Field Notice: FN - 72481 - Cisco SD-WAN Controllers Are Incompatible with Public TLS/SSL X.509 Certificates Signed After September 1, 2022 - Workaround Provided
Available Languages
Notice
THIS FIELD NOTICE IS PROVIDED ON AN "AS IS" BASIS AND DOES NOT IMPLY ANY KIND OF GUARANTEE OR WARRANTY, INCLUDING THE WARRANTY OF MERCHANTABILITY. YOUR USE OF THE INFORMATION ON THE FIELD NOTICE OR MATERIALS LINKED FROM THE FIELD NOTICE IS AT YOUR OWN RISK. CISCO RESERVES THE RIGHT TO CHANGE OR UPDATE THIS FIELD NOTICE AT ANY TIME.
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
26-Sep-22 |
Initial Release |
Products Affected
| Affected OS Type | Affected Software Product | Affected Release | Affected Release Number | Comments |
|---|---|---|---|---|
NON-IOS |
SD-WAN Software Update |
17.2 |
17.2.4, 17.2.5, 17.2.6, 17.2.7, 17.2.8, 17.2.9, 17.2.10 |
|
NON-IOS |
SD-WAN Software Update |
18.3 |
18.3.0, 18.3.1, 18.3.3, 18.3.3.1, 18.3.4, 18.3.5, 18.3.6, 18.3.7, 18.3.8 |
|
NON-IOS |
SD-WAN Software Update |
18.4 |
18.4.0, 18.4.1, 18.4.3, 18.4.4, 18.4.5, 18.4.6 |
|
NON-IOS |
SD-WAN Software Update |
19 |
19.2.0 |
|
NON-IOS |
SD-WAN Software Update |
19.0 |
19.0.0 |
|
NON-IOS |
SD-WAN Software Update |
19.2 |
19.2.1, 19.2.2, 19.2.3, 19.2.4, 19.2.31, 19.2.32 |
|
NON-IOS |
SD-WAN Software Update |
19.3 |
19.3.0 |
|
NON-IOS |
SD-WAN Software Update |
20.1 |
20.1.1, 20.1.1.1, 20.1.2, 20.1.3, 20.1.12 |
|
NON-IOS |
SD-WAN Software Update |
20.3 |
20.3.1, 20.3.2, 20.3.2.1, 20.3.3, 20.3.3.1, 20.3.4, 20.3.4.1, 20.3.4.2, 20.3.5 |
|
NON-IOS |
SD-WAN Software Update |
20.4 |
20.4.1, 20.4.1.1, 20.4.1.2, 20.4.2, 20.4.2.1, 20.4.2.2 |
|
NON-IOS |
SD-WAN Software Update |
20.5 |
20.5.1, 20.5.1.1, 20.5.1.2 |
|
NON-IOS |
SD-WAN Software Update |
20.6 |
20.6.1, 20.6.1.1, 20.6.2, 20.6.2.1, 20.6.2.2, 20.6.3, 20.6.3.1 |
|
NON-IOS |
SD-WAN Software Update |
20.7 |
20.7.1, 20.7.1.1, 20.7.2 |
|
NON-IOS |
SD-WAN Software Update |
20.8 |
20.8.1 |
Defect Information
| Defect ID | Headline |
|---|---|
| CSCwc67625 | OU field is deprecated from CA/B Forum Certificate Authorities |
Problem Description
Beginning September 1, 2022, Cisco SD-WAN controllers (vManage, vBond, and vSmart) are not compatible with public X.509 Transport Layer Security/Secure Sockets Layer (TLS/SSL) controller certificates that conform to the Certification Authority Browser Forum (CA/Browser Forum) Ballot SC47 Organizational Unit (OU) standard. These public TLS/SSL certificates no longer contain the OU field that Cisco SD-WAN requires and they cannot be successfully installed. Without a valid controller certificate all Cisco SD-WAN control connections fail.
This problem only affects Cisco SD-WAN deployments configured to use Enterprise Certificates (that is, the vManage "Controller Certificate Authorization" mode is set to "Enterprise Root Certificate"), where the controller certificate is a public trust TLS/SSL certificate issued by a CA/Browser Forum conforming CA on or after September 1, 2022.
Background
The CA/Browser Forum is a working group of public CAs and browser software vendors. The CA/Browser Forum sets industry standards for public trust model X.509 certificates used by public websites, browsers, and other public facing web services. In June 2021, the CA/Browser Forum voted to revise their standards to include a new rule. The new rule requires removal of the OU field from all public trust TLS/SSL certificates issued on or after September 1, 2022. Public TLS/SSL certificates issued by a CA/Browser Forum conforming CA on or after that date will no longer include the OU field. Depending on the particular CA, certificate signing requests (CSRs) that include the OU field will either be rejected by the CA or have the OU field removed when the certificate is issued.
Cisco SD-WAN currently uses the OU field in the controller certificate and it is a required field. The OU field is used to match the Organization Name of the overlay network when a new SD-WAN device is authenticated to join.
Problem Symptom
Some CAs will not accept a CSR for a public TLS/SSL certificate if the CSR contains an OU field. The CSR generation step will complete successfully in Cisco vManage, but the resulting CSR will be rejected by those CAs when it is submitted.
Other CAs will accept the CSR generated by Cisco vManage, but will silently remove the OU field from the signed TLS/SSL certificate that is issued. Once the resulting certificate is downloaded and installed, Cisco vManage will report an error in the log:
System organization name [overlay name] does not match with cert subject's OU [].
where "overlay name" is replaced by the unique overlay name Cisco vManage used to generate the certificate CSR.
Workaround/Solution
There is no software solution for this problem. If your Cisco SD-WAN instance is affected and you need a new or renewed public TLS/SSL controller certificate after September 1, 2022, there are three workaround options available:
1. Request an exception
Some CAs might have an exception process available (for a limited time) that allows you to request a public TLS/SSL certificate that includes the OU field. Contact your CA account representative to see if this option is available to you.
2. Switch to a private trust model Enterprise Certificate
Private TLS/SSL certificates are not required to conform to all CA/Browser Forum requirements and can continue to be signed with the OU field. Choose a public CA or your own internal CA that provides private trust model signing services with the ability to include the OU field in TLS/SSL certificates.
3. Switch from Enterprise Certificates to Cisco Systems private TLS/SSL certificates
Private TLS/SSL certificates issued by Cisco Systems public key infrastructure (PKI) do include the OU field and are not impacted by the CA/Browser Forum requirements change. Consult the Cisco SD-WAN Controller Certificates and Authorized Serial Number File Prescriptive Deployment Guide for detailed instructions on how to configure and install Cisco Systems private TLS/SSL certificates.
Note: Before you migrate from Enterprise Certificates to Cisco Systems private certificates, ensure that the Cisco root CA bundle is installed on each edge node.
How To Identify Affected Products
This problem only affects Cisco SD-WAN deployments configured to use Enterprise Certificates where the controller certificate is a public trust TLS/SSL certificate issued by a CA/Browser Forum conforming CA. In order to determine if your Cisco SD-WAN controller is affected, navigate to the Administration > Settings > Controller Certificate Authorization window on the Cisco vManage user interface. Verify that your controller is configured to use "Enterprise Root Certificate" as shown in this example.
Note: If your controller is configured to use one of the other certificate sources then your controller is NOT affected by this problem.
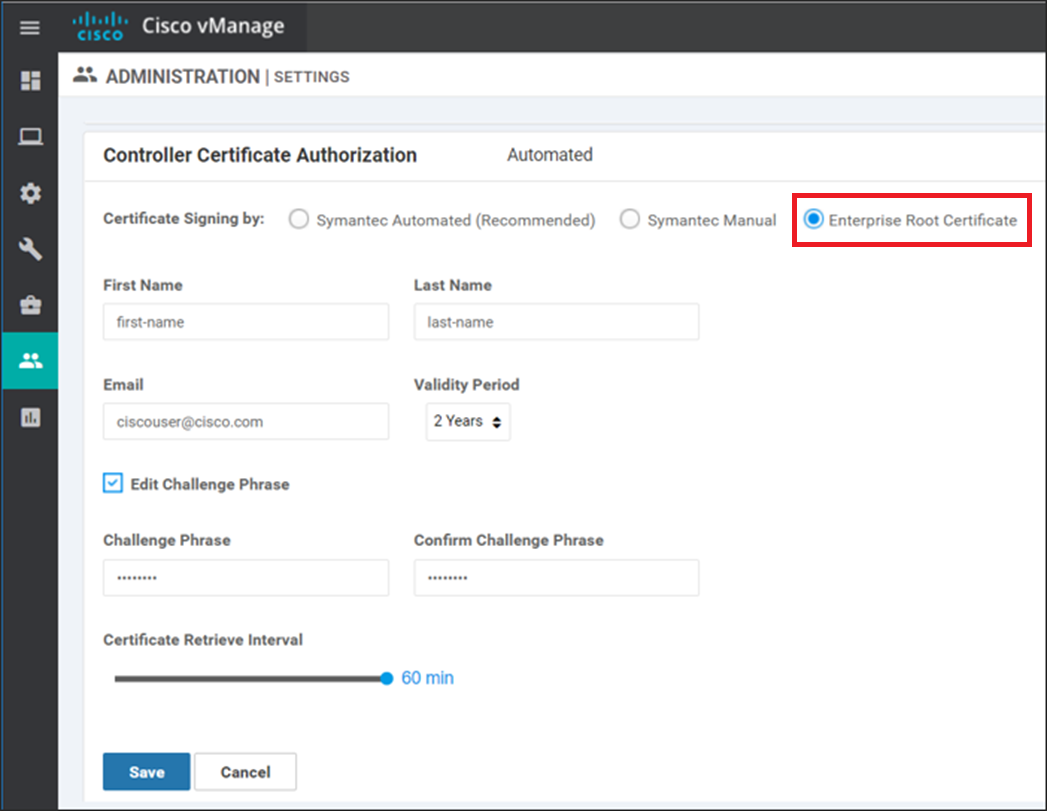
Next, use the controller CLI command show certificate installed | include Issuer to display the CA that signed the controller certificate. Identify the issuer in the CLI output and verify that the issuer is a CA/Browser Forum conforming CA that is configured for public trust model. If it uses a public trust model then your controller IS affected. If it does not use a public trust model then your controller is NOT affected.
These examples show CLI output for controller certificates issued by CAs commonly used for Cisco SD-WAN deployments. These commonly used certificate signing sources use a private trust model and thus are not affected by this problem. If your CLI output matches any of these examples, your Cisco SD-WAN controller is not affected.
Controller1# show certificate installed | include Issuer
Issuer: O=Cisco, OU=Albireo, CN=Viptela SubCA
Controller2# show certificate installed | include Issuer
Issuer: CN = Symantec Class 3 Secure Server CA - G4,OU = Symantec Trust Network,O = Symantec Corporation,C = US
Controller3# show certificate installed | include Issuer
Issuer: C=US, O=Symantec Corporation, CN=Symantec Private SSL SHA256 CA
Controller4# show certificate installed | include Issuer
Issuer: CN = DigiCert Private SSL SHA256 CA - G2,O = DigiCert Inc.,C = US
For More Information
If you require further assistance, or if you have any further questions regarding this field notice, please contact the Cisco Systems Technical Assistance Center (TAC) by one of the following methods:
Receive Email Notification For New Field Notices
My Notifications—Set up a profile to receive email updates about reliability, safety, network security, and end-of-sale issues for the Cisco products you specify.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
This Document Applies to These Products
Unleash the Power of TAC's Virtual Assistance
 Feedback
Feedback