Configuring DN-Based Crypto Maps for VPN Device Access Control
Available Languages
Contents
Introduction
This document describes how to configure Distinguished Name (DN)-based crypto maps to provide access control so that a VPN device can establish VPN tunnels with a Cisco IOS® router. In this document's example, Rivest, Shamir, and Adelman (RSA) signature is the method for the IKE authentication. In addition to standard certificate validation, DN-based crypto maps try to match the peer's ISAKMP identity with certain fields in its certificates, such as the X.500 distinguished name or the fully qualified domain name (FQDN).
Prerequisites
Requirements
This feature was first introduced in Cisco IOS Software Release 12.2(4)T. You must this release or later for this configuration.
The Cisco IOS Software Release 12.3(5) was also tested. However, the DN based crypto maps failed due to Cisco bug ID CSCed45783 (registered customers only) .
Components Used
The information in this document is based on these software and hardware versions:
-
Cisco 7200 routers
-
Cisco IOS Software Release 12.2(4)T1 c7200-ik8o3s-mz.122-4.T1
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
For more information on document conventions, refer to Cisco Technical Tips Conventions.
Background Information
Previously, during IKE authentication using the RSA signature method, and after certification validation and optional certificate revocation list (CRL) checking, Cisco IOS continued the IKE Quick Mode negotiation. It did not provide a method to prevent the remote VPN devices from communicating with any encrypted interfaces, other than restrictions on the encrypting peer's IP address.
Now with DN-based crypto map, Cisco IOS can restrict remote VPN peers to only access selected interfaces with specific certificates. In particular, certificates with certain DNs or FQDNs.
Configure
In this section, you are presented with the information to configure the features described in this document.
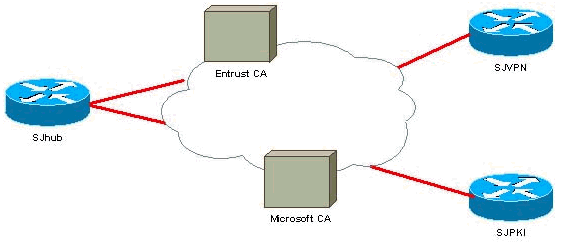
Network Diagram
This document uses the network setup shown in this diagram.
Configurations
This document uses the configurations shown here.
In this example, a simple network setup is used to demonstrate the feature. SJhub router has two identity certificates, one from Entrust certificate authority (CA) and the other one from Microsoft CA. See the Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
15-Jan-2002 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback