Introduction
This document describes the process to configure route leak between Global Routing Table (GRT) to VRF with Cisco IOS® XR software.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Knowledge of Basic IP Routing
- Knowledge of Cisco IOS and Cisco IOS XR command line
Components Used
This procedure is not restricted to any software release in Cisco IOS XR therefore, all releases can be used to complete the next steps.
The information in this document is based on these software and hardware versions:
- Router with Cisco IOS XR software
- Router with Cisco IOS software
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
The purpose of this demonstration is to show the configuration for route leak between global route table and vrf route table on Cisco IOS XR.
Topology
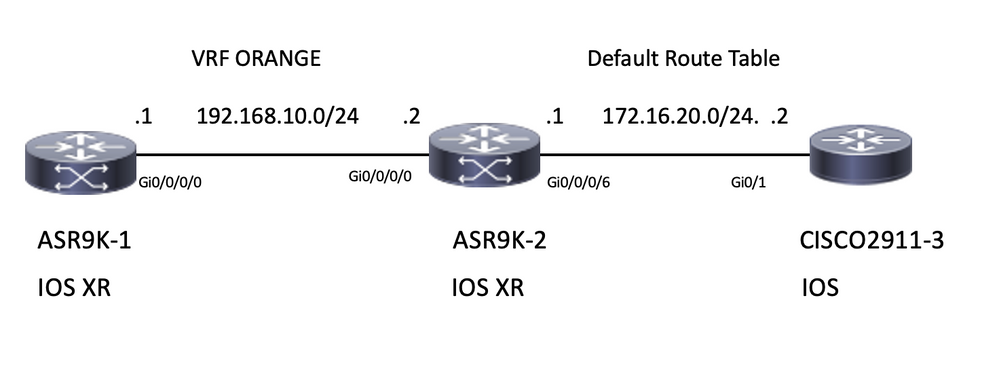
Initial Verification
Interface and Static Route Configuration
ASR9901-1
RP/0/RSP0/CPU0:ASR9901-1#show run interface gi0/0/0/0
Wed Oct 19 15:21:21.122 UTC
interface GigabitEthernet0/0/0/0
cdp
vrf ORANGE
ipv4 address 192.168.10.1 255.255.255.0
!
RP/0/RSP0/CPU0:ASR9901-1#show run router static
Tue Feb 7 19:24:42.730 UTC
router static
vrf ORANGE
address-family ipv4 unicast
172.16.20.0/24 192.168.10.2
ASR9901-2
RP/0/RSP0/CPU0:ASR9901-2#show run int gi0/0/0/0
Wed Oct 19 15:40:18.599 UTC
interface GigabitEthernet0/0/0/0
cdp
vrf ORANGE
ipv4 address 192.168.10.2 255.255.255.0
!
RP/0/RSP0/CPU0:ASR9901-2#show run int gi0/0/0/6
Wed Oct 19 15:41:08.593 UTC
interface GigabitEthernet0/0/0/6
cdp
ipv4 address 172.16.20.1 255.255.255.0
!
CISCO2911-3
CISCO2911-3#show run interface gigabitEthernet0/1
Building configuration...
Current configuration : 100 bytes
!
interface GigabitEthernet0/0
ip address 172.16.20.2 255.255.255.0
duplex auto
speed auto
end
CISCO2911-3#show run | section ip route
ip route 192.168.10.0 255.255.255.0 172.16.20.1
Test connectivity with ping, for example, ASR9901-1 can ping ASR9901-2 on VRF ORANGE.
RP/0/RSP0/CPU0:ASR9901-1#ping vrf ORANGE 192.168.10.2
Wed Oct 19 15:57:50.548 UTC
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
ASR9901-2 can ping CISCO2911-3 on default vrf (GRT).
RP/0/RSP0/CPU0:ASR9901-2#ping 172.16.20.2
Wed Oct 19 15:58:05.961 UTC
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.20.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
If you try to test the reachability from subnet 192.168.10.0/24 on ASR9K-1 (VRF ORANGE) to subnet 172.16.20.0/24 located on router 2911, this test must fail as no configuration has been implemented on ASR9K-2 to complete the connectivity between VRF ORANGE and the GRT.
RP/0/RSP0/CPU0:ASR9901-1#ping 172.16.20.2 vrf ORANGE
Wed Oct 19 19:45:11.801 UTC
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.20.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Configuration
Step1. Configure a BGP process in ASR9K-2, this is the router that performs the route leak and where the configuration needs to be applied. Besides the creation of the BGP process, you need to use some network statements to make sure that the prefixes that you plan to leak get installed in the corresponding BGP table:
RP/0/RSP0/CPU0:ASR9901-2#show run router bgp
Wed Oct 19 20:21:55.118 UTC
router bgp 100
bgp router-id 10.10.10.10
address-family ipv4 unicast
network 172.16.20.0/24
!
address-family vpnv4 unicast
!
vrf ORANGE
rd 100:100
address-family ipv4 unicast
network 192.168.10.0/24
!
!
!
RP/0/RSP0/CPU0:ASR9901-2#
As you can see, there is no need to create any BGP neighborship, BGP is needed to place these prefixes into the BGP table.
Step 2. Configure the route policies, these policies are intended to help you filter which prefixes are permitted to be leaked. In this example, the route-policy GLOBAL-2-VRF and route-policy VRF-2-GLOBAL are used.
RP/0/RSP0/CPU0:ASR9901-2#show run route-policy GLOBAL-2-VRF
Wed Oct 19 20:37:56.548 UTC
route-policy GLOBAL-2-VRF
if destination in (172.16.20.0/24) then
pass
endif
end-policy
!
RP/0/RSP0/CPU0:ASR9901-2#show run route-policy VRF-2-GLOBAL
Wed Oct 19 20:38:10.538 UTC
route-policy VRF-2-GLOBAL
if destination in (192.168.10.0/24 le 32) then
pass
endif
end-policy
!
RP/0/RSP0/CPU0:ASR9901-2#
Step 3. Configure the VRF and apply the route-policy created at the previous step with the commands import from default-vrf route-policy <policy name> and export to default-vrf route-policy <policy name> as shown in the next output:
RP/0/RSP0/CPU0:ASR9901-2#show run vrf ORANGE
Wed Oct 19 20:40:38.851 UTC
vrf ORANGE
address-family ipv4 unicast
import from default-vrf route-policy GLOBAL-2-VRF
import route-target
100:100
!
export to default-vrf route-policy VRF-2-GLOBAL
export route-target
100:100
!
!
!
RP/0/RSP0/CPU0:ASR9901-2#
Final Verification
Once the previous configuration has been committed, you can verify the reachability from subnet 192.168.10.0/24 on ASR9K-1 (VRF ORANGE) to subnet 172.16.20.0/24 located on router 2911, which initially failed. However, with the appropriate configuration, this ping test is now successful:
RP/0/RSP0/CPU0:ASR9901-1#ping 172.16.20.2 vrf ORANGE
Wed Oct 19 22:07:47.897 UTC
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.20.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
RP/0/RSP0/CPU0:ASR9901-1#
A debug ip icmp configured on the router 2911 can also help to verify if the router send the echo reply back to ASR9K-1:
CISCO2911-3#debug ip icmp
ICMP packet debugging is on
CISCO2911-3#
CISCO2911-3#
*Oct 19 21:34:20.069: ICMP: echo reply sent, src 172.16.20.2, dst 192.168.10.1, topology BASE, dscp 0 topoid 0
*Oct 19 21:34:20.073: ICMP: echo reply sent, src 172.16.20.2, dst 192.168.10.1, topology BASE, dscp 0 topoid 0
*Oct 19 21:34:20.077: ICMP: echo reply sent, src 172.16.20.2, dst 192.168.10.1, topology BASE, dscp 0 topoid 0
*Oct 19 21:34:20.077: ICMP: echo reply sent, src 172.16.20.2, dst 192.168.10.1, topology BASE, dscp 0 topoid 0
*Oct 19 21:34:20.081: ICMP: echo reply sent, src 172.16.20.2, dst 192.168.10.1, topology BASE, dscp 0 topoid 0
CISCO2911-3#
Another verification is to check if the prefixes appear in the RIB and BGP tables, for this example, the GRT or default-vrf shows the next information:
RP/0/RSP0/CPU0:ASR9901-2#show route
Wed Oct 19 22:15:03.930 UTC
Codes: C - connected, S - static, R - RIP, B - BGP, (>) - Diversion path
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - ISIS, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, su - IS-IS summary null, * - candidate default
U - per-user static route, o - ODR, L - local, G - DAGR, l - LISP
A - access/subscriber, a - Application route
M - mobile route, r - RPL, t - Traffic Engineering, (!) - FRR Backup path
Gateway of last resort is not set
C 10.88.174.0/24 is directly connected, 1d20h, MgmtEth0/RSP0/CPU0/0
L 10.88.174.223/32 is directly connected, 1d20h, MgmtEth0/RSP0/CPU0/0
L 10.10.10.10/32 is directly connected, 04:33:44, Loopback100
C 172.16.20.0/24 is directly connected, 07:03:18, GigabitEthernet0/0/0/6
L 172.16.20.1/32 is directly connected, 07:03:18, GigabitEthernet0/0/0/6
B 192.168.10.0/24 is directly connected, 03:02:21, GigabitEthernet0/0/0/0 (nexthop in vrf ORANGE)
RP/0/RSP0/CPU0:ASR9901-2#
RP/0/RSP0/CPU0:ASR9901-2#show ip bgp
Wed Oct 19 22:15:13.069 UTC
BGP router identifier 10.10.10.10, local AS number 100
BGP generic scan interval 60 secs
Non-stop routing is enabled
BGP table state: Active
Table ID: 0xe0000000 RD version: 5
BGP main routing table version 5
BGP NSR Initial initsync version 3 (Reached)
BGP NSR/ISSU Sync-Group versions 0/0
BGP scan interval 60 secs
Status codes: s suppressed, d damped, h history, * valid, > best
i - internal, r RIB-failure, S stale, N Nexthop-discard
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 172.16.20.0/24 0.0.0.0 0 32768 i
*> 192.168.10.0/24 0.0.0.0 0 32768 i
Processed 2 prefixes, 2 paths
RP/0/RSP0/CPU0:ASR9901-2#
Now, the next output shows the information displayed for the VRF ORANGE:
RP/0/RSP0/CPU0:ASR9901-2#show route vrf ORANGE
Wed Oct 19 22:21:24.559 UTC
Codes: C - connected, S - static, R - RIP, B - BGP, (>) - Diversion path
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - ISIS, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, su - IS-IS summary null, * - candidate default
U - per-user static route, o - ODR, L - local, G - DAGR, l - LISP
A - access/subscriber, a - Application route
M - mobile route, r - RPL, t - Traffic Engineering, (!) - FRR Backup path
Gateway of last resort is not set
B 172.16.20.0/24 is directly connected, 01:43:49, GigabitEthernet0/0/0/6 (nexthop in vrf default)
C 192.168.10.0/24 is directly connected, 07:06:38, GigabitEthernet0/0/0/0
L 192.168.10.2/32 is directly connected, 07:06:38, GigabitEthernet0/0/0/0
RP/0/RSP0/CPU0:ASR9901-2#
RP/0/RSP0/CPU0:ASR9901-2#
RP/0/RSP0/CPU0:ASR9901-2#show bgp vrf ORANGE
Wed Oct 19 22:21:34.887 UTC
BGP VRF ORANGE, state: Active
BGP Route Distinguisher: 100:100
VRF ID: 0x60000003
BGP router identifier 10.10.10.10, local AS number 100
Non-stop routing is enabled
BGP table state: Active
Table ID: 0xe0000012 RD version: 9
BGP main routing table version 9
BGP NSR Initial initsync version 4 (Reached)
BGP NSR/ISSU Sync-Group versions 0/0
Status codes: s suppressed, d damped, h history, * valid, > best
i - internal, r RIB-failure, S stale, N Nexthop-discard
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 100:100 (default for vrf ORANGE)
*> 172.16.20.0/24 0.0.0.0 0 32768 i
*> 192.168.10.0/24 0.0.0.0 0 32768 i
Processed 2 prefixes, 2 paths


 Feedback
Feedback