Configure AnyConnect Modules for Remote Access VPN On FTD
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how to configure AnyConnect Modules for Remote Access VPN (RA VPN) configuration that pre-exists on a Firepower Threat Defense (FTD) managed by a Firepower Management Center (FMC) through Firepower Device Manager (FDM).
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Basic understanding of RA VPN working.
- Understanding of navigation through the FMC/FDM.
- Basic knowledge of REST API and FDM Rest API Explorer.
Components Used
The information in this document is based on these software versions:
- Cisco Firepower Management Center (FMC) version 6.7.0
- Cisco Firepower Threat Defense (FTD) version 6.7.0
- Cisco Firepower Device Manager (FDM) version 6.7.0
- Cisco AnyConnect Secure Mobility Client running 4.9.0086
- Postman or any other API development tool
Note: FMC/FDM do not have an inbuilt Profile Editor and the AnyConnect Profile Editor for Windows has to be used to create a profile.
Note: The information in this document was created from devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any configuration change.
Background Information
The Cisco AnyConnect Secure Mobility Client is not limited to its support as a VPN client, it has a number of other options that can be integrated as modules. Following modules are supported for Anyconnect :
- Start Before Login (SBL):This module allows the user to establish a VPN connection into the enterprise before logging into Windows.
- Diagnostic and Reporting Tool (DART): This module is used to perform both diagnostics and reporting about the AnyConnect installation and connection. DART works by assembling the logs, status, and diagnostic information for analysis.
- Advanced Malware Protection (AMP): This module provides a cloud-delivered next-generation solution to detect, prevent, and respond to various threats.
- ISE Posture: Cisco Identity Services Engine (ISE) provides a next-generation identity and access control policy. This module provides the ability to identify the Operating System (OS), the AntiVirus, the AntiSpyware, etc that are currently installed on a host. This information is then used along with a policy to determine whether the host will be able to connect to the network.
- Network Visibility Module: The network visibility module monitors an endpoint application usage to uncover potential behavior anomalies and to make more informed network design decisions.
- Umbrella: Cisco Umbrella Roaming is a cloud-delivered security service that protects devices when they are off the corporate network.
- Web Security: Cisco Web Security Appliance (WSA), powered by Cisco Talos, protects the endpoint by automatically blocking risky sites and testing unknown sites.
- Network Access Manager: Network Access Manager provides a secure Layer 2 network in accordance with its policies. It detects and selects the optimal Layer 2 access network and performs device authentication for access to both wired and wireless networks.
- Feedback: This module collects the information and periodically sends it to the server. It helps the product team to improve the quality, reliability, performance, and user experience of AnyConnect.
In Firepower 6.7, FMC UI, and FTD Device REST API support is added to enable seamless deployment of all the mentioned AnyConnect Modules.

This table lists the Profiles Extensions and associated Module types needed to successfully deploy the endpoint functionality.
| Profile Extensions | Module Type |
| .fsp | FEEDBACK |
| .asp or .xml | AMP_ENABLER |
|
.sip or .xml
|
ISE_POSTURE |
|
.nvmsp or .xml
|
NETWORK_VISIBILITY |
|
.nsp or .xml
|
NETWORK_ACCESS_MANAGER |
|
.json or .xml
|
UMBRELLA |
|
.wsp or .xml
|
WEB_SECURITY |
Note: DART and SBL modules do not require any Profile.
Note: No additional licensing is required for the use of this feature.
Configuration
Configuration on Firepower Management Center (FMC)
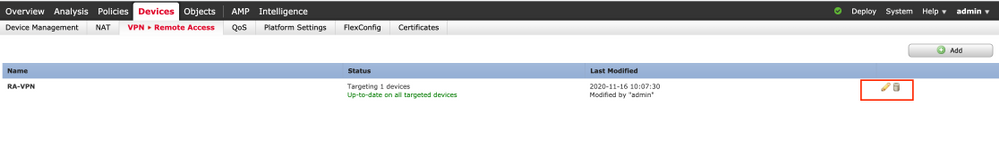
Step 1. Navigate to Device > VPN > Remote Access and click on Edit for the RA VPN configuration.
Step 2. Navigate to Advanced > Group Policies and click on Edit for the concerned Group-policy, as shown in this image.

Step 3. Navigate to AnyConnect > Client Modules and click on + to add the Modules, as shown in this image.

For the purpose of demonstration, Deployment of AMP, DART, and SBL modules are shown.
Step 4. Select the DART module and click on Add, as shown in this image.

Step 5. Click on + to add another module and select Start Before Login module, as shown in this image.

Note: This step allows you to download the SBL Module. SBL also has to enable in anyconnect client profile, which is uploaded as you navigate to AnyConnect > Profile under the Group Policy.
Step 6. Click on + to add another module and select AMP Enabler. Click on + to Add a Client Profile, as shown in this image.

Provide the Name of the Profile and upload the AMP Profile. Click on Save, as shown in this image.

Choose the profile created in the previous step and click on Enable Module download checkbox, as shown in this image.

Step 7. Click on Save once all the desired modules are added.

Step 8. Navigate to Deploy > Deployment and deploy the configuration to the FTD.

Configuration on Firepower Device Manager (FDM)
Step 1. Launch the API Explorer of the FTD on a Browser Window.
Navigate tohttps://<FTD Management IP>/api-explorer
This contains the entire list of API available on the FTD. It is divided based on the main feature with multiple GET/POST/PUT/DELETE requests which is supported by the FDM.
RaVpnGroupPolicy is the API used.

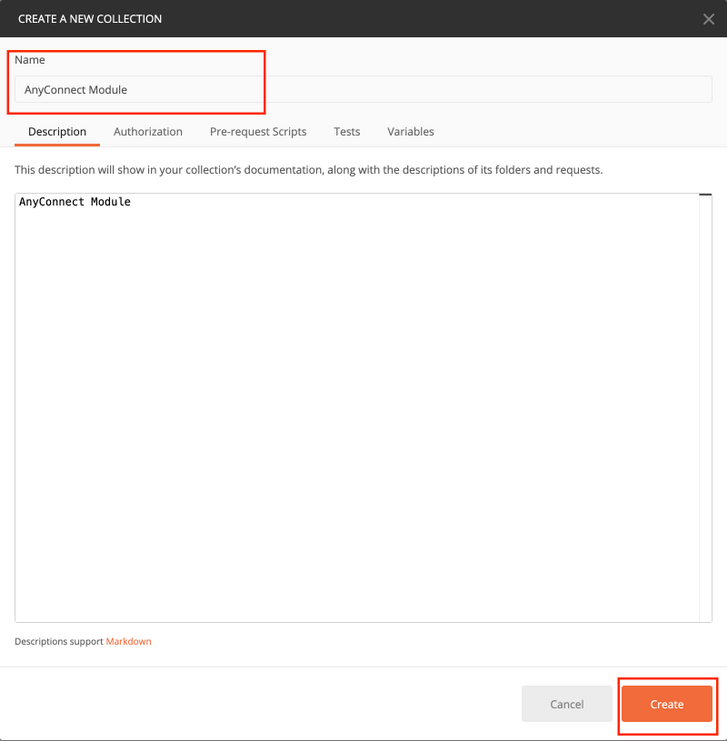
Step 2. Add a Postman collection for AnyConnect Modules. Provide a Name for the collection. Click on Create.
Step 3. Add a new request Auth to create a login POST request to the FTD in order to get the token to authorize any POST/GET/PUT requests. Click on Save.

The Body of the POST request must contain these:
| Type | raw - JSON (application/json) |
| grant_type | password |
| username | Admin Username in order to log in to the FTD |
| password | The password associated with the admin user account |
POST Request:https://<FTD Management IP>/api/fdm/latest/fdm/token

The Body of the Response contains the access token which is used in order to send any PUT/GET/POST requests to/from the FTD.

Step 4. Create aGet Group Policyrequest to add get details of the existing Group Policies. Click on Save, as shown in this image.

The Authorization tab must contain this for all subsequent GET/POST requests:
| Type | Bearer Token |
| Token | The access token received by running the Auth POST Request |
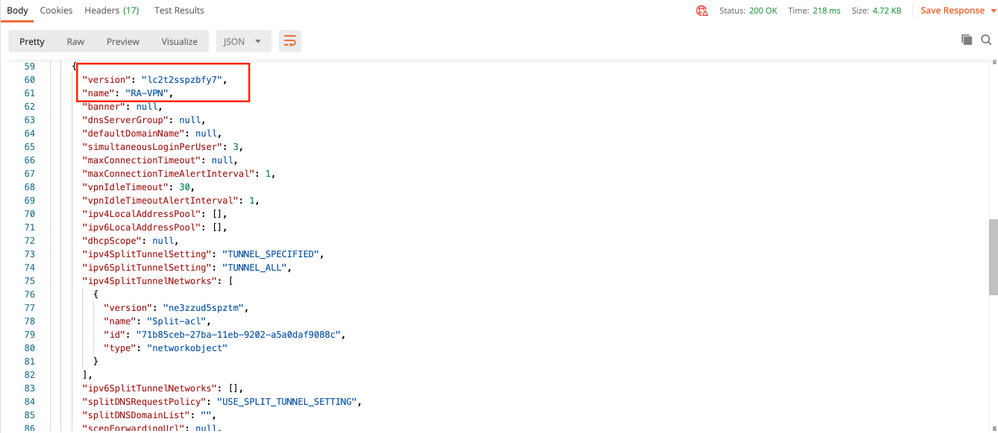
GET REQUEST:https://<FTD Management IP>/api/fdm/latest/object/ravpngrouppolicies

The Body of the response shows all the Group Policies configured on the device. ID of the Group Policy is used to update the specific Group Policy.


For the purpose of demonstration, Deployment of AMP, DART, and SBL modules are shown.
Step 5. Create a request to Upload a Profile. This step is needed only for the modules which require a profile. Upload the Profile in filetoUpload section. Click on Save.
POST REQUEST:https://<FTD Management IP>/api/fdm/latest/action/uploaddiskfile
The Body of the Request must contain the Profile file added in Body in form-data format. The profile needs to be created using AnyConnect Profile Editor for Windows
The key type should beFileforfiletoUpload.


The body of the response gives an id/filename which is used to refer to the profile with the concerned module.

Step 6. Create a request to Update AnyConnect Profile. This step is needed only for the modules which require a profile. Click on Save., as shown in this image.

POST REQUEST: https://<FDM IP>/api/fdm/latest/object/anyconnectclientprofiles
The body of the request contains this information:
| name | Logical name that you would call the file |
| diskFileName | Needs to match the fileName that is received in the Upload Profile POST response |
| anyConnectModuleType | Meeds to match the appropriate module shown in Module Type Table |
| type | anyconnectclientprofile |

The Body of the response shows the Profile ready to be pushed to the device. Name, version, id, and type received in response are used in the next step to bind the profile to Group Policy.

Step 6. Create a PUT request to add Client Profile and Module to existing Group Policy. Click on Save, as shown in this image.

PUT REQUEST:https://<FDM IP>/api/fdm/latest/object/ravpngrouppolicies/{objId}
ObjId is the id obtained in Step 4. Copy the contents of the concerned Group-policy obtained in Step 4 to the body of the request and add this:
Client Profile
Name, version, id, and type of Profile received in the previous Step.
Client Modules
The name of the Module which needs to be enabled should match exactly as given in Module Table.

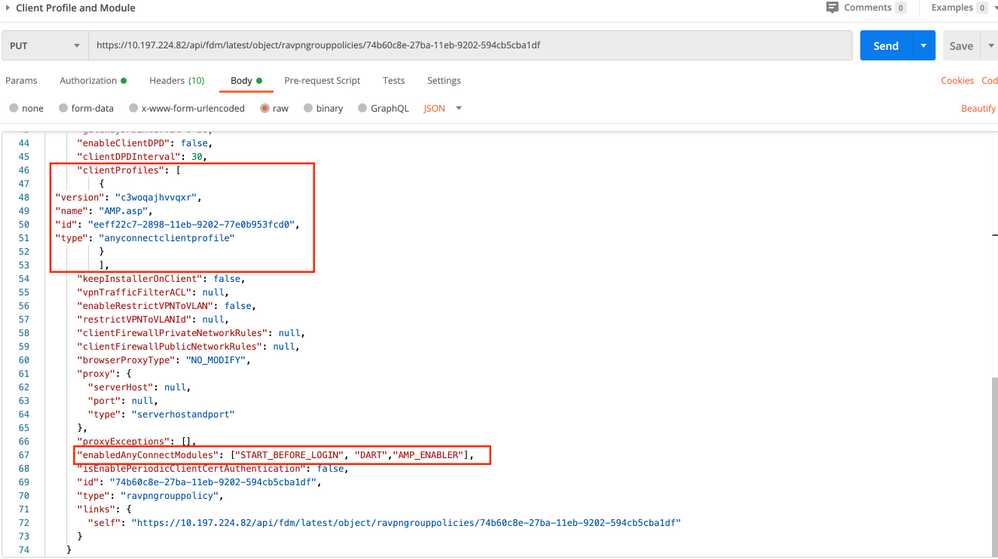
The Body of the response shows the Profile and Module successfully bound to Group-Policy.

Note: This step allows the download SBL Module. SBL also has to enable in anyconnect client profile which can be uploaded as you navigate to Devices > Remote Access VPN > Group Policies > Edit Group Policy > General >AnyConnect Client Profile.
Step 7. Deploy the configuration to the device through FDM. Pending changes show client profile and modules to be pushed.

Configuration pushed to the FTD CLI after successful deployment:
!--- RA VPN Configuration ---!
webvpn
enable outside
anyconnect image disk0:/anyconnpkgs/anyconnect-win-4.9.00086-webdeploy-k9.pkg 2
anyconnect profiles AMP.asp disk0:/anyconncprofs/AMP.asp
anyconnect profiles defaultClientProfile disk0:/anyconncprofs/defaultClientProfile.xml
anyconnect enable
tunnel-group-list enable
!--- Group Policy Configuration ---!
group-policy RA-VPN internal
group-policy RA-VPN attributes
webvpn
anyconnect modules value ampenabler,dart,vpngina
anyconnect profiles value AMP.asp type ampenabler
Verify
Establish a successful connection to the FTD.
Navigate to Settings > VPN > Message History to see the details about modules that were downloaded.

Troubleshoot
Collect DARTfor troubleshooting issues with the installation of client modules.
Contributed by Cisco Engineers
- Rohan BiswasCisco TAC Engineer
- Tazy KhanCisco TAC Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback