Konfigurieren von VRF-Leaks auf IOS XE
Download-Optionen
-
ePub (165.4 KB)
In verschiedenen Apps auf iPhone, iPad, Android, Sony Reader oder Windows Phone anzeigen
Inklusive Sprache
In dem Dokumentationssatz für dieses Produkt wird die Verwendung inklusiver Sprache angestrebt. Für die Zwecke dieses Dokumentationssatzes wird Sprache als „inklusiv“ verstanden, wenn sie keine Diskriminierung aufgrund von Alter, körperlicher und/oder geistiger Behinderung, Geschlechtszugehörigkeit und -identität, ethnischer Identität, sexueller Orientierung, sozioökonomischem Status und Intersektionalität impliziert. Dennoch können in der Dokumentation stilistische Abweichungen von diesem Bemühen auftreten, wenn Text verwendet wird, der in Benutzeroberflächen der Produktsoftware fest codiert ist, auf RFP-Dokumentation basiert oder von einem genannten Drittanbieterprodukt verwendet wird. Hier erfahren Sie mehr darüber, wie Cisco inklusive Sprache verwendet.
Informationen zu dieser Übersetzung
Cisco hat dieses Dokument maschinell übersetzen und von einem menschlichen Übersetzer editieren und korrigieren lassen, um unseren Benutzern auf der ganzen Welt Support-Inhalte in ihrer eigenen Sprache zu bieten. Bitte beachten Sie, dass selbst die beste maschinelle Übersetzung nicht so genau ist wie eine von einem professionellen Übersetzer angefertigte. Cisco Systems, Inc. übernimmt keine Haftung für die Richtigkeit dieser Übersetzungen und empfiehlt, immer das englische Originaldokument (siehe bereitgestellter Link) heranzuziehen.
Inhalt
Einleitung
In diesem Dokument werden häufige Methoden zum Versickern von VRF-Routen (Virtual Routing and Forwarding) beschrieben und entsprechende Beispielkonfigurationen bereitgestellt.
Voraussetzungen
Anforderungen
Cisco empfiehlt, dass Sie über Kenntnisse in folgenden Bereichen verfügen:
- Border Gateway Protocol (BGP)
- Neuverteilung des Routing-Protokolls
- VRF
- Cisco IOS® XE Software
Weitere Informationen zu diesen Themen finden Sie unter:
Weiterverteilung von Routing-Protokollen
Gegenseitige Neuverteilung zwischen EIGRP und BGP - Konfigurationsbeispiel
Analyse der Neuverteilung von OSPF-Routen in das BGP
Verwendete Komponenten
Die Informationen in diesem Dokument basieren auf Routern mit Cisco IOS® XE Versionen 16.12.X und 17.X.
Die Informationen in diesem Dokument beziehen sich auf Geräte in einer speziell eingerichteten Testumgebung. Alle Geräte, die in diesem Dokument benutzt wurden, begannen mit einer gelöschten (Nichterfüllungs) Konfiguration. Wenn Ihr Netzwerk in Betrieb ist, stellen Sie sicher, dass Sie die möglichen Auswirkungen aller Befehle kennen.
Hintergrundinformationen
Mit VRF kann ein Router separate Routing-Tabellen für verschiedene virtuelle Netzwerke verwalten. Wenn Ausnahmen erforderlich sind, ermöglicht das VRF-Route-Leaking das Routing eines Teils des Datenverkehrs zwischen den VRF-Instanzen ohne die Verwendung statischer Routen.
Szenario 1 - VRF-Route-Leak zwischen BGP und IGP ( EIGRP )
Szenario 1 zeigt ein Beispiel für ein VRF-Route-Leaking zwischen BGP und EIGRP. Diese Methode kann für andere IGPs verwendet werden.
Netzwerkdiagramm
Das Netzwerkdiagramm in Abbildung 1 zeigt die Layer-3-Topologie, in der ein Route Leaking erforderlich ist.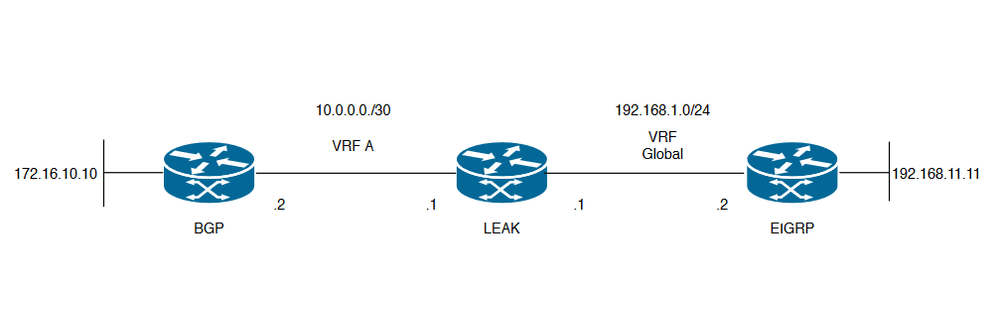
Image 1. Route Leaking-Topologie für Szenario 1
Router LEAK hat eine BGP-Nachbarschaft zu einem Nachbarn in VRF A und einen EIGRP-Nachbarn in der globalen VRF-Instanz. Gerät 192.168.11.11 muss in der Lage sein, eine Verbindung zu Gerät 172.16.10.10 im Netzwerk herzustellen.
Router-LEAK kann zwischen den beiden Routen nicht routen, da sich die Routen in unterschiedlichen VRFs befinden. Diese Routing-Tabellen zeigen die aktuellen Routen pro VRF und geben an, welche Routen zwischen der globalen VRF-Instanz und VRF-A geleakt werden müssen.
LEAK Routing-Tabellen:
| EIGRP-Routing-Tabelle (globales Routing) |
LEAK#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, GigabitEthernet2
L 192.168.1.1/32 is directly connected, GigabitEthernet2
192.168.11.0/32 is subnetted, 1 subnets
D 192.168.11.11 [90/130816] via 192.168.1.2, 02:30:29, GigabitEthernet2 >> Route to be exchange to the VRF A routing table.
| VRF-A-Routing-Tabelle |
LEAK#show ip route vrf A
Routing Table: A
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/30 is directly connected, GigabitEthernet1
L 10.0.0.1/32 is directly connected, GigabitEthernet1
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [200/0] via 10.0.0.2, 01:47:58 >> Route to be exchange to the global routing table.
Konfigurieren
Führen Sie die folgenden Schritte aus, um ein Leck zwischen den beiden Routing-Tabellen zu erzeugen:
Step 1.
Create route-maps to filter the routes to be injected in both routing tables.
LEAK(config)#Route-map VRF_TO_EIGRP
LEAK(config-route-map)#match ip address prefix-list VRF_TO_EIGRP
LEAK(config-route-map)#exit
!
Prefix-list created to match the host that is attached to the previous route-map configured.
!
ip prefix-list VRF_TO_EIGRP permit 172.16.10.10/32
or
LEAK(config)#Route-map VRF_TO_EIGRP
LEAK(config-route-map)# match ip address 10
LEAK(config-route-map)#exit
!
ACL created to match the host that is attached to the previous route-map.
!
LEAK#show ip access-lists 10
10 permit 172.16.10.10
LEAK(config)#Route-map EIGRP_TO_VRF
LEAK(config-route-map)#match ip address prefix-list EIGRP_TO_VRF
LEAK(config-route-map)#exit
LEAK(config)#
!
Prefix-list created to match the host that is attached to the previous route-map configured.
!
ip prefix-list EIGRP_TO_VRF permit 192.168.11.11/32
or
LEAK(config)#Route-map EIGRP_TO_VRF
LEAK(config-route-map)#match ip address 20
LEAK(config-route-map)#exit
LEAK(config)#
!
ACL created to match the host that is attached to the previous route-map.
!
LEAK#show ip access-list 20
10 permit 192.168.11.11
Step 2.
Define the import/export maps and add the route-map names.
LEAK(config)#vrf definition A
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#import ipv4 unicast map EIGRP_TO_VRF >> Import the global routing table routes at the VRF routing table.
LEAK(config-vrf-af)#export ipv4 unicast map VRF_TO_EIGRP >> Export the VRF routes to the Global Routing Table.
LEAK(config-vrf-af)#end
Step 3.
Proceed with the dual redistribution.
Redistribute EIGRP
LEAK(config)#router bgp 1
LEAK(config-router)#redistribute eigrp 1
LEAK(config-router)#end
Redistribution BGP
LEAK(config)#router eigrp 1
LEAK(config-router)#redistribute bgp 1 metric 100 1 255 1 1500
LEAK(config-router)#end
Überprüfung
Routing table from VRF A
LEAK#show ip route vrf A
Routing Table: A
< Snip for resume >
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/30 is directly connected, GigabitEthernet1
L 10.0.0.1/32 is directly connected, GigabitEthernet1
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [200/0] via 10.0.0.2, 00:58:53
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
B 192.168.1.0/24 is directly connected, 00:01:00, GigabitEthernet2
L 192.168.1.1/32 is directly connected, GigabitEthernet2
192.168.11.0/32 is subnetted, 1 subnets
B 192.168.11.11 [20/130816] via 192.168.1.2, 00:01:00, GigabitEthernet2 >> Route from global routing table at VRF A routing table.
Global Routing Table (EIGRP)
LEAK#show ip route
< snip for resume >
Gateway of last resort is not set
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [200/0] via 10.0.0.2 (A), 00:04:47 >> Route from VRF A at global routing table.
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, GigabitEthernet2
L 192.168.1.1/32 is directly connected, GigabitEthernet2
192.168.11.0/32 is subnetted, 1 subnets
D 192.168.11.11 [90/130816] via 192.168.1.2, 01:03:35, GigabitEthernet2
LEAK#
Szenario 2 - VRF-Leaking zwischen VRF A und VRF B
Szenario 2 beschreibt das Leck zwischen zwei verschiedenen VRFs.
Netzwerkdiagramm
In diesem Dokument wird diese Netzwerkeinrichtung verwendet:
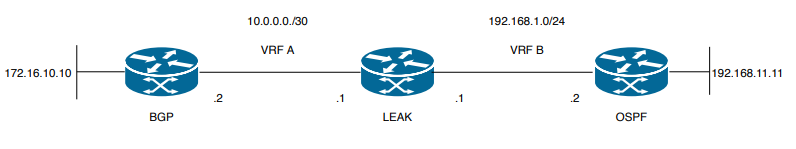
Image 2. Route Leaking-Topologie für Szenario 2
Router LEAK hat eine BGP-Nachbarschaft zu einem Nachbarn in VRF A und einen OSPF-Nachbarn in VRF B. Gerät 192.168.11.11 muss eine Verbindung zu Gerät 172.16.10.10 im Netzwerk herstellen.
Router-LEAK kann zwischen den beiden Routen nicht routen, da sich die Routen in unterschiedlichen VRFs befinden. Diese Routing-Tabellen zeigen die aktuellen Routen pro VRF und geben an, welche Routen zwischen VRF A und VRF B durchlaufen werden müssen.
LEAK-Routing-Tabelle:
| VRF-A-Routing-Tabelle |
LEAK#show ip route vrf A
Routing Table: A
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/30 is directly connected, Ethernet0/0
L 10.0.0.2/32 is directly connected, Ethernet0/0
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [200/0] via 10.0.0.1, 00:03:08 >> Route to be exchange to routing table VRF B.
| VRF-B-Routing-Tabelle |
LEAK#show ip route vrf B
Routing Table: B
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Ethernet0/1
L 192.168.1.2/32 is directly connected, Ethernet0/1
192.168.11.0/32 is subnetted, 1 subnets
O 192.168.11.11 [110/11] via 192.168.1.1, 00:58:45, Ethernet0/1 >> Route to be exchange to routing table VRF A.
Konfigurieren
Gehen Sie wie folgt vor, um ein Leck zwischen den beiden Routing-Tabellen zu erzeugen:
Step 1.
Create route-maps to filter the routes to be injected in both routing tables.
LEAK(config)#Route-map VRFA_TO_VRFB
LEAK(config-route-map)#match ip address prefix-list VRFA_TO_VRFB
LEAK(config-route-map)#exit
!
Prefix-list created to match the host and IP segment that is attached to the previous route-map configured.
!
ip prefix-list VRFA_TO_VRFB permit 172.16.10.10/32
ip prefix-list VRFA_TO_VRFB permit 10.0.0.0/30
or
LEAK(config)#Route-map VRFA_TO_VRFB
LEAK(config-route-map)#match ip address 10
LEAK(config-route-map)#exit
!
ACL created to match the host and IP segment that is attached to the previous route-map.
!
LEAK#show ip access-lists 10
10 permit 172.16.10.10
20 permit 10.0.0.0
LEAK(config)#Route-map VRFB_TO_VRFA
LEAK(config-route-map)#match ip address prefix-list VRFB_TO_VRFA
LEAK(config-route-map)#exit
!
Prefix-list created to match the host and IP segment that is attached to the previous route-map configured.
!
ip prefix-list VRFB_TO_VRFA permit 192.168.11.11/32
ip prefix-list VRFB_TO_VRFA permit 192.168.1.0/24
or
LEAK(config)#Route-map VRFB_TO_VRFA
LEAK(config-route-map)#match ip address 20
LEAK(config-route-map)#exit
!
ACL created to match the host and IP segment that is attached to the previous route-map configured.
!
LEAK#show ip access-lists 20
10 permit 192.168.11.11
20 permit 192.168.1.0
Step 2.
At the VRFs configure the import/export map, use the route-map names to leak the routes.
LEAK(config)#vrf definition A
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#export map VRFA_TO_VRFB
LEAK(config-vrf-af)#import map VRFB_TO_VRFA
LEAK(config)#vrf definition B
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#export map VRFB_TO_VRFA
LEAK(config-vrf-af)#import map VRFA_TO_VRFB
Step 3.
Add the route-target to import and export the route distinguisher from both VRFs.
! --- Current configuration for VRF A
vrf definition A
rd 1:2
!
address-family ipv4
route-target export 1:2
route-target import 1:1
exit-address-family
! --- Current configuration from VRF B
vrf definition B
rd 2:2
!
address-family ipv4
exit-address-family
! --- Import the routes from VRF B into VRF A
LEAK(config)#vrf definition A
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#route-target import 2:2
! --- Import routes from VRF A to VRF B and export routes from VRF B
LEAK(config-vrf-af)#vrf definition B
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#route-target import 1:2
LEAK(config-vrf-af)#route-target export 2:2
Überprüfung
Check the Routing Tables
VRF A Routing Table
LEAK#show ip route vrf A
Routing Table: A
< Snip for resume >
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/30 is directly connected, Ethernet0/0
L 10.0.0.2/32 is directly connected, Ethernet0/0
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [200/0] via 10.0.0.1, 00:07:20
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
B 192.168.1.0/24 is directly connected, 00:00:10, Ethernet0/1
L 192.168.1.2/32 is directly connected, Ethernet0/1
192.168.11.0/32 is subnetted, 1 subnets
B 192.168.11.11 [20/11] via 192.168.1.1 (B), 00:00:10, Ethernet0/1 >> Route from VRF B routing table at VRF A.
VRF B Routing Table
LEAK#show ip route vrf B
Routing Table: B
< Snip for resume >
10.0.0.0/30 is subnetted, 1 subnets
B 10.0.0.0 [200/0] via 10.0.0.1 (A), 00:00:15
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [200/0] via 10.0.0.1 (A), 00:00:15 >> Route from VRF A routing table at VRF B.
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Ethernet0/1
L 192.168.1.2/32 is directly connected, Ethernet0/1
192.168.11.0/32 is subnetted, 1 subnets
O 192.168.11.11 [110/11] via 192.168.1.1, 01:05:12, Ethernet0/1
Szenario 3 - VRF-Leaking zwischen OSPF (VRF) und EIGRP (Global) mit BGP (optional)
Szenario 3 beschreibt die Route Leak zwischen zwei IGPs (VRF B und Global VRF).
Netzwerkdiagramm
In diesem Dokument wird die folgende Netzwerkeinrichtung verwendet: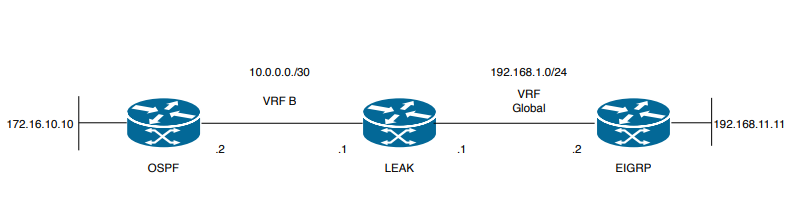
Image 3. Route Leaking-Topologie für Szenario 3
Router LEAK hat eine OSPF-Nachbarschaft zu einem Nachbarn in VRF B und einen EIGRP-Nachbarn in der globalen VRF-Instanz. Gerät 172.16.10.10 muss in der Lage sein, eine Verbindung mit Gerät 192.168.11.11 im Netzwerk herzustellen.
Router LEAK kann diese beiden Hosts nicht verbinden. Diese Routing-Tabellen zeigen die aktuellen Routen pro VRF und geben an, welche Routen zwischen VRF B und globaler VRF-Instanz weitergeleitet werden müssen.
LEAK-Routing-Tabelle:
| EIGRP-Routing-Tabelle (EIGRP) |
LEAK#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Ethernet0/1
L 192.168.1.1/32 is directly connected, Ethernet0/1
192.168.11.0/32 is subnetted, 1 subnets
D 192.168.11.11 [90/1024640] via 192.168.1.2, 01:08:38, Ethernet0/1 >> Route to be exchange from global routing table at VRF B routing table.
| VRF B-Routing-Tabelle (OSPF) |
LEAK#show ip route vrf B
Routing Table: B
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/30 is directly connected, Ethernet0/0
L 10.0.0.2/32 is directly connected, Ethernet0/0
172.16.0.0/32 is subnetted, 1 subnets
O 172.16.10.10 [110/11] via 10.0.0.1, 01:43:45, Ethernet0/0 >> Route to be exchange from routing table VRF B at global routing table.
Konfigurieren
Gehen Sie wie folgt vor, um ein Leck zwischen den beiden Routing-Tabellen zu erzeugen:
Step 1.
Create route-maps for import and export to be injected in both routing tables.
LEAK(config)#Route-map OSPF_TO_EIGRP
LEAK(config-route-map)#match ip address prefix-list OSPF_TO_EIGRP
LEAK(config-route-map)#exit
!
Prefix-list created to match the host that is attached to the previous route-map configured.
!
ip prefix-list OSPF_TO_EIGRP permit 172.16.10.10/32
ip prefix-list OSPF_TO_EIGRP permit 10.0.0.0/30
or
LEAK(config)#Route-map OSPF_TO_EIGRP
LEAK(config-route-map)#match ip address 10
LEAK(config-route-map)#exit
!
ACL created to match the host that is attached to the previous route-map.
!
LEAK#show ip access-lists 10
10 permit 172.16.10.10
20 permit 10.0.0.0
LEAK(config)#Route-map EIGRP_TO_OSPF
LEAK(config-route-map)#match ip address prefix-list EIGRP_TO_OSPF
LEAK(config-route-map)#exit
!
Prefix-list created to match the host that is attached to the previous route-map configured.
!
ip prefix-list EIGRP_TO_OSPF permit 192.168.11.11/32
ip prefix-list EIGRP_TO_OSPF permit 192.168.1.0/24
or
LEAK(config)#Route-map EIGRP_TO_OSPF
LEAK(config-route-map)#match ip address 20
LEAK(config-route-map)#exit
!
ACL created to match the host that is attached to the previous route-map.
!
LEAK#show ip access-lists 20
10 permit 192.168.11.11
20 permit 192.168.1.0/24
Step 2.
Add the import/export maps in order to match the route-map names.
Current configuration
!
vrf definition B
rd 1:2
!
address-family ipv4
exit-address-family
!
!
LEAK(config-vrf)#vrf definition B
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#import ipv4 unicast map EIGRP_TO_OSPF
LEAK(config-vrf-af)#export ipv4 unicast map OSPF_TO_EIGRP
Step 3.
To perform the leak is necessary to create a BGP process, in order to redistribute
the IGPs protocols.
router bgp 1
bgp log-neighbor-changes
!
address-family ipv4 vrf B >> Include the address-family to inject VRF B routing table (OSPF)
!
exit-address-family
Hinweis: Vergewissern Sie sich, dass für die VRF-Instanz ein Route Distinguisher konfiguriert ist, um den Fehler zu vermeiden:"%vrf B does not have rd configured, configure "rd" before configuring import route-map"
Step 4.
Create a Dual Redistribution.
IGPs redistribution.
LEAK(config-router)#router bgp 1
LEAK(config-router)#redistribute eigrp 1
!
LEAK(config-router)#address-family ipv4 vrf B
LEAK(config-router-af)#redistribute ospf 1 match internal external 1 external 2
LEAK(config-router-af)#end
BGP Redistribution
LEAK(config)#router ospf 1 vrf B
LEAK(config-router)#redistribute bgp 1
!
LEAK(config-router)#router eigrp TAC
LEAK(config-router)#
LEAK(config-router)# address-family ipv4 unicast autonomous-system 1
LEAK(config-router-af)#
LEAK(config-router-af)# topology base
LEAK(config-router-af-topology)#redistribute bgp 1 metric 100 1 255 1 1500
Überprüfung
Überprüfen der Routing-Tabellen
| Globale Routingtabelle |
LEAK#show ip route
< Snip for resume >
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [20/11] via 10.0.0.1, 00:14:48, Ethernet0/0 >> Route from VRF B routing table at global routing table ( EIGRP ).
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Ethernet0/1
L 192.168.1.1/32 is directly connected, Ethernet0/1
192.168.11.0/32 is subnetted, 1 subnets
D 192.168.11.11 [90/1024640] via 192.168.1.2, 02:16:51, Ethernet0/1
| VRF-B-Routing-Tabelle |
LEAK#show ip route vrf B
Routing Table: B
< Snip for resume >
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/30 is directly connected, Ethernet0/0
L 10.0.0.2/32 is directly connected, Ethernet0/0
172.16.0.0/32 is subnetted, 1 subnets
O 172.16.10.10 [110/11] via 10.0.0.1, 00:34:25, Ethernet0/0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
B 192.168.1.0/24 is directly connected, 00:08:51, Ethernet0/1
L 192.168.1.1/32 is directly connected, Ethernet0/1
192.168.11.0/32 is subnetted, 1 subnets
B 192.168.11.11 [20/1024640] via 192.168.1.2, 00:08:51, Ethernet0/1 >> Route from global routing table ( EIGRP ) at VRF B routing table.
Zusätzliche Ressourcen
Revisionsverlauf
| Überarbeitung | Veröffentlichungsdatum | Kommentare |
|---|---|---|
4.0 |
16-Oct-2024 |
Formatierung aktualisiert. |
3.0 |
12-Jan-2023 |
Titelanpassung und ein Autorenname wurde festgelegt. Neu zertifiziert. |
2.0 |
26-Oct-2021 |
Anpassung des Titels und Festlegen eines Autorennamens |
1.0 |
16-Dec-2020 |
Erstveröffentlichung |
Beiträge von Cisco Ingenieuren
- Adriana PachecoTechnical Consulting Engineer
- Jose FonsecaTechnical Consulting Engineer
- Ambrose TaylorCustomer Delivery Engineering Technical Leader
Cisco kontaktieren
- Eine Supportanfrage öffnen

- (Erfordert einen Cisco Servicevertrag)
 Feedback
Feedback