Configure EIGRP IPV6 on ASA
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how to configure EIGRP IPV6 on Cisco Adaptive Security Appliance (ASA).
Prerequisites
Minimum Supported Software and Hardware Platforms
|
Min Supported Manager Version |
Managed Devices |
Min Supported Managed Device Version Required |
Notes |
|
ASA |
All ASA platforms |
9.20.1 |
CLI |
|
CSM |
All ASA platforms |
4.27 |
CSM GUI |
|
ASDM |
All ASA platforms |
7.20.1 |
ASDM GUI |
Requirements
Cisco recommends that you have knowledge of these topics:
- Cisco Security Manager
- Adaptive Security Device Manager
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Adaptive Security Appliance (ASA), 9.20.1 or higher
- Cisco Security Manager (CSM) running 4.27
- Cisco Adaptive Secuirty Device Manager running 7.20.1
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
EIGRP for IPV6
• EIGRP is already supported and available on ASA. The demand for EIGRP IPV6 is increasing.
• The configuration for EIGRPv4 and EIGRPv6 are similar, but they can be configured and managed independently.
• Due to differences in protocols, configuration and operation differ slightly.
What is New
• In earlier releases EIGRP was supported only for IPv4 and from ASA 9.20 onwards, EIGRP would be supported with IPV6.
• Support for EIGRP IPv6 with link-local address on ASA only.
Limitations
Supported
• EIGRPv6 is currently supported on ASA only on routed mode, HA, and cluster.
• EIGRPv6 neighborship can be enabled only with link local address.
Not Supported
• Transparent mode
• Multi Context
• Authentication
• On FTD
Feature Details
Functional Feature Description
• EIGRP for IPv6 uses the same framework as EIGRP for IPv4.
• EIGRP IPv6 would communicate only with IPv6 peers and advertise only IPv6 routes.
EIGRP IPV4 and EIGRP IPv6 share similar characteristics as well like:
• Neighbor, routing, and topology tables are maintained.
• It uses DUAL stack for fast convergence and loop free network.
The differences are:
• The network command under router-mode is not used for EIGRP IPv6.
• Use ipv6 router eigrp <AS> to enable EIGRP IPV6 router process.
• Explicitly configure ipv6 eigrp <AS> to enable EIGRP IPv6 on specific interface.
• User configured IPv6 address cannot be used to establish neighborship.
• Authentication is not supported in current release.
EIGRP Features
EIGRP Functional Overview
• EIGRP for IPv6 would be same as EIGRP IPv4.
• EIGRP uses the Diffusing Update Algorithm (DUAL) to achieve rapid convergence.
DUAL not only calculates the best routes but also loop free routes.
There are mainly two tables used by DUAL to for calculation of best route. They are neighbor routing table, topology table.
DUAL calculates alternative path based on reported feasible distance.
• The neighbor table keeps track of all directly connected neighbors. Hello packets are used to check that status of neighbor.
• Topology table keeps information on metrics of all routes in the network. Successor and feasible successor keep the best path and alternate path information.
How It Works
Hello messages are used to discover neighbor before establishing adjacency.
Update messages are exchanged between neighbors to build topology table and routing table.
Query messages are sent to other EIGRP neighbors for a feasible successor when DUAL is re-computing a route in which the firewall does not have a feasible successor.
Reply messages are sent as the response to an EIGRP Query packet.
Acknowledge messages are used to acknowledge EIGRP Updates, Queries, and Replies.
EIGRP Message Flows
EIGRP IPv6 uses a Hello packet to discover other EIGRP-capable devices on directly attached links and to form neighbor relationships.
EIGRP IPv6 transmits Hello packets with a source address being the link-local address of the transmitting interface.
Hello messages are like keep alive messages to keep track of the neighbor status.
Default timer of hello message is 5 seconds. Upon Hello message exchange, an update message is received and sent. This is used to build the topology table and install the routes in the RIB accordingly.
Establishing Neighborship
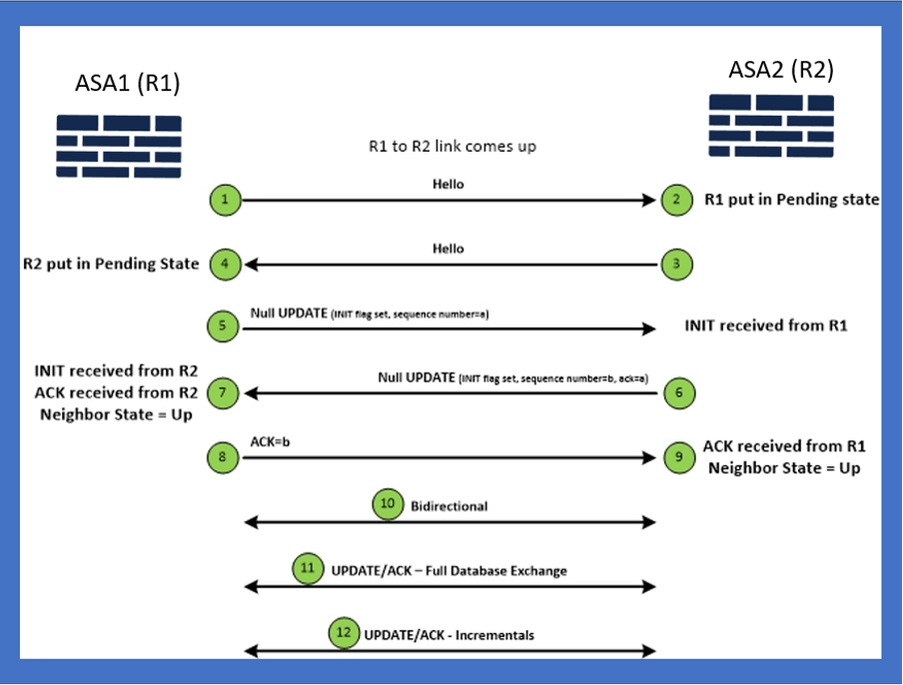
Internal View / ASA CLI
Neighborship: Basic Config and Multi/Unicast
To establish neighborship, router mode config is needed. It is the same for IPv4 except for the config starts with IPv6 keyword.
It also needs to attach the participating interface to autonomous system.
Neighborship can be formed in two ways, using either multicast or unicast.
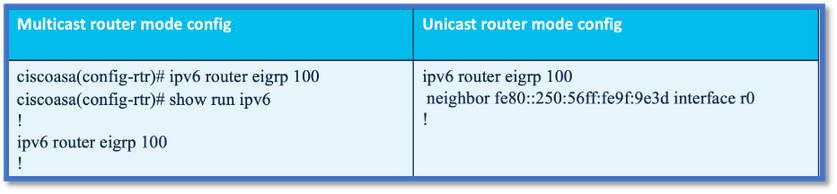
Neighborship: Specify Interface and Router ID
- In addition to router mode configuration, the interface participating in the neighborship needs to be attached to respective autonomous system.
- Make sure to enable IPv6 on the interface.
- Router id is needed for neighborship to form. It would be taken implicitly from the IPv4 interface, or it has to be configured explicitly under router mode, else neighborship would not be formed.
Basic Neighborship
You have simply directed connected topology and configuration for unicast and multicast neighborship.
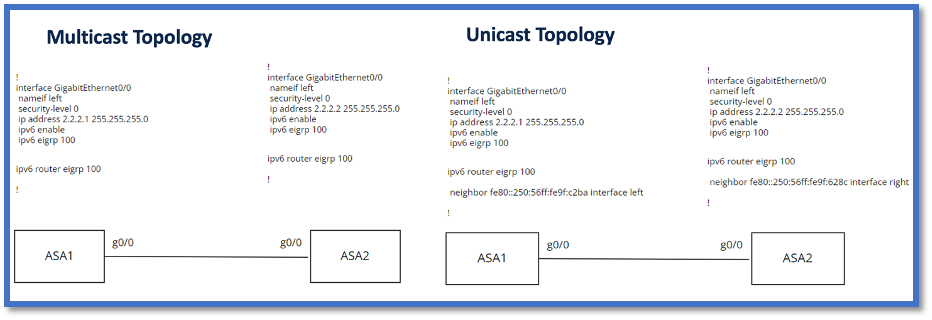
Verify
Check Neighborship State
show ipv6 eigrp neighbors is used to check the neighborship state.
ciscoasa(config-rtr)# show ipv6 eigrp neighbors
EIGRP-IPv6 Neighbors for AS(50)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
1 Link-local address: m3 12 1w3d 270 1620 0 153 fe80::250:56ff:fe9f:e7e8
0 Link-local address: m2 12 1w3d 174 1044 0 152 fe80::250:56ff:fe9f:8d83
Hello and Hold Interval Configuration
- Hello interval and Hold interval can be configured using the configurations under interface.
- For non-broadcast multiple access network (NBMA) interfaces, the default value of hello timer is 5 seconds and hold time default value is 15 seconds.
ciscoasa(config-if)# ipv6 hello-interval eigrp 100 ?
interface mode commands/options:
<1-65535> Seconds between hello transmissions
ciscoasa(config-if)#
ciscoasa(config-if)# ipv6 hold-time eigrp 200 ?
interface mode commands/options:
<1-65535> Seconds before neighbor is considered down
ciscoasa(config-if)#
Passive Interface Configuration
- In case you do not want an interface to form neighborship, passive-interface config can be used so that Hellos on the interface would not be sent and not form adjacency.
ciscoasa(config-rtr)# passive-interface ?
ipv6-router mode commands/options:
Current available interface(s):
default Suppress routing updates on all interfaces
g0 Name of interface GigabitEthernet0/0
mgmt Name of interface Management0/0
ciscoasa(config-rtr)#
Distribute List for Route Filtering
- Distribute list can be used along with the prefix config to filter routing updates either incoming or outgoing for given interface.
ciscoasa(config-rtr)# distribute-list prefix-list abc ?
ipv6-router mode commands/options:
in Filter incoming routing updates
out Filter outgoing routing updates
ciscoasa(config-rtr)#
Redistributing Routes from Other Protocols
- Routes from other routing protocols can be redistributed into EIGRP.
- Use the redistribute command under router.
ciscoasa(config-rtr)# redistribute ?
ipv6-router mode commands/options:
bgp Border Gateway Protocol (BGP)
connected Connected Routes
eigrp Enhanced Interior Gateway Routing Protocol (EIGRP)
isis ISO IS-IS
ospf Open Shortest Path First (OSPF)
static Static Routes
ciscoasa(config-rtr)#
EIGRP IPv6 in ASDM
Overview of New Options for EIGRPv6
- EIGRPv6 support is added as part of ASDM 7.20.1.
- EIGRPv6 configuration added as part of interfaces sub CLI command.
- EIGRPv6 configuration added in router and support router commands.
EIGRPv6 Configuration in Interface
- Navigate to Configuration > Device Setup > Routing > EIGRPv6.
- Select Interface to be able to see all the interfaces which are supported.
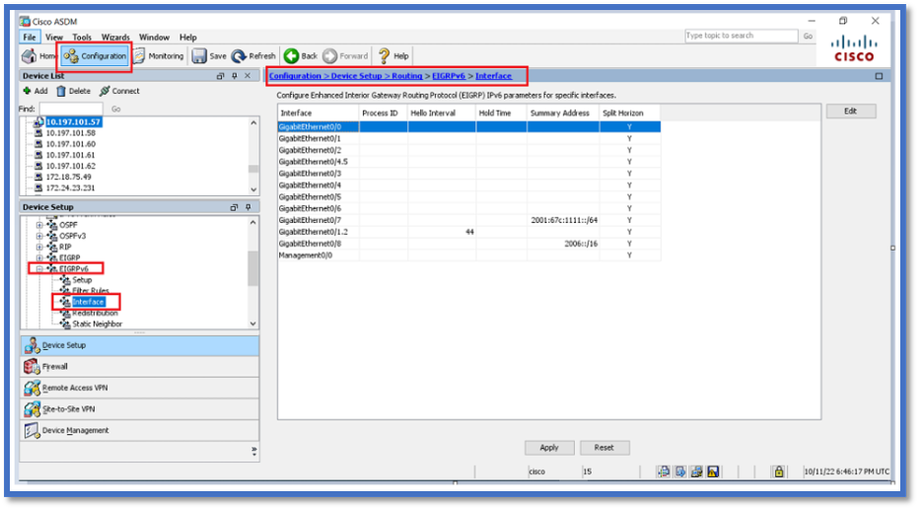
Configure EIGRPv6 Settings for an Interface
- Navigate to Configuration > Device Setup > Routing > EIGRPv6 > Interface.
- Select Interface and click Edit.
- Select checkbox(es) to configure process ID, Hello Interval, Hold Time, Split Horizon, and/or Summary Address.
- Configure the settings, then click OK.
- Click Send.
- When the CLI's appear, Click Send, Cancel, or Save to File.
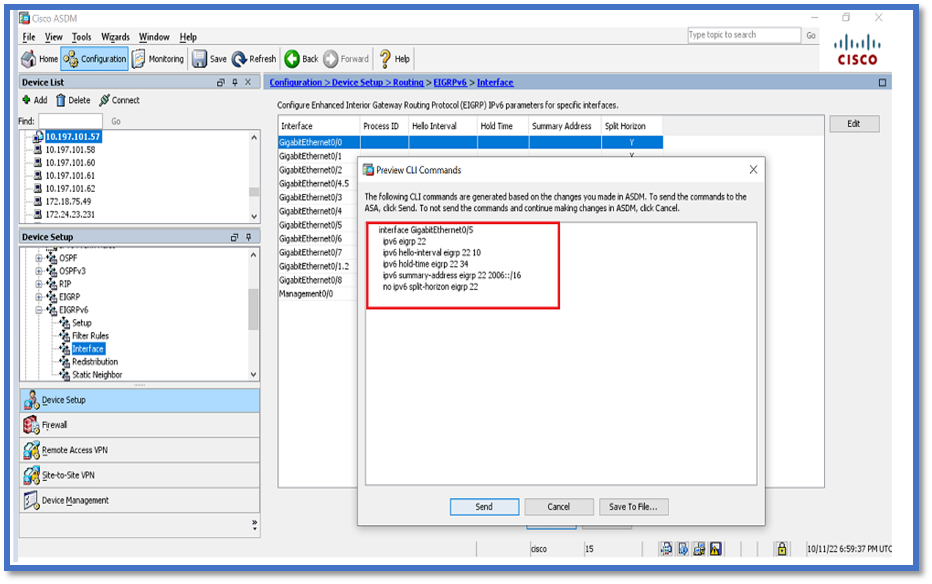
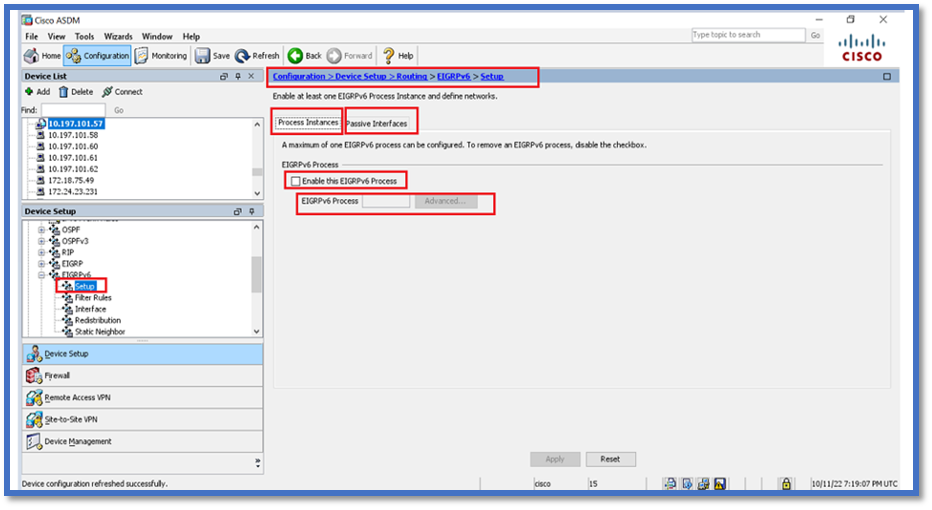
Process Instances and Passive Interfaces
- Navigate to Configuration > Device Setup > Routing > EIGRPv6 > Set up.
- Able to See Process Instances and Passive Interfaces.
- Under Process Instances, Enable EIGRPv6 Process.
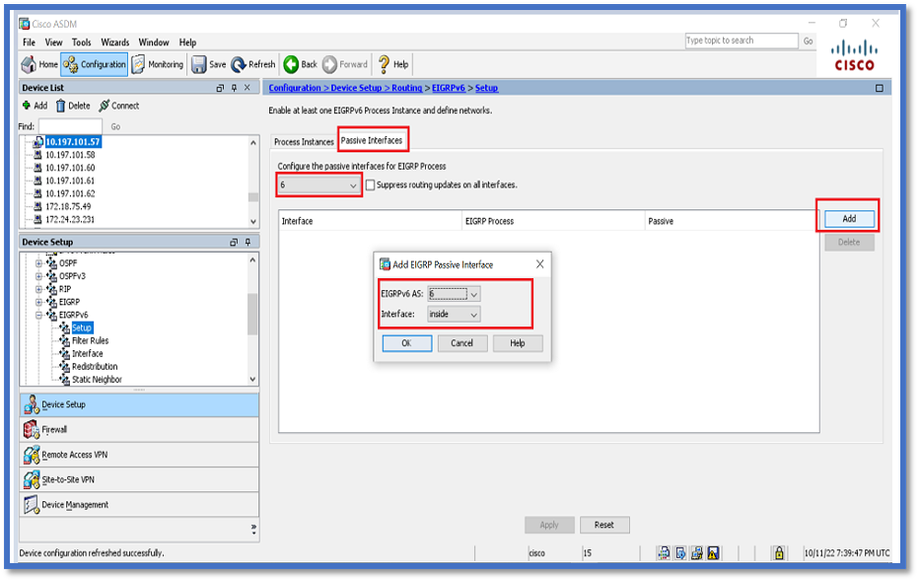
Passive Interfaces Configuration
- Navigate to Configuration > Device Setup > Routing > EIGRPv6 > Set up.
- Click Passive Interfaces > Add > Select Interface.
- Click OK.
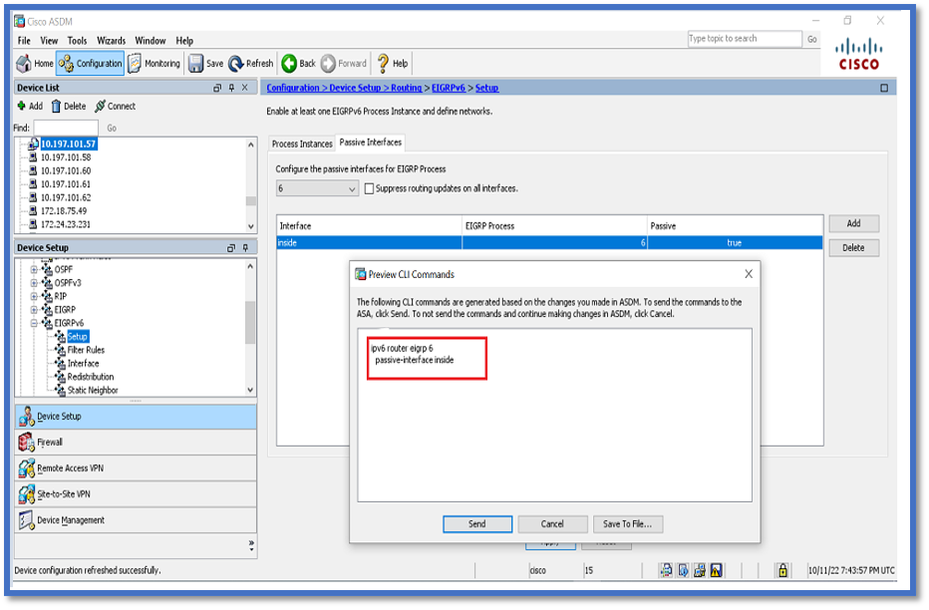
- Click Apply.
- The CLI window appears.
Router EIGRP and Default Metrics Configuration
- Navigate to Device Setup > Routing > EIGRPv6 > Set up.
- Click Process Instances > Provide Process ID Value.
- Click Advanced button.
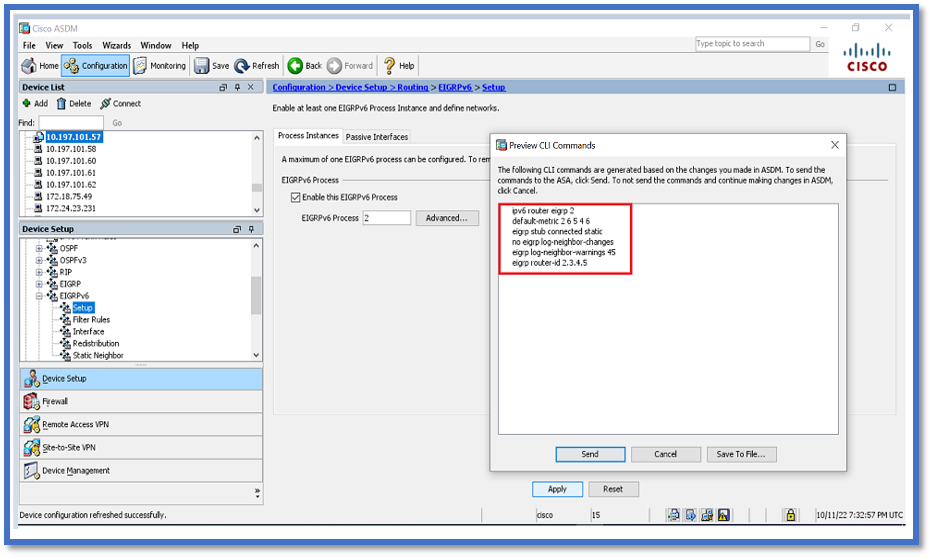
- Provide Router ID, Default Metrics, Stub, and log neighbor values.
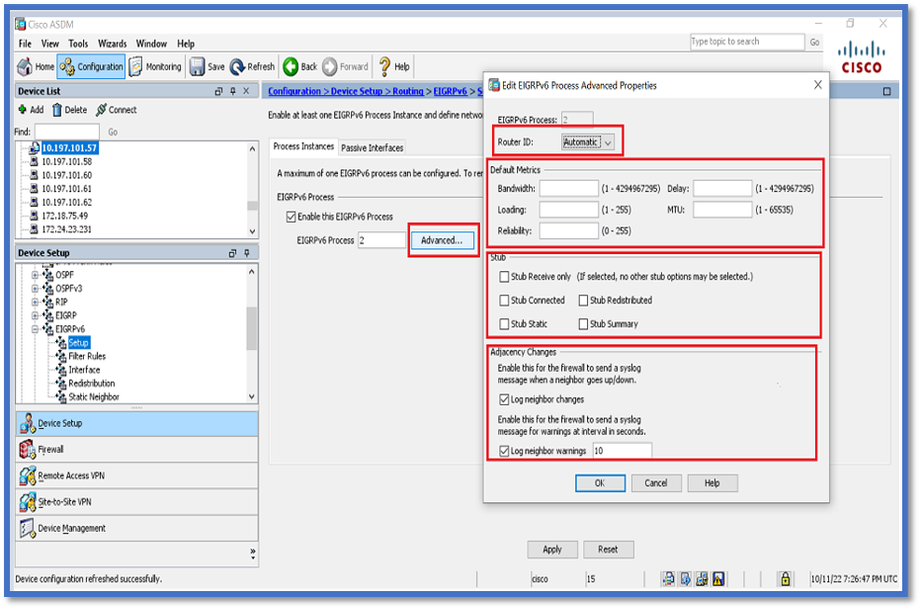
- Click Apply.
- The CLI window appears.
Filter Rules (Distribute-List) Configuration
- Navigate to Configuration > Device Setup > Routing > EIGRPv6 > Filter Rules.
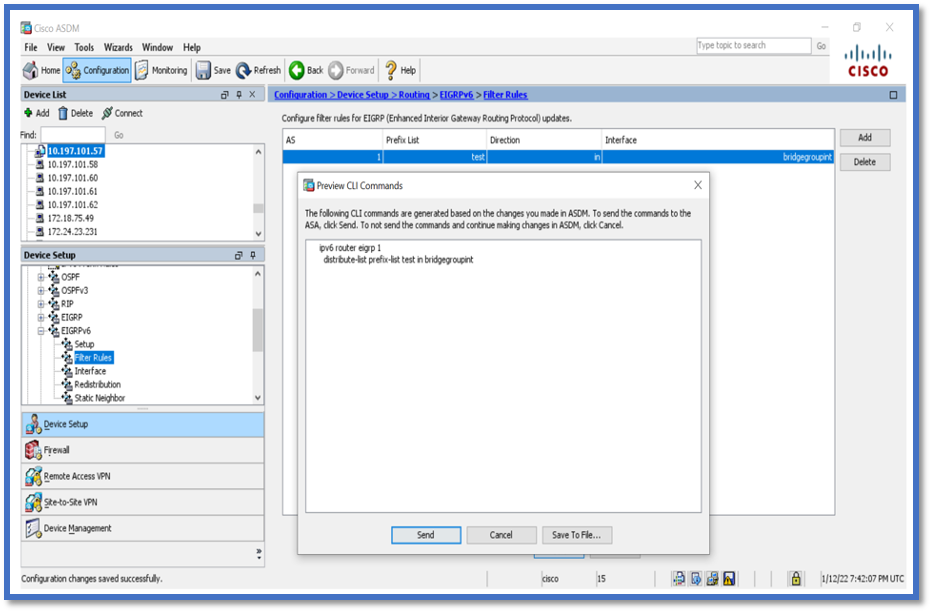
- Click Add > Select Prefix list > Direction > Interface.
- Click OK.
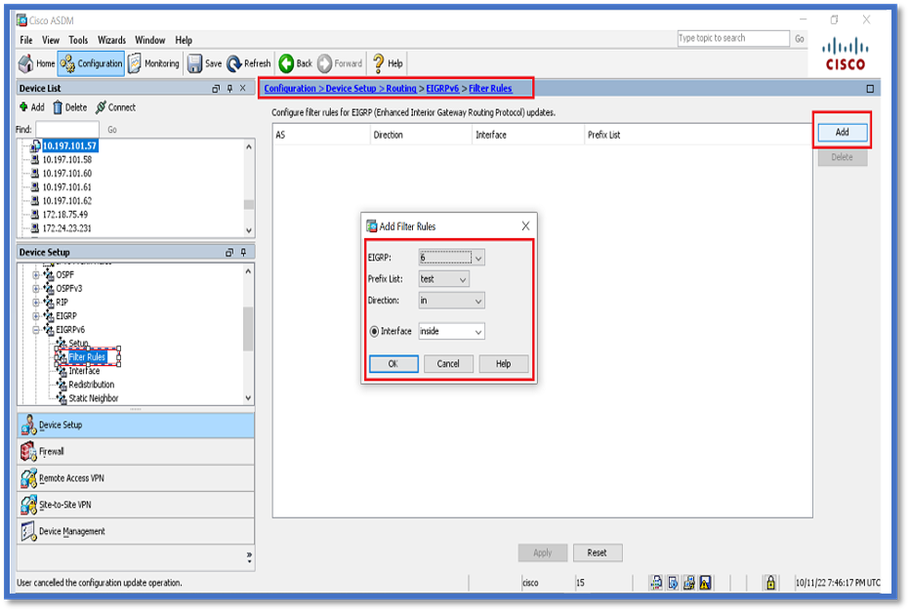
- Click Apply.
- The CLI window appears.
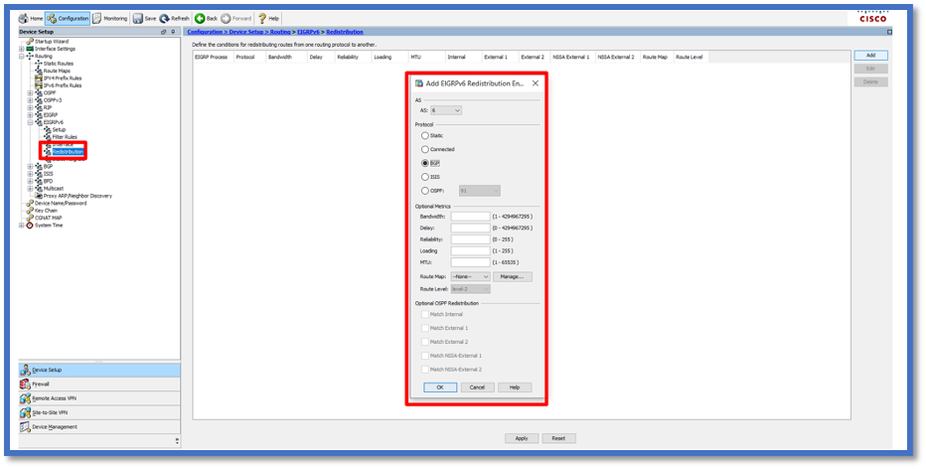
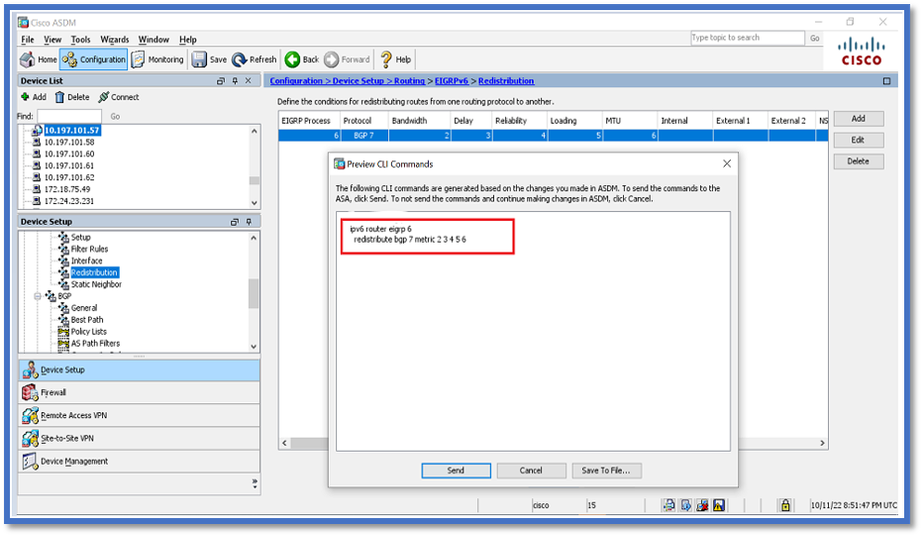
Redistribute Routes Configuration
- Navigate to Configuration > Device Setup > Routing > EIGRPv6 > Redistribution.
- Click Add > Select protocol.
- Provide Optional metrics
- Click OK.
- Click Apply.
- The CLI window appears
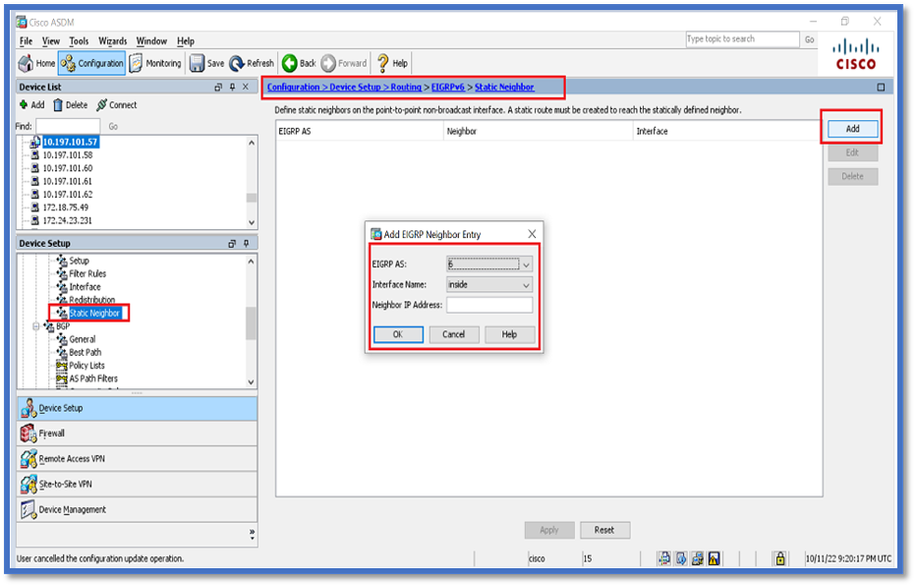
Neighbor: Unicast Router Mode
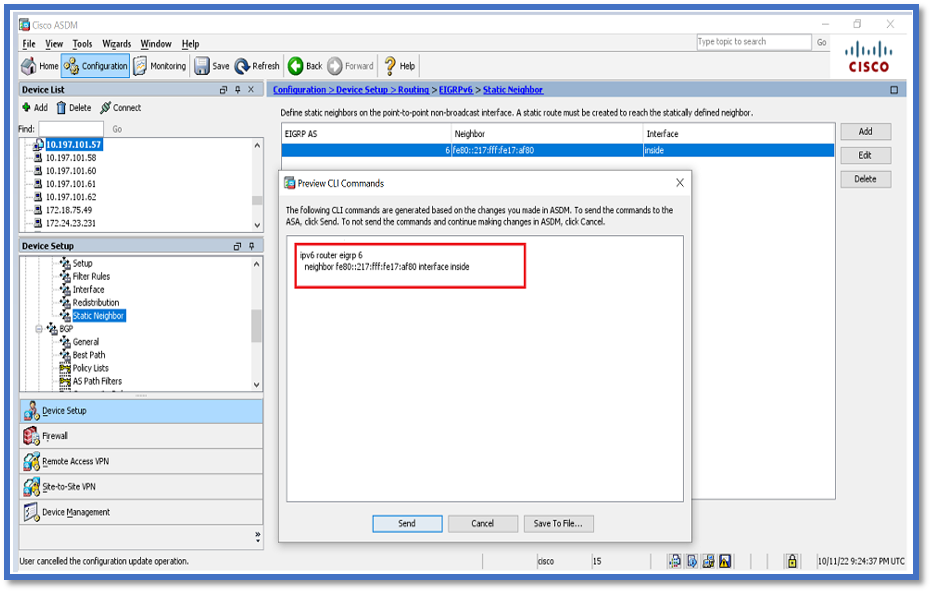
- Navigate to Configuration > Device Setup > Routing > EIGRPv6 > Static Neighbor.
- Click Add > Select Interface.
- Provide Neighbor Address.
- Click OK.
- Click Apply.
- The CLI window appears.
Multicast Router Mode
The configuration for Multicast router mode is similar to that for Unicast Router Mode.
- Navigate to Configuration > Device Setup > Routing > EIGRPv6 > Setup.
- Enable checkbox to enable EIGRPv6 Process.
- Enter value in EIGRPv6 Process input field.
- Click Apply.
- Able to see the CLI.
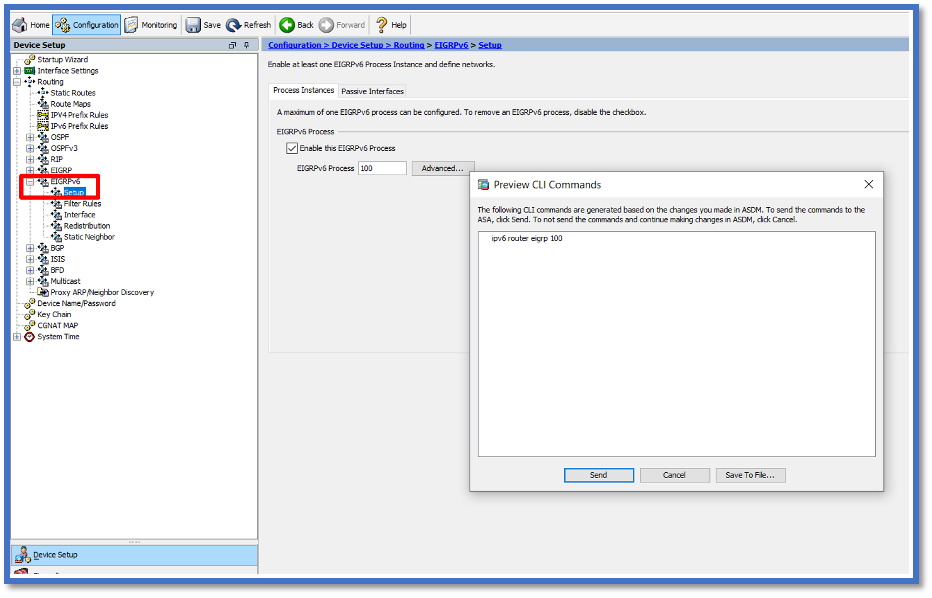
IPv6 EIGRP in CSM
Overview of New Options in CSM for EIGRPv6
- EIGRPv6 support is added as part of CSM 4.27.
- EIGRPv6 configuration added as part of Interfaces Sub CLI command.
- EIGRPv6 configuration added in Router and Support Router commands.
Enable EIGRP IPv6 Support
- Navigate to Platform > Routing > EIGRP > IPv6 Family.
- Enable IPv6 by clicking the Enable IPv6 EIGRP checkbox.
- Provide AS Number between 1 and 65535.
- Tabs allow for configuring Setup (shown here), Filter Rules, Neighbors, Redistribution, Summary Address, and Interfaces.
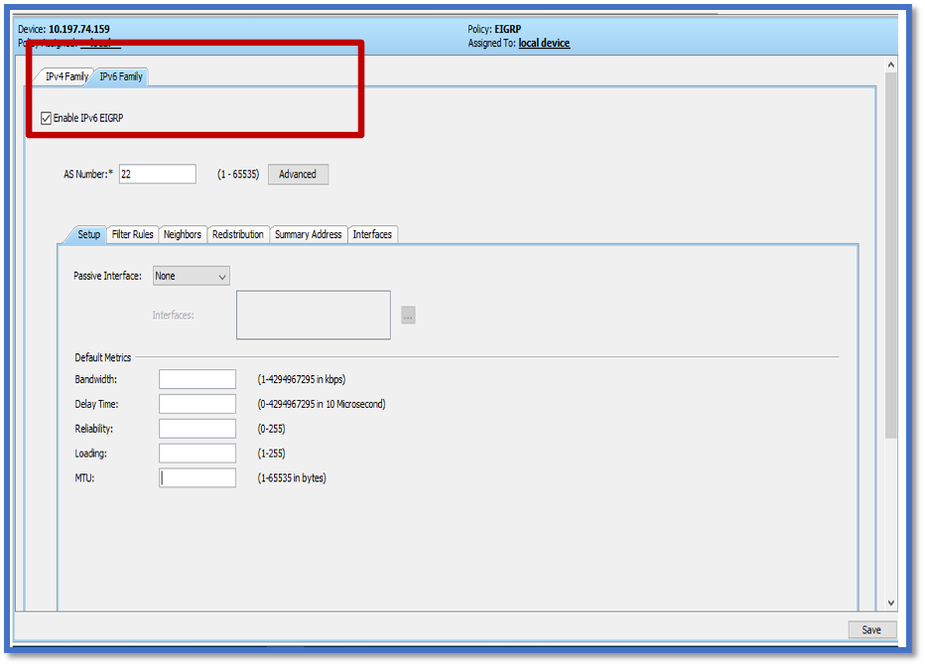
EIGRP IPv6 Setup Tab
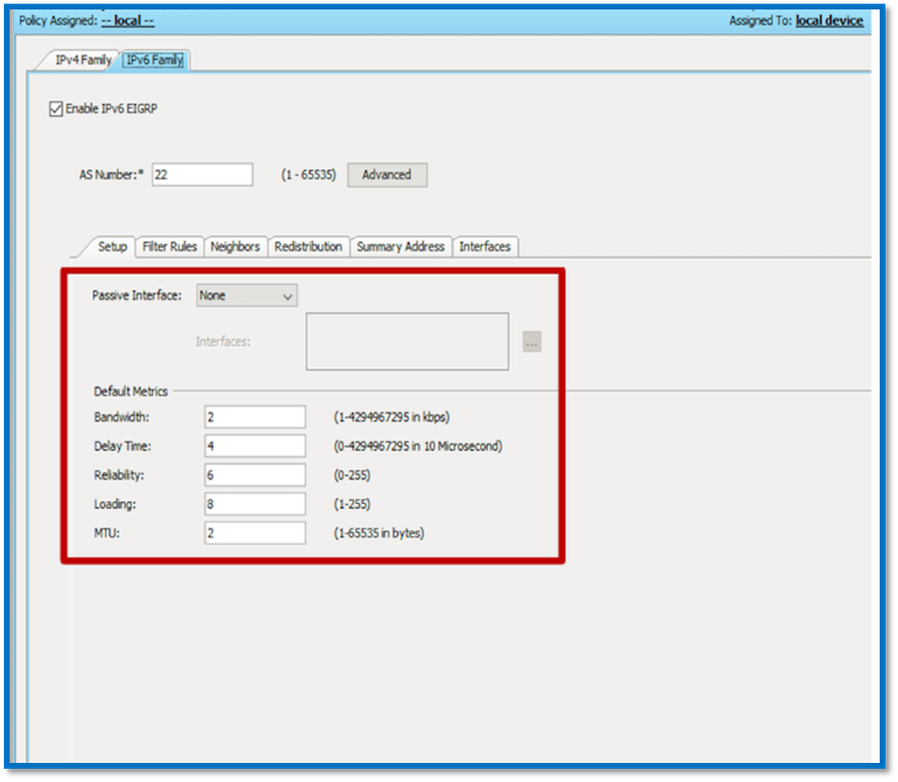
- Navigate to Platform > Routing > EIGRP > IPv6 Family > Setup Tab.
- Passive Interface has 3 options
1. None
2. Default
3. Specific Interface
- Default Suppress routing updates on all interfaces.
- In Specific Interface, select interface from Interface selector.
- Assign values to Default Metrics.
- Click OK and Save.
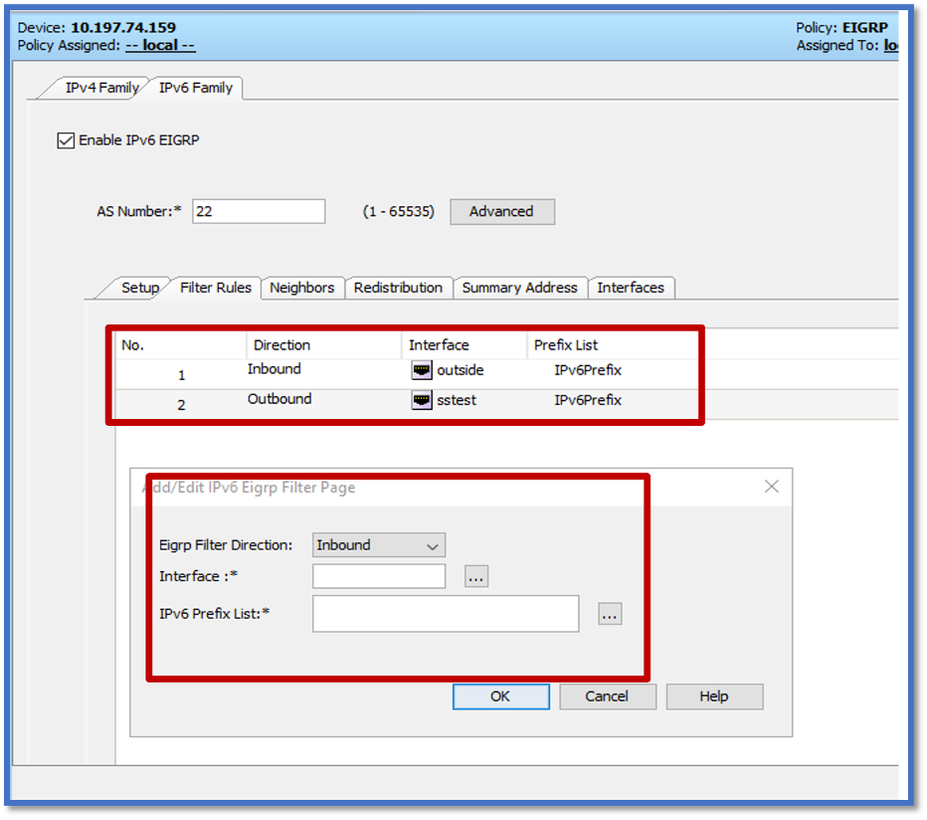
EIGRP IPv6 Filter Rules Tab
- Navigate to Platform > Routing > EIGRP > IPv6 Family > Filter Rules tab.
- Select Eigrp Filter Direction according to Direction (either Inbound or Outbound).
- Select Interface.
- Enter the IPv6 Prefix-list to filter connections based on an IPv6 prefix-list.
EIGRP IPv6 Neighbors Tab
- Navigate to Platform > Routing > EIGRP > IPv6 Family > Neighbors tab.
- Enter the Interface and Network in the Add/Edit IPv6 Eigrp Neighbor Page dialog.
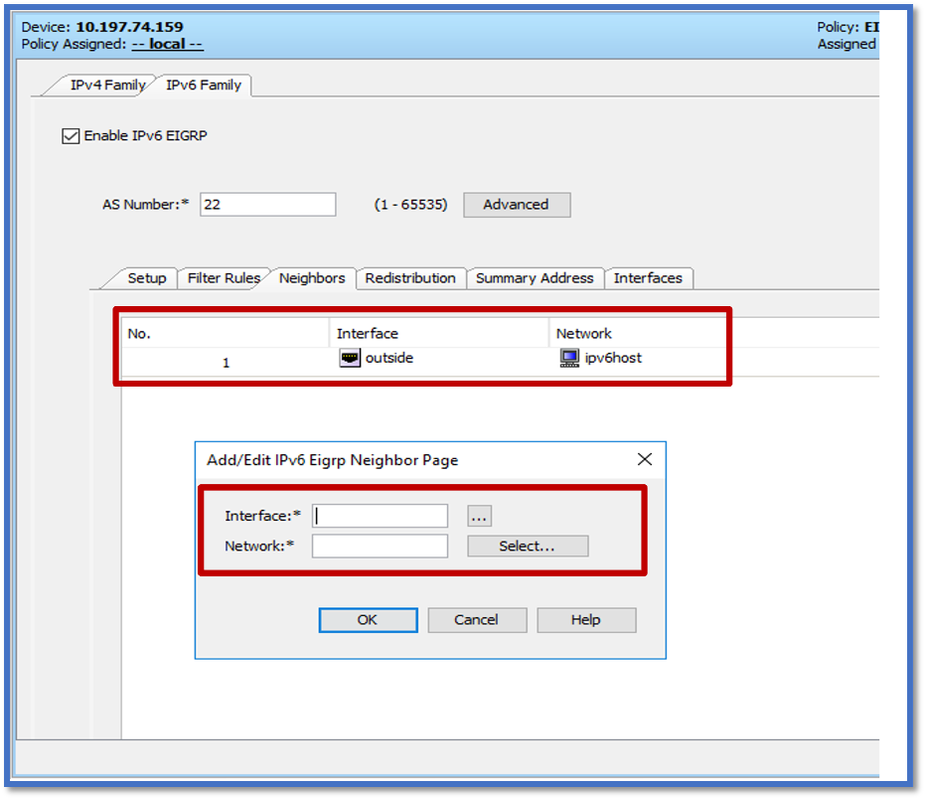
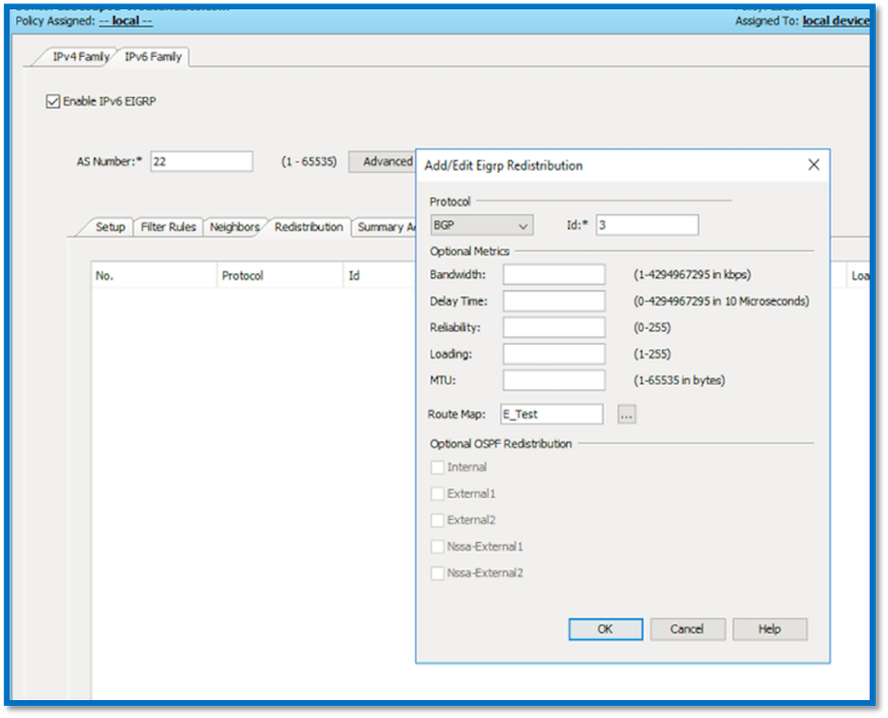
EIGRP IPv6 Redistribution Tab
- Navigate to Platform > Routing > EIGRP > IPv6 Family > Redistribution tab.
- Click the Add button and select Protocol. Based on the Protocol selection, other options get enabled.
- For BGP and OSPF, ID textbox enabled.
- If OSPF is enabled, Optional OSPF Redistribution options enabled
- If ISIS is enabled ISIS Level is enabled.
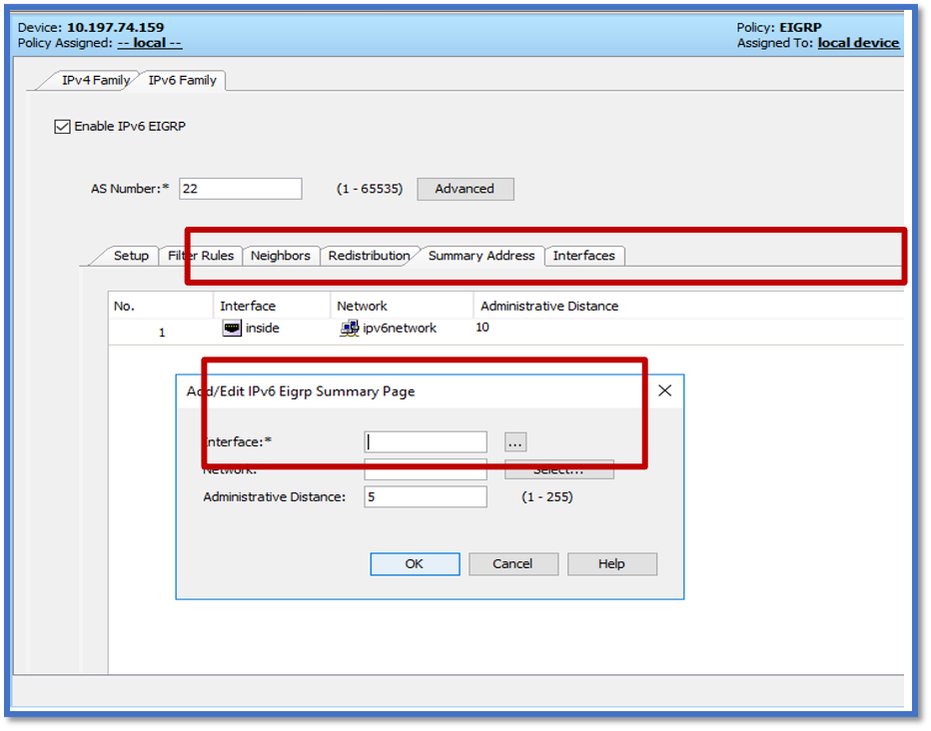
EIGRP IPv6 Summary Address Tab
- Navigate to Platform > Routing > EIGRP > IPv6 Family > Summary Address tab.
- Click the Add button and select interface from Interface selector.
- In Network, select IPv6 address and Administrative Distance value.
- Click OK and Save.
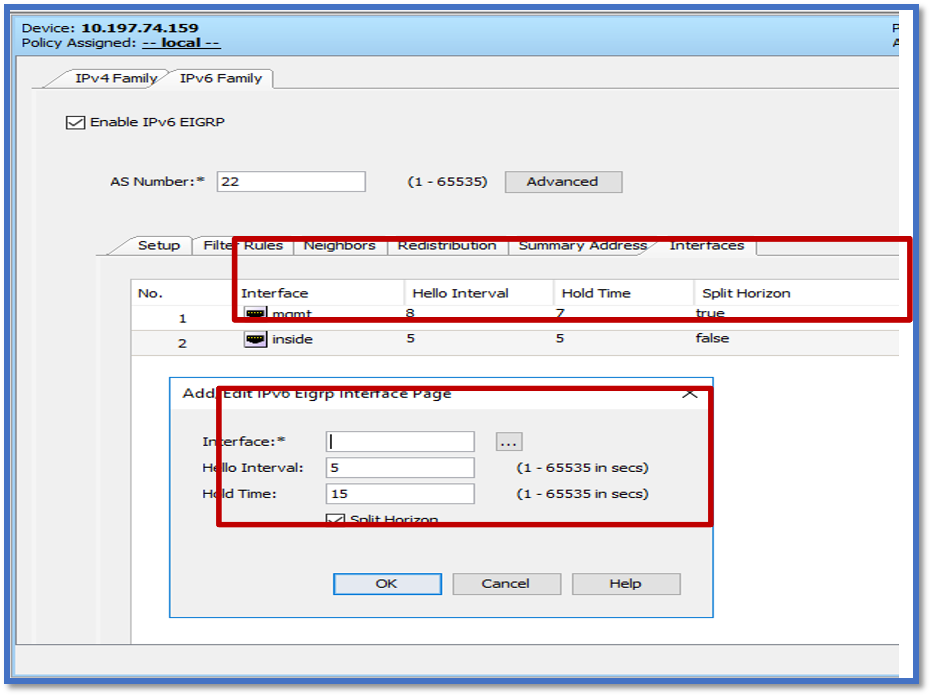
EIGRP IPv6 Interfaces Tab
- Navigate to Platform > Routing > EIGRP > IPv6 Family > Interfaces tab.
- Click Add button and select interface from Interface selector.
- You can change the Hello Interval and Hold Time (optional).
- Split Horizon is enabled by default. It can be unchecked.
- Click OK and Save.
Troubleshooting
Steps to Troubleshoot
- Check the neighborship state using the show commands.
- Check show ipv6 eigrp topology output to verify the contents of topology table.
- Use the show ipv6 eigrp events command, which can give useful info on the major events related to EIGRP.
- Use show eigrp tech-support detailed to check neighborship and topology table timer values.
Show ipv6 eigrp events
show ipv6 eigrp events displays important event logging in the systems which are helpful in debugging.
ciscoasa(config-rtr)# show ipv6 eigrp events
Event information for AS 50:
1 18:05:56.203 Metric set: 1001::/64 768
2 18:05:56.203 Route installing: 1001::/64 fe80::250:56ff:fe9f:e7e8
4 18:05:56.203 FC sat rdbmet/succmet: 768 512
5 18:05:56.203 Rcv update dest/nh: 1001::/64 fe80::250:56ff:fe9f:e7e8
6 18:05:56.203 Change queue emptied, entries: 1
7 18:05:56.203 Metric set: 1001::/64 768
8 18:05:56.203 Update reason, delay: new if 4294967295
Show ipv6 eigrp timers
show ipv6 eigrp timers shows the current hello timer and the hold timer applied.
- Default timer for hello interval and hold timer is 5 seconds and 15 seconds.
- If NBMA interface with lower bandwidth, the default value for hello timer is 15 seconds; for hold timer,180 seconds
ciscoasa(config-rtr)# show ipv6 eigrp timers
EIGRP-IPv6 Timers for AS(50)
Hello Process
Expiration Type
| 0 .406 (parent)
| 0 .406 Hello (m2)
Update Process
Expiration Type
| 11.600 (parent)
| 11.600 (parent)
| 11.600 Peer holding
| 11.930 (parent)
| 11.930 Peer holding
Show ipv6 eigrp topology
show ipv6 eigrp topology The topology table consists of all destinations advertised by a neighboring router.
ciscoasa(config-rtr)# show ipv6 eigrp topology
EIGRP-IPv6 Topology Table for AS(50)/ID(172.27.173.103)
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply,
r - reply Status, s - sia Status
P 1001::/64, 1 successors, FD is 768, serno 8907
via fe80::250:56ff:fe9f:8d83 (768/512), m2
P 3001::/64, 1 successors, FD is 768, serno 8906
via fe80::250:56ff:fe9f:8d83 (768/512), m2
P 2001::/64, 1 successors, FD is 768, serno 8905
via fe80::250:56ff:fe9f:8d83 (768/512), m2
Show Tech for EIGRP
Show tech can be used for troubleshooting as it collects useful information including timer parameters, neighborship details, traffic statistics for EIGRP, memory usage counters, and others.
ciscoasa(config-if)# show eigrp tech-support detailed ?
exec mode commands/options:
| Output modifiers
<cr>
ciscoasa(config-if)#
Sample Problem
Problem Seen with Neighbor Formation
- If problem seen with neighbor formation:
- Check if you have at least an IPv4 address configured if router-id is not explicitly configured under router-mode configuration.
- Make sure to configure router-id under router mode configuration.
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
|
2.0
|
19-Jul-2024
|
Updated Formatting.
|
|
1.0
|
18-Jul-2024
|
Initial Release
|
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
29-Jul-2024 |
Initial Release |
Contributed by Cisco Engineers
- Surabhi SrivastavaTechnical Consulting Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback