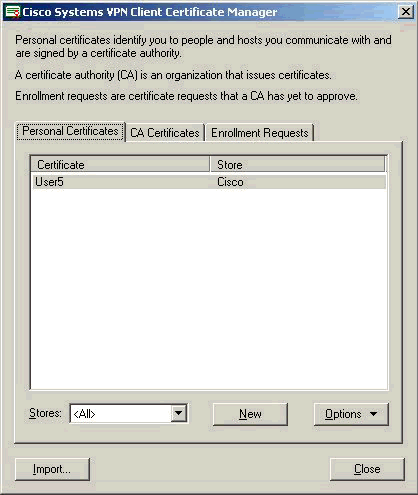
-
Ensure that the root certificate appears under the CA Certificates tab.
Verify
There is currently no verification procedure available for this configuration.
Troubleshoot
When you attempt to enroll with the Microsoft CA Server, it can generate this error message.
Initiating online request Generating key pair Generating self-signed Certificate Initiating online request Received a response from the CA Your certificate request was denied
If you receive this error message, refer to the Microsoft CA logs for details, or refer to these resources for more information.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
19-Jan-2006 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)





















 Feedback
Feedback