Introduction
This document describes the steps needed to remove the dependency of Microsoft Active Directory (AD) in order to manage authorization locally in Package Contact Center Enterprise (PCCE) components.
Contributed by Meenakshi Sundaram, Ramiro Amaya, and Anuj Bhatia, Cisco TAC Engineers.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Cisco Package Contact Center Enterprise
- Microsoft Active Directory
Components Used
The information used in the document is based on PCCE 12.5(1) version.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any step.
Background Information
The PCCE 12.5 release provides user privileges to local user groups on the Administration Servers (AW), which allows users to move authorization out of Active Directory (AD). This is controlled by the registry ADSecurityGroupUpdate which by default is enabled and avoids the use of Microsoft AD Security Groups to control user access rights to perform setup and configuration tasks.
Note: The support for Local Authorization started in Unified Contact Center Enterprise (UCCE) 12.0 and it is now supported in PCCE 12.5.

Note: If business needs to have the prior behaviour implemented (AD authorization), the ADSecurityGroupUpdate flag can be changed to 1.
Configure
To Grant UcceConfig group permissions in a local AW server, first, permissions need to be provided at the registry level, and second, to the folder level.
Step 1. Configure Registry Permissions.
1. Run the regedit.exe utility.
2. Select HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\WinSock2.
3. In Permissions under security tab Select UcceConfig group and check Allow for the Full Control option.
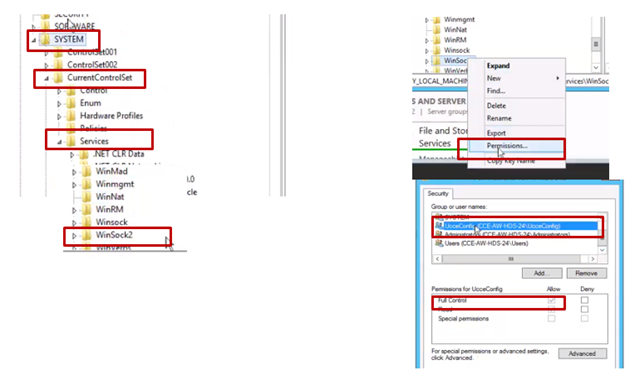
4. Repeat the previous steps to grant full control to the UcceConfig group for these registries.
- Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Cisco Systems, inc.\ICM
- Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Cisco Systems, inc.\ICM
Step 2. Configure Folder Permissions.
1. In Windows Explorer, navigate to <ICM Installed Directory>:\icm and select Properties.
2. In Security tab, select UcceConfig and check Allow for the Full Control option.

3. Select OK to save the changes.
4. Repeat the previous steps to grant full control to the UcceConfig group for C:\Temp folder.
5. In SQL Management Studio, do this:
a) Navigate to Security > Logins.
b) Locate <Machine name>\UcceConfig.
c) Right-click and select properties.
d) Navigate User Mappings and select the AWDB database.
e) Tick the GeoTelAdmin, GeoTelGroup and public check boxes.
f) Repeat step d) for the Historical Data (HDS) database.

As preliminary configuration has been achieved, follow the steps of how you can promote a domain user in order to have configuration and setup rights.
Step 3. Domain User Configuration.
1. Create a domain user in AD. For this excercise testconfig1 user was created.
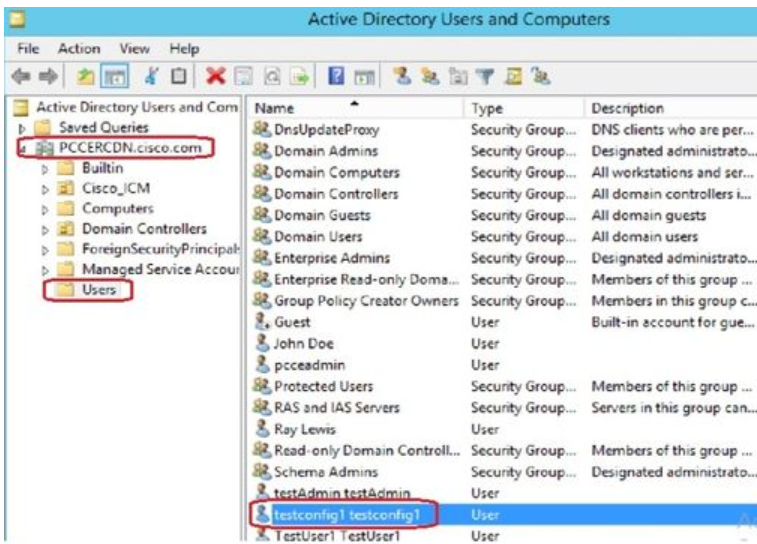

 2. Log in to the AW server with a domain admin or local admin account.
2. Log in to the AW server with a domain admin or local admin account.
3. Open the CCE Admin on the AW. Navigate to the User Setup card, and select Administrators. Add the user and select the role ConfigAdmin.
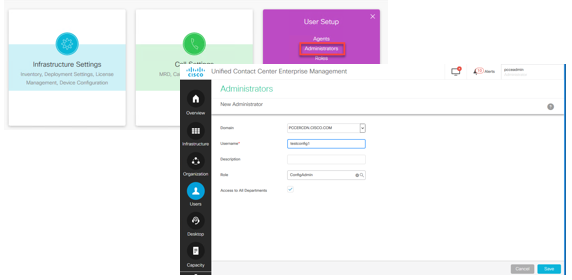
Prior to 12.5 version of PCCE this change would have updated the Config security groups in the domain under an instance Organizational Unit (OU), but with 12.5 the default behaviour is no to add that user to the AD group. As shown in the image, there is no update of this user in the domain ICM Config security group.

4. In the AW Server under computer management > Local Users and Groups > Groups select UcceConfig and add testconfig1 user into it.
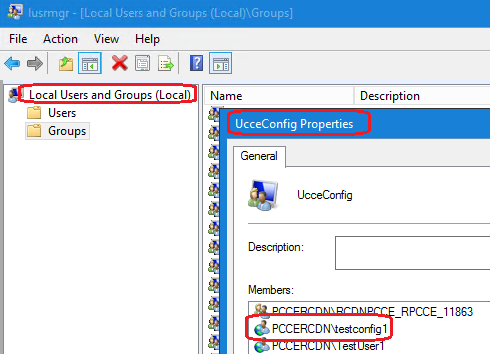
5. Log out from the machine and log in with the credentials of testconfig1 user. As this user has configuration rights, he is able to run CCE configuration tools such as the CCE Admin, Script or Internet Script Editor.
6. However, If the user tries to run any task which require setup rights, it fails. This user does not have access to all the CCE Admin resources or setup tools.
As show in the image, testconfig1 user in PCCE 4K deployment attempts to run the Peripheral Gateway (PG) configuration and the system restricts the change with a warning message.

7. If business requires this user to have setup rights along with config, then you have to ensure the user role is changed to SystemAdmin in CCEAdmin.
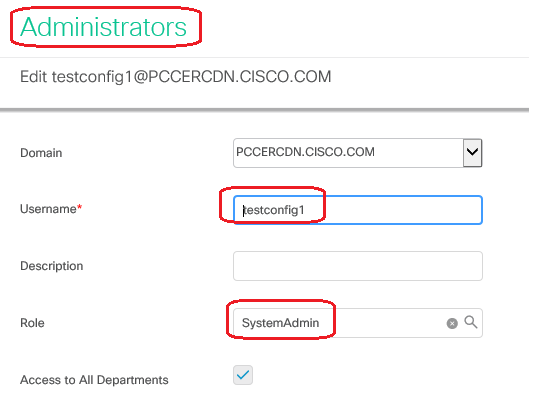
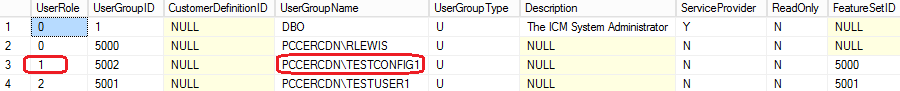
User role has been updated as 1 (SystemAdmin) in the database:
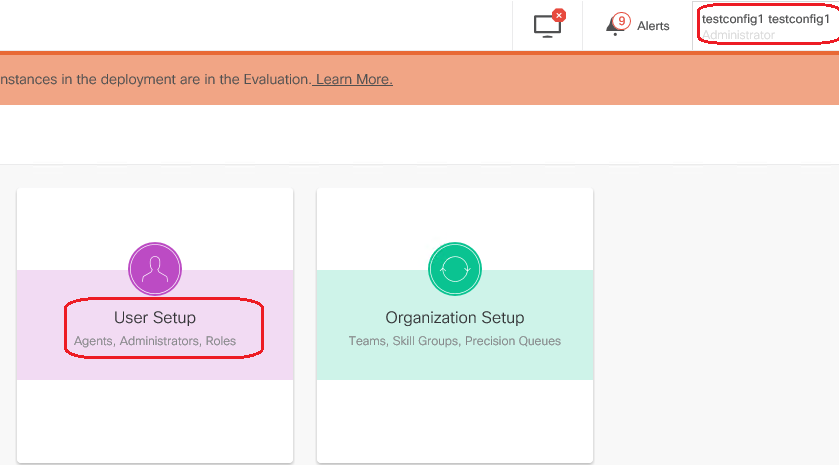
8. Log in to the AW server with the domain or local admin rights account and via computer management > Local Users and Groups > groups select Groups and in Administrators add the user to the user.

10. The user is now able to access all the resources of CCE application in that AW server and make desired changes.
Verify
The verification procedure is actually part of the configuration process.
Troubleshoot
There is currently no specific steps available to troubleshoot this configuration.
Related Information
PCCE Administration guide
Technical Support & Documentation - Cisco Systems
